Forensic resistance 1 or Last ActivityView. Data on user activity in Windows 10 and how to remove them
Good time reading, dear readers of Habr.
The prompting to research, published in this article, was the more and more popular word “fornsica” and the desire to understand the question - what data on the digital life of an ordinary user collects Windows 10, where it stores and how to make a button - “Delete all” (I would take it in parts, but I need to immediately (c) Ostap Bender).
And the emergence of this motivation was promoted by the fact that, as it turned out, the interest in the question "how to delete history", issued by the epic LastActivityView , still stirs the minds
')
at the same time, often on the forums the question remains unanswered. Fuel to the fire adds that the vanilla CCleaner in the case of LastActivityView does not help.
Those who are mostly interested in the practical side of the question, about the “Delete All” button, can immediately go to the end of the article - I suggest solutions there.
And in the article - I want to share the results of these studies with those who are interested in it. It will be about the data that is stored by Windows 10 locally and which can be easily and quickly accessed using the “free and publicly available means of forensica,” including the NirSoft utilities . Although it is not about them (why - see below).
I want to make a reservation right away - I am not a specialist in computer security or forensic analysis, I do not have any criminal experience or impulses, I swear to my mother that I cannot see the age of will.
This article discusses Windows 10. Other editions of Windows are, of course, also sinful in collecting and storing data, but they have registry keys, folders, services, etc. are different.
And here fornica
Why is it not about NirSoft
What data is stored Windows
Why does Windows collect data and what is fraught with their removal
Where is this data stored?
Since, in the end, they wipe something?
Sources
In the article, the question concerns the use of its methods and means to access private user data. And, due to their distribution and availability, it is likely - in vain, home-grown forzensik-kultshakerami, Trojan affairs masters and other amateurs calculate by IP or easy money, and just unfriendly curious, as for downloading, running and reading / saving data issued by the same LastActivityView, Nir Sofer does not need to be.
In the “introduction” I did not accidentally give a link to LastActivityView on the Soft Portal. There really is only a brief description of the functionality of this utility, but in Russian. And on off. Nir Sofer writes a page for his utilities, and he also speaks English. But, on the other hand, for almost every utility of it, there is a description of where it gets the data from. For LastActivityView at the very bottom, under the heading "How to delete the information displayed by LastActivityView".
It must be admitted that I myself have the same keen-eyed eye - once, like him, only a week later I noticed that "there is no wall at the barn." But, the truth is, this week was a little bit earlier than LastActivityView began to frighten users or, more likely, when they got to the Soft Portal and learned to be afraid of it themselves.
Although NirSoft utilities, along with SysInternals, IMHO is a sample of professionalism for a programmer and extremely convenient for administration. Yes, and to conduct investigations and they are often recommended. ProofExample: Hacker №229. Forensic and he is not the only one.
Although, I think, a similar direction of their use by itself occurred to those who somehow dealt with them.
Everything that is connected with access to files and folders and their location, using programs (including protable), and connecting storage devices (including encrypted file containers) is stored.
Yes, it is not in all cases, something is saved only under certain events, but something can be turned off, but it is better, nevertheless, to assume that everything is always. What connected, what folders-files opened, what programs used.
And from the fact that with Windows logs it is unpredictable what will be recorded there. Due, at least, to the fact that it strongly depends on the specific settings of a specific OS and each of its subsystems, and these logs are available for recording messages in them by third-party programs.
And where does "access" and "location"? A highly exaggerated example: a bank card number and its pin-code will remain in the file “D: \ MySuperSecretContact \ CardPin.docx”, will not be recorded in Windows, but the fact of access and the “talking” folder and file names, that for example, MS Office 2007 portable was used, as well as the date-time of at least the last (sometimes each) access / launch — fixed by Windows, and smeared with a thin layer throughout the system.
About some other data - you can read below in the text, under the heading "Other sources of information leaks known to me, but not falling under the subject of the article"
So, if they connected, started, opened something that I wouldn’t want to become the property of the general public, then it would not be bad for them to sweep away the traces.
An absolutely fair comment from Hanabishi - “But the topic of real logging is not touched at all ... nothing is mentioned concerning telemetry and Win10 in particular” - I apologize, I didn’t really describe that the article is about private data stored locally on users PC . Issues of surveillance, as well as issues of anonymity on the network, is still another, separate topic.
Most of the data Windows collects for the convenience of the user - for example, to speed up the launch of applications, to display folders in Explorer with the settings that the user specified, to display a list of previously opened files, etc. etc. To wipe only the data, without losing the amenities at the same time - will not work.
Also, part of the data is collected to assess the performance and condition of the computer and the OS (including failures and errors) by IT specialists and specialized software to solve the problems arising from the user. Without this data, it will be difficult to solve problems if they arise.
And all this is another reason to think about the question of when it is really necessary to erase the data, and when it is not worth it and it may not be necessary to erase it with an empty image every time the computer is turned on and off.
An absolutely fair comment from Hanabishi - “why clean the service logs, if you can simply disable these services?” I did not mention it. Can. As regular means, and dances with a tambourine. But this again means - once and for all to lose the fertilizers, which are our everything.
What will be to me from Vinda for large-scale cutting out of private data, including using the solution proposed here?
Epic fails should not happen, especially if you carefully read the description of each “cleaning” rule and, if anything, turn it off. But the new cap, with a new burqa, is also not expected.
