The art of picking someone else's passwords
In the cult film of the beginning of the two thousandth “Password“ Swordfish ”, a talented hacker needs to pick up a password within one minute. In this he is helped by a friend who carefully holds a pistol at his temple and a temperamental blonde hiding under the table. What if there are no such friends nearby, and you need to pick a password? For example, during penetration testing ...

A small but important warning: if the approach proposed in the article is not used in security testing projects, then your actions can easily fall under Article 272 of the Criminal Code of the Russian Federation (Illegal access to computer information).
In order to come up with an effective password selection strategy, an ethical hacker must try to get into the heads of users and administrators.
What factors influence our choice of passwords?
You can name at least the following three:
- ease of memorization;
- restrictions on the choice of password imposed by the system;
- the number of people using this password in their activities.
What can users easily remember?
Consider the things that are easiest for us to remember:
1) The, that before eyes.
Before our eyes most often appear trademarks of monitors, laptops, computer mice and keyboards, the inscription "password:". It is said that the choice of such a trivial password as “password” by the head of the election campaign of Hilary Clinton had a disastrous effect on the results of the American elections.
2) What is important.
For a person are important:
- pleasant memories and related dates: for example, wedding date;
- relationship: the name of the beloved. Napoleon would choose a cute josephine;
- Property: car make. James Bond would not have changed himself and chose aston, and if he had, he would have changed bmw;
- affection: pet name. Emil from Lenneberg would perpetuate the name of his little friend: svinushok;
- dream: vacation in a particular place. The temperamental girl from the movie would surely choose a wonderful bali;
- Work: the name of the organization or its type. The Lehman brothers would make an unequivocal choice - the bank.
- Hobbies: sports, collecting, music. Well who doesn't love beatles?
3) What the fingers remember:
- geometric shape on the keyboard: qwerty;
- character sequence: 12345678.
4) What is the system / site:
- system name;
- words associated with the business process that it automates. For example, in the summer of 2015, there was a leakage of passwords from users of amateurs going to the left, searching for hot companions and companions through the site Ashley Madison. Among the passwords often come across options like: 67lolita, 68cougar, love69pussies, lovesex.
In 2014, there was a big leak of Gmail, Yandex and Mail.ru passwords. The password lists were analyzed by varagian in the article "Analysis of the lost passwords of Gmail, Yandex and Mail.Ru" and you can see that users choose passwords according to the considered scheme.
How do password protection restrictions affect the choice of passwords by users?
To protect users in many systems, developers have a password policy mechanism, which, unfortunately (fortunately for ethical hackers), is not always used. Consider the limitations and how they are performed / treated by creative users.
Typical restrictions on password policy:
- password length (usually at least 8);
- use of characters in different registers;
- the use of combinations of letters and numbers;
- use of special characters;
- ban on using the previous password.
To come up with a password longer than 8 characters is not difficult, but to use characters in different registers is already difficult, as you need to remember for which character in its password the upper case was chosen. The most obvious and likely solution: choose the first or last character.
If the system forces you to add numbers, then here users are slightly more inventive:
- Add numbers to the beginning or end. As a rule, from one to 4. Accordingly, it can be just one digit, as in the common password “Password1”, if two, then the user will most likely select a year or age, as in the password “68cougar” from our erotic example. If there are three digits, then they may simply be the sequence "123". In case the user wants to add 4 digits, then it will be already a year in full spelling: "Alexander2018".
