Epic fail resistance 1 or Lisets crept unnoticed. Testing anonymity and security + VPN for a user
Good time reading, dear readers of Habr.
Continuing the theme of Big Data resistance 1 . After reading the comments on the article from dartraiden and YourChief , I started thinking about whether everything is good and whether there are enough anonymity and security tests on 2ip and Whoer, or if everything is fine, it means something isn’t noticed. In addition, a number of problems found on the Internet or faced with them at the time of this writing.
I want to offer to the court of a respected Habrasoobshchestva a compilation of misunderstandings found and suggestions for solving them, as well as a number of ways to test browsers and vulnerabilities.
')
Also, in this article, I propose to consider a simple and free configuration of VPN and secure DNS at the user level.
Structure
I'll start with mistakes from my
A series of browser security tests
A number of problems found hiding IP, browser and OS
Mythic Theoretical File IKnowWhatYouDownloaded
I offer offers
It may be interesting.
Sources
Alas, not without sin. The previous article “big data” is not entirely successful, although it was proposed to create the entire structure on a clean test profile. Since one of the problems is the inconsistency of the work of different components and, as a result, the same under-tuned sites of the Russian Federation, Clear Links and even Privacy Badger can ruin your life. But the configured can greatly simplify it.
The main file with Cookie AutoDelete, as it is implicit, but negates the “first level isolation” (later confirmed, see article number 2 at the end of this chapter).
If you are interested in - currently made a number of edits, you need to re-read Big Data resistance 1 and make the appropriate changes to the equipment of Fox.
SereverWorkers began to appear and add seamlessly to FireFox on many sites. about: serviceworkers consistently gives youtube, yandex and another 100,500. An addon appeared, but literally “the other day” BlockServiceWorkers (so far only two users).
You can also disable SereverWorkers completely, along with synchronization and web notifications (previous article, user.js file)
1. Label E-Tag Website CookielessCookies . (it is safe, but if you do not install addons from the previous article and there are no other similar ones, it will be difficult to get rid of)
2. Isolation of first-level domains and containers
The remaining containers that are offered there, as an example for Google personally, are not worth it, because their appearance seems to be due to the fact that they have a theme and fashionable content, and the functionality of this kind is questionable.
3. Justify the isolation!
Pure empirically:
- If all the necessary and useful services are laid out in containers "by default" and a letter comes from the bank \ social. networks, etc. with a link, then clicking on the link in the browser should appear something in this spirit . If you do not appear, there will be something to think about.
. If you do not appear, there will be something to think about.
- Half of the scam is based on the theft of cookies, etc. - XSS and other mysterious and scary things. At the same time, a phishing link throwsinto the orbit of the planet Earth outside the domain (VKontakte or the bank is unlikely to stick the left page into the domain). Profit from isolation, I think, is obvious (the domains of each other do not see, the data of each other, including the cookie, too).
Clean almost:
- In the previous article, see about EverCookie (for the most part, the problem is solved by isolation and containers, and you cannot do without CanvasBlocker for one item only)
- I highly recommend this testing: BrowserAudit
4. Justify the rest!
With the transfer of arrows (if it does not work, you need to update FireFox)
1. Parable by Specter & Meltdown (below the Click to check button).
2. Check WITCH . Access to the site can be given (the fox will live and will not stop smiling). Not the essence, even what it is (presumably, another breakdown in SMB, which even with Windows XP suddenly gave admin access from under the user), but it should not work. If worked - treatment on Habré (as well as the testing site - the author of the article) .
3. Check for BrowserCheck vulnerabilities. There link:
Without translation of arrows
1. Test encryption .
2. To test the parameters of the user.js file from the previous article, as far as it turned off the main malicious technologies, such as ping in HTML5, you can on the BrowserSpy website
3. You can test the browser on Do I leak .
- If you offer to save data on your computer - you can refuse, it will not break
- If isp. VPN - I propose to allow the torrent test (check Activate additional Torrent Tests.), Give the client a magnetic link and see what the site returns, if you do not understand IP VPN, then you understand).
- If isp. proxy - pay attention to the SSL traffic parameter
Right arrows everywhere, expand the hint on the parameters.
4. You can check external access to the local FireFox repositories (at the bottom is a label, must be Empty and Not supported).
5. Website with advertising . Testing ad blockers
6. If Malwarebytes from the previous article was installed and configured - Blacklist of sites . And the site is not connected with network security, it seems connected with advertising, but the list leads.
Malwarebytes does not block all the transitions, IMHO except phishing sites are not worth the risk and open + this is the site of the Russian Federation, but some of them block, other similar add-ons have coped with a smaller number or did not respond at all.
As for the fingerprint tests. Paying attention:
- The previously proposed CanvasBlocker addon fakes them, not erases them. Those. they are supposed to be, but will change. If nothing changes in the settings of CanvasBlocker, they will change each time - i.e. You can press F5 on the test page and they should change.
- If you set the recommended values (below the spoiler), it will be necessary to restart the browser so that the prints change.
- Some sites burn complex in all respects, including cookies, until you close the tab and clear the same cookies.
1. BrowserLeaks . Just pay attention, there are other tests at the bottom of the page.
2. UberCookie
Everything except SSL encryption and what is related to “FireFox Update” should go through the steps in the previous article. Understand correctly, I’m not an article on PR or a method of my own, it's just that there are answers to how-what is being treated if something “has not passed”.
On testing IP and DNS leaks, I would suggest the following (why - see files below)
1. DnsLeakTest . Displays including and ISP DNS. Some testers only show the country, and this can be, as you understand, both encrypted Cloudflare and, in the event of a leak, MGTS.
2. IpLeak.Net . Here a lot of things unnoticed can be found out. You can protest torrent. Specializes mainly in IP and DNS, but, it seems, without flaws, if there is at least some leakage.
3. IpLeak.Com . Comprehensive analysis (including E-Tag and canvas).
4. WhatLeaks Previously, it was bundled with 2ip, including, there is a passive OS analysis via TCP, cookies and storage, open ports, the presence of IP in blacklists, etc.
5. IP-Score. IP anti fraud detections . Yuzat including MaxMind and Ip2location database bases (switch at the top of the page).
The “History” button is the entire history of visits from an IP address (it can be there for many years, and IP is still dynamic, so it can be there more than once)
Among other things:
- section "Real IP detection", at the bottom of the section button "Run decloaking tests"
- the “Blacklists” section, below the “View” button (different blacklists and what is the IP address. Getting there is typical for a proxy and VPN, but there may be random hits on some list, if from your IP sometime, someone lit up something)
- “Browser information” section, “View” buttons (plugins and headers)
6. And then our all: 2ip and Whoer
Justify for justify!
1. An uncaused Khomak back (attention, Lurka!) Suddenly gathered everything squeezed and in one bottle , however, as always, in three floors and in three rolls (about where the fox can be inserted, see the paragraph “And browsers too!”)
2. This article . I highly recommend it, including to users, since IMHO is concise, accessible and understandable.
3. Anonymous Browser Identification (Habr)
I apologize to the respected Habrasoobschestva. Due to the fact that some of the techniques suggested below can be used for a wide variety of purposes, which is worse, stupid, and at the same time, especially by very young people:
The overall solution proposal - at the end, under the spoilers - is a solution of interest to solve, and not from the point of view of practical use.
Using any user-agent switch, inserting an uncharacteristic type of browser (say, Chrome or IE, etc.), changing the OS and buying anonymity on 2ip and Whoer sites
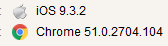
it is not always possible to notice that Chrome, concocted in such a manner - a fox tail gives out
1. Fail 8ab3a24c55ad99f4e3a6e5c03cad9446 (Firefox)
Ip-check
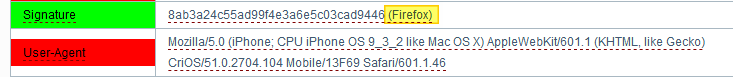
Moreover, in addition, with aterry green color, as according to JonDonym - this is normal (there is a pop-up hint, really in English). Apparently, following his logic, the fact that this does not fit in any way with the user agent is not a bug, but a feature.
2. Fail - clickable touchpad and tapping mouse
I think everyone already guessed from the name, as applied to changing the user agent to a mobile one from the desktop and vice versa Touch - mouse detection, the result should also be exactly the opposite.
3. Fail p0f
The OS, including its version, is delivered not by Fox, but by TCP / IP OS settings. This is caught by sniffers listening to the site (including p0f and nmap).