After the “surveys” stated in the introduction and the reconciliation of the new reality with the surrounding reality, I got the impression that,apart from IBM-286, they had already managed to invent some basic “reserved places” that had not changed since XP, except that the location and format of some have changed. And something was added, but, it seems, a little. Therefore, I am therefore sure that I will not open the Americas, especially to specialists, but it may be that someone will be interested in this selection, in connection with the growing interest in anonymity and security.
I just want to warn you - this is far from everything, only the most basic and informative (in the sense of the description, not everything is erased in the proposed solution much more) and not deployed also by the “gallop on Europe”. For those to whom this topic is really interesting, at the end of this chapter - interesting materials known to me for independent study + a number of specific “reserved places” are given in the solutions for their cleanup.
The main, known to me, sources of information leakages about user activity
Windows logs: well, here without comments ... even completely fair.
There are a few more places in the registry and on the disc, but they are much less informative and not very interesting (see “solutions”, below). And there is a sea of other places, like the "* .log" files of various services, and even not always Microsoft. True, it is encouraging that CCleaner on steroids (see below) is overwritten by almost everything.
Other sources of information leaks are known to me, but not covered by the article for one reason or another. And here, too, it should be noted that almost everything is overwritten by CCleaner or there are other freeware utilities.
Materials on this topic, except for the “sources” at the end of the article.
I propose the following option for consideration and criticism: Bleed the CCleaner (which, I think, is more convenient for users and more correct, since it excludes the invention of the next bicycle) and
use the bat file to wipe windows logs.
Plus, below is its own solution, in the form of a bat-file, but, nevertheless, it is not advisable to use it even in my opinion (especially since it erases only the most basic and mainly for windows 10). Is that - I propose to read the comments on the code.
First, you need to download and run CCEnhancer , perform the "update" (according to the instructions on the page). Just be sure to select and click on this menu item (after closing the CCleaner, if it started):
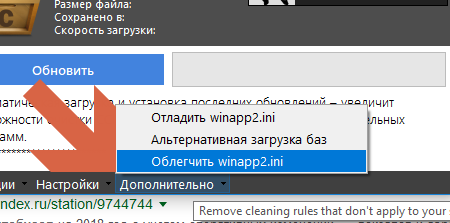
Otherwise, the winapp2.ini file will contain 100,500 rules that are extremely relevant for the general public, such as the cleaning rules for the Zaiki Spectrum emulator (maybe someone even remembers such a computer), but at the same time slowing down the CCleaner.
Then you need to go to the folder where CCleaner is installed. Find the winapp2.ini file there, congratulate it with relief and open it (for example, in nodepad ++).
Save file.
Just in case, before the first launch, you need to create a restore point.
You can additionally read a detailed and understandable description of all the basic rules of CCleaner and the consequences of their use here (Rus.)
Run the bat file. Wait until the work is finished.
Open CCleaner, go to it in the "Cleaning".
Perform cleaning.
Finals
After using the first or second option, you can run the NirSoft utilities in order to see if we have achieved the desired effect.
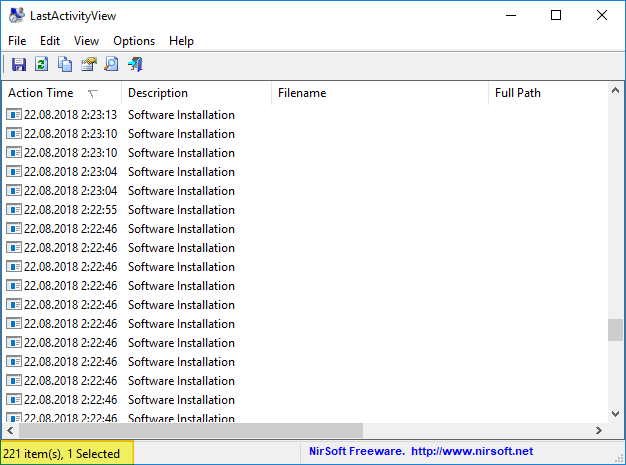
Profit ... Now, the main thing is to feed the dogs and not touch anything. And then she will again start writing opera ...
Possible scenarios for using bat and CCleaner solutions
By the way, why is Forensic resistance 1?
This will become clear if it ever comes to 2.
The prompting to research, published in this article, was the more and more popular word “fornsica” and the desire to understand the question - what data on the digital life of an ordinary user collects Windows 10, where it stores and how to make a button - “Delete all” (I would take it in parts, but I need to immediately (c) Ostap Bender).
And the emergence of this motivation was promoted by the fact that, as it turned out, the interest in the question "how to delete history", issued by the epic LastActivityView , still stirs the minds
')

at the same time, often on the forums the question remains unanswered. Fuel to the fire adds that the vanilla CCleaner in the case of LastActivityView does not help.
Those who are mostly interested in the practical side of the question, about the “Delete All” button, can immediately go to the end of the article - I suggest solutions there.
And in the article - I want to share the results of these studies with those who are interested in it. It will be about the data that is stored by Windows 10 locally and which can be easily and quickly accessed using the “free and publicly available means of forensica,” including the NirSoft utilities . Although it is not about them (why - see below).
