Conference DEFCON 20. How to fuck the bad guys (and the mafia) using a JavaScript botnet. Part 2
Conference DEFCON 20. How to fuck the bad guys (and the mafia) using a JavaScript botnet. Part 1
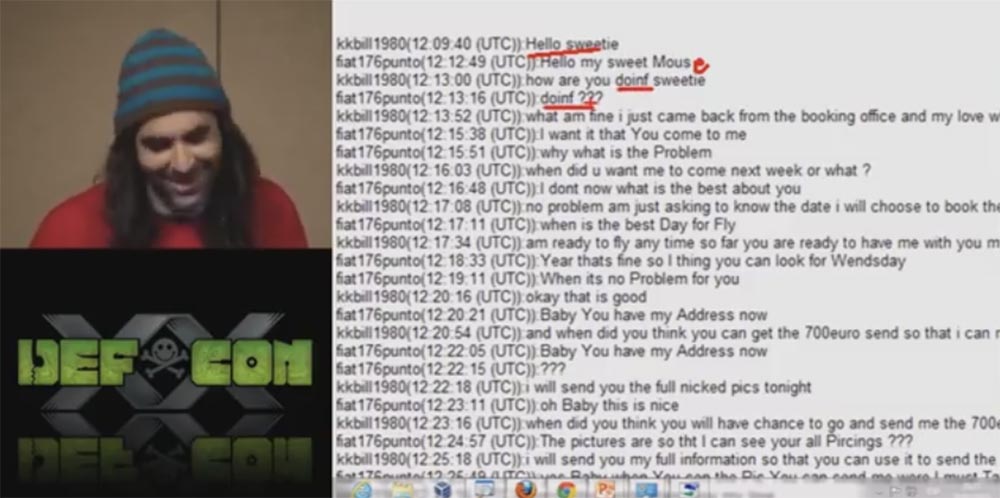
This guy kept all the chats with those who are interested in the profile of this girl. This slide shows my favorite chat, kkbill1980 is the one who pretends to be a girl, and fiat176punt is his victim. “Kkbill1980: hello, sweetie! - fiat176punto: hello, my sweet mouse! ”, And so on, very cheerful chat.
')
Further in the chat, they discuss the details of their love relationship, and the most interesting detail is 700 euros, which the victim must send to her “sweet mouse” as if to book a hotel during a fake girl’s trip to Germany.
And then the fan writes that this night he sent his beloved a “completely nude photo”, to which she replies: “Oh, baby, this is wonderful!”
The bottom line is that this scam guy talked to a lot of people at the same time with the help of fake girls profiles on dating sites and extorted money from his victims on one pretext or another. However, somewhere in the middle of the chat, this guy “punctured”, apparently confusing the open tabs, and began to write in German.
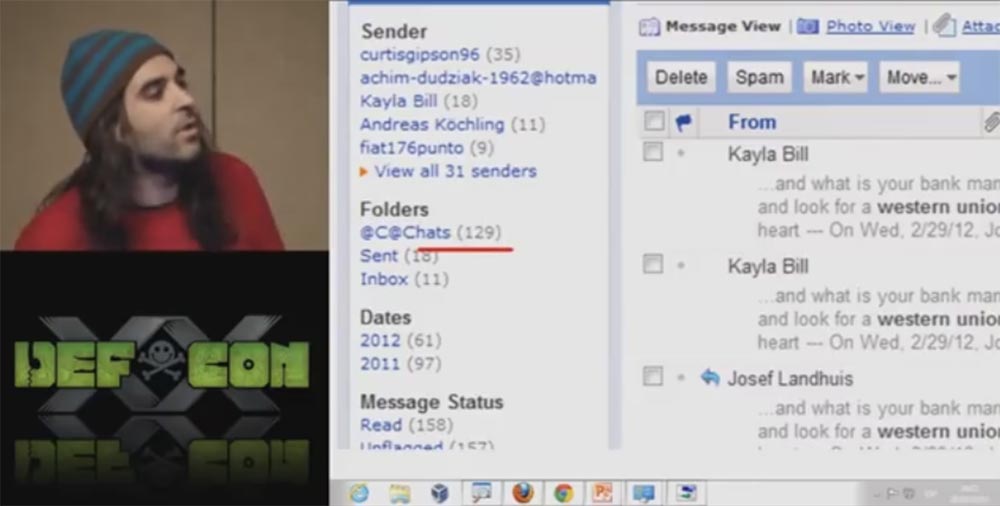
In his mailbox everything was perfectly systematized, and he kept all his chats in a special folder, with which he continued to work even now. We decided to find in the correspondence all the references to the men who were going to use Western Union to send money to their "lover", and found 158 such messages.
The next slide shows a sample of the correspondence of this girl and the victim. Photos are again mentioned here - the girl asks why the man did not send her the promised “naked” photos. And he answers that he does not know why, but the bank manager told him that it was impossible to send money to the address indicated, so let the girl give him some other address.
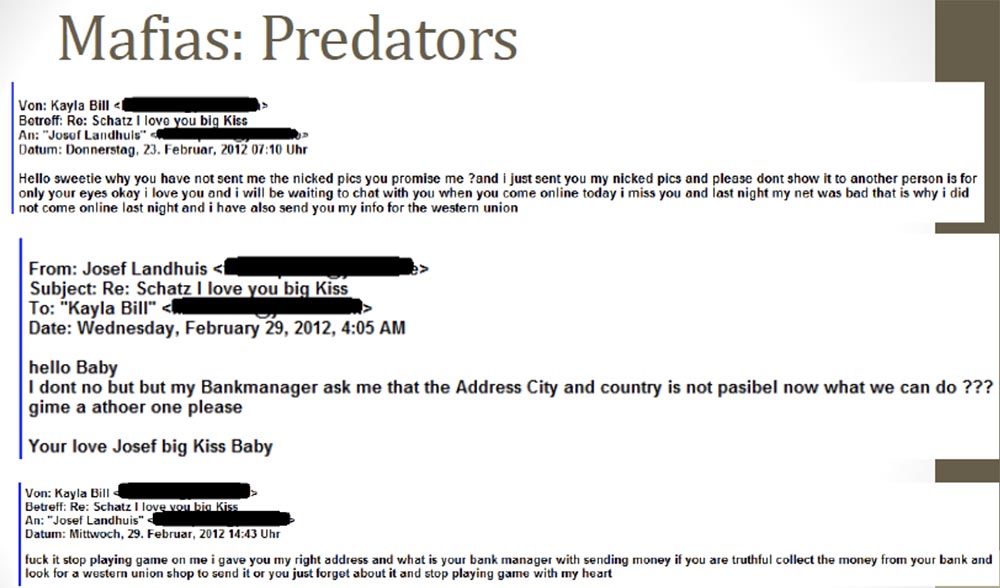
