Intel ME Manufacturing Mode - hidden threat or what is behind CVE-2018-4251 vulnerability in MacBook
The principle of “ security through obscurity ” has been criticized by experts for years, but this does not prevent large electronics manufacturers, under the pretext of protecting intellectual property, from signing non-disclosure agreements to obtain technical documentation. The situation is worsening due to the increasing complexity of microcircuits and the integration of various proprietary firmware into them. This in fact makes it impossible to analyze such platforms for independent researchers, which puts at risk both ordinary users and equipment manufacturers.
An example is the Intel Management Engine (Intel ME) technology, as well as its versions for server (Intel SPS) and mobile (Intel TXE) platforms (for more information about this technology, see [5] , [6] . In this article we will tell like using undocumented commands (if the term “documented” is generally applicable to Intel ME), you can overwrite the SPI flash memory and implement the worst scenario - local exploitation of the vulnerability in ME (INTEL-SA-00086). The undocumented mode of operation of Intel ME was the root of this problem - Manufacturing Mode.
')
What is Manufacturing Mode
Intel ME Manufacturing Mode - service mode of operation, designed to configure, configure and test the final platform at the production stage; it must be disabled before the equipment is on sale and shipped to the user. Neither this mode nor its potential risks are described in the Intel public documentation. A regular user does not have the ability to turn it off independently, since the utility for managing it from the Intel ME System Tools package is not officially available. Note that no software protection is able to protect the user if this mode is turned on, or at least notify him about it. Even the Chipsec [2] utility, which is specifically designed to detect chipset and processor configuration errors at the UEFI firmware level (in particular, incorrect configuration of access rights to SPI flash regions), does not know anything about Intel Manufacturing Mode.
This mode allows you to set critical platform parameters stored in single write memory (FUSES). An example of such parameters that are “sewn up” in FUSES are the BootGuard parameters (mode, policies, digital signature key checksum for ACM and UEFI modules). Some of them are called FPF (Field Programmable Fuses). A list of FPFs that can be written to FUSES (incomplete, in fact, a number of FPFs cannot be specified directly) can be obtained through the FPT (Flash Programming Tool) utility from the Intel ME System Tools package.
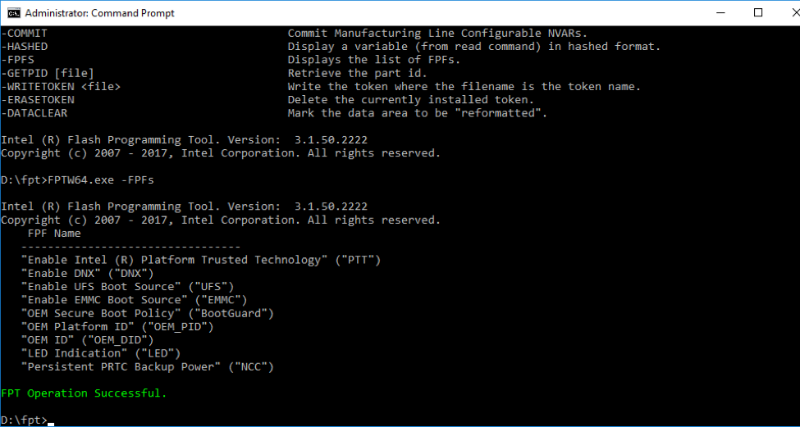
Figure 1. Result of the work of the –FPFs option of the FPT utility
It should be noted that FPFs account for only a fraction of the total FUSE array, and most of this memory is used by Intel itself for storing a variety of platform parameters. For example, part of the space of this array is called IP Fuses and is intended for storing the configuration parameters of individual hardware modules (Intelligent Property). Thus, a special DFx Aggregator device stores at FUSE whether the platform is serial or test.
In addition to FPF, in the Manufacturing Mode, the hardware manufacturer has the ability to set the parameters of the Intel ME firmware, which are stored in the internal file system of the firmware - MFS, on the SPI flash media. These parameters can be changed if SPI flash is reprogrammed. They are called CVARs (Configurable NVARs, Named Variables).
The installation of CVARs is the responsibility of the Intel ME firmware module - mca_server. MCA is the abbreviation of the Manufacture-Line Configuration Architecture, a generic name for the platform configuration process during production. CVARs, like FPF, can be specified and read using FPT.
