Conference DEFCON 22. Andrew "Zoz" Brooks. Don't screw it up! Part 2
Conference DEFCON 22. Andrew "Zoz" Brooks. Don't screw it up! Part 1
Use Opsec 24 hours a day, 7 days a week. You see a screenshot from a chat on Reddit with Sabu, already after he became a snitch, in which he advises the other person to use Opsec 24/7. So if the "friends" want to drown you, they can do it. Never before has any federal informer said more truthful words.

')
Another case that we all heard about. A Harvard student who reported an explosion threat during exams. He used Tor to connect to the Guerilla mail service, which allows you to send disposable email messages.
The feds caught him because Tor adds the original IP of the sender to the message header. So Opsec fails in this case. Basically, such nonsense is related to privacy tools with which you are “not friendly.” Therefore, you should have privacy for breakfast, lunch and dinner. She's like bacon that makes everything better!
I'll tell you how this student fucked up. First, the Harvard intranet requires you to register your MAC address . Another reason MIT is better than Harvard is because we don’t require it. So, the user's registration in the network is tied to his MAC-address , in addition, they log outgoing traffic. It is a common microcosm of observation. All this together created threat vectors that allowed this guy to “get it”. For example, investigators could see who went to the site and downloaded the Tor installer just before the threat of an explosion, or to see everyone who was tied to a well-known Tor recording site at the time, or who was accessing the servers in the Tor directory.
When I think about it, I understand that in our country there is already a model of ubiquitous observation, with which everyone is familiar - these are credit agencies. And we are doing a kind of Opsec with credit agencies. We receive credit primarily due to our reputation. Therefore, use confidentiality before taking out a loan. We do not cancel credit cards, even when we don’t need them anymore, because they themselves create our reputation. So don't stop using privacy tools, even when you're done doing something bad. Just like using a credit agency, using Tor can put you on the list. But you have a good reason to be on this list.
So there are many ways that this guy could not spoil everything. To begin with, he at least had to analyze the situation and prepare for the inevitable interview with the police as a Tor user. He could use bridge connection switches to connect to Tor . Although it later became known that the NSA also monitors them. He could have prepared for the fact that the entry point of traffic could be tracked, leave the campus and use the Starbucks café network or a disposable mobile phone, and then, probably, he would not have been caught.
People constantly receive threats of terrorist attacks and bombings, and in fact there are no ways to track such messages. You just have to make your discovery difficult. And, of course, he could use a mail service that did not identify the IP and opened its output Tor node.
What do we know about how vulnerable ordinary Tor users are? It is known that this network caused a lot of trouble to the UK GSHQ government communications center, they even held two conferences on combating Tor , the last one in 2012. So, probably there is not a simple backdoor. This is good news that they should have held such a conference. We know that using Tor is obvious because it forces users to be different from users of open networks. So consider that you have already been fingerprinted.
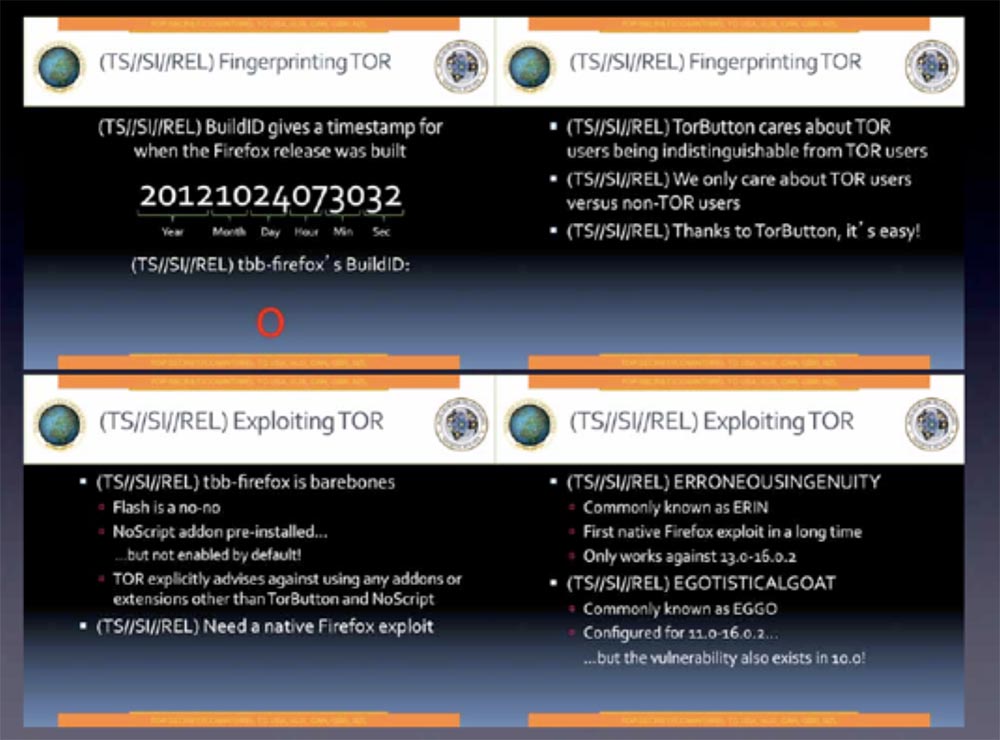
We know that the attacks on Tor in 2012 were quite difficult for the special services, so they tried to introduce an exploit into the version of Firefox , which is used in the Tor software package. I think this is also a good sign. These are slides from the famous Tor stinks presentation (Thor stinks ...), I am sure that you have already seen it, so I’ll show them quickly.

So, there is a recognition that the feds have never managed to reveal all TOR users. With the help of manual analysis, they can identify a very small number of users; in addition, attempts to reveal users using Tor queries have never been successful.
So you must use Comsec inside your Tor sessions. Of course, they commit traffic correlation attacks, albeit on a small scale. They are trying to discover Tor users at a time when they don’t use them. To do this, they are trying to extract cookies that have been preserved from using this browser. Tor is good because it does not store such cookies. They also recommend using the QUANTUM exploit method, which helps extract cookies from Tor thanks to the presence of Firefox elements.
The above should give you some thoughts about how secure Tor is as the only solution for anonymous Internet use. Never use the only solutions, have a backup option. Using Tor regularly is good, making it difficult to detect, but not absolutely impossible.
Here is the third secret document, released at the same time. Here, Tor leads in low detection and high anonymity of users.
Here it is indicated that it is widely distributed throughout the world, is an open resource, is actively developing, reduces the risk of threats, is very safe. It says here that “Thor is king in the field of ensuring anonymity and secrecy and in the near future no other contenders for his throne are foreseen.”
The positive feedback from the secret police was received by software platforms used on the client side, such as the fully autonomous Tails software downloaded from the CD.