I want to make a reservation right away - I am not a specialist in computer security or forensic analysis, I do not have any criminal experience or impulses, I swear to my mother that I cannot see the age of will.
Target operating system
This article discusses Windows 10. Other editions of Windows are, of course, also sinful in collecting and storing data, but they have registry keys, folders, services, etc. are different.
Content
And here fornica
Why is it not about NirSoft
What data is stored Windows
Why does Windows collect data and what is fraught with their removal
Where is this data stored?
Since, in the end, they wipe something?
Sources
And here fornica
In the article, the question concerns the use of its methods and means to access private user data. And, due to their distribution and availability, it is likely - in vain, home-grown forzensik-kultshakerami, Trojan affairs masters and other amateurs calculate by IP or easy money, and just unfriendly curious, as for downloading, running and reading / saving data issued by the same LastActivityView, Nir Sofer does not need to be.
Why is it not about NirSoft
In the “introduction” I did not accidentally give a link to LastActivityView on the Soft Portal. There really is only a brief description of the functionality of this utility, but in Russian. And on off. Nir Sofer writes a page for his utilities, and he also speaks English. But, on the other hand, for almost every utility of it, there is a description of where it gets the data from. For LastActivityView at the very bottom, under the heading "How to delete the information displayed by LastActivityView".
It must be admitted that I myself have the same keen-eyed eye - once, like him, only a week later I noticed that "there is no wall at the barn." But, the truth is, this week was a little bit earlier than LastActivityView began to frighten users or, more likely, when they got to the Soft Portal and learned to be afraid of it themselves.
Although NirSoft utilities, along with SysInternals, IMHO is a sample of professionalism for a programmer and extremely convenient for administration. Yes, and to conduct investigations and they are often recommended. ProofExample: Hacker №229. Forensic and he is not the only one.
Although, I think, a similar direction of their use by itself occurred to those who somehow dealt with them.
And for those who did not have, but became interested
In order not to download them at retail - you can download in bulk with the bonus in the form of the NirSoft Launcher launcher (when downloading, note that the zip file is password-protected, the password is on this page).
What data is stored Windows
Everything that is connected with access to files and folders and their location, using programs (including protable), and connecting storage devices (including encrypted file containers) is stored.
Yes, it is not in all cases, something is saved only under certain events, but something can be turned off, but it is better, nevertheless, to assume that everything is always. What connected, what folders-files opened, what programs used.
And from the fact that with Windows logs it is unpredictable what will be recorded there. Due, at least, to the fact that it strongly depends on the specific settings of a specific OS and each of its subsystems, and these logs are available for recording messages in them by third-party programs.
And where does "access" and "location"? A highly exaggerated example: a bank card number and its pin-code will remain in the file “D: \ MySuperSecretContact \ CardPin.docx”, will not be recorded in Windows, but the fact of access and the “talking” folder and file names, that for example, MS Office 2007 portable was used, as well as the date-time of at least the last (sometimes each) access / launch — fixed by Windows, and smeared with a thin layer throughout the system.
About some other data - you can read below in the text, under the heading "Other sources of information leaks known to me, but not falling under the subject of the article"
So, if they connected, started, opened something that I wouldn’t want to become the property of the general public, then it would not be bad for them to sweep away the traces.
An absolutely fair comment from Hanabishi - “But the topic of real logging is not touched at all ... nothing is mentioned concerning telemetry and Win10 in particular” - I apologize, I didn’t really describe that the article is about private data stored locally on users PC . Issues of surveillance, as well as issues of anonymity on the network, is still another, separate topic.
Why does Windows collect data and what is fraught with their removal
Most of the data Windows collects for the convenience of the user - for example, to speed up the launch of applications, to display folders in Explorer with the settings that the user specified, to display a list of previously opened files, etc. etc. To wipe only the data, without losing the amenities at the same time - will not work.
Also, part of the data is collected to assess the performance and condition of the computer and the OS (including failures and errors) by IT specialists and specialized software to solve the problems arising from the user. Without this data, it will be difficult to solve problems if they arise.
And all this is another reason to think about the question of when it is really necessary to erase the data, and when it is not worth it and it may not be necessary to erase it with an empty image every time the computer is turned on and off.
An absolutely fair comment from Hanabishi - “why clean the service logs, if you can simply disable these services?” I did not mention it. Can. As regular means, and dances with a tambourine. But this again means - once and for all to lose the fertilizers, which are our everything.
What will be to me from Vinda for large-scale cutting out of private data, including using the solution proposed here?
Epic fails should not happen, especially if you carefully read the description of each “cleaning” rule and, if anything, turn it off. But the new cap, with a new burqa, is also not expected.
- If any “repair and restoration” works are supposed, then the information important for this will be erased. But this mainly concerns erasing Windows logs.
- If the display of some folders customized for themselves, you have to customize the new
- If you set any programs compatibility mode or run as administrator, you will have to set again
- Due to the mashing of data needed to speed up access to data, their display and launch of programs, the next one, after mashing, access \ display \ launch, will slow down a bit
- Due to the mashing of data about previously opened files, you will have to look for them again, use the menu item "previously opened files" in the programs will not work
- If you choose to delete the cache of Windows updates, then you will not be able to uninstall the updates in a regular manner
Where is this data stored?