This is because the profile of the girl was given a fake address, which, apparently, did not suit the bank clerk. To which the fake girl angrily replies: “fuck, stop playing games with me! I gave you the correct address, so take the money from the bank and send it to me through Western Union, otherwise forget about everything and stop playing games with my heart! ”
In general, you can imagine what it was for the correspondence. And this scheme worked, because for sending money through Western Union it is enough to specify only the city and the name of the recipient of the transfer, and then tell him the secret code.
The next case, which interested us, was a crook associated with dogs. We wondered what he did with dogs if he needed an anonymous proxy server for his work?
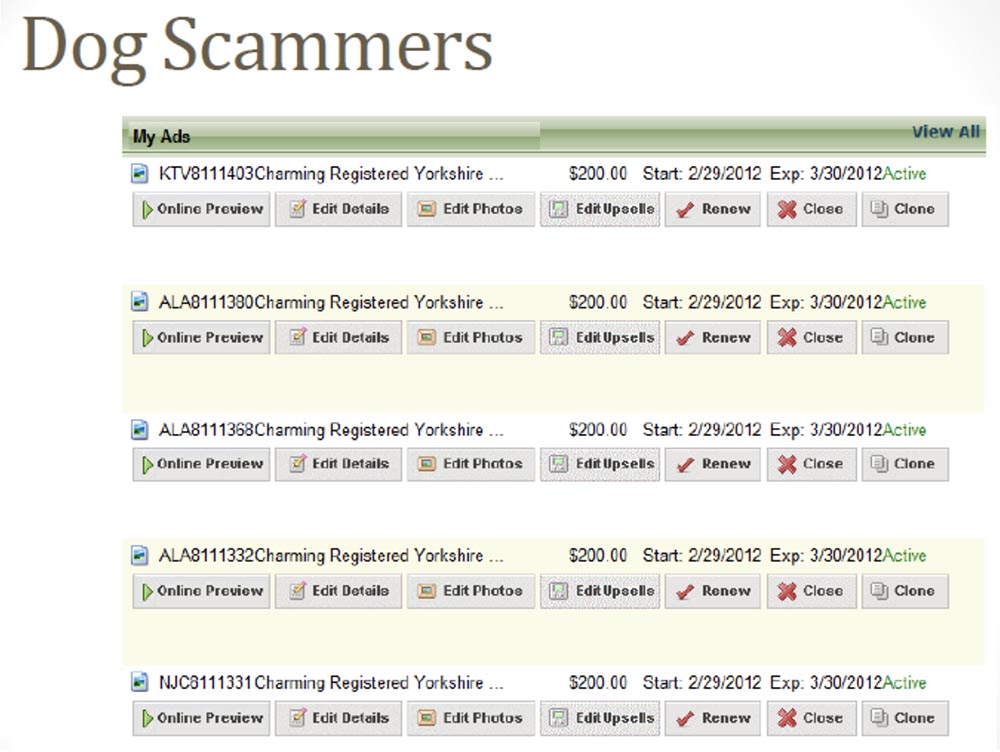
We, as usual, decided to use his username and password to get into his inbox. And there we found something heavy, so if you love animals, do not look at the next picture. On the next slide, we even posted the following warning: “Attention! This picture can hurt your feelings! ” But, actually, the picture itself.
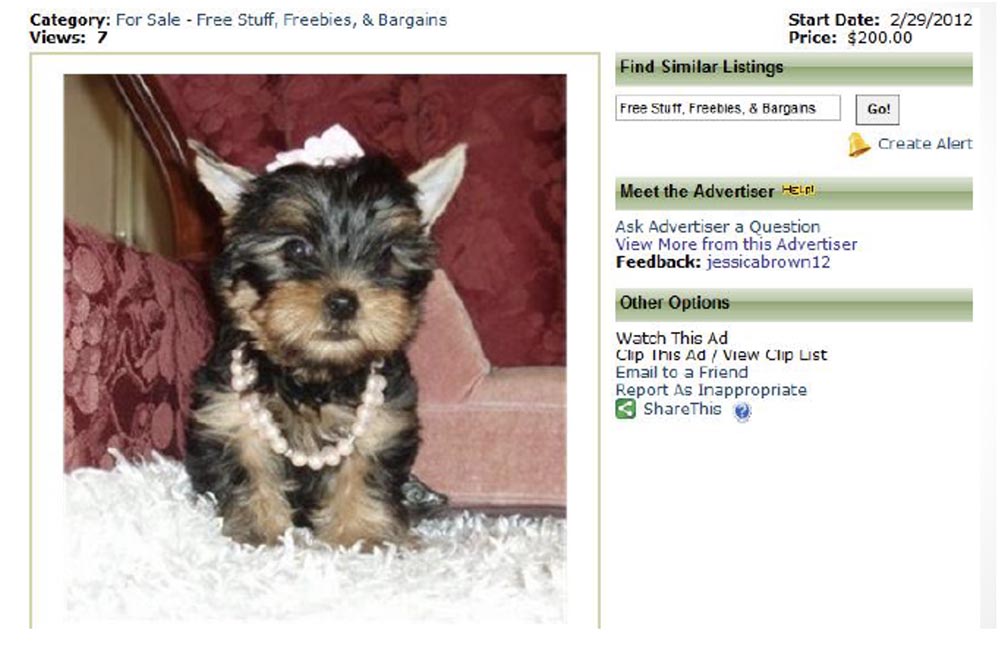
He placed this fake Yorkshire terrier, fake, because he placed the same dog for sale all over the world, so this is the most profitable york on earth. He put this picture and made money on it, as the cheapness of the purebred dog tempted everyone and they made an advance payment.
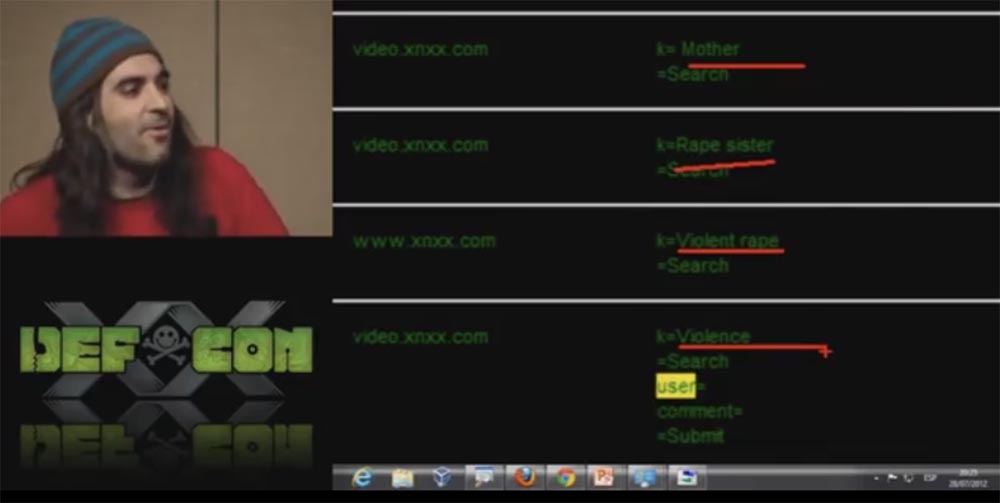
We, naturally, came across and psychopaths. This slide shows the control panel where you can see how the guy from the same IP address constantly searched video.xnxx.com for video materials on the topic “mother”, “rape of the sister”, “forced rape”, “violence” and the like . We decided to give his IP address to the local police, because this guy is obviously insane.
So, many people strive for anonymity on the Internet, so the first thing they do is check their anonymity. But the problem is that using a proxy, you are anonymous for the final page, but not for the proxy itself. For example, you claim that your IP address is in the US, we look at your real IP address and make sure that this is the case or not. No anonymity on the proxy server!
