Child, internet and parents. How to avoid traps, get a favor and stay friends?

Screenagers - so recently in America they call adolescents. This word is made up of two English words: screen (screen) and teenager (teenager). After all, today's teenagers have already grown up with a phone in their hands.
In 2016, in the same place in America, a documentary with the same name was shot, and to this day it is shown to parents and children all over the world. It clearly presents the consequences of long-term and uncontrolled use of gadgets, as they affect not only the life of a child, but also his health.
In Russia, the mass use of gadgets came later, but today we are already catching up with America in the amount of time we spend on the Internet. This means that this problem concerns us and our children.
Yes, probably it would be foolish to think that we will be able to take away the phones from our children, because most likely this will lead to the fact that in the modern world they will simply lag behind in development and become outcasts in their society. But what we can do for sure is to teach them to consciously use them.
')
In addition to the film, we were pushed to write this article by a brochure published by the White House of the United States. In it the story goes on behalf of the wife of President Melania Trump. In her address, at the beginning of this booklet, she earnestly asks parents to talk to the children about the Internet and explain to them what they might encounter there. And the main thing is to tell the children what they should do in this or that unfamiliar situation. This brochure was translated by us and taken as the basis of the document, which you can read below.
We also made a brochure for people with basic knowledge of information technology, collected all the most important things in one text and tried to write in the language most understandable to the widest audience.
We know that many Habr readers are even better versed in this topic, so we want to encourage you to discuss.
Our goal is to collect the maximum amount of information and opinions. After all, each of us has friends and acquaintances who absolutely do not understand IT.
And we are simply obliged to explain to them what practical actions can be taken so that the lives of their children become safer not only in the real, but also in the virtual world.
The Internet is a unique space in which you can find everything: from sneakers and hot pizza to new friends. We do not think our daily life without the Internet. He helps us in communication and in the search for information. Convenient applications are always at hand, they allow us to pay for a purchase or order a product at a discount, watch a movie or listen to music. This environment can be so attractive that sometimes you want to dive into it and forget about all the limitations of the real world. And we are actively using this opportunity.
In 2017, each of us spent almost four hours a day on the Internet: 115 minutes on a computer and 104 minutes on a mobile device.
Today, 80% of Russians use the Internet, and most of them are children and teenagers.
What do children do on the Internet?
The same thing as adults - they communicate, search for information, watch movies and cartoons, listen to music, download applications, and often understand all the subtleties much faster than we do.
What do adults do?
As a rule, they simply hand the child a gadget or computer and hope that nothing terrible will happen.
Is it correct?
In fact, uncontrolled use of the Internet can cause many very unpleasant and even dangerous situations. Psychologists talk about the epidemic of Internet addiction. And computer scientists - about hundreds of fraudulent schemes that trap a careless user on the Internet.
In this brochure we:
- talk about the risks of uncontrolled and mindless use of the Internet;
- show you how to communicate with children on computer security;
- We will teach you how to configure and use gadgets, network equipment and software to avoid traps and threats on the Internet.
Opinion of the psychologist
Back in 2009, biologist, member of the Royal Academy of Medicine Arik Sigman, in a speech before the European Parliament, made public shocking statistics.
A modern child, who is not limited to using the Internet, spends exactly 1 year in his / her virtual space by his seventh birthday .
By the age of 18, the experience of using the World Wide Web is 4 years .
At the same time, the “radius of activity” of children, that is, the area of space around the house, in which they freely explore the world around them, has been significantly reduced. The current children do not run through the streets and courtyards, do not climb trees, do not chat with each other, and sit for hours, buried in smartphones or tablets.
These trends adversely affect brain development. An independent study of the external world stimulates the development of independent thinking, helps the child to comprehend his impressions and experiences. It also teaches the child to draw conclusions and plan their activities. If, instead of the natural environment, the children's brain interacts with the Internet, children literally grow up “cut off from reality”.
Children who use the Internet uncontrollably do not know how to adequately assess the risks of the world around them, have difficulty in communicating and do not know how to empathize. As adults, they will face problems both in their careers and in their personal lives.
The time of live communication is steadily reduced. The number of single people who have real friendship and love has been replaced by “virtual relationships” is growing.
In 1995, the term “Internet addiction” was used for the first time; today this diagnosis no longer surprises anyone.
How is Internet addiction formed?
Psychiatrist Ivan Kenneth Goldberg, who coined the term “Internet addiction,” defined it as “a painful negative stressful condition caused by prolonged use of the Internet.”