What does this mean? The fact that Tor puts you in the field of view of the authorities, but Tor and Tails complicate their lives. I think that just using Tor puts you on a rather extensive list of people, and if your “disobedience” will help move you to a smaller list of people deserving more attention, then it’s probably better to be on the big list. Because the more people on this big list, the better.
But never make your life or freedom dependent on one element, one factor of personal security. This also applies to Tor , and many other tools on your Internet communication networks. I like the motto posted on the CryptoCat website - never trust your life or freedom with software. We trust our life to software every day, every time we get into a car or a plane. But when you drive in a car, you also rely on seat belts. It's like an old Muslim saying: “Hope for Allah, but tie a camel.”
Here's some more good news. A large list and a small list are the recently leaked filtering rules. I know that this is completely unreadable, but basically it shows that the security authorities are obsessed with the idea of making this big list as big as possible.
Anyone who connects to the Tor directory service or to the Tor website is included in this large list. From the point of view of the state, this is the reception of the secret police. It's great. This is akin to finding a needle in a stack, into which we will throw even more hay. Therefore, guys, try to make this big list even bigger to add work to them. They are more aimed at everyone who uses Tor , and not at real criminals, this is stupid, but it is no more than the total surveillance we are talking about. It just proves that we need more people using similar services.
The right side of the slide is worse. I have already mentioned that they collect the email addresses of people who are used to receive "bridge switches", that is, Tor nodes . You should know that they are engaged in such vile things. Thus, a Harvard student might not have been caught using a “bridge switch”. Maybe yes, maybe no. We don’t know for sure, because we don’t know how much information federal agencies and providers share with each other, so just be careful.
Finally, at the bottom of the slide there is evidence that Thor and Tails are being promoted by extremists in extremist forums. So congratulations, it turns out, we are all extremists!
We all know the history of the anonymous Silk Road trading platform and its administrator Pirate Roberts. Silk Road worked as a hidden service Tor for 2 years, until Roberts was arrested.
We know that the feds made hundreds of drug purchases through the Silk Road, allowing him to work longer to make sure that they could arrest someone. It looks like standard organized crime. They arrested Pirate Roberts and at the same time captured all the information on the Silk Road server.
So what made him screw up? We know, Dread Pirate Roberts has repeatedly failed due to the neglect of Opsec - this is both a saved messaging stack and forum posts from the same account that included its real email address. That and the orders of fake IDs with his photos, so that he had enough opportunity to screw it up.
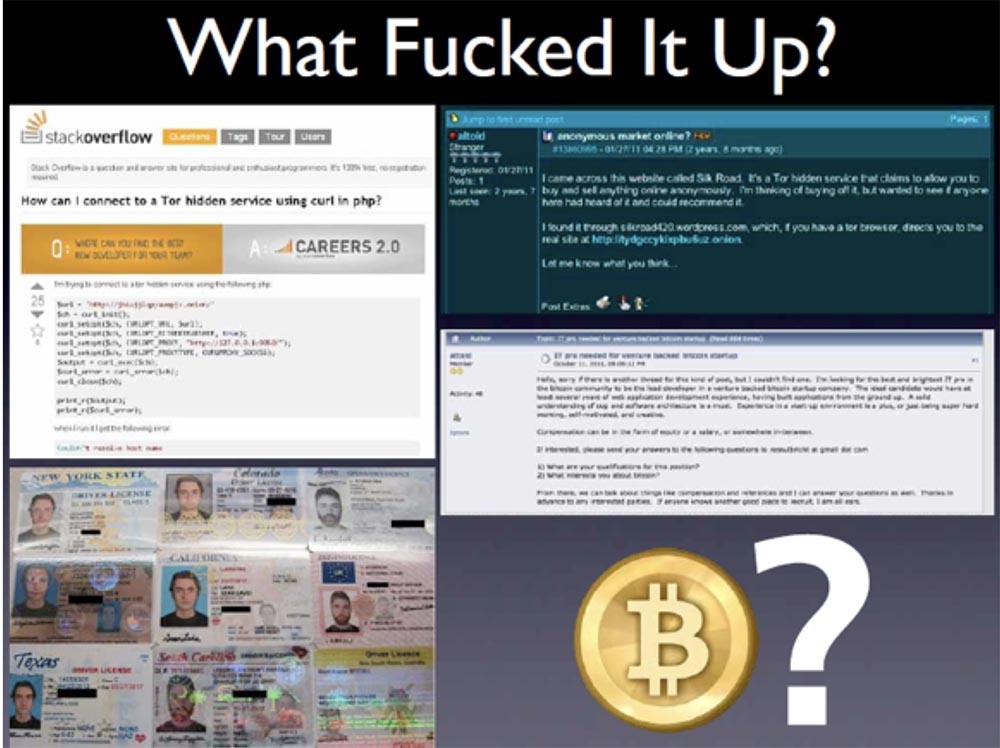