Another type of anonymous internet activity caught our attention when we discovered a person who made money from reading blog posts. This is such a business - you read blog posts from people around the world, and they pay you for it. Within a month, this man earned as much as $ 24, so this is also a good business. We called this phenomenon "Strange people in a strange world."
Many users of our proxy server were engaged in hacking and corruption of these websites. One of these users caught our attention - on the control panel you see local files intercepted by us from a hacked site, this hacker used a malicious WebShell script to crack, using which you can distort JavaScript.
The next slide shows hacking, we looked at its implementation in real time. Below you see the attacker's email address.
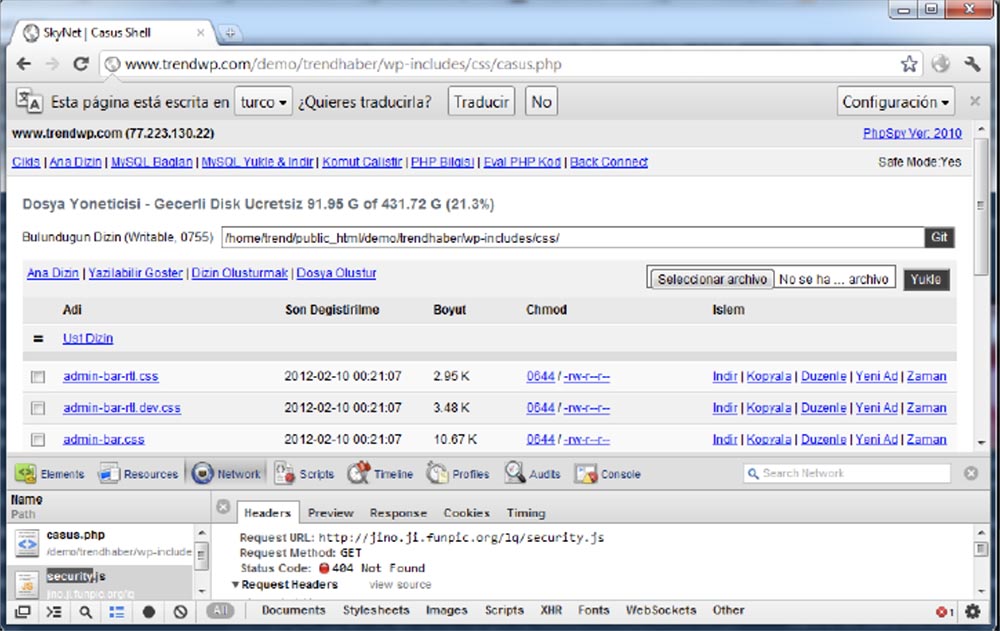
When we studied how this site was hacked, we realized that the hacker used an infected WebShell that loads a JavaScript file, which, in turn, reported the URL of this WebShell. This JavaScript file was also infected by our proxy server and allowed us to find out where this WebShell is located. It turns out that the hacker himself was hacked by our hacking.
The next slide shows a WebShell request that calls JavaScript.
As you remember, interesting in our system was that even after disconnecting the client from our proxy server, it still remained infected with our malicious JavaScript. Until now, everything was obtained by passive observation of the navigation, so we thought about whether it is possible to infect an Intranet, that is, an internal network that was not viewed through our proxy server.
Therefore, one of the points that attracted our attention when reviewing the collected data was the ability to search for information about machines that were not published on the Internet, that is, about applications that are used within the Intranet, as can be seen from the following data in the internal ERP system .