If you do not consciously control the “virtual life” of children, the dependence is formed quickly enough. And that's why:
- Social networks annoy our fun centers. We rejoice when someone comments on our posts and likes photos. Therefore, we, like Pavlov's dog, again and again go to social networks to get the attention that we lack in the real world.
- The Internet and social networks provide a constant influx of new information. And even this not very high-quality information forms the habit of “chewing on virtual food” (this effect can be compared to chewing gum).
- The Internet gives us a “refuge” from reality - motley content helps to forget about real problems and fill the brain with “empty” news.
We are delayed by this process, which eventually gets out of control. We go on the Internet to look at something, but when we “recover” in an hour or two, it is even difficult to remember what we were looking for. Familiar picture? However, there are things and terrible.
Virtual reality traps
Shocking content
A random click on the bright picture may lead the user to the site with scenes of violence, shocking photos or gambling. And if an adult may simply spoil his mood due to “undesirable content”, for a child such an episode is fraught with real psychological trauma, tears, hysterics, the emergence of obsessive states and fears.

Cyberbullying
Harassment in the virtual space (cyberbulling) - can begin with a trifling quarrel and quickly reach horrific proportions. A person who has become the hero of humiliating rumors, discrediting photos and video clips has the feeling that the whole world has turned against him. Negative information on the Internet not only spreads instantly, but remains forever in the form of a so-called “digital track”. Nervous exhaustion or even attempted suicide of young people under the influence of cyberbulling are the terrible symptoms of our time.
Sex and blackmail
Teens are willing to use the Internet to communicate on sexual topics. Barriers of bashfulness are falling, and when the correspondence becomes very frank, there is a danger of sexing - dishonest people can put intimate messages and photos in open access or extort money, threatening to ruin their reputation.
Dangerous dating
The number of victims of virtual pedophiles increases every year. It’s very easy to get hooked on a maniac: it all starts with innocuous correspondence, which goes into unequivocal hints, exchanging photos of an intimate nature and provokes the child to a personal meeting, which can end sadly.
In 2017 alone, about 400 parents turned up on the hotline of the Russian organization “Pass a Pedophile”, whose young children were caught on social networks using pedophile tricks.
Theft of information
Phishing is “catching up” of users' confidential data, from email address to payment card details and savings accounts. Fraudsters steal user data under various plausible pretexts: authorization on the site, the need to “unsubscribe” from spam email, payment for purchases at a low price or with a big discount, the need to install a new application. In order for the victim to voluntarily disclose his personal data, attackers can use phishing sites, e-mail newsletters, “fake sites”, pop-up windows and advertising.
Spam
Junk mail or spam - not just takes time and litters your inbox. Newsletters may contain dubious promotional offers and “letters of happiness,” which a young user may take for good coin. In addition, through spam, you can get a computer virus or become a victim of phishing.
Viruses
Downloading questionable files or programs can lead to virus infection of your computer and mobile device. Malicious programs are capable of completely destroying the software in a matter of seconds and even making your equipment part of a hacker network. You won't even know about it. Viruses are disguised as useful programs, and it is impossible to recognize them without special software. The absence of an installed antivirus program on a computer or phone increases the chance to “catch” the virus at times.

So what to do?
After all, the Internet is so useful. There are so many convenient applications. There you can find any kind of information and write to any person, even if you don’t know it at all, and he lives on the other side of the planet.
Here are just some of the great features of the internet:
- Online education: a variety of courses, lecture halls, and even virtual universities provide great opportunities for self-education and for acquiring useful skills.
- Acquaintance with the outside world, nature and customs of different nations: in order to make an exciting virtual tour, it is not necessary to leave home.
- Reading and listening to books, music and movies: the Internet offers you a myriad of amazing worlds and gives you new discoveries every day.
- Communication, exchange of ideas and new acquaintances: in social networks and blogs you can find people of similar spirit, share knowledge and ideas, keep your blog and get inspiration for creativity and development.
- Just rest: on the Internet you can do shopping and play educational games, and besides, all the latest news is also here.
Good news
Psychologists advise parents to actively participate in bringing children to the Internet and take part in its daily use.