But we do not know how we managed to reveal the anonymity of the server. This is 180,000 bitcoins. How could this happen? We do not know the answer. But there are several options. Pirate Roberts was identified and tracked in the same way that Sabu was tracked down. For example, he could log in only once without Tor , for example, to fix something on the server.
You can not deny this possibility. He could be tracked by financial connections with the provider thanks to tools for tracking payments on all hosting servers, as was the case with other independent hosting providers. They could inject an exploit into the Silk Road server, capture it and break the anonymity mode.
They could also perform a large-scale hidden attack on anonymous services. We do not know the answers, so let's talk about the only way that includes a direct attack on Tor . What you need to know about hidden services is that they are quite vulnerable from the point of view of correlation attacks, since an attacker can offer them to generate traffic. There are two Tor outlines connected around one point. Anyone who connects to Tora for a long time becomes vulnerable to this kind of thing. Especially to switchable segments, because the network is not so great, so sooner or later you will be able to stumble upon a malicious node.
This is not a big problem for the average user, but if you support a long-term project such as a global drug supply company, then it is dangerous. I did not have time to go into details, but I want to show you a piece of research that Biryukov, Pustogravov and Weinman from the University of Luxembourg conducted in 2013, it is called Trawling for Tor Hidden Services: Detection, Measurement, Deanonymization ( services: detection, research, de-anonymization "). They created a chart of popular hidden services Tor, Silk Road and DuckDuckGo , showing the change in the number of requests throughout the day.
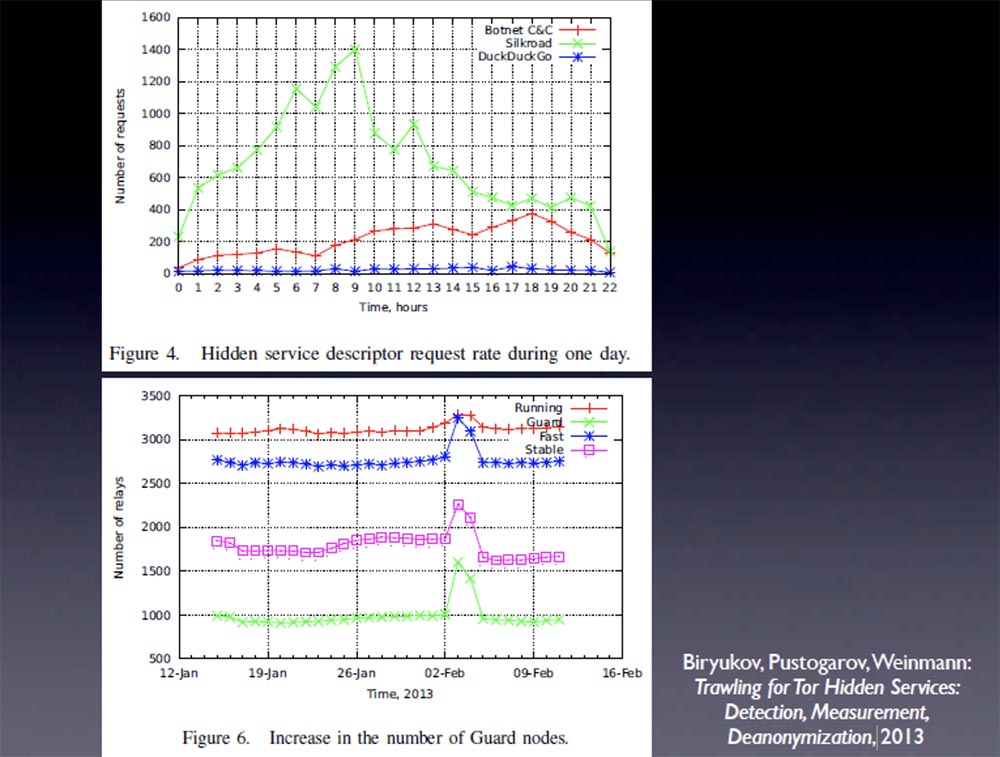
The following shows the display of "onion" addresses and their use. Two days and less than one hundred dollars, and they see two examples. There is also confirmation that a certain Tor node acted as a border node of a hidden service to de-anonymize this hidden service, with a probability of 90% within 8 months for $ 11,000. Such studies are entirely within the financial capabilities of state actors. This was made possible thanks to the error Tor , which has already been fixed. This week, Black Hawk told about another similar error that was also fixed. They could detect Tor traffic for hidden services. It was very irresponsible, because now there are fears that the feds can track all the traffic passing through Tor . Thus, if Tor's encryption mechanisms are compromised, people cannot be sure of their anonymity.
The good news is that these things leave traces. There was a surge in the increase in the number of protection nodes at the time when Biryukov and the company were making their incursions into the network. So we can find these errors and correct them, but keep in mind that there are potential attacks on Tor , though not against everyone and not constantly.
I will not talk much about what is shown on the next slide - this is also secret information that concerns the technical analysis of hidden services.
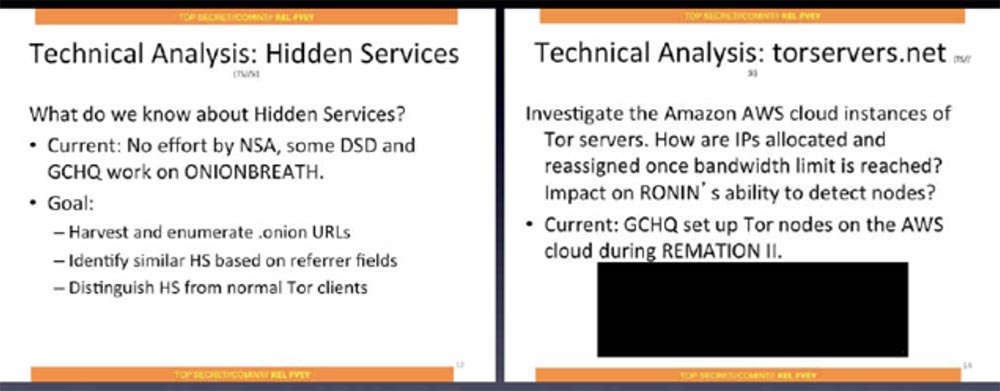
