“Standoff” on PHDays 8 - A View from SOC
In May of this year, the Positive Hack Days 8 conference was held, where we again participated in the role of SOC in the already traditional Confrontation (The Standoff).
This year, the organizers took into account past mistakes and the standoff began on time. The attackers are great! They attacked almost continuously for 30 hours, so our night shift could not even take a nap.

We talked about the event in our last year’s article , but briefly to refresh.
')
The battle takes place between the Defenders and the Attackers. Defenders can defend alone, and can use the services of expert monitoring centers (SOS) and keep the defense “looking in both”. Defenders also allocate means of defense and protection from hackers, villains.
This year, the organizers built 7 objects that had to be protected:

And 3 SOC teams participated:

Hackers could have fun at their discretion. In fact, the only rule was not to attack the infrastructure directly, on which the Confrontation was “spinning”. In addition, the organizers periodically "played up" to the attacker, deploying holey services. And in the end, the anti-fraud systems in the city were completely turned off.
For hackers, a special cryptocurrency currency and miners were developed, which they could implement in compromised objects. “The miner is spinning, bitcoin is muddling” - according to the apt remark of a member of the Kazakh team Tsark.
This year we again acted as SOC for one of the office segments. The defenders of this segment were the guys from Servionics, already familiar to us from last year’s event.
For defense, we used:
And of course, in our sensors, we use our own developed rules, which also include signatures on the latest attacks that frightened the whole world!
During the period of opposition by SoC analysts, prospective monitoring recorded about 2 million events, 30 information security incidents were revealed.
The alignment of forces on the battle map was as follows:
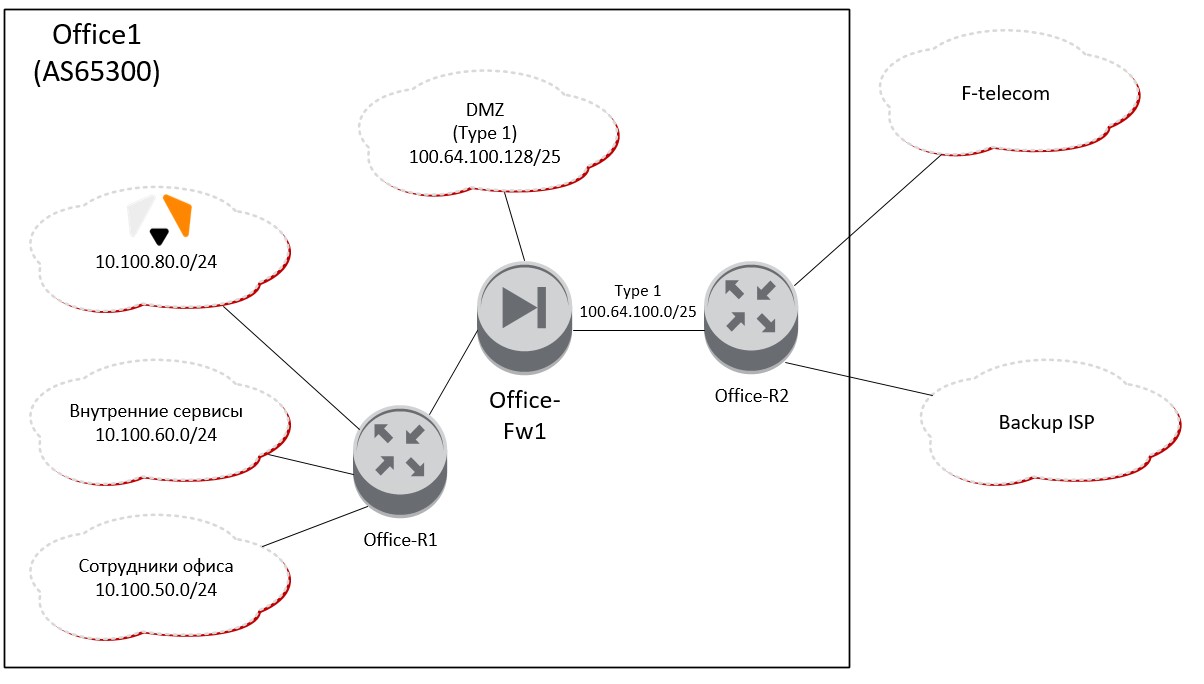
Our colleagues, the Servionika team, were responsible for supporting the infrastructure facilities of Office 1. Our task was to inform when something goes wrong with the guys.
After the start of the game, the majority of events took place around the DMZ-zone. The attackers tried to break through the external barrier through the exploitation of web vulnerabilities. It all started according to tradition with scanning. The attackers launched DirBuster and Acunetix scanners and walked through the addresses in the DMZ.
The attacker with ip 100.110.255.127 persistently tried to establish a connection with the MySQL database of the online store on the protected node 100.64.100.167. All enumeration attempts were successfully blocked by the server.
After some time, traditionally began to pick up passwords for SSH and RDP.
At node 100.64.100.183, when scanning an attacker with address 100.110.255.17, a vulnerability was found in SMB. There was no MS17-010 update on the server . Docs.microsoft.com/en-us/security-updates/SecurityBulletins/2017/ms17-010 . What defenders were timely informed.
It is noteworthy that the test for the possibility of exploiting vulnerabilities in EternalBlue was carried out a great number of times. These events were among the most frequent during the Confrontation. But this is not surprising. Despite the fact that a year has passed since the moment of mass infection, there are still a lot of machines vulnerable to this attack.
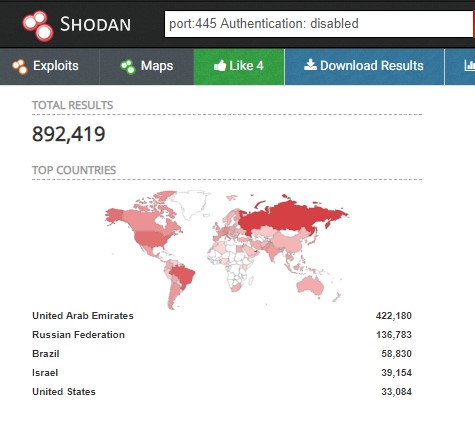
Also, the attackers massively tried to exploit the vulnerability CVE-2014-6271 (remote code execution in Bash).
At around 4:00 pm on the first day, the successful exploitation of the SambaCry vulnerability at node 100.64.100.167 was fixed. Advocates lost access to this site until the next day. The attacker with the address 100.110.255.176 after the operation conducted a reconnaissance of the perimeter using NMAP and took outfile with the data on scanning.
On the night of the compromised node, connections were made to port 443 of node 100.100.100.202. After resetting all sessions, the activity has ended. Presumably, the miner from the hacked 100.64.100.167 was flooded to the node 100.100.100.202.