4. Fail with prints
Comparison of different types of prints at different points in time for the purpose of pursuing foxes, with their competent substitution, leads to a search for neural networks on the 12th tomnik “tracks of animals and birds”, falling into recursion and falling into the astral plane. But comparing the specified user agent with the reference fingerprint for a specific user agent, I think, here, too, is already clear to everyone. Browsers and OS (+ specific "hardware"), as it turned out, leave different.
5. WebRTC or hello again
After installing uBlock Origin and / or Privacy Badger, problems of IP address leakage in this way magically disappear. Only one and the other does not turn off the damned peering, but patches a hole. Which leads to the perfect picture on the above check sites, but invisibly and, worst of all, an imperceptible file with a DNS leak does not always appear after switching to VPN, even if the VPN provider blocks DNSLeaks. Here, perhaps - to disconnect completely.
6. Some other files for clarity.
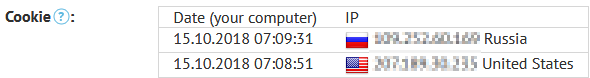
(sudden switch to VPN)

(open ports for attack)
Mythic theoretical story I Know What You Download
It’s not that something is legally forbidden in our country, but it acts on our nerves, but how to check whether you are anonymous or so-so is not always clear.
All that concerns the user agent is to change only within the limits proposed in the previous article to supplement Chameleon.
Disable IPv6 if not used, which is most likely (instead of wi-fi, as in the instructions, it will most likely be Ethernet and the “connected” state). In the same place, at the same time, you can also disable QoS (alert distribution service, not used at home)
A number of facts that came to hand when writing an article:
1. If someone does not know (I did not know until the last moment) - the prototype of FireFox is not a fox, but a small (red) panda . I was interested in this because in addons there are private badgers, even more private opossums and othercrap animals.
2. If Google dials "where I am" will give a place (if there is no wi-fi - stupidly calculate by IP), a photo of the area and the index (if the edblocker does not cut the frame). Yandex doesn’t do that, see that the RF is a rhetorical question, but on Sat. in the morning the plan will not help, therefore Yandex.Taxi.
3. On the topic of cutting advertising Yandex there is a sea of proposals on the Internet, right up to Ban Rambler via host or uBlock. The most difficult and hakrean method known to me -this . There you can hack and everything else, including the expected search results. But then the cookies will have to be stored, and she will follow.
4. On the hidden features of different search engines, sometimes with original functionality (Malwarebytes for some reason blocks, the site is safe): DuckDuckGo , Yandex , Google
5. Yandex has a search for people in all soc. networks .
6. FireFox has Monitor service ( article on Habr). You can try to find out if the e-mail address has been compromised (hacked). Probably the same can be useful if in social. networks that someone offers, especially for money. If his mail in the database lit up - he either an exceptional loser or himself hacked for further fraud.
7. Online there is a website Online Trust . In a clear form to the user is given infa. About the site. Including - the age of the domain in days + below is analyzed by Yandex and Google + by the WOT service + user comments.
In the example, FireFox has a supplement , it promises completely free cheese. And different reviews about him. Check . In addition to the "Fraud" and the "European Union" and "age" of 250 days.
8. As an option, it is convenient to hang up the services on the flagfox button (only it is necessary to disable “receive site icons” in the settings, otherwise it downloads favicons every time).
1. Methods of anonymity online. Just about the complex
2. Fingerprinting of a specific PC with an accuracy of 99.24%: it does not help even changing the browser
3. Passive fingerprinting to detect synthetic traffic
4. Use the Service Worker to create a botnet
5. Surf anonymity checklist
Continuing the theme of Big Data resistance 1 . After reading the comments on the article from dartraiden and YourChief , I started thinking about whether everything is good and whether there are enough anonymity and security tests on 2ip and Whoer, or if everything is fine, it means something isn’t noticed. In addition, a number of problems found on the Internet or faced with them at the time of this writing.
I want to offer to the court of a respected Habrasoobshchestva a compilation of misunderstandings found and suggestions for solving them, as well as a number of ways to test browsers and vulnerabilities.
')
Also, in this article, I propose to consider a simple and free configuration of VPN and secure DNS at the user level.
Structure
- Safety tests / anonymity. IMHO in the comments to the previous article correctly wrote YourChief, but where is the guarantee that something has been achieved and that is enough? I was also interested in this question.
- Feil in general on one topic, just turned out to be not always noticeable. Almost all at once corrected by the choice of adequate user agents. There are proposals for a solution for almost every item, but they are only from the point of view of academic interest.
- VPN + Secure DNS - Addition to the previous article. How to get and configure at user level
I'll start with mistakes from my
A series of browser security tests
A number of problems found hiding IP, browser and OS
- Fail 8ab3a24c55ad99f4e3a6e5c03cad9446 (Firefox)
- Fail - clickable touchpad and taped mouse
- Feil p0f
- Fail with prints
- WebRTC or hello again
- Some other fails for clarity and in order not to forget about them
Mythic Theoretical File IKnowWhatYouDownloaded
I offer offers
It may be interesting.
Sources
I'll start with mistakes from my
Alas, not without sin. The previous article “big data” is not entirely successful, although it was proposed to create the entire structure on a clean test profile. Since one of the problems is the inconsistency of the work of different components and, as a result, the same under-tuned sites of the Russian Federation, Clear Links and even Privacy Badger can ruin your life. But the configured can greatly simplify it.
The main file with Cookie AutoDelete, as it is implicit, but negates the “first level isolation” (later confirmed, see article number 2 at the end of this chapter).
If you are interested in - currently made a number of edits, you need to re-read Big Data resistance 1 and make the appropriate changes to the equipment of Fox.
SereverWorkers began to appear and add seamlessly to FireFox on many sites. about: serviceworkers consistently gives youtube, yandex and another 100,500. An addon appeared, but literally “the other day” BlockServiceWorkers (so far only two users).
It works like this
When the site attempts to connect ServerWorkers, a window appears