The purpose of the analysis is to collect and compile a list of "onion" addresses, identify similar hidden services based on similar anonymity technologies, and separate hidden services from normal Tor clients. The following is a study of the capabilities of the Amazon AWS cloud service for hosting Tor servers and the British GCHQ toolkit for detecting Tor nodes in Amazon cloud computing facilities, which was mentioned at the Remation II conference.
Remember also about the capabilities of such a tool as the JTRIG Tools , I think its page should have been decorated with DefCon flags.
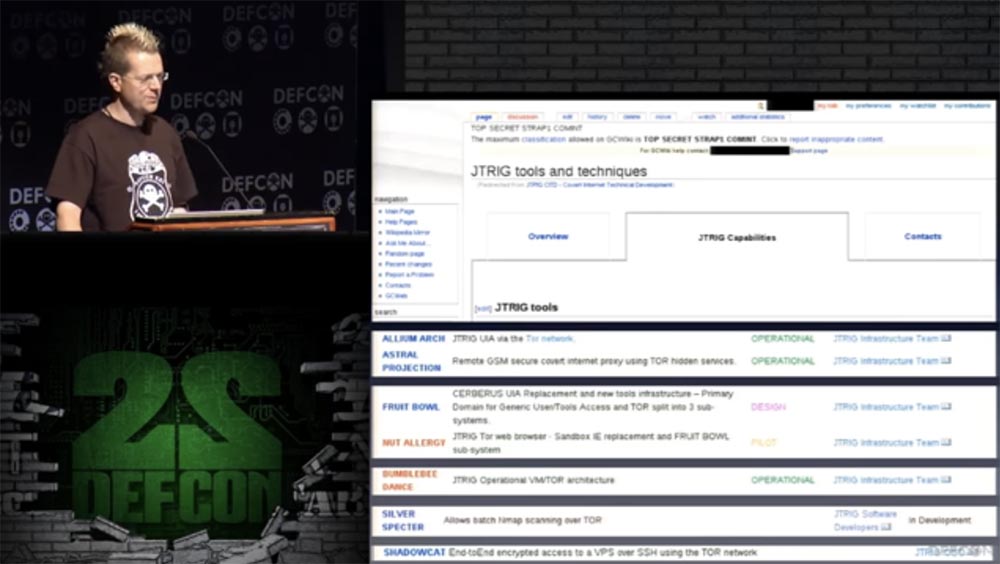
"Hearing" Spooks use Tor quite intensively, as do English intelligence services. I think the developers of Tor , many of whom I personally know, are subject to the sin of excessive trust. They believe that their activities will not be disclosed, although they do not walk on the hind legs before the state, do not receive handouts from him, and do not leave a loophole in their software for the "hearers".
I think that the key purpose of the special services was not to disclose the entire anonymous network, but only to discover such hidden services as the “Silk Road”. It is theoretically possible for the server to be fully identified and open, because here there is a bidirectional Tor operating scheme, thanks to which Pirate Roberts was captured. Perhaps if he had practiced the use of COMSEC properly , he would not have been caught. So the moral of this story is this: do not launch massive online sales of drugs if you do not have a plan to effectively protect anonymity. For a large organization, maintaining anonymity for a long period of time is a very difficult task. You have to do everything perfectly, and for this you do not need to have the mind of an international cyber-criminal, so that your opponents could not take proactive measures. So find out in advance what the consequences of your activity may be, do a Tradecraft analysis .
Now let's go to the phones. Do not screw it up using cell phones! What does this little Benedict Arnold (the American general of the times of the war for independence of the USA who went over to the side of the British), hidden in your pocket, say?
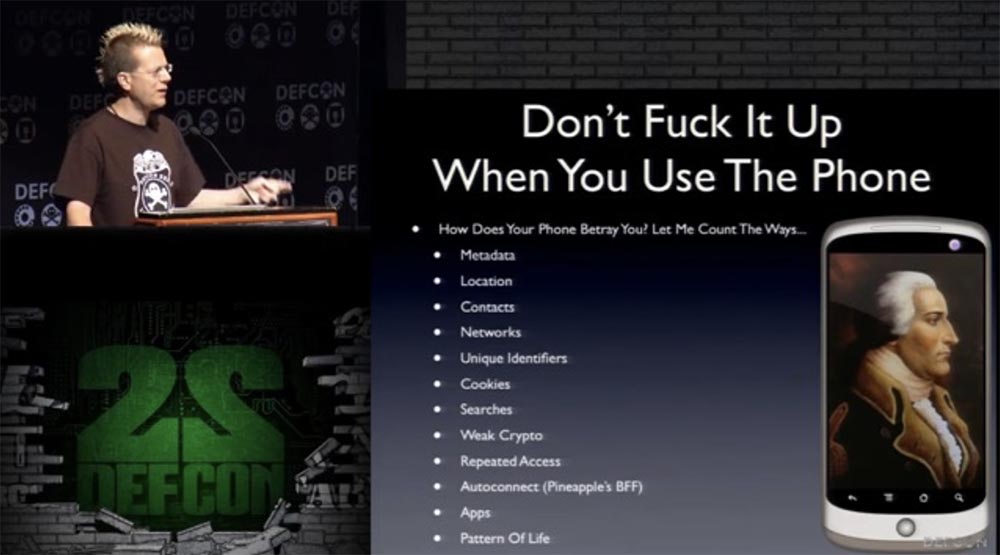
The phone can betray you in these ways:
The security agency constantly monitors these kinds of things, especially they watch for the simultaneous presence and on-off schemes of telephones. I am known for not carrying a mobile phone, because I don’t like to publicly associate myself with criminal organizations, by which I mean, of course, telephone companies. But there is a time of year when I use my little seven-year-old Nokia phone, which looks great in this metadata store. Because every time this phone is used, it is constantly surrounded by thousands of famous hackers.
But for the secret police, smartphones are the best gift they could ever get. It's like Christmas, Hanukkah and Blowjob Day, merged into one big spy orgasm. Their most perfect scenario is very simple - they control the simple exchange of photos, which occurs millions of times a day, they get all the necessary data from it.
Now for the CIA. February 2003, abduction by the American special services of the Egyptian clergyman Abu Omar in Milan. . 25 , , . , . , .

