Keystone Project: Trusted Environment for Running Applications Based on RISC-V
A team of researchers from MIT and the University of California at Berkeley, with the support of Facebook, Google, Microsoft and other IT giants, presented the Keystone project. This is an open source component that allows you to create a trusted environment for running programs (trusted execution environment, TEE ) based on the RISC-V architecture.
Further - about why the decision was needed and how it works.

/ photo Wikimedia CC
')
Trusted execution environment is an isolated area (enclave) of the main processor with a set of security mechanisms. It is believed that the code and data loaded into this area are reliably protected from changes and interference from outside.
The idea is that in these enclaves it is possible to carry out operations on personal and confidential data without fear of compromising them, since neither the operating system nor other applications have access to these areas of the processor.
There are systems and solutions on the market that protect data at the hardware level. However, all of them are proprietary, as they are implemented by the manufacturers of computer chips themselves. And there is an opinion that these technologies are not well protected (since they are not available for evaluation by independent security experts).
For example, Intel offers an expansion of the Software Guard Extensions (SGX) architecture that protects data from unauthorized access and alteration. This technology also involves enclaves in which the code of the user application is executed. However, recently it became known that this system is vulnerable to Foreshadow attack ( CVE-2018-3615 ). Attackers can gain access to data in the SGX enclave using features of speculative command execution .
In addition to Intel, AMD offers its solutions - their names are Secure Processor and SEV, as well as ARM - they have a TrustZone. However, their security experts also have questions .
According to researchers from MIT and the University of California, the open source system, although it will not make the enclaves invulnerable, will still improve their security through the expertise of many community experts.

/ photo Brad Holt CC
Thus, the Keystone system is an open source project based on the RISC-V architecture for building TEE. The researchers chose RISC-V because it is less vulnerable to third-party attacks aimed at practical implementation of cryptosystems. In particular, this type of architecture is not subject to vulnerabilities like Meltdown and Specter.
Keystone developers set the following goals :
The Keystone concept is based on SGX technologies and the Sanctum Processor enclave developed at MIT .
The latter is built using the so-called trusted abstraction layer , or the trusted abstract platform (TAP). The platform (TAP) consists of a processor with a command counter , general-purpose registers , a system for translating virtual addresses and a set of primitives for executing code in a secure enclave.
From the SGX Keystone system, he “picked up” the Memory Encryption Engine (MEE) engine. The core of the solution is organized using a parameterized RISC-V BOOM processor (Berkeley Out-of-Order Machine) on the Rocket SoC generator.
In general, the scheme of implementing a system with an enclave on RISC-V is as follows:
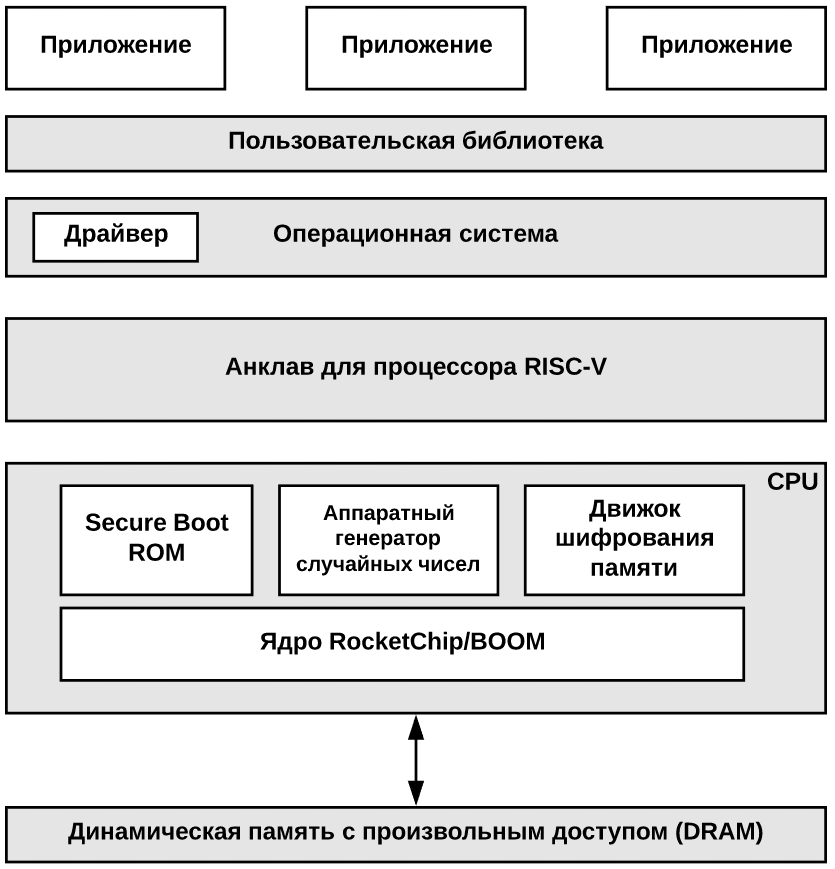
Researchers have already conducted several tests of their solution and have established that it reliably isolates the code execution environment and protects it from outside interference (at least from known attacks).
The first version - Keystone v0.1 - will appear this fall and will be executed on the FPGA. The researchers come to life that in the future it will be able to replace SGX in the implementation of blockchain platforms.
PS Additional materials from the First Corporate IaaS Blog:
PPS A couple of posts from our blog on Habré:
Further - about why the decision was needed and how it works.