We followed a guy from Mexico, he searched for porn on the Internet. He disconnected from the proxy server, but remained infected, so you see here the internal server that we tried to join. There is a lot of data, passwords, usernames. This makes it clear that the use of remote JavaScript files on the Intranet may be undesirable, and opens the door to potential attacks of this kind.
Seeing this, we thought that it would be easy to prepare a targeted attack on any application on the Intranet or the Internet, analyzing previously loaded JavaScript files and forcing clients to download these files from any domain, because we installed forced caching.
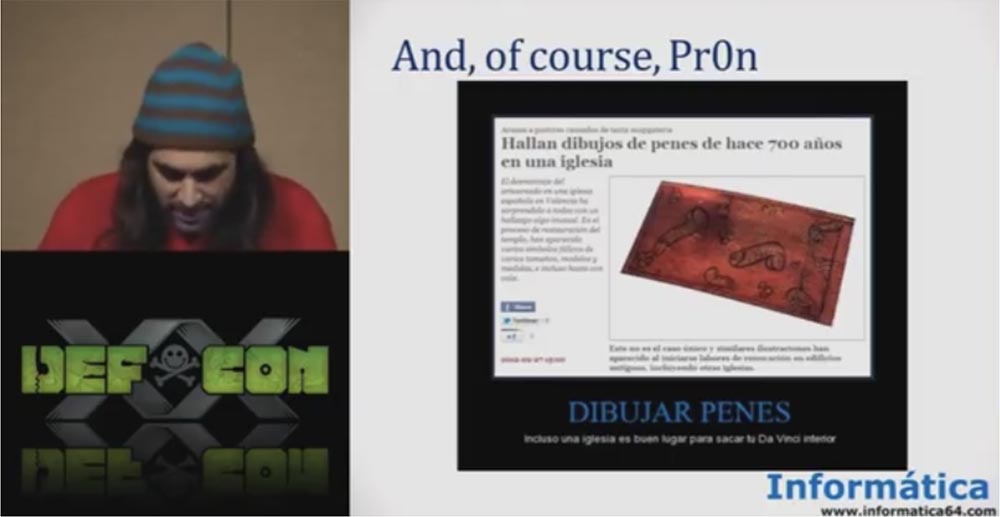
And of course, the users of our proxy server were addicted to pornography. There was a lot of porn here, porn is real business. We even read an interesting story about how “frank” drawings made by a monk in 700 AD were discovered in a Catholic church. We collected URLs and collected an extensive collection of usernames and passwords, and of course, we will sell them on the Internet (just kidding).
But most of all our attention was attracted by the rape chat on the Internet. We have always believed that it is very difficult to rape someone on the Internet, but it turned out that this is not the case.
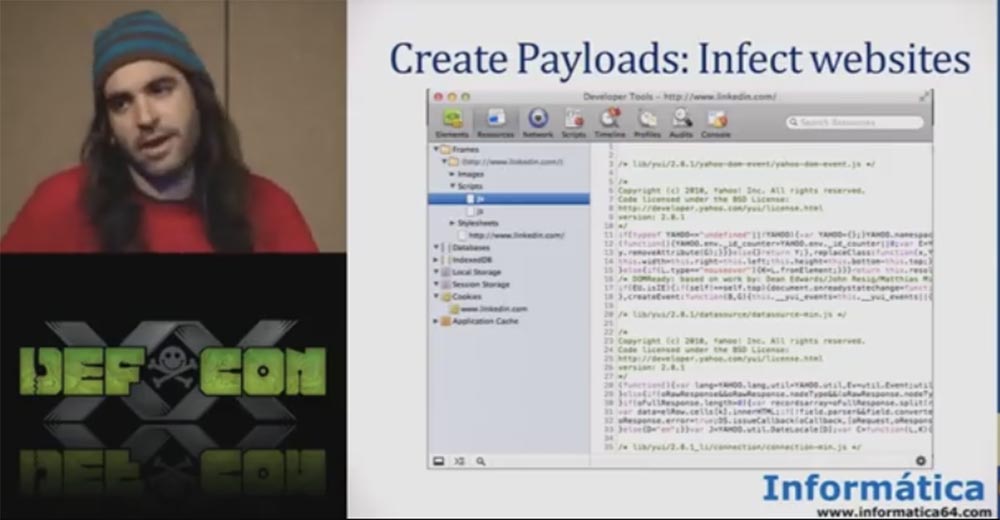
So we created a javascript file that infected websites. We created a "payload." To prepare a targeted attack on a specific site, i.e., to ensure that a user who is part of a botnet gets infected after visiting a specific site, you need to know which JavaScript files are uploaded to this site. To do this, you can use the network inspection in Google Chrome or Firefox Firebug and select the file that you want to infect.
Of course, if you connect to the network via a proxy server, you will not connect to the banking system, or to your social network profile, Intranet or your personal site, but if you do not clear the cache, then you are in the hands of those who made you download a malicious javascript file. And if this file is located on the page that you are going to open after visiting the proxy server, you will be hacked.
The next slide shows the code on the website of the social network website linkedin.com, where you can see some scripts that are loaded into Java, so if you use a proxy server, then we can create a special payload, download these JavaScript files. Then these files will be infected, and as soon as you disconnect from the proxy and connect to linkedin.com, the payload will be executed.
This is very simple, so we can create targeted attacks on several websites to collect passwords of people who used our proxy server before starting to use the normal, not anonymous Internet.
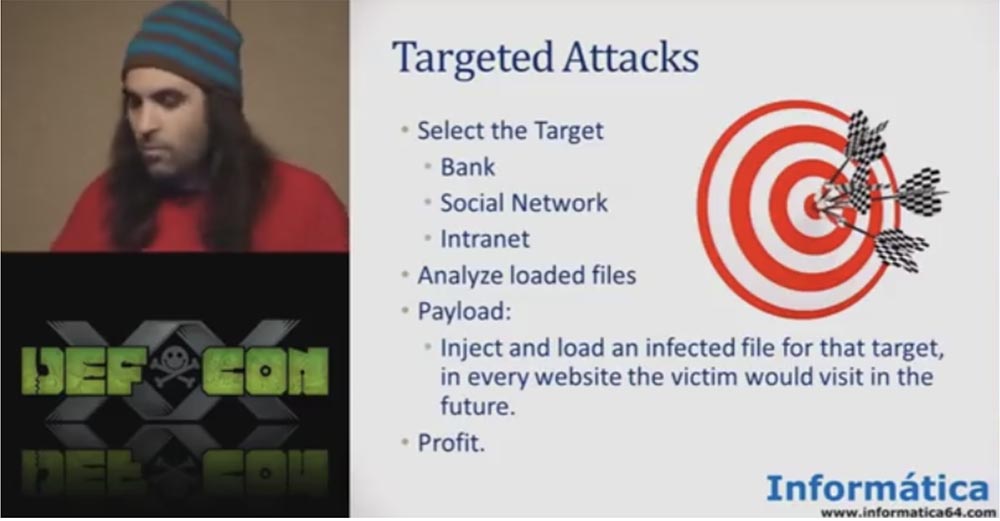
To do this, you first need to select a target: a bank, a social network, an Intranet, analyze the files uploaded to the site and launch the “payload”. That is, infect and download the infected file for the selected target, and it will be on every site that the victim will visit in the future.
Now I want to show you how we got into the banking system and show how our control panel looks like. Of course, we turned off our proxy server long ago, but for BlackHat and DefCon conferences, I created a new control panel. I did not host this proxy server on the Internet. But after my report on BlackHat, I don’t know why, someone posted it on the Internet (laughter in the audience).
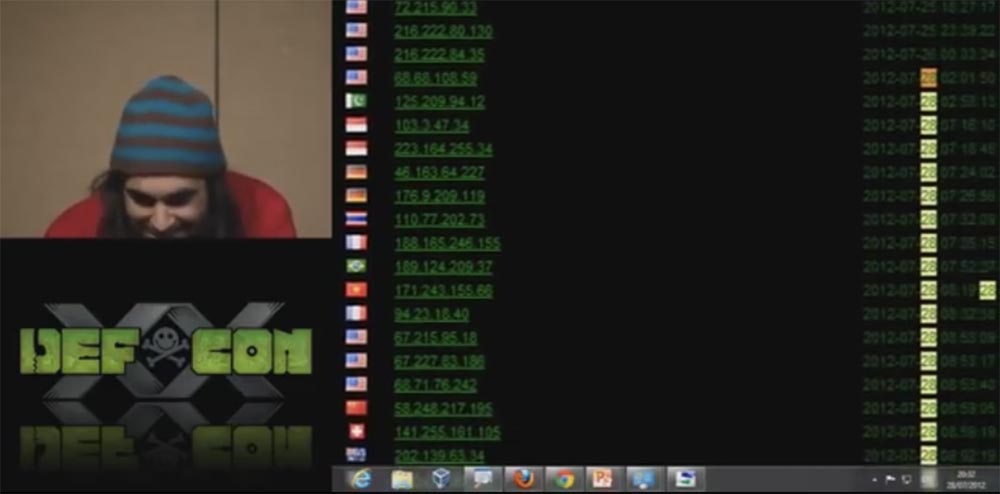
So, we configured this proxy server only for 10 parallel connections, and right now, this morning, I’m ready to show you all the bots, all our zombies for today, July 28th. You see here a large number of bots from different countries, USA, Brazil and so on.
We are collecting a lot of information from them right now, but we don’t use it, we don’t publish these IP addresses, trust me.
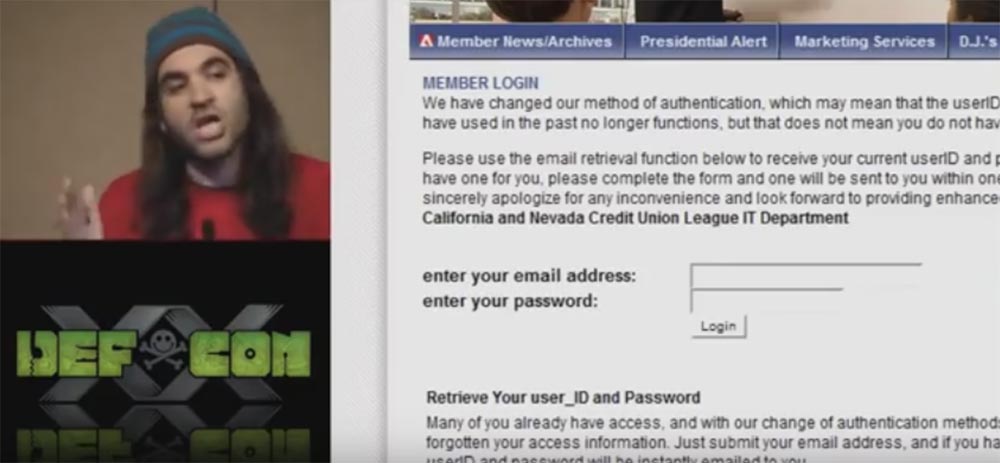
So, I want to show you penetration into the banking system. Now I will show you this website. This is the United Credit League of California. As you can see, this site is great for attacks, because it is an HTTP web site.