After the “surveys” stated in the introduction and the reconciliation of the new reality with the surrounding reality, I got the impression that,
I just want to warn you - this is far from everything, only the most basic and informative (in the sense of the description, not everything is erased in the proposed solution much more) and not deployed also by the “gallop on Europe”. For those to whom this topic is really interesting, at the end of this chapter - interesting materials known to me for independent study + a number of specific “reserved places” are given in the solutions for their cleanup.
The main, known to me, sources of information leakages about user activity
Windows Registry
Background Activity Moderator (BAM ) service. The next nanotechnology from Microsoft - started in Windows 10 starting, if not mistaken, from version 1709 for some of its internal needs.
This service maintains activity logs, although these logs are stored until the computer is restarted (which was confirmed by verification), but still not comme il faut.
We were especially impressed with the results of such an experiment: we run TrueCrypt (protable), a favorite by many, we mount the container file, we run LastActivityView from it.
We see in the registry entry:

That is, theoretically, after running such portable utilities, it would be necessary either to reboot or wipe.
Trying to disable the BAM service is not worth it, catch the blue screen.
The history of mounting disks MountPoints2 (also contains records of type "TrueCryptVolumeK")
The AppCompatCache registry key parameter AppCompatCache is also extremely interesting (it stores data in binary form).
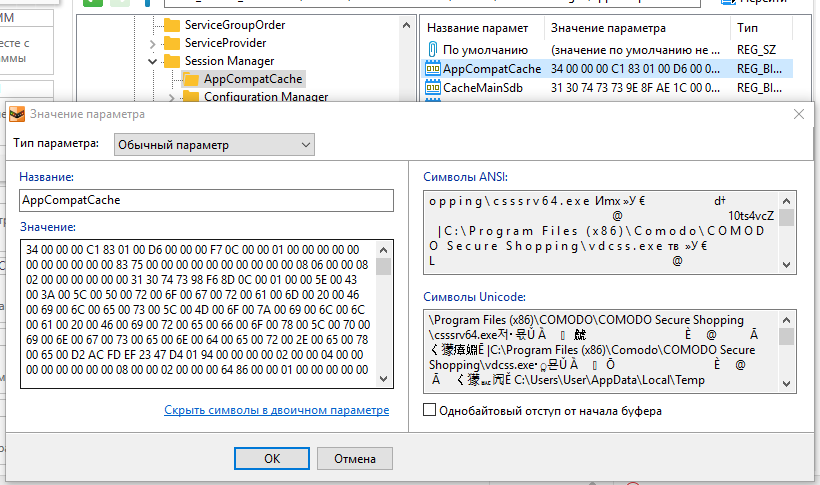
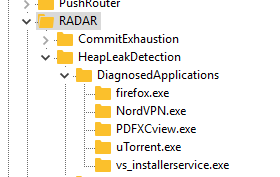
The registry key is DiagnosedApplications. For some reason, nowhere on the forensic forums I later did not encounter a mention (perhaps, just bad looking) of the registry key:
Windows service information for debugging memory leaks in programs.
- ShellBags - Bags, BagMRU. It also stores information on access to folders, including date-time, for saving and restoring them with user settings (explorer window size, choosing to display “list / thumbnails”, etc.).
- OpenSavePidlMRU. History dialogs "open, save."
- MUICache. History of previously running programs for the list of the Start button.
- Uninstall Information is stored to uninstall the installed programs. Thanks CEP - not at all, always happy to help. Clearly, you cannot delete it (thanks again). Contains the date and time of installation of the program.
- MountedDevices. History of mounted (including encrypted) disks.
Background Activity Moderator (BAM ) service. The next nanotechnology from Microsoft - started in Windows 10 starting, if not mistaken, from version 1709 for some of its internal needs.
This service maintains activity logs, although these logs are stored until the computer is restarted (which was confirmed by verification), but still not comme il faut.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\bam\UserSettings\<SID > We were especially impressed with the results of such an experiment: we run TrueCrypt (protable), a favorite by many, we mount the container file, we run LastActivityView from it.
We see in the registry entry:

That is, theoretically, after running such portable utilities, it would be necessary either to reboot or wipe.
Trying to disable the BAM service is not worth it, catch the blue screen.
The history of mounting disks MountPoints2 (also contains records of type "TrueCryptVolumeK")
HKEY_USERS\<SID >\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2 The AppCompatCache registry key parameter AppCompatCache is also extremely interesting (it stores data in binary form).

The registry key is DiagnosedApplications. For some reason, nowhere on the forensic forums I later did not encounter a mention (perhaps, just bad looking) of the registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RADAR\HeapLeakDetection\DiagnosedApplications 
Windows service information for debugging memory leaks in programs.
File system
- Folder Prefetch Windows directory. Well, it 's hardly better to say Vika . There is also a database of another optimizer - SuperFetch (files, such as AgAppLaunch.db). The format of them, as I understand it, is not yet clear to the people, I don’t really care, but when viewed in the hex editor, the paths to the applications are viewed.
- File
C:\Windows\inf\setupapi.dev.log
Information about device connections, network interfaces and more. - Explorer folders with a jump list (aka Jump list). Data is stored along the path type:
:\Users\User\AppData\Roaming\Microsoft\Windows\Recent - Folder (see registry - AppCompatCache)
C:\Windows\appcompat\Programs - Folder
C:\Windows\Panther
Here information is stored for rollback, if you updated the version of Windows
Windows logs: well, here without comments ... even completely fair.