/ photo Wikimedia CC
')
Why do you need Keystone
Trusted execution environment is an isolated area (enclave) of the main processor with a set of security mechanisms. It is believed that the code and data loaded into this area are reliably protected from changes and interference from outside.
The idea is that in these enclaves it is possible to carry out operations on personal and confidential data without fear of compromising them, since neither the operating system nor other applications have access to these areas of the processor.
There are systems and solutions on the market that protect data at the hardware level. However, all of them are proprietary, as they are implemented by the manufacturers of computer chips themselves. And there is an opinion that these technologies are not well protected (since they are not available for evaluation by independent security experts).
For example, Intel offers an expansion of the Software Guard Extensions (SGX) architecture that protects data from unauthorized access and alteration. This technology also involves enclaves in which the code of the user application is executed. However, recently it became known that this system is vulnerable to Foreshadow attack ( CVE-2018-3615 ). Attackers can gain access to data in the SGX enclave using features of speculative command execution .
In addition to Intel, AMD offers its solutions - their names are Secure Processor and SEV, as well as ARM - they have a TrustZone. However, their security experts also have questions .
According to researchers from MIT and the University of California, the open source system, although it will not make the enclaves invulnerable, will still improve their security through the expertise of many community experts.

/ photo Brad Holt CC
Thus, the Keystone system is an open source project based on the RISC-V architecture for building TEE. The researchers chose RISC-V because it is less vulnerable to third-party attacks aimed at practical implementation of cryptosystems. In particular, this type of architecture is not subject to vulnerabilities like Meltdown and Specter.
Keystone developers set the following goals :
- Build a chain of trust to test each component of hardware and software (this includes Secure boot systems and remote hardware reliability checks);
- Isolate memory from outside interference;
- Implement methods of protection against attacks on third-party channels;
- Implement encryption methods for memory and address bus.
Solution Components
The Keystone concept is based on SGX technologies and the Sanctum Processor enclave developed at MIT .
The latter is built using the so-called trusted abstraction layer , or the trusted abstract platform (TAP). The platform (TAP) consists of a processor with a command counter , general-purpose registers , a system for translating virtual addresses and a set of primitives for executing code in a secure enclave.
From the SGX Keystone system, he “picked up” the Memory Encryption Engine (MEE) engine. The core of the solution is organized using a parameterized RISC-V BOOM processor (Berkeley Out-of-Order Machine) on the Rocket SoC generator.
In general, the scheme of implementing a system with an enclave on RISC-V is as follows:

Researchers have already conducted several tests of their solution and have established that it reliably isolates the code execution environment and protects it from outside interference (at least from known attacks).
When release
The first version - Keystone v0.1 - will appear this fall and will be executed on the FPGA. The researchers come to life that in the future it will be able to replace SGX in the implementation of blockchain platforms.
PS Additional materials from the First Corporate IaaS Blog:
- New functionality in VMware vSphere 6.7: what you need to know
- "How are VMware?": A review of new solutions
- How to test disk system in the cloud
PPS A couple of posts from our blog on Habré:
Source: https://habr.com/ru/post/423777/
All Articles