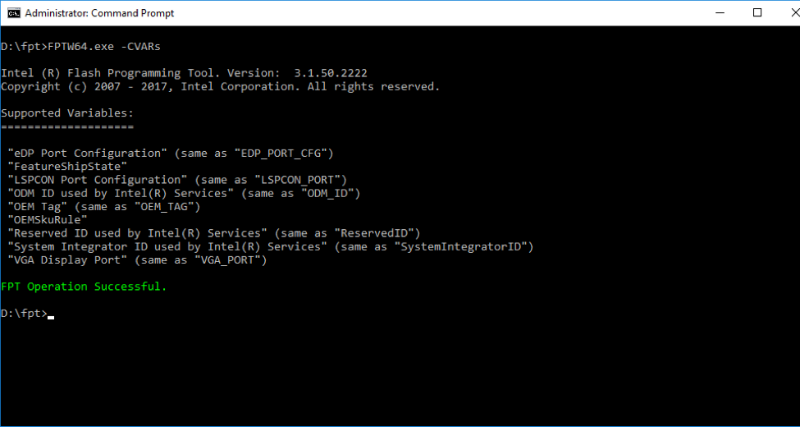
Figure 2. List of CVARs displayed by the FPT utility for the Broxton P platform
The CVARs variable list depends on the platform and version of the Intel ME firmware. For chipsets that support Intel AMT, one of these variables is the MEBx login password (ME BIOS Extension).
Installing FPFs and virtually all CVARs variables is possible only if the Intel ME firmware operates in Manufacturing Mode. The FPFs installation process itself is divided into two stages: setting the FPFs values (which are stored in temporary memory) and transferring the FPFs values to the array of fusions. In this case, the first stage is possible only in Manufaturing Mode, and the actual “burning” occurs automatically after exiting the Manufacturing Mode, if during operation in this mode the manufacturer specified FPF values and the corresponding range in the array of fusions has never been recorded yet. Thus, if the system functions in the Manufacturing Mode, the FPF variables are most likely not initialized.
The disablement sign of Manufacturing Mode is stored in the / home / mca / eom file on MFS, so when overwriting SPI flash firmware with the base file system (for more details in [9] ), the platform has the ability to function again in the Manufacturing Mode (but it will not work to overwrite FUSES) .
OEM public key
Thus, the procedure for configuring Intel platforms is quite complicated and consists of several stages. If the manufacturer of the equipment has broken or changed the sequence, then the platform is at serious risk. Even if the Manufacturing Mode is complete, the manufacturer could not write FUSES, which would allow an attacker to do it for him, writing down his values instead of the key for signing the start code of the BootGuard (ACM) and UEFI modules and thus allowing the platform to boot only with its malicious code, and full time. This will lead to irretrievable loss of equipment, since the fraudulent key will be stored in permanent memory forever (details of this attack can be found in the study of Safeguarding rootkits: Intel BootGuard [8] by Alexander Yermolov).
In the new systems (Apollo Lake, Gemini Lake, Cannon Point), FPF stores not only the key for BootGuard, but also the OEM public key (or rather, the SHA-256 from the RSA OEM public key), on which several ME protection mechanisms rely at once. For example, in a special section SPI flash, called the Signed Master Image Profile (SMIP), stores are set by the manufacturer PCH Straps (hardware configuration PCH). This section is signed on the key, SHA-256 from which is placed in a special file on SPI flash. This file is called oem.key, located in the FTPR section and contains various public keys supplied by the OEM to sign a wide variety of data. Here is a complete list of data sets that are signed by the manufacturer, each on a unique key, for the Cannon Point platform:
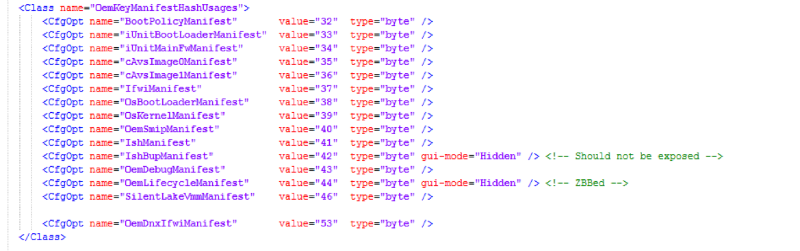
Figure 3. List of OEM Data Signed by the CNP Platform
The oem.key file itself is signed by the OEM shared root key, the hash sum of which should be written to FPFs.