There are a few more places in the registry and on the disc, but they are much less informative and not very interesting (see “solutions”, below). And there is a sea of other places, like the "* .log" files of various services, and even not always Microsoft. True, it is encouraging that CCleaner on steroids (see below) is overwritten by almost everything.
Other sources of information leaks are known to me, but not covered by the article for one reason or another. And here, too, it should be noted that almost everything is overwritten by CCleaner or there are other freeware utilities.
List of those
1. Everything connected with the network and the Internet (this is not included in this article about “locally” stored stories). But CCleaner and Privazer deal with it . Immediately, it should be noted that CCleaner, on steroids, from the solutions at the end of the article, increases its ability to do this.
2. Everything connected with the history of connecting USB devices . To view and delete it, you can use, for example, Usboblivion .
3. Everything related to the file system . “Permanent” deletion of files and cleaning of free space (the same “irretrievable deletion” of previously deleted files left in the wilds of the file system). In general, issues related to the fact that deleted files can be recovered. At the same time it is necessary to mention about the thumbnail caches of Windows images, which tend to store thumbnails of even already deleted images. CCleaner and Privazer can do this, too.
4. Everything related to recovery points (“shadow copies”) in which files are saved, including the system registry with unclosed data. You can connect, view and restore files \ folders from them (without making system rollbacks) with the help of NirSoft utilities (you can also read information from the registry files from there), but, in my opinion, it is more convenient - ShadowExplorer . You can delete restore points with CCleaner. And before creating points, you can run a “sweep” to cut out unnecessary information before saving it.
5. Here is the registry key .
Here they write their data programs, including portable. And they remain here. And if you want to hide the use of a program, then it would be nice to check this thread and, if that, delete the data.
6. Everything connected with the installation of unlicensed software and what is brought to light by God's police program Defacto . There is also a “free analogue” of Lpro (although I have a not very reasonable assumption that the Defacto engine based on it or on its idea was made). But it, in contrast to Defacto, determines only that the software is paid, and not "violation of copyright and related rights."
Exit, IMHO - do not use like. In addition to the well-known Soft Portal on this topic, I can still offer (if anything, this is not advertising, I have no relation to these sites):
- GiveAwayOfTheDay . Every day they distribute one licensed program (you can subscribe to the newsletter).
- Free licenses on the COMSS website . Free (for various promotions) licensed software and subscriptions. As an example - there is now a share of free VPN for a year. And a handy registry editor from Reg Organizer, which I used for research. And even Acronis True Image and encrypted cloud storage for 2TB and much more. “How much?” - “Freebie, sir” (s). (you can subscribe to the newsletter; not bearded jokes, in the sense, but this site).
2. Everything connected with the history of connecting USB devices . To view and delete it, you can use, for example, Usboblivion .
3. Everything related to the file system . “Permanent” deletion of files and cleaning of free space (the same “irretrievable deletion” of previously deleted files left in the wilds of the file system). In general, issues related to the fact that deleted files can be recovered. At the same time it is necessary to mention about the thumbnail caches of Windows images, which tend to store thumbnails of even already deleted images. CCleaner and Privazer can do this, too.
4. Everything related to recovery points (“shadow copies”) in which files are saved, including the system registry with unclosed data. You can connect, view and restore files \ folders from them (without making system rollbacks) with the help of NirSoft utilities (you can also read information from the registry files from there), but, in my opinion, it is more convenient - ShadowExplorer . You can delete restore points with CCleaner. And before creating points, you can run a “sweep” to cut out unnecessary information before saving it.
5. Here is the registry key .
HKEY_USERS\<SID >\Software Here they write their data programs, including portable. And they remain here. And if you want to hide the use of a program, then it would be nice to check this thread and, if that, delete the data.
6. Everything connected with the installation of unlicensed software and what is brought to light by God's police program Defacto . There is also a “free analogue” of Lpro (although I have a not very reasonable assumption that the Defacto engine based on it or on its idea was made). But it, in contrast to Defacto, determines only that the software is paid, and not "violation of copyright and related rights."
Exit, IMHO - do not use like. In addition to the well-known Soft Portal on this topic, I can still offer (if anything, this is not advertising, I have no relation to these sites):
- GiveAwayOfTheDay . Every day they distribute one licensed program (you can subscribe to the newsletter).
- Free licenses on the COMSS website . Free (for various promotions) licensed software and subscriptions. As an example - there is now a share of free VPN for a year. And a handy registry editor from Reg Organizer, which I used for research. And even Acronis True Image and encrypted cloud storage for 2TB and much more. “How much?” - “Freebie, sir” (s). (you can subscribe to the newsletter; not bearded jokes, in the sense, but this site).
Materials on this topic, except for the “sources” at the end of the article.
List of materials
- Scientific article: Some features of the forensic study of the Windows registry (highly recommend, including users)
- ForensicFocus Articles (eng.)
- SANS Digital Forensics (eng.)
- Literature:
- "Inside Windows", Mark Russinovich, 7th edition
- Forensic Analysis of File Systems, Carrie Bryan
- “Windows Forensic Investigation,” Carvey Harlan
- "Forensic - computer forensics", Fedotov NN
- On Habr, on professional forsenic drugs:
- Means of data collection in computer technical expertise
- A selection of free computer forensic tools
- For programmers:
- Parsing a number of forensic data formats in C # can be found here: EricZimmerman github
- Read about ShellBag prasing here.