The installation will not happen if you do not click on this window (when clicked, the page will reload and ServiceWorkers will be installed). At the current moment - anywhere the installation did not allow, until nothing broke, but if some background synchronization of some data with the site is required, then it will be necessary to allow the installation.

The installation will not happen if you do not click on this window (when clicked, the page will reload and ServiceWorkers will be installed). At the current moment - anywhere the installation did not allow, until nothing broke, but if some background synchronization of some data with the site is required, then it will be necessary to allow the installation.
You can also disable SereverWorkers completely, along with synchronization and web notifications (previous article, user.js file)
Justify threats and solutions! A series of browser security tests
1. Label E-Tag Website CookielessCookies . (it is safe, but if you do not install addons from the previous article and there are no other similar ones, it will be difficult to get rid of)
You can protest this way
You need to write something, press the "store" button and then try to get rid of this label. When using Chameleon and Cookiebro - even if not deleted, after 2-3 reopenings and pressing F5 - it will disappear by itself, if deleted through Cookiebro by clicking "Clear ..." - it disappears immediately.

You need to write something, press the "store" button and then try to get rid of this label. When using Chameleon and Cookiebro - even if not deleted, after 2-3 reopenings and pressing F5 - it will disappear by itself, if deleted through Cookiebro by clicking "Clear ..." - it disappears immediately.
2. Isolation of first-level domains and containers
I think I can add an addon to isolation
Containers on the go adds a button to the tabs.  and in the context menu item
and in the context menu item  .
.
Open tab with a new temporary (!) Container. Everything (cookies, data), what happens there, will be reset to zero when all tabs of this container are closed.
 and in the context menu item
and in the context menu item  .
.Open tab with a new temporary (!) Container. Everything (cookies, data), what happens there, will be reset to zero when all tabs of this container are closed.
The remaining containers that are offered there, as an example for Google personally, are not worth it, because their appearance seems to be due to the fact that they have a theme and fashionable content, and the functionality of this kind is questionable.
3. Justify the isolation!
Pure empirically:
- If all the necessary and useful services are laid out in containers "by default" and a letter comes from the bank \ social. networks, etc. with a link, then clicking on the link in the browser should appear something in this spirit
 . If you do not appear, there will be something to think about.
. If you do not appear, there will be something to think about.- Half of the scam is based on the theft of cookies, etc. - XSS and other mysterious and scary things. At the same time, a phishing link throws
Clean almost:
- In the previous article, see about EverCookie (for the most part, the problem is solved by isolation and containers, and you cannot do without CanvasBlocker for one item only)
- I highly recommend this testing: BrowserAudit
Check for all sorts of vulnerabilities
Tests pass minutes 3, so it was boring, where the panel with “Test Details” can be deployed androbbed , you can see how the tests go.
Expected to be warnings of such a plan: test.browseraudit.com -> browseraudit.com. The isolation does not apply to subdomains; on the other hand, on some sites, registration is tied to this.
IMHO a real file if it shows a transmission error of the type: browseraudit.com -> browseraudit.org - because This is the unfortunate forwarding a'lya XSS.
(For those interested in appearing tests, there are also deployable panels with program codes of a specific vulnerability under test)

Tests pass minutes 3, so it was boring, where the panel with “Test Details” can be deployed and
Expected to be warnings of such a plan: test.browseraudit.com -> browseraudit.com. The isolation does not apply to subdomains; on the other hand, on some sites, registration is tied to this.
IMHO a real file if it shows a transmission error of the type: browseraudit.com -> browseraudit.org - because This is the unfortunate forwarding a'lya XSS.
(For those interested in appearing tests, there are also deployable panels with program codes of a specific vulnerability under test)
4. Justify the rest!
With the transfer of arrows (if it does not work, you need to update FireFox)
1. Parable by Specter & Meltdown (below the Click to check button).
2. Check WITCH . Access to the site can be given (the fox will live and will not stop smiling). Not the essence, even what it is (presumably, another breakdown in SMB, which even with Windows XP suddenly gave admin access from under the user), but it should not work. If worked - treatment on Habré (as well as the testing site - the author of the article) .
3. Check for BrowserCheck vulnerabilities. There link:

Without translation of arrows
1. Test encryption .
If feil
- Put HTTPS everywhere (see previous article)
- Mixed Content Tests (mixed content, allows https and http at the same time), can be turned off in FireFox, googling, but there mostly - Image and can break websites
- Problems with unreliable and outdated protocols. What can break when disconnected I do not know, but something can
about: config
Problem with TLS 1.0 - security.tls.version.min = 2
Problems with TLS_RSA_WITH_AES_128_CBC_SHA, etc.
security.ssl3.rsa_aes_128_sha = false
security.ssl3.rsa_aes_256_sha = false
security.ssl3.rsa_des_ede3_sha = false
- Mixed Content Tests (mixed content, allows https and http at the same time), can be turned off in FireFox, googling, but there mostly - Image and can break websites
- Problems with unreliable and outdated protocols. What can break when disconnected I do not know, but something can
about: config
Problem with TLS 1.0 - security.tls.version.min = 2
Problems with TLS_RSA_WITH_AES_128_CBC_SHA, etc.
security.ssl3.rsa_aes_128_sha = false
security.ssl3.rsa_aes_256_sha = false
security.ssl3.rsa_des_ede3_sha = false
2. To test the parameters of the user.js file from the previous article, as far as it turned off the main malicious technologies, such as ping in HTML5, you can on the BrowserSpy website
3. You can test the browser on Do I leak .
- If you offer to save data on your computer - you can refuse, it will not break
- If isp. VPN - I propose to allow the torrent test (check Activate additional Torrent Tests.), Give the client a magnetic link and see what the site returns, if you do not understand IP VPN, then you understand).
- If isp. proxy - pay attention to the SSL traffic parameter
Right arrows everywhere, expand the hint on the parameters.
4. You can check external access to the local FireFox repositories (at the bottom is a label, must be Empty and Not supported).
5. Website with advertising . Testing ad blockers
6. If Malwarebytes from the previous article was installed and configured - Blacklist of sites . And the site is not connected with network security, it seems connected with advertising, but the list leads.
Malwarebytes does not block all the transitions, IMHO except phishing sites are not worth the risk and open + this is the site of the Russian Federation, but some of them block, other similar add-ons have coped with a smaller number or did not respond at all.
As for the fingerprint tests. Paying attention:
- The previously proposed CanvasBlocker addon fakes them, not erases them. Those. they are supposed to be, but will change. If nothing changes in the settings of CanvasBlocker, they will change each time - i.e. You can press F5 on the test page and they should change.
- If you set the recommended values (below the spoiler), it will be necessary to restart the browser so that the prints change.
- Some sites burn complex in all respects, including cookies, until you close the tab and clear the same cookies.
About settings CanvasBlocker
- I don’t think it’s worthwhile to set the change of prints for each request (set by default).
When paying for mobile, utilities, etc. real difficulties may arise if you forget to add sites to the white list or disable the spoofing of prints. Pativen is unlikely to come, but a number of questions may arise.
In the settings you can set as follows:
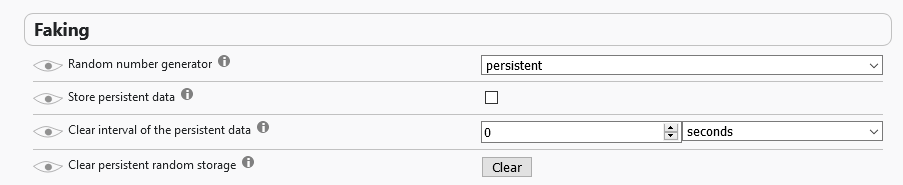
Fingerprints will change once the browser is started (session). But, for each domain (with subdomains) they will be different for the duration of the session (you can check simultaneously with two different canvas checkers). And since the task with fingerprints, IMHO, is not to deceive the site, and not to let the path through the sites be followed in one way or another with the definition of user preferences and other things useful for advertising - this should be solved.
0 seconds (or any other time interval) is a trip. Expose a timer shift IMHO, too, is not worth it, because it will be unclear at what moment it will happen and what exactly at this moment you will do.
“Clear” - performs a forced change of fingerprints, with such settings as above.
- I think that in the CanvasBlocker it is worthwhile to set minimal changes to fingerprints (or rather not to change them, they are minimal by default). It should still work, but there is less chance that something will break, because, you know, prints are still using ordinary web technologies that were not invented for such purposes + see below for a comparison of prints with a standard.
CanvasBlocker does not replace plugins, geolocation, WebRTC, WebGL Report Hash - vendor, renderer. ("WebGL Image Hash" - substitutes). To disable these options, see the previous article, the “user.js” file, and comments on the article.
CanvasBlocker by default (this can be done in the settings by ticking “Expert mode”):
- Does not replace fonts. Settings "Lists" - "whitelist", but after that get the difficulty with Google Doc and other useful things in the household.
- The protection of "windows.name" is disabled. Settings “Window API” - “Protected windows API”, since after that the captcha “I am not a robot” stops working, and you can see it, after setting a tick, everything looks fine, and the window with pictures does not appear. In Chameleon, it is also there, there it is, if anything, it is more convenient to turn it on / off - since it’s on the panels and you don’t need to go to the expansion settings.
When paying for mobile, utilities, etc. real difficulties may arise if you forget to add sites to the white list or disable the spoofing of prints. Pativen is unlikely to come, but a number of questions may arise.
In the settings you can set as follows:

Fingerprints will change once the browser is started (session). But, for each domain (with subdomains) they will be different for the duration of the session (you can check simultaneously with two different canvas checkers). And since the task with fingerprints, IMHO, is not to deceive the site, and not to let the path through the sites be followed in one way or another with the definition of user preferences and other things useful for advertising - this should be solved.
0 seconds (or any other time interval) is a trip. Expose a timer shift IMHO, too, is not worth it, because it will be unclear at what moment it will happen and what exactly at this moment you will do.
“Clear” - performs a forced change of fingerprints, with such settings as above.
- I think that in the CanvasBlocker it is worthwhile to set minimal changes to fingerprints (or rather not to change them, they are minimal by default). It should still work, but there is less chance that something will break, because, you know, prints are still using ordinary web technologies that were not invented for such purposes + see below for a comparison of prints with a standard.
CanvasBlocker does not replace plugins, geolocation, WebRTC, WebGL Report Hash - vendor, renderer. ("WebGL Image Hash" - substitutes). To disable these options, see the previous article, the “user.js” file, and comments on the article.
CanvasBlocker by default (this can be done in the settings by ticking “Expert mode”):
- Does not replace fonts. Settings "Lists" - "whitelist", but after that get the difficulty with Google Doc and other useful things in the household.
- The protection of "windows.name" is disabled. Settings “Window API” - “Protected windows API”, since after that the captcha “I am not a robot” stops working, and you can see it, after setting a tick, everything looks fine, and the window with pictures does not appear. In Chameleon, it is also there, there it is, if anything, it is more convenient to turn it on / off - since it’s on the panels and you don’t need to go to the expansion settings.
List of prints
CanvasBlocker substitutes (the fingerprint functionality is the same as the anti-browser browsers):
· Canvas. The HTML5 element for displaying graphics depends on the characteristics of the video system.
· Audiofingerprint. A technology that allows you to identify a computer by the audio system: a small sound file is played in the background, an oscillogram is taken.
· WebGL (WebGL Image Hash). Browser implementation of OpenGL, designed to work with three-dimensional graphics in the browser.
· ClientRects. Identification method based on receiving hashes when scaling an image.
· Ubercookies. Hash from ClientRects and Audiofingerprint, allows you to identify the device with a high degree of probability.
All but Ubercookies can be tested on BrowserLeaks (see below).
Recently, there have been technologies for fingerprinting mouse movements and typing on a keyboard. The ScriptSafe addon is able to make the appropriate noise (interface in Russian), but
· Its functionality combines CanvasBlocker, NoScript, adBlocker, and a) not yet such flexible settings for each functional b) IMHO a lot of unnecessary for the user c) his description is a separate article
· In order to be able to reliably track the user across different sites, it is necessary that the technology be distributed, now it seems to be wrong, I think if it spreads, the CanvasBlocker will be improved.
· Canvas. The HTML5 element for displaying graphics depends on the characteristics of the video system.
· Audiofingerprint. A technology that allows you to identify a computer by the audio system: a small sound file is played in the background, an oscillogram is taken.
· WebGL (WebGL Image Hash). Browser implementation of OpenGL, designed to work with three-dimensional graphics in the browser.
· ClientRects. Identification method based on receiving hashes when scaling an image.
· Ubercookies. Hash from ClientRects and Audiofingerprint, allows you to identify the device with a high degree of probability.
All but Ubercookies can be tested on BrowserLeaks (see below).
Recently, there have been technologies for fingerprinting mouse movements and typing on a keyboard. The ScriptSafe addon is able to make the appropriate noise (interface in Russian), but
· Its functionality combines CanvasBlocker, NoScript, adBlocker, and a) not yet such flexible settings for each functional b) IMHO a lot of unnecessary for the user c) his description is a separate article
· In order to be able to reliably track the user across different sites, it is necessary that the technology be distributed, now it seems to be wrong, I think if it spreads, the CanvasBlocker will be improved.
An example of spherical nanotechnology in a vacuum, at least for the time being spherical
Mouse wheel . Some Jose Carlos Norte .
This Malevich proposes to hover the mouse on the red square and scroll (sometimes with the touch of a button it works). Displays data on the chart.
Translation from his page:
The mouse wheel scrolling event in most browsers (including Tor) provides information about the scroll delta. For an ordinary mouse, it is 3, but when using the trackpad, the deltas are variable and are associated with the trackpad and usage patterns. Also, the fingerprint can be the scrolling speed associated with the operating system configuration and hardware capabilities.
This Malevich proposes to hover the mouse on the red square and scroll (sometimes with the touch of a button it works). Displays data on the chart.
Translation from his page:
The mouse wheel scrolling event in most browsers (including Tor) provides information about the scroll delta. For an ordinary mouse, it is 3, but when using the trackpad, the deltas are variable and are associated with the trackpad and usage patterns. Also, the fingerprint can be the scrolling speed associated with the operating system configuration and hardware capabilities.
1. BrowserLeaks . Just pay attention, there are other tests at the bottom of the page.
2. UberCookie
Everything except SSL encryption and what is related to “FireFox Update” should go through the steps in the previous article. Understand correctly, I’m not an article on PR or a method of my own, it's just that there are answers to how-what is being treated if something “has not passed”.
On testing IP and DNS leaks, I would suggest the following (why - see files below)
1. DnsLeakTest . Displays including and ISP DNS. Some testers only show the country, and this can be, as you understand, both encrypted Cloudflare and, in the event of a leak, MGTS.
2. IpLeak.Net . Here a lot of things unnoticed can be found out. You can protest torrent. Specializes mainly in IP and DNS, but, it seems, without flaws, if there is at least some leakage.
3. IpLeak.Com . Comprehensive analysis (including E-Tag and canvas).
4. WhatLeaks Previously, it was bundled with 2ip, including, there is a passive OS analysis via TCP, cookies and storage, open ports, the presence of IP in blacklists, etc.
5. IP-Score. IP anti fraud detections . Yuzat including MaxMind and Ip2location database bases (switch at the top of the page).
The “History” button is the entire history of visits from an IP address (it can be there for many years, and IP is still dynamic, so it can be there more than once)
Among other things:
- section "Real IP detection", at the bottom of the section button "Run decloaking tests"
- the “Blacklists” section, below the “View” button (different blacklists and what is the IP address. Getting there is typical for a proxy and VPN, but there may be random hits on some list, if from your IP sometime, someone lit up something)
- “Browser information” section, “View” buttons (plugins and headers)
6. And then our all: 2ip and Whoer
Justify for justify!
1. An uncaused Khomak back (attention, Lurka!) Suddenly gathered everything squeezed and in one bottle , however, as always, in three floors and in three rolls (about where the fox can be inserted, see the paragraph “And browsers too!”)
2. This article . I highly recommend it, including to users, since IMHO is concise, accessible and understandable.
3. Anonymous Browser Identification (Habr)
I apologize to the respected Habrasoobschestva. Due to the fact that some of the techniques suggested below can be used for a wide variety of purposes, which is worse, stupid, and at the same time, especially by very young people:
Disclaimer
1. Everything set forth in these articles is to suggest options for how to avoid some common problems, and not to find new ones for your job.
2. If that, “they will still hit on the IP-passport”, regardless of the fact that on this non-passport, an anonymus mask or, especially, a hood mask.
In general, Joe is inconceivable - and the answer to the question “until he is elusive” is contained in the joke itself.
2. If that, “they will still hit on the IP-passport”, regardless of the fact that on this non-passport, an anonymus mask or, especially, a hood mask.
In general, Joe is inconceivable - and the answer to the question “until he is elusive” is contained in the joke itself.
Now tailing! A number of problems found hiding IP, browser and OS
The overall solution proposal - at the end, under the spoilers - is a solution of interest to solve, and not from the point of view of practical use.
Using any user-agent switch, inserting an uncharacteristic type of browser (say, Chrome or IE, etc.), changing the OS and buying anonymity on 2ip and Whoer sites