The main investigation tool is a sheet of paper and a pen.
At night, the attackers actively took up the hacking of the Zabbix monitoring system. Attempts were made to exploit the eternalblue vulnerability, pick up a password for ssh and try to flood the shell via /zabbix/zabbix.php.

On the morning of the second day, suspicious activity was recorded from the protected node 100.100.100.202. A connection to ip from the external network 100.64.100.242 was established from it and suspicious certificates were sent. The conducted investigation showed that the ssh password was stranded on this node and the miner was flooded. Also stole the database file bd.frm. In general, the attacker "slept" on a self-signed certificate. We immediately reacted to this car, watched the session, and there still sits a hacker. Warm.
Almost in parallel with this, the breaking of another node 100.64.100.242 (Wordpress) was discovered. It had some pretty interesting credentials. For login "Shaggy" picked up a password. And he turned out to be ... of course Scooby.
After a compromise from this site, perimeter reconnaissance was performed. We scanned ports 20, 25, 80. Hacker kicked out, took the car.
Until recently, hackers tried to conduct attacks like sql-injections, bruteed FTP, RDP, SSH. In general, they acted according to the classical scheme.

"Confrontation" succeeded! Of course, this time we did not manage to “get dry out of the water.” The attackers managed to partially penetrate the defense of the office. However, this event brought invaluable experience. The obtained information will help to better understand modern attack vectors and take measures to counter them in practice.
This year, the organizers took into account past mistakes and the standoff began on time. The attackers are great! They attacked almost continuously for 30 hours, so our night shift could not even take a nap.

What is what
We talked about the event in our last year’s article , but briefly to refresh.
')
The battle takes place between the Defenders and the Attackers. Defenders can defend alone, and can use the services of expert monitoring centers (SOS) and keep the defense “looking in both”. Defenders also allocate means of defense and protection from hackers, villains.
This year, the organizers built 7 objects that had to be protected:
- Offices
- Telecom operator
- CHP
- Oil company
- Railway company
- Bank
- IoT devices

And 3 SOC teams participated:
- Prospective monitoring
- Angara Technologies Group
- Rostelecom