To begin with the most important rules :
- Take time to communicate with your child. When parents sit down a child at the computer so that he does not interfere with his business, they open all the Internet traps with their hands.
- Take care of the leisure of your child. The more interests and hobbies he has, the greater the chances that the Internet will become a valuable source of information for the young user, and there will simply be no time left for the negative.
- Become a guide for your child to the Internet (and not vice versa). Parents better be a little ahead of their own child in the field of Internet development. It is not easy, but worth trying.
- Know what your child is doing on the Internet. Add it to your friends in social networks and support communication on the Internet. At the same time you will be aware of who he communicates with.
The main landmark - the age of the child
The smallest users (2-5 years)
If you give mobile devices to your young children, be sure to pre-configure them so that the child can only see information that corresponds to his age.
It is still too early to tell the kid about the threats to the Internet: he just won't understand you.
The actions of a very young child are the easiest to control - just be near and look at what he is doing. Do not forget to keep track of time: too much internet is bad for a child’s health.
Young researchers (6-11 years)
Kindergarten graduates and junior schoolchildren are already taking the first independent steps in mastering the Internet. This age is the most suitable to start talking with your child about computer security, about the traps of virtual reality and the need for metered use of the Internet.

What to ask?
- What is he interested in on the Internet, what is he looking for?
- Is there something he can't find?
- What questions about the use of the Internet does he have?
What to explain?
- Which sources of information are reliable and secure.
- What the user is sharing can be made public.
- Show the difference between the real and the virtual world. The child must remember that not everything seen on the Internet is true - this applies to people and information.
How to say?
Discuss with the young researcher news that relates to the negative impact of the Internet on human life and health.
Show maximum patience and always monitor the child's reaction to this or that information.
Express your opinion calmly and openly. Some information should be discussed several times for a better understanding.
Teenagers (12+)
Adolescence is associated with active socialization - parents are fading into the background, peers, their idols and current trends in the youth environment are becoming increasingly important in the life of a student. At this time, communication with close adults, including on computer security, may not be so confidential. But a teenager is able to become your soul mate and ally in the struggle for computer security - for this, you just need to captivate him with this topic.
What to teach?
- In adolescence, people strive for independence - so now is the time to teach a child to make independent decisions, adequately assess his or her competence and, if necessary, seek help.
- Teens often go to the Internet from their mobile phones. Tell them in detail about the threats and their signs.
- How to act if he is faced with any danger on the Internet.
Universal advice: in case of any doubts and in any difficult situation, the child should seek the help of a parent .
What to talk about?
- Different types of cyber threats, their manifestations and consequences for adolescents and family members.
- Confidentiality of personal information, caution when disseminating information about the adolescent and his relatives, their property status and plans.
- Security measures for online dating and the transition "from virtual life to real."
- Setting up mobile devices, antivirus programs, rules for creating accounts and choosing a password.
Teach your children to take breaks every 30-40 minutes working at a computer or communicating with a gadget to relieve tension from their eyes, stretch their muscles and get some rest.
How to say?
- It is very important not to put pressure on the teenager, so as not to cause rejection. Speak calmly and respectfully. Be consistent with your requirements.
- Do not scold a teenager if you see that he is watching something inappropriate on the Internet. Arguably explain why you should not visit these sites.
Try to make computer security a habit with your whole family .
Then you just find the information that will help you do it.
Before giving the child a phone or computer

Step 1. Create a new account on your mobile device.
This account must be configured for the child:
- Browsing the web on the Internet: specify a list of sites that you want to block to view.
- Applications and games: you can block the launch of certain applications.
- Timer work: set the time at which the child can use the mobile device.
- Shopping and spending: take care of tracking baby purchases in applications.
- Search for the child: connect the useful function of tracking the location of the gadget.
How to do it?
- The simplest parental control for Android is by default on Google Play. It can be configured here: Google Play - Settings - Parental Control. Do not forget to set content filtering.
- In Google Play and the App Store there is the possibility of protection from accidental and unwanted purchases.
On Google Play, this can be configured here: Google Play - Settings - Authentication upon purchase (enter the password).
In the App Store, this can be configured here: Settings - General - Restrictions (enter the password for restrictions) - Enable restrictions (software installation, software removal and in-app purchases). - In iOS, there is a “Guide-access” function, which limits the use of the device to only one application, and you can choose which functions of an open program will be available. Exit from the “Guide-access” is possible only with the help of a secret digital combination. You can enable the function here: Settings - General - Universal access - Guide access. Then in the active program you will need to press the “Home” button three times, and the “Access Guide” will be turned on.
- There are so-called “child shells”, they allow you to create a safe zone on your device in which only allowed applications and games can be run. To find such applications, go to Google Play and enter the query “child mode” in the search bar.
- There are applications that allow you to set the entrance to the selected applications by password or fingerprint, thereby restricting access to them. To find such applications, go to Google Play and enter the query “password for applications” in the search bar.
- There is an application for Android and iOS, which allows you to limit the time of using a mobile device, blocks unwanted sites and applications. In addition, the application informs about which sites the child visited, what search queries did and determines the location of the gadget on the map. To find such an application, go to Google Play or the App Store and enter the query "Safety of children on the Internet"
Step 2. Install the parental control device on the computer