it is not always possible to notice that Chrome, concocted in such a manner - a fox tail gives out
1. Fail 8ab3a24c55ad99f4e3a6e5c03cad9446 (Firefox)
Ip-check

Moreover, in addition, with a
For those who are interested
Fail in order of issuing http headers, scorching fox, who wouldn’t pretend. The same is true for the Tor browser, if you enable java with this test ( a php implementation of a similar setup, the function createHeaderSignature function)
I suggest the following option:
1. Install Simple modify header addon
2. Remove Accept-Language header
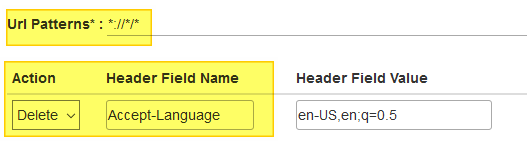
The result - traces of unseen beasts.
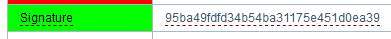
But with a “serious” definition, it looks like this:
I suggest the following option:
1. Install Simple modify header addon
2. Remove Accept-Language header


The result - traces of unseen beasts.

But with a “serious” definition, it looks like this:

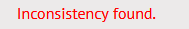
2. Fail - clickable touchpad and tapping mouse
I think everyone already guessed from the name, as applied to changing the user agent to a mobile one from the desktop and vice versa Touch - mouse detection, the result should also be exactly the opposite.
For those who are interested
Standard FireFox tool called by F12 -  “Adaptive Design Mode”.
“Adaptive Design Mode”.
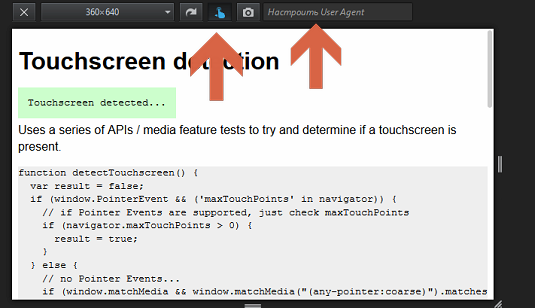
(here you can even simulate the presence of a touchscreen and add a mobile user agent)
However, this mobility problem does not solve - the stationary company, who would have thought, does not have an accelerometer, a gyroscope and other uncharacter filling, access to which is from the outside , some of the mobiles are turned off only by a soldering iron, just so far this access has gone far only "ahead of time" , but it’s clear that you can check.
 “Adaptive Design Mode”.
“Adaptive Design Mode”.
(here you can even simulate the presence of a touchscreen and add a mobile user agent)
However, this mobility problem does not solve - the stationary company, who would have thought, does not have an accelerometer, a gyroscope and other uncharacter filling, access to which is from the outside , some of the mobiles are turned off only by a soldering iron, just so far this access has gone far only "ahead of time" , but it’s clear that you can check.
3. Fail p0f
The OS, including its version, is delivered not by Fox, but by TCP / IP OS settings. This is caught by sniffers listening to the site (including p0f and nmap).

For those who are interested
There is a TCPOptimizer administration utility used to automatically optimize the Windows network.
Theoretically, with its help, you can customize the settings, in practice, if you use the spear method, you can shoot Winde’s leg, so this experiment is not recommended, the previous ones, at least without such consequences. Yes, and change the OS from Windows to Linux - is unlikely to succeed, except that within versions of Windows 7/10.
However, it is possible to try to optimize the network with its help, after creating a restore point, indicating the Internet speed with the slider and selecting the “optimal” mode. Until now, it seems to be not let down.
Theoretically, with its help, you can customize the settings, in practice, if you use the spear method, you can shoot Winde’s leg, so this experiment is not recommended, the previous ones, at least without such consequences. Yes, and change the OS from Windows to Linux - is unlikely to succeed, except that within versions of Windows 7/10.
However, it is possible to try to optimize the network with its help, after creating a restore point, indicating the Internet speed with the slider and selecting the “optimal” mode. Until now, it seems to be not let down.
4. Fail with prints
Comparison of different types of prints at different points in time for the purpose of pursuing foxes, with their competent substitution, leads to a search for neural networks on the 12th tomnik “tracks of animals and birds”, falling into recursion and falling into the astral plane. But comparing the specified user agent with the reference fingerprint for a specific user agent, I think, here, too, is already clear to everyone. Browsers and OS (+ specific "hardware"), as it turned out, leave different.
5. WebRTC or hello again
After installing uBlock Origin and / or Privacy Badger, problems of IP address leakage in this way magically disappear. Only one and the other does not turn off the damned peering, but patches a hole. Which leads to the perfect picture on the above check sites, but invisibly and, worst of all, an imperceptible file with a DNS leak does not always appear after switching to VPN, even if the VPN provider blocks DNSLeaks. Here, perhaps - to disconnect completely.
6. Some other files for clarity.