Since, in the end, they wipe something?
I propose the following option for consideration and criticism: Bleed the CCleaner (which, I think, is more convenient for users and more correct, since it excludes the invention of the next bicycle) and
use the bat file to wipe windows logs.
Plus, below is its own solution, in the form of a bat-file, but, nevertheless, it is not advisable to use it even in my opinion (especially since it erases only the most basic and mainly for windows 10). Is that - I propose to read the comments on the code.
Bleed CCleaner + add your own rules + bat file to erase Windows logs
First, you need to download and run CCEnhancer , perform the "update" (according to the instructions on the page). Just be sure to select and click on this menu item (after closing the CCleaner, if it started):

Otherwise, the winapp2.ini file will contain 100,500 rules that are extremely relevant for the general public, such as the cleaning rules for the Zaiki Spectrum emulator (maybe someone even remembers such a computer), but at the same time slowing down the CCleaner.
Then you need to go to the folder where CCleaner is installed. Find the winapp2.ini file there, congratulate it with relief and open it (for example, in nodepad ++).
Add the following to the end of the file:
[All Prefetch] Section=Windows10 Default=False FileKey1=%WinDir%\Prefetch|*.pf;*.db;*.fx;*.7db;*.ini;*.ebd;*.bin|RECURSE [AppCompatFlags Layer] Section=Windows10 Default=False RegKey1=HKCU\.DEFAULT\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers [Explorer RunMRU] Section=Windows10 Default=True RegKey1=HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU [OpenSaveFilesView] Section=Windows10 Default=True RegKey1=HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder RegKey2=HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder RegKey3=HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRULegacy RegKey4=HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU [UserAssist] Section=Windows10 Default=True RegKey1=HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist [DiagnosedApplications] Section=Windows10 Default=False RegKey1=HKLM\SOFTWARE\Microsoft\RADAR\HeapLeakDetection\DiagnosedApplications [BAM] Section=Windows10 Default=True RegKey1=HKLM\SYSTEM\CurrentControlSet\Services\bam\UserSettings\.DEFAULT RegKey2=HKLM\SYSTEM\ControlSet001\Services\bam\UserSettings\.DEFAULT [MountedDevices] Section=Windows10 Default=True RegKey1=HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2 [Panther] Section=Windows10 Default=True FileKey1=%WinDir%\Panther|*.*|RECURSE [Minidump] Section=Windows10 Default=True FileKey1=%WinDir%\Minidump|*.* Save file.
Create a bat file to clear all Windows logs:
1. You need to create a text file on your computer, for example, using a nodepad ++, in OEM 866 (DOS) encoding (otherwise, instead of Russian letters, there may be cracks). Copy the text into it and save. Rename the file, replacing the .txt extension with .bat
2. It is necessary to run it on behalf of the administrator (otherwise it will generate an error “You must run this script on behalf of the administrator”).
2. It is necessary to run it on behalf of the administrator (otherwise it will generate an error “You must run this script on behalf of the administrator”).
REM Last- ActivityView. Windows @ECHO OFF REM , DOS-866 CHCP 866 COLOR A CLS REM ---------------------------------------------------------------------------------------- REM FOR /F "tokens=1,2*" %%V IN ('bcdedit') DO SET adminTest=%%V IF (%adminTest%)==() GOTO errNoAdmin IF (%adminTest%)==(Access) GOTO errNoAdmin REM ---------------------------------------------------------------------------------------- ECHO 1 ENTER ECHO. SET /p doset=" : " ECHO. REM ---------------------------------------------------------------------------------------- REM ---------------------------------------------------------------------------------------- REM . 1 - IF %doset% NEQ 1 EXIT REM ------------------------------------------------------------------------------------------ REM Windows. , CCleaner, wevtutil ECHO. ECHO Windows FOR /F "tokens=*" %%G in ('wevtutil.exe el') DO (call :do_clear "%%G") ECHO. ECHO ECHO. REM ------------------------------------------------------------------------------------------ PAUSE EXIT :do_clear ECHO %1 wevtutil.exe cl %1 GOTO :eof :errNoAdmin COLOR 4 ECHO ECHO. PAUSE Just in case, before the first launch, you need to create a restore point.
You can additionally read a detailed and understandable description of all the basic rules of CCleaner and the consequences of their use here (Rus.)
Run the bat file. Wait until the work is finished.
Open CCleaner, go to it in the "Cleaning".