Many companies offer software that allows you to configure or limit access to the Internet. Such programs may include the following functions:
- Filtering and blocking. Allows you to restrict access to certain sites, programs and images.
- Lock the data that the child sends from the computer. Does not allow children to share information on the Internet, including sending something by e-mail.
- Browsers for kids. Allow to filter the content that your child sees.
- Search engines for kids. Restrict the search and filter its results.
- Monitor child activity in the browser. Organizes the control of children's access to the Internet. He fixes the addresses of websites that the child visited, sends messages to parents at the moment when the child visits a prohibited site.
How to do it?
The simplest parental control tool in Windows is by default. To set it up:
- create a new account (Settings - Accounts - Family and other people - Add user for this computer);
- configure it (Settings - Accounts - Family and other users - Manage family settings via the Internet);
- in the “Browsing the Web” section, enable blocking of unwanted websites or specify a list of available and unavailable sites;
- in the section “Applications, games and multimedia” restrict access to selected programs;
- in the “Timer working with the device” section, limit the time spent working at the computer.
The simplest parental control tool on Apple devices is by default. To set it up:
- go to “Parental Control” (System Settings - Parental Control), create a new account with parental control and configure it;
- On the “Programs” tab, disable or allow to use the camera, limit the list of allowed contacts in the mail and allow the use of certain programs;
- on the “Web” tab, allow access to some sites;
- on the “Shops” tab, disable Apple’s built-in stores, as well as limit watching movies and listening to iTunes music;
- on the “Time” tab, limit the time spent at the computer.
In the Google Chrome browser, you can enable the “Parental Control” feature. To do this, create a new user account (Google Chrome - Settings - Users - Add a new user). When creating, tick the “User Controlled Controlled Profile” and set up an account.
In the Yandex search engine, you can exclude Internet resources with obscene words and “adult” content from the results of the issue. To do this: go to the search engine page, select its settings (Settings - Portal settings) and the “Search results” section. In the “Page Filtering” menu, select the “Family Search” setting.
Step 3. Teach your child to create strong passwords.
Tell the children the basic rules for creating passwords:
- the password must consist of at least 6 characters;
- The password may include numbers, Latin letters, spaces and special characters (periods, commas, exclamation marks, etc.);
- it is recommended to compose a password from a mixed set of numeric and alphabetic characters;
- do not use common words and stable phrases;
- do not use character sets, which are combinations of keys located in a row on the keyboard, for example, such as: qwerty, 123456789, qazwsx, etc .;
- personal data should not be used: first and last names, addresses, passport numbers, insurance certificates, etc .;
- for different accounts you must use different passwords.
How to do it?
There are free and fairly easy to use programs for creating and storing passwords. Find such a program on the Internet, install it, create a password and save it.
Step 4. Install an antivirus program
Viruses can cause irreparable harm to the information stored on your computer and mobile device.
Antivirus software is the primary means of protecting your computer and mobile device from viruses. Therefore, it must be installed on each device with Internet access.
New viruses appear every day, so antivirus programs need to be updated regularly.
Almost any antivirus program has a selective scan - with its help you can check any file.
Step 5. Protect your home network
New routers come with standard network names (SSID) and passwords. This information can only be used the first time you connect to the Internet. Then be sure to change the network name and password so that the attackers could not access the router.
Create a secure password and a unique name for your Wi-Fi network.
Modern routers support various methods of encrypting data transmitted over a wireless network, including WEP, WPA and WPA2. WPA2 is optimal in terms of reliability.
Router settings allow you to filter network access by unique device identifiers (MAC addresses). You can create a list of MAC addresses of trusted devices or deny connecting devices with specific addresses.
There is no perfect technology. Attackers are constantly finding new vulnerabilities. Periodically update the firmware of your router to protect against intruders.
Some routers have a built-in attack against network attacks - firewall. Look in the security settings of the router for a function with a name like Firewall, “Firewall” or “Firewall” and enable it if possible. Configure additional firewall settings in accordance with the official instructions or contact a specialist for help.
Most home routers and wireless access points have the ability to restrict Internet access at certain hours. Therefore, you can limit the possibility of using the Internet for family members who do not have devices with Internet access and a modem function.
Step 6. Do not use open Wi-Fi networks
Find a free Wi-Fi network is simple: just starting the search, you will probably stumble upon a couple. Without them, it is difficult to imagine the airport, train station and other public places. Most often, these networks are open, that is, everyone can get access to them.
If you have an inexpensive mobile Internet, then it is better to use it, rather than open Wi-Fi networks, as they are insecure.
Tell your children the danger of open Wi-Fi networks:
- Traffic analysis. The owner of the Wi-Fi network or the person who accessed it can view all traffic passing through it. With the help of a data packet analyzer, he can find out which pages you entered from the connected devices and what data you entered.
- “Fake” password theft pages. When connecting to Wi-Fi in a public place, the user is often asked to confirm his identity by phone number or register through social networks. All data entered at the same time, the owner of the point can collect for personal use. Also, a person who has access to the management of the router has the ability to configure phishing: for example, redirecting from facebook.com to facebook10k.com, which will contain a copy of the main page of the popular social network, created to steal passwords.
- Malware infection. The user of the open network can be redirected unnoticed for him, not only to phishing sites, but also to download pages for Trojans and viruses that can steal a lot of valuable information for fraudsters (passwords, documents, etc.) from a computer.
Step 7. Setting up security in social networks
Make sure that the strictest security settings are set in the child’s social networks.