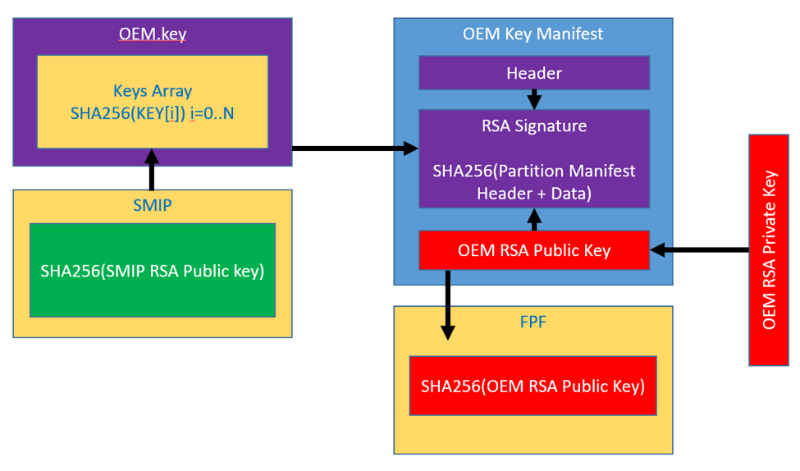
Figure 4. OEM Signing
Bypassing write blocking in the ME region
Until recently (before Intel Apollo Lake), Intel ME firmware was located in a separate SPI-region, which had independent access rights for CPU, GBE and ME. Thus, with the correct configuration of access attributes from the CPU (main system), it was impossible to neither read nor write ME firmware. However, modern Intel chipset SPI controllers have a special Master Grant mechanism. This technology assigns to each SPI master a strictly defined part of the SPI flash, this master is the owner of its region, regardless of the access rights specified in the SPI descriptor. Each master has the opportunity to provide access (for reading or writing) to his (and only his) region to another master, to whom he wishes.

Figure 5. An excerpt of Intel documentation describing the SPI Master Grant.
Thus, even if a ban on access to the SPI region of the ME from the host side is registered in the SPI descriptor, the ME can still provide access to its data. In our opinion, this is done in order to update the Intel ME firmware bypassing the standard algorithm.
Host ME Region Flash Protection Override
The Intel ME firmware has a special HECI command that allows you to open the write access to the ME-region SPI from the CPU. It is called HMR FPO (Host ME Region Flash Protection Override). In one of our previous studies, we described this team in detail [5]. She has several features.
After receiving the HMR FPO command, the firmware will open access to its region only after a reboot. The ME itself also provides protection: the command is perceived only during the execution period of the UEFI BIOS, up to the so-called End of Post moment (EOP). EOP is another HECI command that the UEFI BIOS sends before it transfers control to the operating system (ExitBootServices). In some BIOS Setup, you can find an option that ensures that the HMRFPO command is sent to EOP.

Figure 6. Opening the ME-region in the BIOS
After receiving the EOP, the ME firmware ignores the HMR FPO, returning the corresponding status. But this happens only after the completion of the Manufacturing Mode . Thus, ME firmware in Manufacturing Mode accepts HMR FPO at any time, regardless of the End of Post . If the manufacturer did not close the Manufacturing Mode, the attacker (formally speaking, administrator rights are required, but even the OS kernel cannot overwrite the ME firmware initially) can change the ME firmware at any time. At this stage, the attacker can overwrite the image of ME, for example, to exploit the INTEL-SA-00086 vulnerability. In this case, it is necessary to reboot, but this is not a hindrance on almost all platforms except the MacBook. It is on Apple computers that there is an additional check in UEFI, which is carried out at the time of launch and blocks the launch of the system if the ME region is opened using HMRFPO. However, as we will show later, this protection mechanism is overcome if ME firmware works in Manufacturing Mode.
Reboot ME without rebooting the main CPU
In modern computers there are several options for restarting the platform. Of these, documented: global reboot and reboot only the main CPU (without rebooting the ME). However, if there is a way to reboot the ME without rebooting the main CPU (after also executing the HMRFPO command), access to the region will open and the main system will continue to function.

Figure 7. Reboot Type Management
Examining the internal ME firmware modules, we found that there is a HECI command ( “80 06 00 07 00 00 0b 00 00 00 03 00” , for more information on sending commands, see [ 5 ]) to reboot only (!) The Intel ME core, which in Manufacturing Mode can also be sent at any time, even after EOP.
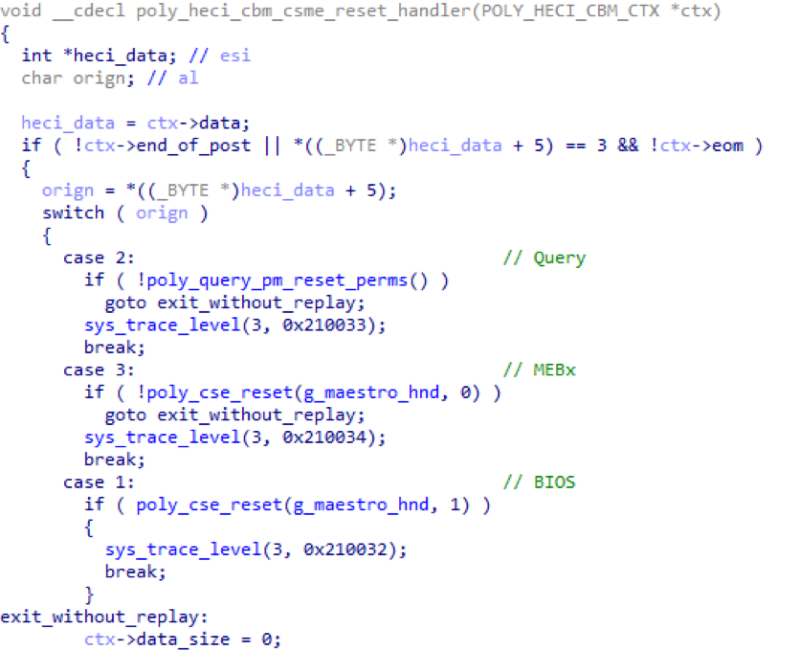
Figure 8. Listing of the disassembler of the function that performs the processing of HECI-commands to restart ME
Thus, the attacker, sending these two HECI-commands, opens the ME-region and can write any data there, without reloading the platform . At the same time, it does not matter what the SPI descriptor contains, that is, the correct protection attributes of the SPI regions do not protect the ME firmware from being changed if the system is operating in the Manufacturing Mode.