Here you see the user login form where you need to enter your email address and password. Since we can very easily insert our infected JavaScript file into the HTTP site, I “hooked” the form and pulled out user names and passwords from this site.
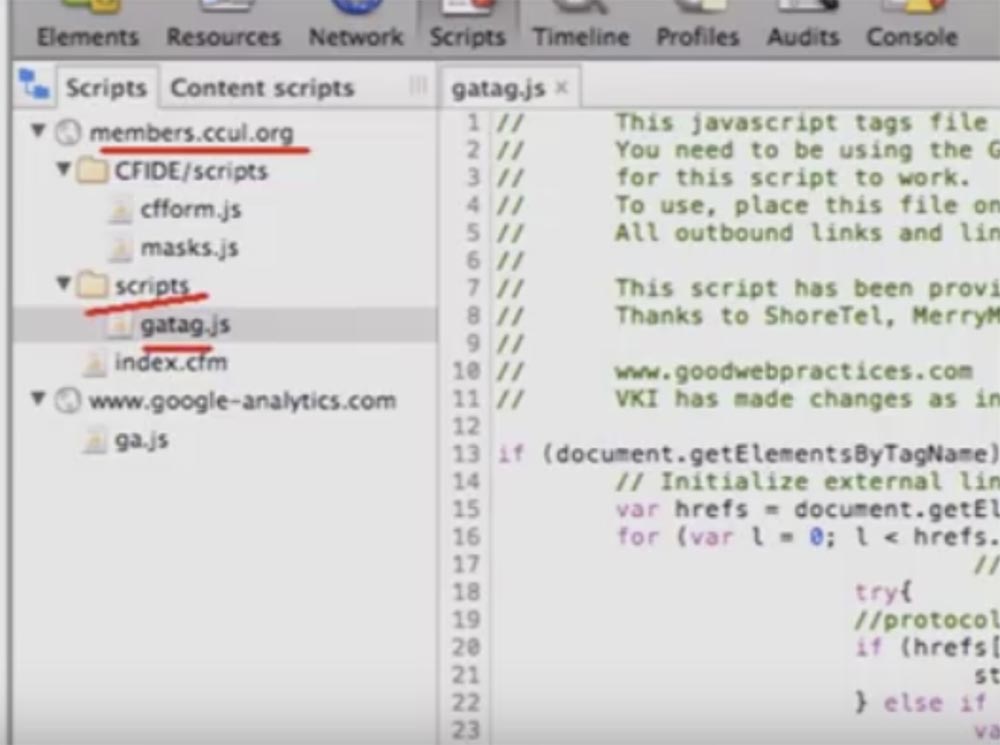
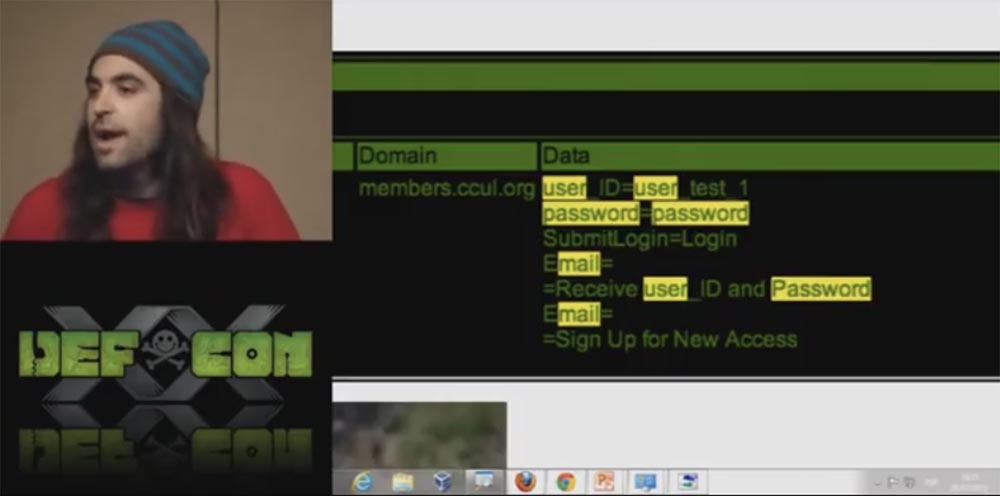
The only thing we needed to do in the control panel of our proxy server was to analyze the target and select one file. In our example, this is the members.ccul.org page and the gatag.js script file.
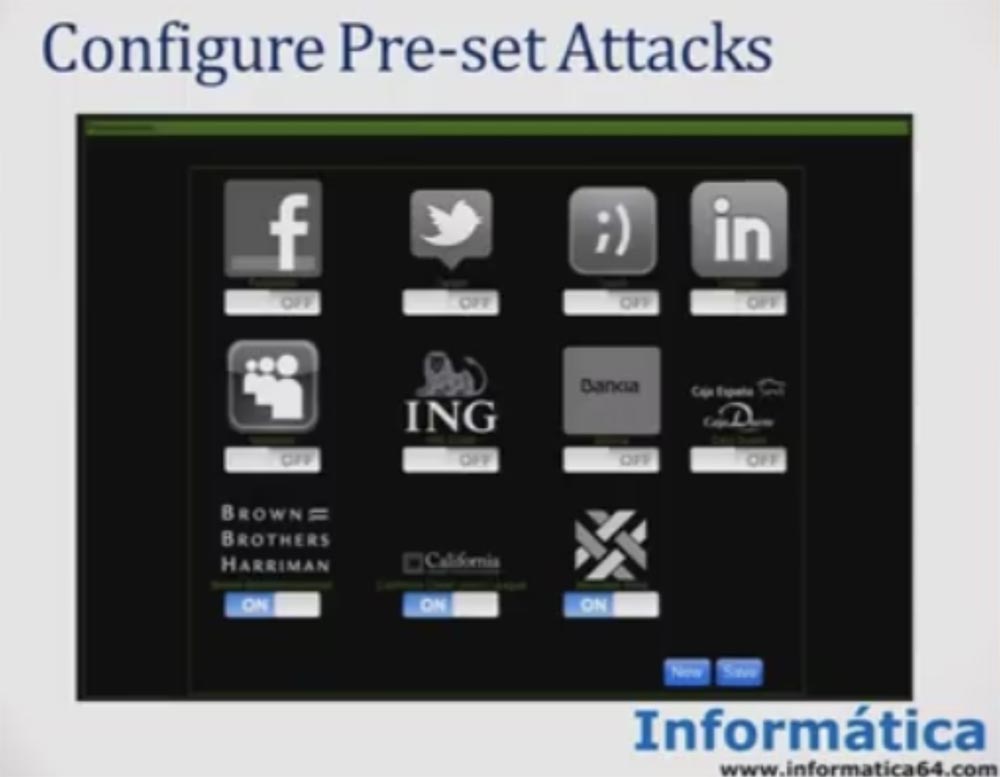
Then I created a "payload" in our control panel and created a preset for the site that interests us.
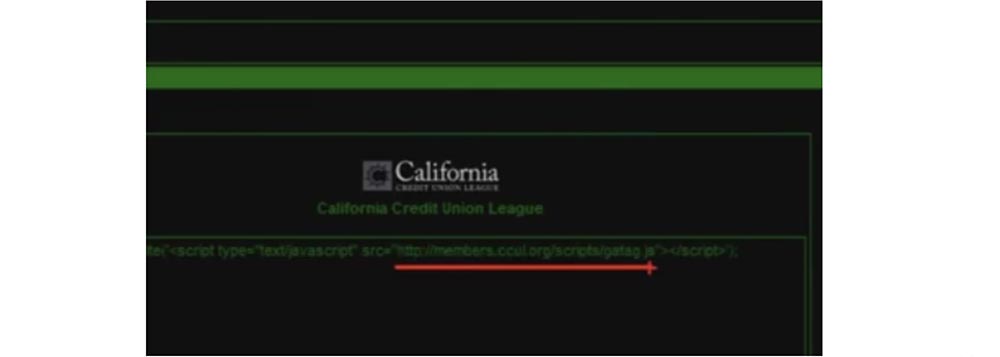
On the next slide, you can see how the target site looks in the control panel - here is the command to perform the function on the members.ccul.org address for the gatag.js script, which will launch our payload.
Thus, the guy who uses our proxy server to view porn will load this file into the cache. He can watch porn, hack sites, do anything, and at the same time he will download this JavaScript file for a targeted attack.
After he disconnects from our proxy server and selects the item “Do not use a proxy server” in the network settings of your computer, our file will still remain in the cache of its browser, because it has already been loaded before and has no expiration date.
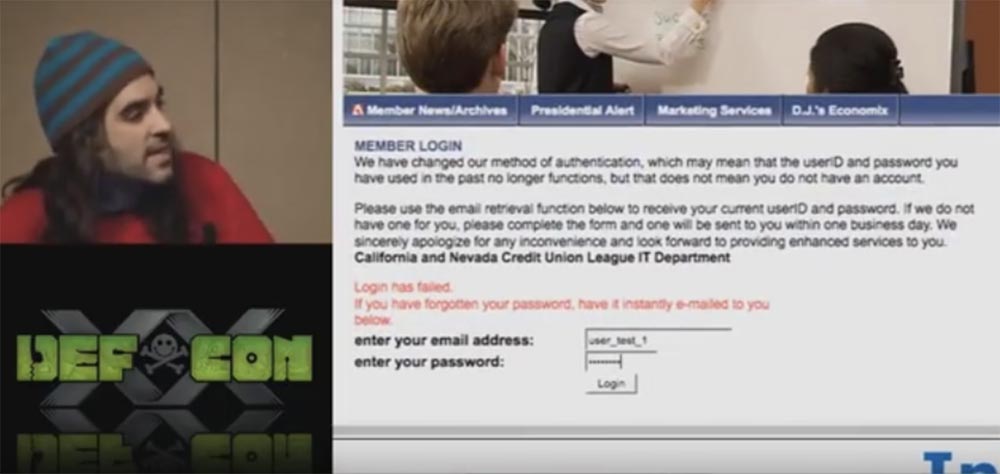
After this guy connects to the target site and enters user data, we will “pick up” this form and display all this data in the control panel of our proxy server. It is very simple.
And now I will give some thoughts about the benefits of a JavaScript botnet:
And now the question is: how many of you think that bad guys like government intelligence agencies are doing the same thing on the Internet? The question is, which of you thinks that only one proxy server guarantees Internet security? Nobody thinks so, right?
So, relying on the proxy server to ensure your anonymity on the Internet is a bad idea. But thousands and thousands of sites tell people - if you want anonymity on the Internet, use a proxy server. And this problem has existed for a very, very long time. So, remember - do not use proxy servers! Do not believe that they ensure your anonymity.
Here are some ways to protect yourself.