, , , . , . , .
, , , , , . , « », , . . , . , EFF NSA . , , , SIM- , . , , .
, :

, , , - , . , . . . . , , . , , .
-, , , Gmail . , Red Team , , , . — . , .
, . «». , IP- . , ! http https . – , . , SSL , . ? . , PGP , , .
, . – . - : « , Gmail , Google , ». , , Google . .
. : , .

, , , . , .
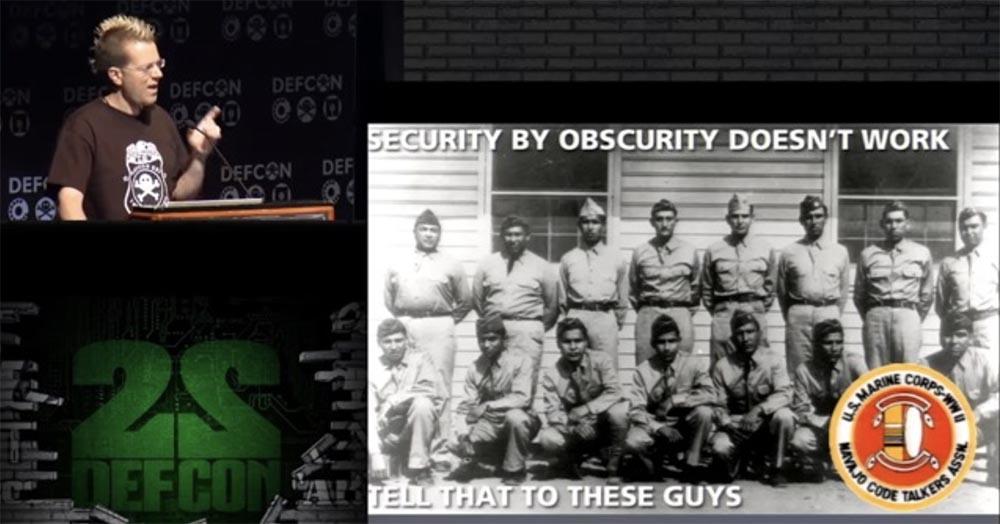
, , , . .
, , , . , , .
. , 2011 . , . , .
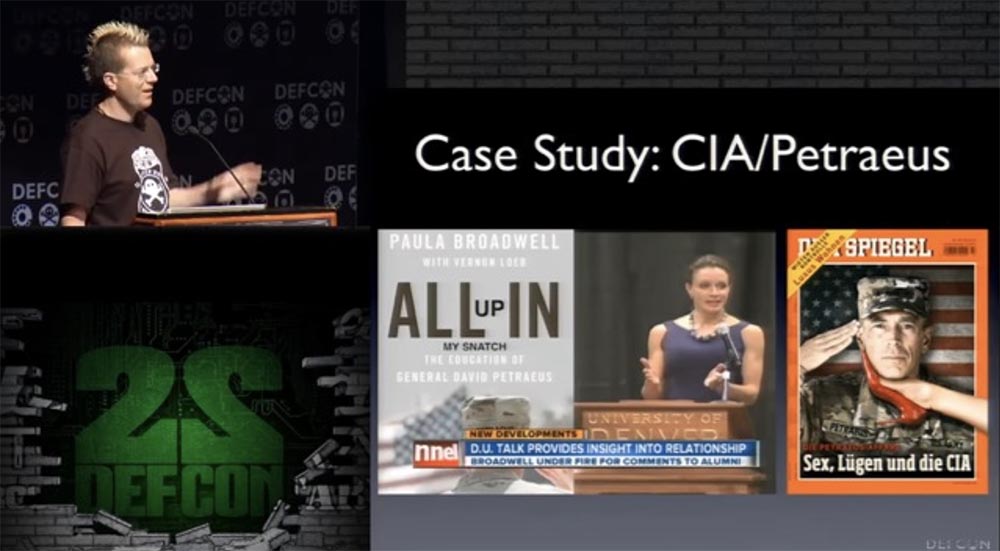
, . . « », , . , , . , «-» - . — , .
- , , : « , ». -, , . Google , . , . , . , : «, …».
, , . .
, «» … - — . . , , . , . , . .
, Darkmail - , . , - .
Skype , . , . 2013 . , , Skype . , , Skype. , PRISM, SIGINT, JTRIG, Pre-MS EOL Skype , . , «». , , . .
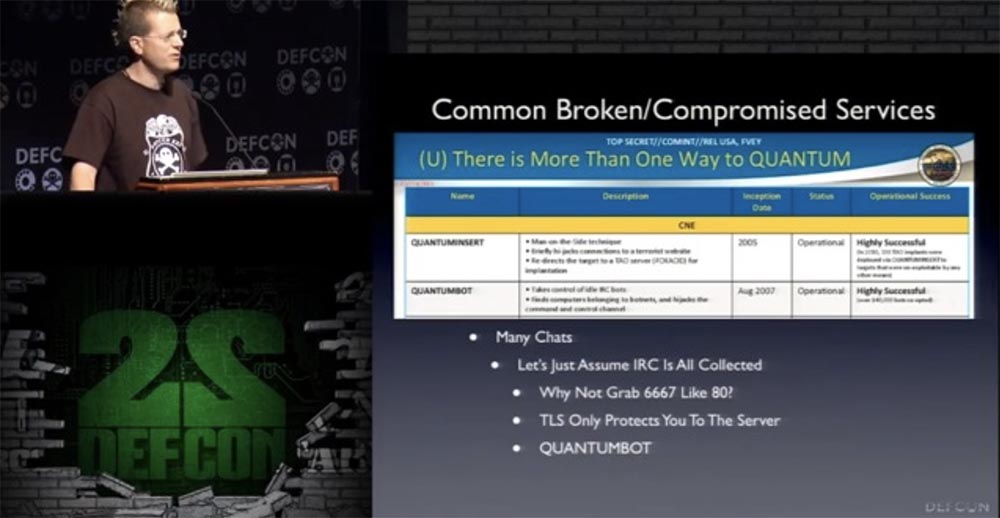
, . 80, 6667. SSL - IFC , , . , IFC IFC Quantumbot . «» 140 000 . , «» Spooks IFC . IFC . -, .
, Google , ? , OTR . « ». OTR . , - . .
, ?
, OTR , , , , . Cryptocat , , «», . .
Bitmessage . 100%, , . - , .
Retroshare , , . peer-to-peer . .
, . , , .
, , . -, , « » Glasshole , .

, , - Glasshole , , .
, , , , . :
!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Use Opsec 24 hours a day, 7 days a week. You see a screenshot from a chat on Reddit with Sabu, already after he became a snitch, in which he advises the other person to use Opsec 24/7. So if the "friends" want to drown you, they can do it. Never before has any federal informer said more truthful words.