(sudden switch to VPN)

(open ports for attack)
Mythic theoretical story I Know What You Download
It’s not that something is legally forbidden in our country, but it acts on our nerves, but how to check whether you are anonymous or so-so is not always clear.
I offer offers
All that concerns the user agent is to change only within the limits proposed in the previous article to supplement Chameleon.
Disable IPv6 if not used, which is most likely (instead of wi-fi, as in the instructions, it will most likely be Ethernet and the “connected” state). In the same place, at the same time, you can also disable QoS (alert distribution service, not used at home)
DNS offer
Install Simple DNSCrypt

More details can be found here . Especially if something is not working. Reboot.
Test on DnsLeakTest by clicking on the “Extended test” button.

Tune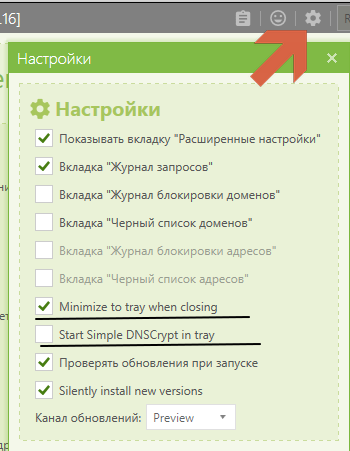
To always display the tray - you can put two underlined checkboxes.
1. Tab "Main" (you may be more lucky with the Russification)
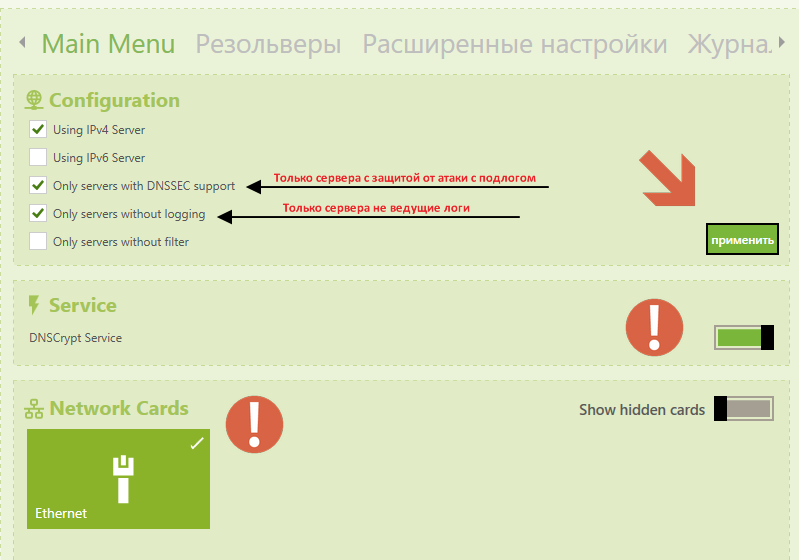
“Configuration” - filtering DNS servers (see the second tab).
The service must be turned on, ticked on the network card, click "Apply".
2. Tab "Resolvers"
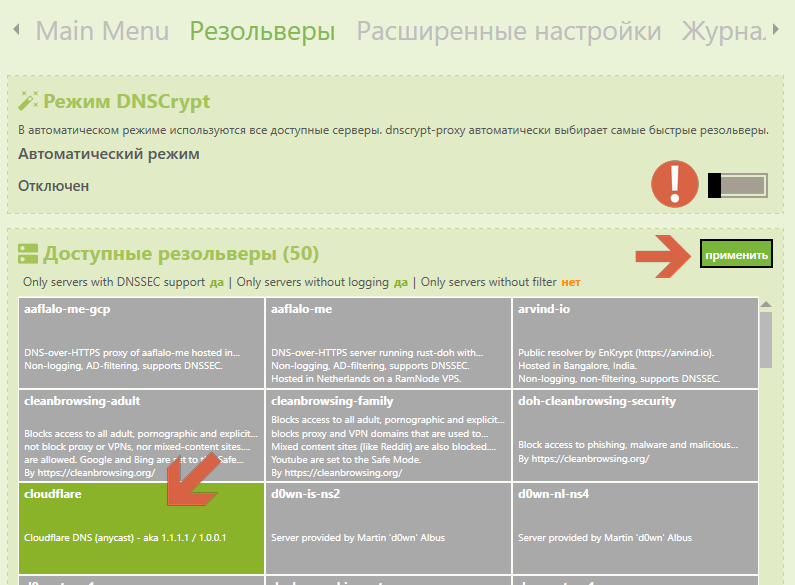
I propose to disable the automatic mode. Remove from the list all the servers that are installed there, leaving only one Cloudflare.
Yes, it is “commercial”, but on the first tab it was set up without logs. And Google did not get something on this list.
Others do not advise.
Firstly, there is not everything with encryption and not everything "without leaks." Secondly, it is not entirely clear what kind of DNS it is (although, on the Internet, there is, of course, information). Thirdly, it is “public”, in the good sense of the word. Many people use in all countries and even if suddenly the country IP does not coincide with the DNS, but it will show that this is Cloudflare - there will be no problems. Put another one - for the same reasons, IMHO is not worth it, the program will choose the most nimble at any given time and there may suddenly be a leak and stuff like that.
3. Advanced Settings Tab

I suggest the IP address of the reserve resolver 8.26.56.26 (this is Comodo Secure DNS )
4. Log tab - disable logging.
This will be for the entire system, including all programs. For FireFox, you can, too , for loyalty.