Remember the “man in the middle” scheme, because someone can configure your browser for your needs through a proxy server. Think twice before using a proxy.
Think about whether you trust the TOR network too much. Because lately we have heard a lot about fake TOR networks and hacks in this network.
After you use an anonymous network or proxy server, clear all information in your browser from sites, clear the cache and delete cookies.
Remember that VPN is not a panacea, because in this case, many people connect to this network, then they use a proxy server, and therefore infection of your virtual network can happen very easily, as there is a free exchange of malicious files and traffic.
Remember again - the cache is not your friend, so treat it accordingly.
This is the end of today's conversation, and I want to tell you that tomorrow at 17-00 I will be speaking on SkyTalks with the theme “Pull the Fork” Domain: Bureaucratic DOS ”. Thank you very much!

Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
This guy kept all the chats with those who are interested in the profile of this girl. This slide shows my favorite chat, kkbill1980 is the one who pretends to be a girl, and fiat176punt is his victim. “Kkbill1980: hello, sweetie! - fiat176punto: hello, my sweet mouse! ”, And so on, very cheerful chat.

')
Further in the chat, they discuss the details of their love relationship, and the most interesting detail is 700 euros, which the victim must send to her “sweet mouse” as if to book a hotel during a fake girl’s trip to Germany.
And then the fan writes that this night he sent his beloved a “completely nude photo”, to which she replies: “Oh, baby, this is wonderful!”
The bottom line is that this scam guy talked to a lot of people at the same time with the help of fake girls profiles on dating sites and extorted money from his victims on one pretext or another. However, somewhere in the middle of the chat, this guy “punctured”, apparently confusing the open tabs, and began to write in German.
In his mailbox everything was perfectly systematized, and he kept all his chats in a special folder, with which he continued to work even now. We decided to find in the correspondence all the references to the men who were going to use Western Union to send money to their "lover", and found 158 such messages.