')
Another case that we all heard about. A Harvard student who reported an explosion threat during exams. He used Tor to connect to the Guerilla mail service, which allows you to send disposable email messages.
The feds caught him because Tor adds the original IP of the sender to the message header. So Opsec fails in this case. Basically, such nonsense is related to privacy tools with which you are “not friendly.” Therefore, you should have privacy for breakfast, lunch and dinner. She's like bacon that makes everything better!
I'll tell you how this student fucked up. First, the Harvard intranet requires you to register your MAC address . Another reason MIT is better than Harvard is because we don’t require it. So, the user's registration in the network is tied to his MAC-address , in addition, they log outgoing traffic. It is a common microcosm of observation. All this together created threat vectors that allowed this guy to “get it”. For example, investigators could see who went to the site and downloaded the Tor installer just before the threat of an explosion, or to see everyone who was tied to a well-known Tor recording site at the time, or who was accessing the servers in the Tor directory.
When I think about it, I understand that in our country there is already a model of ubiquitous observation, with which everyone is familiar - these are credit agencies. And we are doing a kind of Opsec with credit agencies. We receive credit primarily due to our reputation. Therefore, use confidentiality before taking out a loan. We do not cancel credit cards, even when we don’t need them anymore, because they themselves create our reputation. So don't stop using privacy tools, even when you're done doing something bad. Just like using a credit agency, using Tor can put you on the list. But you have a good reason to be on this list.
So there are many ways that this guy could not spoil everything. To begin with, he at least had to analyze the situation and prepare for the inevitable interview with the police as a Tor user. He could use bridge connection switches to connect to Tor . Although it later became known that the NSA also monitors them. He could have prepared for the fact that the entry point of traffic could be tracked, leave the campus and use the Starbucks café network or a disposable mobile phone, and then, probably, he would not have been caught.
People constantly receive threats of terrorist attacks and bombings, and in fact there are no ways to track such messages. You just have to make your discovery difficult. And, of course, he could use a mail service that did not identify the IP and opened its output Tor node.
What do we know about how vulnerable ordinary Tor users are? It is known that this network caused a lot of trouble to the UK GSHQ government communications center, they even held two conferences on combating Tor , the last one in 2012. So, probably there is not a simple backdoor. This is good news that they should have held such a conference. We know that using Tor is obvious because it forces users to be different from users of open networks. So consider that you have already been fingerprinted.

We know that the attacks on Tor in 2012 were quite difficult for the special services, so they tried to introduce an exploit into the version of Firefox , which is used in the Tor software package. I think this is also a good sign. These are slides from the famous Tor stinks presentation (Thor stinks ...), I am sure that you have already seen it, so I’ll show them quickly.

So, there is a recognition that the feds have never managed to reveal all TOR users. With the help of manual analysis, they can identify a very small number of users; in addition, attempts to reveal users using Tor queries have never been successful.
So you must use Comsec inside your Tor sessions. Of course, they commit traffic correlation attacks, albeit on a small scale. They are trying to discover Tor users at a time when they don’t use them. To do this, they are trying to extract cookies that have been preserved from using this browser. Tor is good because it does not store such cookies. They also recommend using the QUANTUM exploit method, which helps extract cookies from Tor thanks to the presence of Firefox elements.
The above should give you some thoughts about how secure Tor is as the only solution for anonymous Internet use. Never use the only solutions, have a backup option. Using Tor regularly is good, making it difficult to detect, but not absolutely impossible.
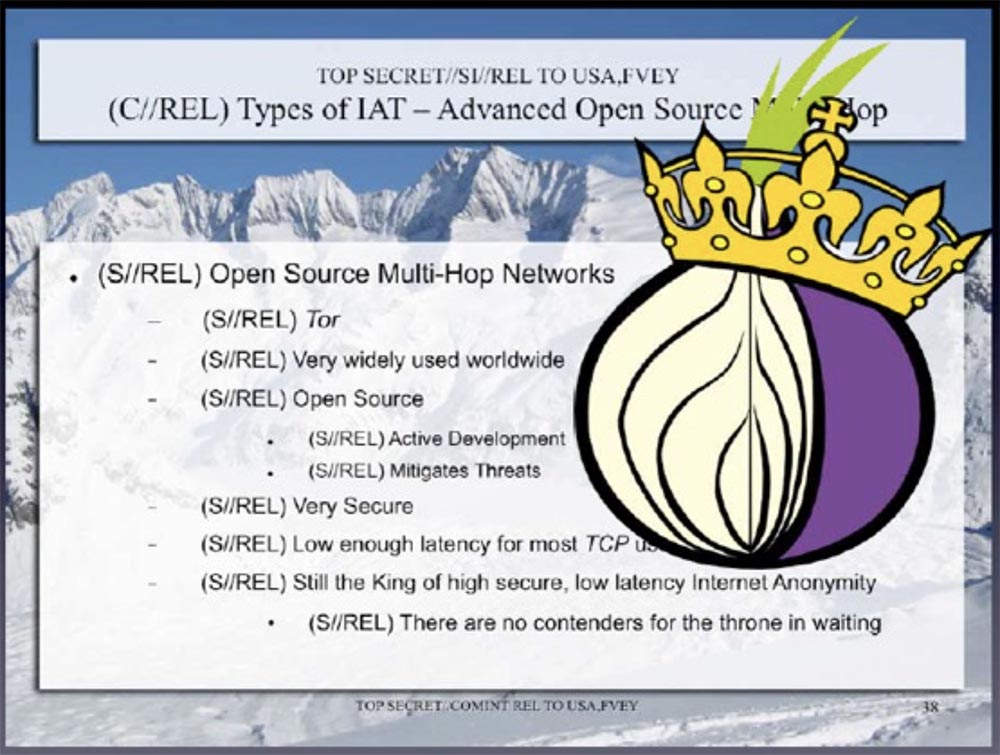
Here is the third secret document, released at the same time. Here, Tor leads in low detection and high anonymity of users.

Here it is indicated that it is widely distributed throughout the world, is an open resource, is actively developing, reduces the risk of threats, is very safe. It says here that “Thor is king in the field of ensuring anonymity and secrecy and in the near future no other contenders for his throne are foreseen.”
The positive feedback from the secret police was received by software platforms used on the client side, such as the fully autonomous Tails software downloaded from the CD.