Practical case: CVE-2018-4251 vulnerability
We analyzed several platforms from different manufacturers. Among them were Lenovo laptops and Apple MacBook Pro. In the studied computers from the Yoga and ThinkPad line, we did not find any problems related to the Manufacturing Mode, but Apple’s laptops based on Intel chipsets function in Manufacturing Mode . After this information was sent to Apple, this error (CVE-2018-4251) was fixed in the macOS High Sierra 10.13.5 OS update.
Local operation of INTEL-SA-00086
So, using the CVE-2018-4251 vulnerability, an attacker can write old ME firmware versions containing the INTEL-SA-00086 vulnerability, and at the same time, he does not need any SPI programmer or access to the HDA_SDO jumper (that is, physical access). Thus, the most dangerous - local - vector of this vulnerability is implemented (execution of arbitrary code in ME firmware). It is noteworthy that in the explanations to the security bulletin INTEL-SA-00086, Intel does not mention open Manufacturing Mode as a means to exploit this vulnerability locally, without physical access, but only indicates that local operation is possible only if SPI regions are configured incorrectly. that is not true. To protect users, we decided to describe how to check the availability of the Manufacturing Mode and how to disable it.
How to protect
The package of system utilities for developers of equipment based on chipsets and Intel processors (Intel System Tools) includes the MEInfo utility (TXEInfo, SPSInfo for mobile and server platforms, respectively), which is designed to obtain advanced diagnostic information about the current firmware management engine and the whole platform as a whole. We demonstrated this utility in one of our previous studies on the disconnection of ME and the undocumented HAP (High Assurance Platform) mode [ 6 ]. This utility, invoked with the –FWSTS flag, gives a detailed description of the status HECI registers and reports the status of the Manufacturing Mode (the 4th bit of the FWSTS status register indicates that Manufacturing Mode is active).

Figure 9. Example of the MEInfo utility output
We also developed a program [ 7 ] that can be used to check the status of the Manufacturing Mode if the user does not have access to Intel ME System Tools for any reason.

Figure 10. Example of the mmdetect script
The question arises of how to complete the Manufacturing Mode on its own, if it turned out that the manufacturer did not. To complete the Manufacturing Mode, the FPT utility has a special option, –CLOSEMNF, which, in addition to its main purpose, also allows you to set the recommended access rights to the SPI flash regions in the descriptor.

Figure 11. The result of running the FTP utility with the –CLOSEMNF option
In this example, we used the NO option of the –CLOSEMNF option to not perform a platform reboot, which is done by default immediately after the completion of the Manufacturing Mode.
Conclusion
Our research shows that the problem of Manufacturing Mode firmware Intel ME exists and even such large manufacturers as Apple are able to make mistakes when configuring Intel platforms. Worst of all, there is no public information on this topic and the end users do not even know about such a serious problem that could lead to the loss of confidential information, the appearance of unrecoverable rootkits and the irretrievable removal of equipment.
In addition, we have suspicions that being able to reboot ME without rebooting the main CPU may lead to other security problems due to the out of sync BIOS / UEFI and ME states.
Authors: Mark Yermolov and Maxim Hot
[1] Intel Management Engine Critical Firmware Update, Intel-SA-00086
[2] GitHub - chipsec / chipsec: Platform Security Assessment Framework
[4] Fast, secure and flexible OpenSource firmware, Coreboot
[5] Mark Ermolov, Maxim Goryachy, PHDays VI, 2016
[6] Mark Ermolov, Maxim Goryachy, Disabling Intel ME 11 via undocumented mode, Positive Technologies' blog
[7] Intel ME Manufacturing Mode Detection Tools
[8] Alexander Ermolov, Safeguarding rootkits: Intel BootGuard
[9] Dmitry Sklyarov, Intel ME: Flash File System. Explained
Source: https://habr.com/ru/post/425105/
All Articles