For example, the “On Contact” page should be open only for those whom the child has added to friends, and only friends can write messages to him too.
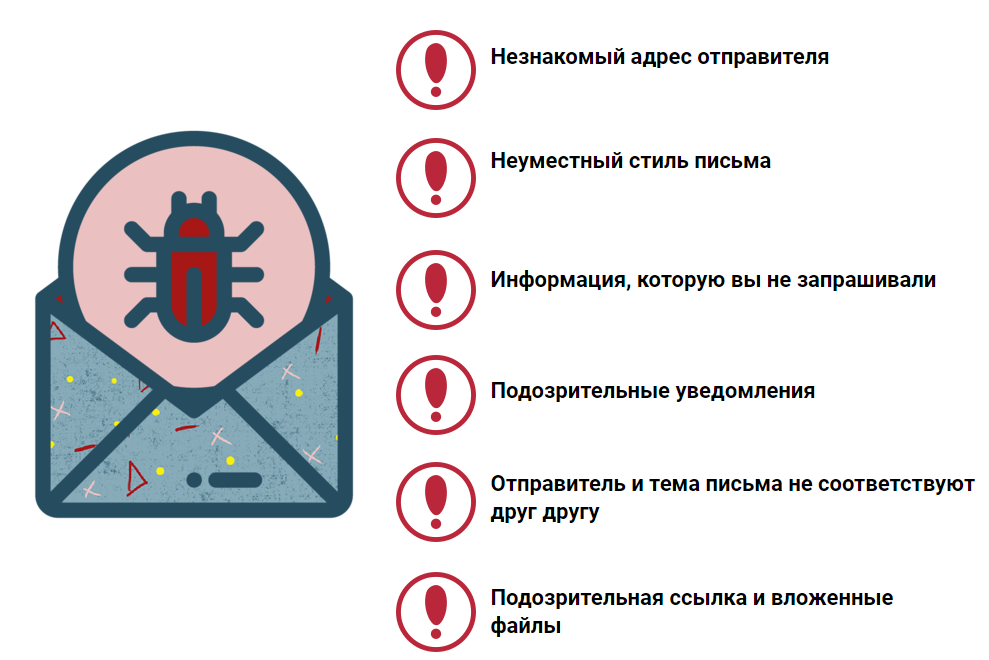
Step 8. Do not read spam letters
Learn yourself and teach your children to recognize spam letters.
The main signs of spam emails
Universal protection against threats does not exist. Therefore, the best way to protect a child from this is to participate in his “virtual life” and teach him to abide by the rules of computer security.
Sit nearby when he plays games, visit his favorite sites, discuss topics of interest to the child. Let your child introduce you to their virtual friends.
Tell your child about the different situations that happened to people on the Internet. The child is much easier to understand with examples how the Internet can harm him.
What categorically can not do on the Internet?
These internet security rules must be followed by everyone:
- Do not share passwords from social media accounts to anyone.
- Never send passwords and personal data via e-mail or via instant messenger.
- , , .
- , , , . , , 100% , .
- , , .
- . , - .
- , , .
- , , , , .
- e-mail .
! , - .
?
, , - , , , .
“ ”. .
. , , - , .
:
- , . , .
- , .
- , .
- .
- , .
- . , “” , . .
- . - , . .
— , : .
, , . .
:
" , . , ? "
:
- ( , ).
- Screenagers .
- “ ”.
- “ : ? ”.
- “ : ? ”.
- “ ” — “ ”.
Source: https://habr.com/ru/post/423557/
All Articles