Hacker found a way to track visitors to competitor sites
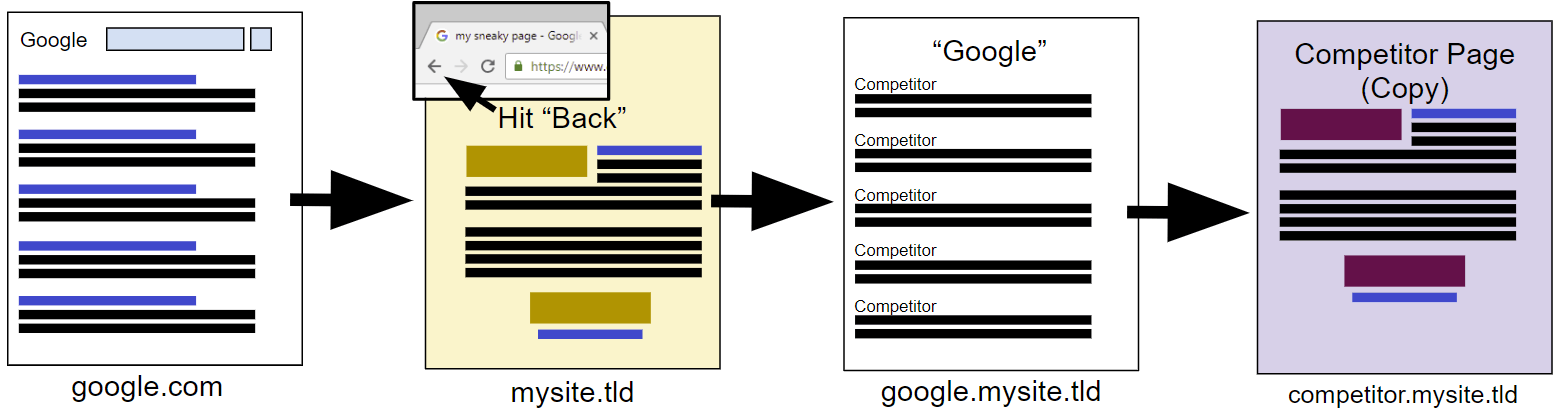
A simple script changes the behavior of the Back button in the browser and replaces the original search results, directing users to hacker-controlled copies of competitors' sites.
Common pattern: open the Google search page and click on different results to find the necessary information. You can open dozens of individual tabs or go to each site in turn, then return to the search results (the Back button in the browser). Dan Petrovich, a specialist in search engine optimization from Australian company Dejan Marketing, figured out how to exploit this pattern to his advantage and to get extensive statistics on visits to competitors' sites, depriving them of traffic.
')
The diagram is shown in the illustration above. Intercepting the traffic of competitors, the specialist can:
- generate heat maps of other sites (clicks, transitions, scroll depth)
- record real sessions (mouse movements, keystrokes)
- receive all the text from the filled-in forms, including the forms for ordering goods
Of course, Dan Petrovich did not do any of the above, because it is a clear violation of the law. Probably, an alternative way of studying competitors' sites, without faking search results, and using the usual cloning of someone else's site - and buying traffic through social media, etc., will be against the law.
The bug in browsers is still not closed, so other attackers can use this method: JavaScript code to exploit the vulnerability is published in the public domain. Actually, it is easy to write such a script yourself, knowing the functionality of the
history.pushState() method for changing the browser history taking into account the referrer.Dan Petrovich notes that he first used this trick in November 2012 . Then, instead of closing the vulnerability, Google manually lowered its page in search results (the page from which it was redirected to fake search results using the Back button). Now, when he re-demonstrated this method, Google acted even harder. Without any notification in the Search Console, his site was removed from the search index entirely .
The hacker admits that in the information security community it is customary to handle the vulnerabilities found differently. They are first reported to the developers and are awaiting bug fixes, and only after the fact they tell about it. Professional pentesters explained in detail to the author how he was supposed to demonstrate this vulnerability in a safe way. But Petrovich acted differently - he showed the scheme on real sites and immediately told everyone. In addition, there are big doubts about the legality of such a hack, even without real surveillance of users, that is, the legality of creating fake copies of other sites and redirecting users there. But over the years, none of the competitors have filed lawsuits, like Google (which is also affected by the fake search results). This is a full-fledged phishing, albeit for demonstration purposes and without malicious intent. That is, the ethical actions of the SEO specialist are questionable.
But the fact remains: over the years, the Back button in the browser is still vulnerable to manipulation. According to Petrovich, other sites also use this technique to spy on visitors on competitors' sites. He thinks that Google shouldn’t exclude his site from the search index, but rather hold a series of events for this old trick to stop working:
- Eliminate the ability to manipulate the Back button in Chrome.
- Automatically downgrading sites that use this trick (and not manually fining him alone). At the moment, Google does not notice these scripts: Petrovich’s experiment went unnoticed for five years and his website ranked high in search results.
- Mark pages with
history.pushState()and search results as “dangerous”.
SSL phrases that are linked to the organization (OV) and with extended verification (EV) partially protect against such phishing, but this is still not a panacea for users inattention.
The experiment of Dan Petrovich showed that now about 50% of users do not find anything suspicious when they are redirected to a fake search results, and then to a copy of another site in the local domain. Many users do not check who owns the certificate and do not read the URL - they are just happy that the browser has a secure connection icon, although it is issued for someone else’s domain. Attackers have long figured out that a secure connection icon increases confidence in a phishing site .
To solve this problem, you can take a number of measures, for example:
- Require user to confirm that
history.pushStateandHistory#replaceState. - Highlight the most important part of the URL in the Chrome address bar, as Firefox does.
- Do not mark HTTPS sites as “secure” because it misleads the user and gives a false sense of security.
- Change the icon of the Back button if it leads to a different address from the previous page.

Source: https://habr.com/ru/post/421501/
All Articles