The next slide shows a sample of the correspondence of this girl and the victim. Photos are again mentioned here - the girl asks why the man did not send her the promised “naked” photos. And he answers that he does not know why, but the bank manager told him that it was impossible to send money to the address indicated, so let the girl give him some other address.

This is because the profile of the girl was given a fake address, which, apparently, did not suit the bank clerk. To which the fake girl angrily replies: “fuck, stop playing games with me! I gave you the correct address, so take the money from the bank and send it to me through Western Union, otherwise forget about everything and stop playing games with my heart! ”
In general, you can imagine what it was for the correspondence. And this scheme worked, because for sending money through Western Union it is enough to specify only the city and the name of the recipient of the transfer, and then tell him the secret code.
The next case, which interested us, was a crook associated with dogs. We wondered what he did with dogs if he needed an anonymous proxy server for his work?

We, as usual, decided to use his username and password to get into his inbox. And there we found something heavy, so if you love animals, do not look at the next picture. On the next slide, we even posted the following warning: “Attention! This picture can hurt your feelings! ” But, actually, the picture itself.

He placed this fake Yorkshire terrier, fake, because he placed the same dog for sale all over the world, so this is the most profitable york on earth. He put this picture and made money on it, as the cheapness of the purebred dog tempted everyone and they made an advance payment.
We, naturally, came across and psychopaths. This slide shows the control panel where you can see how the guy from the same IP address constantly searched video.xnxx.com for video materials on the topic “mother”, “rape of the sister”, “forced rape”, “violence” and the like . We decided to give his IP address to the local police, because this guy is obviously insane.

So, many people strive for anonymity on the Internet, so the first thing they do is check their anonymity. But the problem is that using a proxy, you are anonymous for the final page, but not for the proxy itself. For example, you claim that your IP address is in the US, we look at your real IP address and make sure that this is the case or not. No anonymity on the proxy server!
Another type of anonymous internet activity caught our attention when we discovered a person who made money from reading blog posts. This is such a business - you read blog posts from people around the world, and they pay you for it. Within a month, this man earned as much as $ 24, so this is also a good business. We called this phenomenon "Strange people in a strange world."
Many users of our proxy server were engaged in hacking and corruption of these websites. One of these users caught our attention - on the control panel you see local files intercepted by us from a hacked site, this hacker used a malicious WebShell script to crack, using which you can distort JavaScript.
The next slide shows hacking, we looked at its implementation in real time. Below you see the attacker's email address.
When we studied how this site was hacked, we realized that the hacker used an infected WebShell that loads a JavaScript file, which, in turn, reported the URL of this WebShell. This JavaScript file was also infected by our proxy server and allowed us to find out where this WebShell is located. It turns out that the hacker himself was hacked by our hacking.