What does this mean? The fact that Tor puts you in the field of view of the authorities, but Tor and Tails complicate their lives. I think that just using Tor puts you on a rather extensive list of people, and if your “disobedience” will help move you to a smaller list of people deserving more attention, then it’s probably better to be on the big list. Because the more people on this big list, the better.
But never make your life or freedom dependent on one element, one factor of personal security. This also applies to Tor , and many other tools on your Internet communication networks. I like the motto posted on the CryptoCat website - never trust your life or freedom with software. We trust our life to software every day, every time we get into a car or a plane. But when you drive in a car, you also rely on seat belts. It's like an old Muslim saying: “Hope for Allah, but tie a camel.”
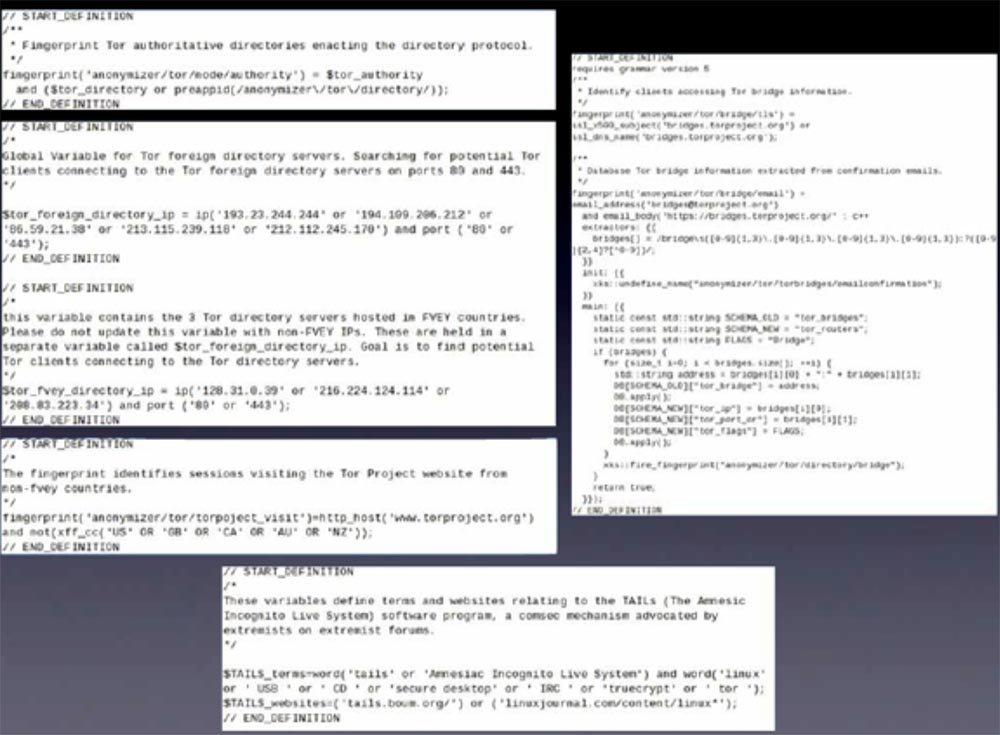
Here's some more good news. A large list and a small list are the recently leaked filtering rules. I know that this is completely unreadable, but basically it shows that the security authorities are obsessed with the idea of making this big list as big as possible.

Anyone who connects to the Tor directory service or to the Tor website is included in this large list. From the point of view of the state, this is the reception of the secret police. It's great. This is akin to finding a needle in a stack, into which we will throw even more hay. Therefore, guys, try to make this big list even bigger to add work to them. They are more aimed at everyone who uses Tor , and not at real criminals, this is stupid, but it is no more than the total surveillance we are talking about. It just proves that we need more people using similar services.
The right side of the slide is worse. I have already mentioned that they collect the email addresses of people who are used to receive "bridge switches", that is, Tor nodes . You should know that they are engaged in such vile things. Thus, a Harvard student might not have been caught using a “bridge switch”. Maybe yes, maybe no. We don’t know for sure, because we don’t know how much information federal agencies and providers share with each other, so just be careful.
Finally, at the bottom of the slide there is evidence that Thor and Tails are being promoted by extremists in extremist forums. So congratulations, it turns out, we are all extremists!
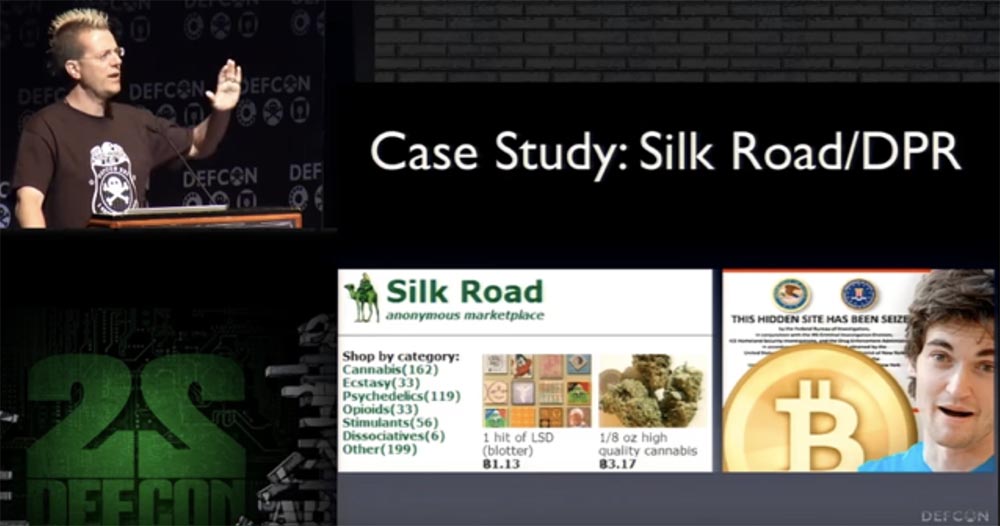
We all know the history of the anonymous Silk Road trading platform and its administrator Pirate Roberts. Silk Road worked as a hidden service Tor for 2 years, until Roberts was arrested.

We know that the feds made hundreds of drug purchases through the Silk Road, allowing him to work longer to make sure that they could arrest someone. It looks like standard organized crime. They arrested Pirate Roberts and at the same time captured all the information on the Silk Road server.
So what made him screw up? We know, Dread Pirate Roberts has repeatedly failed due to the neglect of Opsec - this is both a saved messaging stack and forum posts from the same account that included its real email address. That and the orders of fake IDs with his photos, so that he had enough opportunity to screw it up.

But we do not know how we managed to reveal the anonymity of the server. This is 180,000 bitcoins. How could this happen? We do not know the answer. But there are several options. Pirate Roberts was identified and tracked in the same way that Sabu was tracked down. For example, he could log in only once without Tor , for example, to fix something on the server.
You can not deny this possibility. He could be tracked by financial connections with the provider thanks to tools for tracking payments on all hosting servers, as was the case with other independent hosting providers. They could inject an exploit into the Silk Road server, capture it and break the anonymity mode.
They could also perform a large-scale hidden attack on anonymous services. We do not know the answers, so let's talk about the only way that includes a direct attack on Tor . What you need to know about hidden services is that they are quite vulnerable from the point of view of correlation attacks, since an attacker can offer them to generate traffic. There are two Tor outlines connected around one point. Anyone who connects to Tora for a long time becomes vulnerable to this kind of thing. Especially to switchable segments, because the network is not so great, so sooner or later you will be able to stumble upon a malicious node.
This is not a big problem for the average user, but if you support a long-term project such as a global drug supply company, then it is dangerous. I did not have time to go into details, but I want to show you a piece of research that Biryukov, Pustogravov and Weinman from the University of Luxembourg conducted in 2013, it is called Trawling for Tor Hidden Services: Detection, Measurement, Deanonymization ( services: detection, research, de-anonymization "). They created a chart of popular hidden services Tor, Silk Road and DuckDuckGo , showing the change in the number of requests throughout the day.