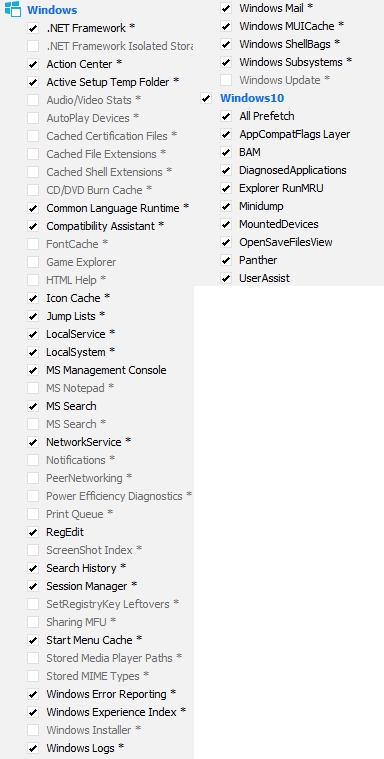
Select the following rules
On the "Windows" tab

On the "Applications" tab
If you use FireFox and Thunderbird , I suggest using the following rules:
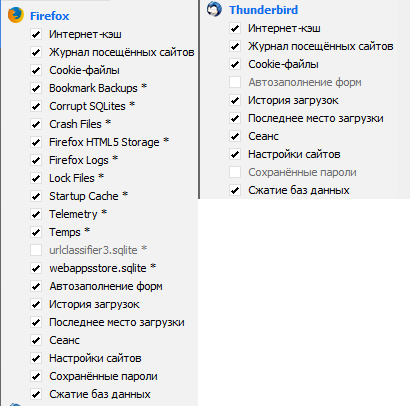
It should be noted that for FireFox, the saved passwords to the websites will be erased (you will have to re-enter it when entering the site). But you can uncheck the “saved passwords” rule.

On the "Applications" tab

If you use FireFox and Thunderbird , I suggest using the following rules:

It should be noted that for FireFox, the saved passwords to the websites will be erased (you will have to re-enter it when entering the site). But you can uncheck the “saved passwords” rule.
Perform cleaning.
Option 2 - Use the bat file
Instruction
This is an alpha version and, theoretically, it can break something, so we use it at our own peril and risk. The first time, before starting, making a system restore point.
1. You need to create a text file on your computer, for example using a nodepad ++, in OEM 866 (DOS) encoding (otherwise, Russian letters may be cracked). Copy the text into it and save it by renaming the file, replacing the extension .txt with .bat
2. Carefully read the comments to his code (as described there are negative points associated with mashing)
3. Run it on behalf of the administrator (otherwise it will generate an error “You must run this script as an administrator”).
4. If there are no registry keys or folders, the script should skip this action.

(this is not an error, it is not found and skipped)
1. You need to create a text file on your computer, for example using a nodepad ++, in OEM 866 (DOS) encoding (otherwise, Russian letters may be cracked). Copy the text into it and save it by renaming the file, replacing the extension .txt with .bat
2. Carefully read the comments to his code (as described there are negative points associated with mashing)
3. Run it on behalf of the administrator (otherwise it will generate an error “You must run this script as an administrator”).
4. If there are no registry keys or folders, the script should skip this action.

(this is not an error, it is not found and skipped)
Bat file text
I apologize, I did not find the highlighting of the batch files.
REM Last- ActivityView. 1 Alpha @ECHO OFF REM , DOS-866 CHCP 866 REM - ... , COLOR A CLS REM ---------------------------------------------------------------------------------------- REM FOR /F "tokens=1,2*" %%V IN ('bcdedit') DO SET adminTest=%%V IF (%adminTest%)==() GOTO errNoAdmin IF (%adminTest%)==(Access) GOTO errNoAdmin REM ---------------------------------------------------------------------------------------- REM !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! REM 1 , , . REM (\ ..) REM .. 2-3 REM 1. - Windows .. , , ( .. ) REM - Prefetch SuperFetch REM 2. REM - - REM ...AppCompatFlags\Layers REM 3. REM , " ", REM !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! REM ---------------------------------------------------------------------------------------- REM ECHO. ECHO ! ECHO , , - ECHO. ECHO. REM , NirSoft ECHO 1 - REM , . REM ( NirSoft ) REM : REM 1. , , (- Perfect SuperFetch) REM 2. (Minidump) REM 3. "" REM 4. , " ". REM ( ) ECHO 2 - , Perfect Minidump REM . .2 + Windows ECHO 3 - , Perfect Windows ECHO ENTER ECHO. SET /p doset=" : " ECHO. REM ---------------------------------------------------------------------------------------- REM ---------------------------------------------------------------------------------------- REM . 1 2 3 - IF %doset% NEQ 1 ( IF %doset% NEQ 2 ( IF %doset% NEQ 3 EXIT ) ) REM ---------------------------------------------------------------------------------------- REM ------------------------------------------------------------------------------------------ REM Windows, 3. , wevtutil REM NirSoft - LastActivityView IF %doset% EQU 3 ( ECHO. ECHO Windows FOR /F "tokens=*" %%G in ('wevtutil.exe el') DO (call :do_clear "%%G") ECHO. ECHO ECHO. ) REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM ShellBag. , "" REM NirSoft - LastActivityView, ExecutedProgramsList, ShellBagsView ECHO. ECHO ShellBag - REG DELETE "HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\MuiCache" /va /f REG DELETE "HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\BagMRU" /f REG DELETE "HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\Bags" /f REG DELETE "HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\BagMRU" /f REG DELETE "HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\Bags" /f ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM Explorer. "" ECHO. ECHO Explorer - REG DELETE "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU" /va /f ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM ComDlg32. "\" " " REM NirSoft - LastActivityView ECHO. ECHO OpenSave LastVisited - REG DELETE "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder" /va /f REG DELETE "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU" /va /f REG DELETE "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRULegacy" /va /f REM ( NirSoft - OpenSaveFilesView) REG DELETE "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU" /f REG ADD "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU" ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM 1 .. 