To always display the tray - you can put two underlined checkboxes.
1. Tab "Main" (you may be more lucky with the Russification)

“Configuration” - filtering DNS servers (see the second tab).
The service must be turned on, ticked on the network card, click "Apply".
2. Tab "Resolvers"

I propose to disable the automatic mode. Remove from the list all the servers that are installed there, leaving only one Cloudflare.
Yes, it is “commercial”, but on the first tab it was set up without logs. And Google did not get something on this list.
Others do not advise.
Firstly, there is not everything with encryption and not everything "without leaks." Secondly, it is not entirely clear what kind of DNS it is (although, on the Internet, there is, of course, information). Thirdly, it is “public”, in the good sense of the word. Many people use in all countries and even if suddenly the country IP does not coincide with the DNS, but it will show that this is Cloudflare - there will be no problems. Put another one - for the same reasons, IMHO is not worth it, the program will choose the most nimble at any given time and there may suddenly be a leak and stuff like that.
3. Advanced Settings Tab

I suggest the IP address of the reserve resolver 8.26.56.26 (this is Comodo Secure DNS )
4. Log tab - disable logging.
This will be for the entire system, including all programs. For FireFox, you can, too , for loyalty.
More details can be found here . Especially if something is not working. Reboot.
Test on DnsLeakTest by clicking on the “Extended test” button.
The result should be something like this.
Note. The server shows the ownership of Cloudflare, and on other sites, often, only IP and its “citizenship”. And most likely everything will be the Russian Federation. , DNS — Cloudflare , , .
, , 2ip . :
( (. ), — + + IP).


Note. The server shows the ownership of Cloudflare, and on other sites, often, only IP and its “citizenship”. And most likely everything will be the Russian Federation. , DNS — Cloudflare , , .
, , 2ip . :

( (. ), — + + IP).
VPN offer
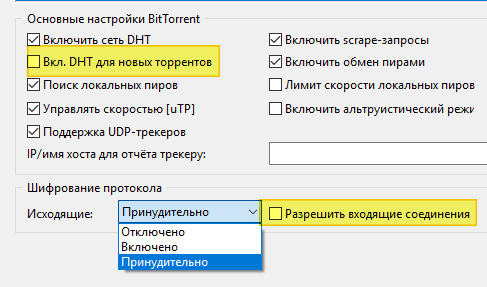
1. VPN — Chameleon .
2. VPN- , .. (. ) . Those. , «» — «».
10 — WindScribe , . , ( , 10 , — 2, — . ).
. , IP :
1. DnsLeakTest
2. IpLeak
3. WhatLeaks
4. 2ip .ru Whoer
Attention! ( , , )
, . .. — VPN (. cookies). () . , «WindScribe». . — .
() ! + , IP- VPN.
2. VPN- , .. (. ) . Those. , «» — «».
10 — WindScribe , . , ( , 10 , — 2, — . ).
To register
1. ( FireFox ), . (, , !)
— «Automatic» , . , , .. IP
— — ,
— « Secure.Link» — - ,
2.
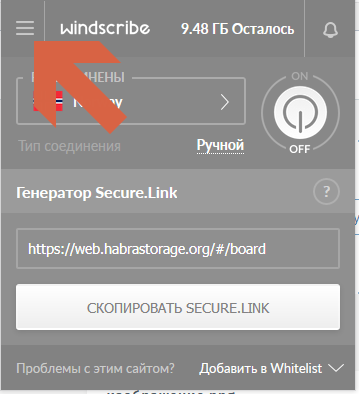
— « » — , , , — ().
— « » — . , ( ), , .
— VPN. , Chameleon "+1".

— «Automatic» , . , , .. IP
— — ,
— « Secure.Link» — - ,
2.


— « » — , , , — ().
— « » — . , ( ), , .
— VPN. , Chameleon "+1".
. , IP :
1. DnsLeakTest
2. IpLeak
3. WhatLeaks
4. 2ip .ru Whoer
10
Attention! ( , , )
, . .. — VPN (. cookies). () . , «WindScribe». . — .
() ! + , IP- VPN.
1. ( « », « » .. — , )
2. : ( , ) Windows ( - , . ). «» « Ipv6» .
3. + , Double VPN

4. 10 , \ . , «»
2. : ( , ) Windows ( - , . ). «» « Ipv6» .
3. + , Double VPN

4. 10 , \ . , «»
Torrent Offer
It may be interesting.
A number of facts that came to hand when writing an article:
1. If someone does not know (I did not know until the last moment) - the prototype of FireFox is not a fox, but a small (red) panda . I was interested in this because in addons there are private badgers, even more private opossums and other
2. If Google dials "where I am" will give a place (if there is no wi-fi - stupidly calculate by IP), a photo of the area and the index (if the edblocker does not cut the frame). Yandex doesn’t do that, see that the RF is a rhetorical question, but on Sat. in the morning the plan will not help, therefore Yandex.Taxi.
3. On the topic of cutting advertising Yandex there is a sea of proposals on the Internet, right up to Ban Rambler via host or uBlock. The most difficult and hakrean method known to me -this . There you can hack and everything else, including the expected search results. But then the cookies will have to be stored, and she will follow.
4. On the hidden features of different search engines, sometimes with original functionality (Malwarebytes for some reason blocks, the site is safe): DuckDuckGo , Yandex , Google
5. Yandex has a search for people in all soc. networks .
6. FireFox has Monitor service ( article on Habr). You can try to find out if the e-mail address has been compromised (hacked). Probably the same can be useful if in social. networks that someone offers, especially for money. If his mail in the database lit up - he either an exceptional loser or himself hacked for further fraud.
7. Online there is a website Online Trust . In a clear form to the user is given infa. About the site. Including - the age of the domain in days + below is analyzed by Yandex and Google + by the WOT service + user comments.
In the example, FireFox has a supplement , it promises completely free cheese. And different reviews about him. Check . In addition to the "Fraud" and the "European Union" and "age" of 250 days.
8. As an option, it is convenient to hang up the services on the flagfox button (only it is necessary to disable “receive site icons” in the settings, otherwise it downloads favicons every time).
Sources from Habr
1. Methods of anonymity online. Just about the complex
2. Fingerprinting of a specific PC with an accuracy of 99.24%: it does not help even changing the browser
3. Passive fingerprinting to detect synthetic traffic
4. Use the Service Worker to create a botnet
5. Surf anonymity checklist
Source: https://habr.com/ru/post/426009/
All Articles