The following shows the display of "onion" addresses and their use. Two days and less than one hundred dollars, and they see two examples. There is also confirmation that a certain Tor node acted as a border node of a hidden service to de-anonymize this hidden service, with a probability of 90% within 8 months for $ 11,000. Such studies are entirely within the financial capabilities of state actors. This was made possible thanks to the error Tor , which has already been fixed. This week, Black Hawk told about another similar error that was also fixed. They could detect Tor traffic for hidden services. It was very irresponsible, because now there are fears that the feds can track all the traffic passing through Tor . Thus, if Tor's encryption mechanisms are compromised, people cannot be sure of their anonymity.
The good news is that these things leave traces. There was a surge in the increase in the number of protection nodes at the time when Biryukov and the company were making their incursions into the network. So we can find these errors and correct them, but keep in mind that there are potential attacks on Tor , though not against everyone and not constantly.
I will not talk much about what is shown on the next slide - this is also secret information that concerns the technical analysis of hidden services.

The purpose of the analysis is to collect and compile a list of "onion" addresses, identify similar hidden services based on similar anonymity technologies, and separate hidden services from normal Tor clients. The following is a study of the capabilities of the Amazon AWS cloud service for hosting Tor servers and the British GCHQ toolkit for detecting Tor nodes in Amazon cloud computing facilities, which was mentioned at the Remation II conference.
Remember also about the capabilities of such a tool as the JTRIG Tools , I think its page should have been decorated with DefCon flags.

"Hearing" Spooks use Tor quite intensively, as do English intelligence services. I think the developers of Tor , many of whom I personally know, are subject to the sin of excessive trust. They believe that their activities will not be disclosed, although they do not walk on the hind legs before the state, do not receive handouts from him, and do not leave a loophole in their software for the "hearers".
I think that the key purpose of the special services was not to disclose the entire anonymous network, but only to discover such hidden services as the “Silk Road”. It is theoretically possible for the server to be fully identified and open, because here there is a bidirectional Tor operating scheme, thanks to which Pirate Roberts was captured. Perhaps if he had practiced the use of COMSEC properly , he would not have been caught. So the moral of this story is this: do not launch massive online sales of drugs if you do not have a plan to effectively protect anonymity. For a large organization, maintaining anonymity for a long period of time is a very difficult task. You have to do everything perfectly, and for this you do not need to have the mind of an international cyber-criminal, so that your opponents could not take proactive measures. So find out in advance what the consequences of your activity may be, do a Tradecraft analysis .
Now let's go to the phones. Do not screw it up using cell phones! What does this little Benedict Arnold (the American general of the times of the war for independence of the USA who went over to the side of the British), hidden in your pocket, say?

The phone can betray you in these ways:
- metadata about all your calls;
- information about your location, which mobile operators transfer to federal agencies, as well as geotagging on your photos;
- contact list;
- a list of Wi-Fi networks that you have connected to and are listening in this area;
- unique identifiers such as IMEI , UEID, and so on;
- cookie residues from browsers;
- pure search queries;
- poor encryption. Older devices have weak cryptography, especially on the basis of the OS of mixed versions of Android;
- re-access. Web browsers on these tiny little devices have little RAM and cache, so they continually reload tabs as fast as they can. Therefore, everything that you have done recently, when you were on another network, reboots again;
- automatic connection, which is the best friend of the Pineapple WiFi interceptor. Hello, ATT Wi-Fi , Hello, Xfiniti Wireless , I remember you!
- Any mobile apps, since they suffer a leak of all crap;
- the very image of your life reflected in the mobile phone.
The security agency constantly monitors these kinds of things, especially they watch for the simultaneous presence and on-off schemes of telephones. I am known for not carrying a mobile phone, because I don’t like to publicly associate myself with criminal organizations, by which I mean, of course, telephone companies. But there is a time of year when I use my little seven-year-old Nokia phone, which looks great in this metadata store. Because every time this phone is used, it is constantly surrounded by thousands of famous hackers.
But for the secret police, smartphones are the best gift they could ever get. It's like Christmas, Hanukkah and Blowjob Day, merged into one big spy orgasm. Their most perfect scenario is very simple - they control the simple exchange of photos, which occurs millions of times a day, they get all the necessary data from it.
Now for the CIA. February 2003, abduction by the American special services of the Egyptian clergyman Abu Omar in Milan. . 25 , , . , . , .

, , , . , . , .
, , , , , . , « », , . . , . , EFF NSA . , , , SIM- , . , , .
, :
- ;
- ;
- ;
- ;
- , ;
- ;
- ;
- , , ,
, ; - , , .

, , , - , . , . . . . , , . , , .
-, , , Gmail . , Red Team , , , . — . , .
, . «». , IP- . , ! http https . – , . , SSL , . ? . , PGP , , .
, . – . - : « , Gmail , Google , ». , , Google . .
. : , .

, , , . , .

, , , . .
, , , . , , .
. , 2011 . , . , .

, . . « », , . , , . , «-» - . — , .
- , , : « , ». -, , . Google , . , . , . , : «, …».
, , . .
, «» … - — . . , , . , . , . .

, Darkmail - , . , - .
Skype , . , . 2013 . , , Skype . , , Skype. , PRISM, SIGINT, JTRIG, Pre-MS EOL Skype , . , «». , , . .
, . 80, 6667. SSL - IFC , , . , IFC IFC Quantumbot . «» 140 000 . , «» Spooks IFC . IFC . -, .

, Google , ? , OTR . « ». OTR . , - . .
, ?
, OTR , , , , . Cryptocat , , «», . .
Bitmessage . 100%, , . - , .
Retroshare , , . peer-to-peer . .
, . , , .
, , . -, , « » Glasshole , .

, , - Glasshole , , .
, , , , . :
- ID;
- «»;
- ;
- – , ;
- ;
- ;
- ;
- , .
!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/422793/
All Articles