The next slide shows a WebShell request that calls JavaScript.

As you remember, interesting in our system was that even after disconnecting the client from our proxy server, it still remained infected with our malicious JavaScript. Until now, everything was obtained by passive observation of the navigation, so we thought about whether it is possible to infect an Intranet, that is, an internal network that was not viewed through our proxy server.
Therefore, one of the points that attracted our attention when reviewing the collected data was the ability to search for information about machines that were not published on the Internet, that is, about applications that are used within the Intranet, as can be seen from the following data in the internal ERP system .

We followed a guy from Mexico, he searched for porn on the Internet. He disconnected from the proxy server, but remained infected, so you see here the internal server that we tried to join. There is a lot of data, passwords, usernames. This makes it clear that the use of remote JavaScript files on the Intranet may be undesirable, and opens the door to potential attacks of this kind.
Seeing this, we thought that it would be easy to prepare a targeted attack on any application on the Intranet or the Internet, analyzing previously loaded JavaScript files and forcing clients to download these files from any domain, because we installed forced caching.

And of course, the users of our proxy server were addicted to pornography. There was a lot of porn here, porn is real business. We even read an interesting story about how “frank” drawings made by a monk in 700 AD were discovered in a Catholic church. We collected URLs and collected an extensive collection of usernames and passwords, and of course, we will sell them on the Internet (just kidding).
But most of all our attention was attracted by the rape chat on the Internet. We have always believed that it is very difficult to rape someone on the Internet, but it turned out that this is not the case.
So we created a javascript file that infected websites. We created a "payload." To prepare a targeted attack on a specific site, i.e., to ensure that a user who is part of a botnet gets infected after visiting a specific site, you need to know which JavaScript files are uploaded to this site. To do this, you can use the network inspection in Google Chrome or Firefox Firebug and select the file that you want to infect.

Of course, if you connect to the network via a proxy server, you will not connect to the banking system, or to your social network profile, Intranet or your personal site, but if you do not clear the cache, then you are in the hands of those who made you download a malicious javascript file. And if this file is located on the page that you are going to open after visiting the proxy server, you will be hacked.
The next slide shows the code on the website of the social network website linkedin.com, where you can see some scripts that are loaded into Java, so if you use a proxy server, then we can create a special payload, download these JavaScript files. Then these files will be infected, and as soon as you disconnect from the proxy and connect to linkedin.com, the payload will be executed.
This is very simple, so we can create targeted attacks on several websites to collect passwords of people who used our proxy server before starting to use the normal, not anonymous Internet.

To do this, you first need to select a target: a bank, a social network, an Intranet, analyze the files uploaded to the site and launch the “payload”. That is, infect and download the infected file for the selected target, and it will be on every site that the victim will visit in the future.
Now I want to show you how we got into the banking system and show how our control panel looks like. Of course, we turned off our proxy server long ago, but for BlackHat and DefCon conferences, I created a new control panel. I did not host this proxy server on the Internet. But after my report on BlackHat, I don’t know why, someone posted it on the Internet (laughter in the audience).
So, we configured this proxy server only for 10 parallel connections, and right now, this morning, I’m ready to show you all the bots, all our zombies for today, July 28th. You see here a large number of bots from different countries, USA, Brazil and so on.

We are collecting a lot of information from them right now, but we don’t use it, we don’t publish these IP addresses, trust me.
So, I want to show you penetration into the banking system. Now I will show you this website. This is the United Credit League of California. As you can see, this site is great for attacks, because it is an HTTP web site.

Here you see the user login form where you need to enter your email address and password. Since we can very easily insert our infected JavaScript file into the HTTP site, I “hooked” the form and pulled out user names and passwords from this site.

The only thing we needed to do in the control panel of our proxy server was to analyze the target and select one file. In our example, this is the members.ccul.org page and the gatag.js script file.

Then I created a "payload" in our control panel and created a preset for the site that interests us.

On the next slide, you can see how the target site looks in the control panel - here is the command to perform the function on the members.ccul.org address for the gatag.js script, which will launch our payload.

Thus, the guy who uses our proxy server to view porn will load this file into the cache. He can watch porn, hack sites, do anything, and at the same time he will download this JavaScript file for a targeted attack.
After he disconnects from our proxy server and selects the item “Do not use a proxy server” in the network settings of your computer, our file will still remain in the cache of its browser, because it has already been loaded before and has no expiration date.

After this guy connects to the target site and enters user data, we will “pick up” this form and display all this data in the control panel of our proxy server. It is very simple.

And now I will give some thoughts about the benefits of a JavaScript botnet:
- we didn’t care about previously cached objects like E-tag or expiration time, so we didn’t fight them;
- we didn’t care about secure HTTPS connections because we didn’t want to raise any alarms or fire ’authentication certificates. In addition, Moxie was too busy for us to consult him about the use of these certificates (the speaker refers to Moxie Marlinspike, who spoke at DefCon conferences on the subject of falsifying SSL certificates from CA authorization centers);
- it took us only one day to configure our proxy server so that it finds IP addresses, creates JavaScript and collects all the information we need
And now the question is: how many of you think that bad guys like government intelligence agencies are doing the same thing on the Internet? The question is, which of you thinks that only one proxy server guarantees Internet security? Nobody thinks so, right?
So, relying on the proxy server to ensure your anonymity on the Internet is a bad idea. But thousands and thousands of sites tell people - if you want anonymity on the Internet, use a proxy server. And this problem has existed for a very, very long time. So, remember - do not use proxy servers! Do not believe that they ensure your anonymity.
Here are some ways to protect yourself.

Remember the “man in the middle” scheme, because someone can configure your browser for your needs through a proxy server. Think twice before using a proxy.
Think about whether you trust the TOR network too much. Because lately we have heard a lot about fake TOR networks and hacks in this network.
After you use an anonymous network or proxy server, clear all information in your browser from sites, clear the cache and delete cookies.
Remember that VPN is not a panacea, because in this case, many people connect to this network, then they use a proxy server, and therefore infection of your virtual network can happen very easily, as there is a free exchange of malicious files and traffic.
Remember again - the cache is not your friend, so treat it accordingly.
This is the end of today's conversation, and I want to tell you that tomorrow at 17-00 I will be speaking on SkyTalks with the theme “Pull the Fork” Domain: Bureaucratic DOS ”. Thank you very much!

Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/425791/
All Articles