Hackers could have fun at their discretion. In fact, the only rule was not to attack the infrastructure directly, on which the Confrontation was “spinning”. In addition, the organizers periodically "played up" to the attacker, deploying holey services. And in the end, the anti-fraud systems in the city were completely turned off.
For hackers, a special cryptocurrency currency and miners were developed, which they could implement in compromised objects. “The miner is spinning, bitcoin is muddling” - according to the apt remark of a member of the Kazakh team Tsark.
This year we again acted as SOC for one of the office segments. The defenders of this segment were the guys from Servionics, already familiar to us from last year’s event.
What defended
For defense, we used:
- ViPNet IDS for DMZ.
- ViPNet IDS for LAN.
- ViPNet HIDS (host IDS) to monitor key Office servers.
- ViPNet Threat Intelligence Analytics System (TIAS) for log analysis, monitoring and analytics.
And of course, in our sensors, we use our own developed rules, which also include signatures on the latest attacks that frightened the whole world!
What was fixed
During the period of opposition by SoC analysts, prospective monitoring recorded about 2 million events, 30 information security incidents were revealed.
The alignment of forces on the battle map was as follows:

- Office-R2 is the border router of the Office 1 object, through which it connected to two Internet providers F-telecom and Backup ISP.
- Office-FW1 - firewall for access control between local network segments and external resources (DMZ).
- Office-R1 - used for routing within the office segment.
Our colleagues, the Servionika team, were responsible for supporting the infrastructure facilities of Office 1. Our task was to inform when something goes wrong with the guys.
After the start of the game, the majority of events took place around the DMZ-zone. The attackers tried to break through the external barrier through the exploitation of web vulnerabilities. It all started according to tradition with scanning. The attackers launched DirBuster and Acunetix scanners and walked through the addresses in the DMZ.
The attacker with ip 100.110.255.127 persistently tried to establish a connection with the MySQL database of the online store on the protected node 100.64.100.167. All enumeration attempts were successfully blocked by the server.
After some time, traditionally began to pick up passwords for SSH and RDP.
At node 100.64.100.183, when scanning an attacker with address 100.110.255.17, a vulnerability was found in SMB. There was no MS17-010 update on the server . Docs.microsoft.com/en-us/security-updates/SecurityBulletins/2017/ms17-010 . What defenders were timely informed.
It is noteworthy that the test for the possibility of exploiting vulnerabilities in EternalBlue was carried out a great number of times. These events were among the most frequent during the Confrontation. But this is not surprising. Despite the fact that a year has passed since the moment of mass infection, there are still a lot of machines vulnerable to this attack.

Also, the attackers massively tried to exploit the vulnerability CVE-2014-6271 (remote code execution in Bash).
At around 4:00 pm on the first day, the successful exploitation of the SambaCry vulnerability at node 100.64.100.167 was fixed. Advocates lost access to this site until the next day. The attacker with the address 100.110.255.176 after the operation conducted a reconnaissance of the perimeter using NMAP and took outfile with the data on scanning.
On the night of the compromised node, connections were made to port 443 of node 100.100.100.202. After resetting all sessions, the activity has ended. Presumably, the miner from the hacked 100.64.100.167 was flooded to the node 100.100.100.202.

The main investigation tool is a sheet of paper and a pen.
At night, the attackers actively took up the hacking of the Zabbix monitoring system. Attempts were made to exploit the eternalblue vulnerability, pick up a password for ssh and try to flood the shell via /zabbix/zabbix.php.

On the morning of the second day, suspicious activity was recorded from the protected node 100.100.100.202. A connection to ip from the external network 100.64.100.242 was established from it and suspicious certificates were sent. The conducted investigation showed that the ssh password was stranded on this node and the miner was flooded. Also stole the database file bd.frm. In general, the attacker "slept" on a self-signed certificate. We immediately reacted to this car, watched the session, and there still sits a hacker. Warm.
Almost in parallel with this, the breaking of another node 100.64.100.242 (Wordpress) was discovered. It had some pretty interesting credentials. For login "Shaggy" picked up a password. And he turned out to be ... of course Scooby.

After a compromise from this site, perimeter reconnaissance was performed. We scanned ports 20, 25, 80. Hacker kicked out, took the car.
Until recently, hackers tried to conduct attacks like sql-injections, bruteed FTP, RDP, SSH. In general, they acted according to the classical scheme.
Results

"Confrontation" succeeded! Of course, this time we did not manage to “get dry out of the water.” The attackers managed to partially penetrate the defense of the office. However, this event brought invaluable experience. The obtained information will help to better understand modern attack vectors and take measures to counter them in practice.
Source: https://habr.com/ru/post/423863/
All Articles