2 3 IF %doset% NEQ 1 ( REM UserAssist. "" REM NirSoft - UserAssistView ECHO. ECHO UserAssist - REG DELETE "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist" /f REG ADD "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist" ECHO. ) REM ------------------------------------------------------------------------------------------ REM AppCompatCache ECHO. ECHO AppCompatCache - REG DELETE "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\AppCompatCache" /va /f REG DELETE "HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager\AppCompatCache" /va /f ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM DiagnosedApplications. Windows ECHO. ECHO DiagnosedApplications - REG DELETE "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RADAR\HeapLeakDetection\DiagnosedApplications" /f REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RADAR\HeapLeakDetection\DiagnosedApplications" ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM SID - FOR /F "tokens=2" %%i IN ('whoami /user /fo table /nh') DO SET usersid=%%i REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM Search. ECHO. ECHO Search - REG DELETE "HKEY_USERS\%usersid%\Software\Microsoft\Windows\CurrentVersion\Search\RecentApps" /f REG ADD "HKEY_USERS\%usersid%\Software\Microsoft\Windows\CurrentVersion\Search\RecentApps" ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM BAM. REM , . REM bat , , portable- ECHO. ECHO Background Activity Moderator - REG DELETE "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\bam\UserSettings\%usersid%" /va /f REG DELETE "HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\bam\UserSettings\%usersid%" /va /f ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM AppCompatFlags ECHO. ECHO AppCompatFlags - REM NirSoft - ExecutedProgramsList REG DELETE "HKEY_USERS\%usersid%\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store" /va /f REM 1 .. 2 3 IF %doset% NEQ 1 ( REM , " " " " REM NirSoft - AppCompatibilityView REG DELETE "HKEY_USERS\%usersid%\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers" /va /f ) ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM "" .. TrueCrypt ECHO. ECHO MountedDevices - ECHO. REG DELETE "HKEY_USERS\%usersid%\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2" /f REG ADD "HKEY_USERS\%usersid%\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2" ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ REM ECHO. REM NirSoft - JumpListsView, RecentFilesView ECHO Recent - DEL /f /q %APPDATA%\Microsoft\Windows\Recent\*.* DEL /f /q %APPDATA%\Microsoft\Windows\Recent\CustomDestinations\*.* DEL /f /q %APPDATA%\Microsoft\Windows\Recent\AutomaticDestinations\*.* ECHO ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ ECHO. ECHO Panther - DEL /f /q %systemroot%\Panther\*.* ECHO ECHO. REM ------------------------------------------------------------------------------------------ REM ------------------------------------------------------------------------------------------ ECHO. ECHO AppCompat - DEL /f /q %systemroot%\appcompat\Programs\*.txt DEL /f /q %systemroot%\appcompat\Programs\*.xml DEL /f /q %systemroot%\appcompat\Programs\Install\*.txt DEL /f /q %systemroot%\appcompat\Programs\Install\*.xml ECHO ECHO. REM ---- REM ------------------------------------------------------------------------------------------ IF %doset% NEQ 1 ( ECHO. REM Prefetch. , . Windows REM NirSoft - LastActivityView, ExecutedProgramsList ECHO Prefetch - DEL /f /q %systemroot%\Prefetch\*.pf DEL /f /q %systemroot%\Prefetch\*.ini DEL /f /q %systemroot%\Prefetch\*.7db DEL /f /q %systemroot%\Prefetch\*.ebd DEL /f /q %systemroot%\Prefetch\*.bin REM SuperFetch. SuperFetch DEL /f /q %systemroot%\Prefetch\*.db REM Trace. DEL /f /q %systemroot%\Prefetch\ReadyBoot\*.fx ECHO ECHO. ECHO. ECHO Minidump - REM REM NirSoft - LastActivityView DEL /f /q %systemroot%\Minidump\*.* ECHO ) ECHO. REM ------------------------------------------------------------------------------------------ PAUSE EXIT :do_clear ECHO %1 wevtutil.exe cl %1 GOTO :eof :errNoAdmin COLOR 4 ECHO ECHO. PAUSE Finals
After using the first or second option, you can run the NirSoft utilities in order to see if we have achieved the desired effect.

Profit ... Now, the main thing is to feed the dogs and not touch anything. And then she will again start writing opera ...
Possible scenarios for using bat and CCleaner solutions
- Use separately. Especially since it makes sense to wipe out magazines completely in “private cases”
- Make a single bat-file, which first wipes logs, and instead of everything else - calls CCleaner, that is, after erasing the logs, put the call: "C: \ Program Files \ CCleaner \ CCleaner64.exe" / AUTOS
- Put this bat-file in autoload (which will probably also solve the problem with running CCleaner on Windows 10)
- bat- Windows, « ». gpedit.msc — « » — « Windows» — « (/)» — « ».
Sources
- Procmon SysinternalsSuite , c — … NirSoft. (.) .
- Windows registry and forensics: 1 2 . (.)
- () CodeBy . Forensics Windows Registry (.) .
- Article Cleanup Windows Logs (anl.) .
- Article Create your own rules CCleaner (eng.) .
By the way, why is Forensic resistance 1?
This will become clear if it ever comes to 2.
Source: https://habr.com/ru/post/424161/
All Articles