- Replace the letters with similar numbers: A = 4, E = 3, I = 1, O = 0. Particularly creative users can fully use l33t
In the case of the need to use special characters, users usually use one of the most well-known special characters, as can be seen in the following illustration:
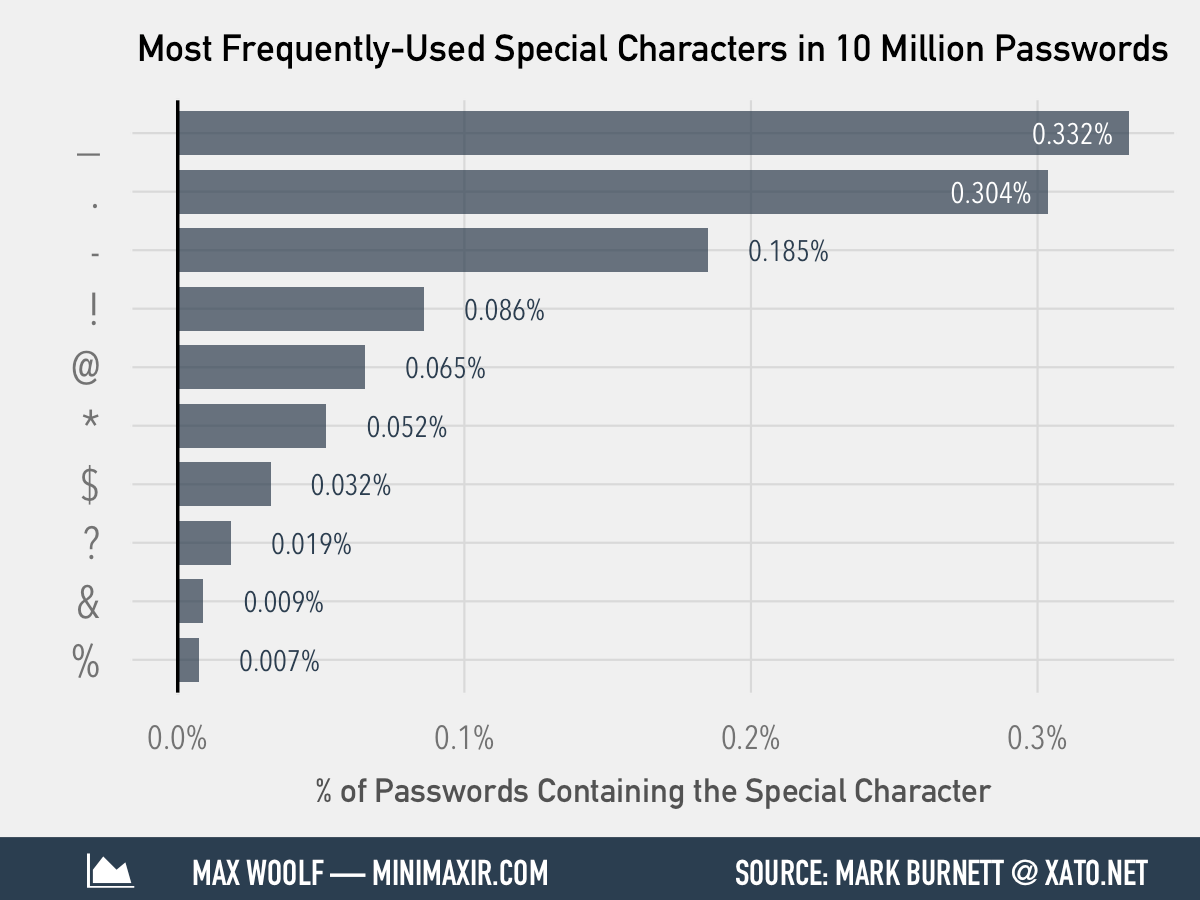
Nothing is as annoying as a ban on using the old password, and users have learned to bypass this restriction by making minimal changes, for example, increasing the number at the end of their password by 1: it was “Alexander2018”, it became “Alexander2019”.
Understanding these small tricks of users, it is quite simple for an ethical hacker to narrow down the list of candidate words for a password.
Number of password users
If the password will be used by many users, for example, system administrators or students in the classroom, then it is usually specifically made not very difficult (for example, coinciding with the account name), and is often left as it was set by the vendor default.
Password selection strategy
Having dealt with the nuances of choosing a password by users, we can develop a password guessing strategy during penetration testing.
Fix the initial conditions:
- Perform penetration testing (purely ethical hacking)
- there are systems with an authentication mechanism for the login-password pair;
- we want to compromise the maximum number of user accounts in the maximum number of systems;
- We consider only online password selection (we do not consider hacking hashes).
Step 1. Determine user account names
To successfully authorize a single password, as a rule, is not enough, you also need to know the name of the account. We will figure out how to get it.
Option 1. Getting a list of accounts using a vulnerability in the system.
For example, a Windows domain controller can be configured to allow an anonymous user to get a list of user accounts.
Anyone can check their domain controller for this opportunity, for example, using the command line utility rpcclient from the “Scanner-VS” :
- Connect to the domain controller and when prompted to enter the password, just press Enter:
rpcclient -U "" ip_domain_address_address - Run the built-in command enumdomusers
rpcclient $> enumdomusers
Option 2. Formation of the list on the basis of “intelligence” and analysis.
User names, even in small organizations, are defined by administrators based on some standard. The most common options are: the first letter of the name + surname: adorofeev, the same, but through the dot a.dorofeev, the full name + surname: alexander.dorofeev. Also, the names of internal accounts often coincide with the e-mail account. Accordingly, the rule of forming a user name can be determined simply by “running” the addresses of employees lit up on the Internet, and a complete list can be generated based on the list of employees that can be obtained from the internal telephone directory, as well as social networks. In a pinch, you can form combinations of the most common first and last names using the most common rules for forming account names.
Option 3. The most common accounts and default entries.
Many systems have default accounts. At a minimum, this is admin or administrator. There are a lot of them in some systems, so in Oracle you can find SYSTEM, SYS, ANONYMOUS, CTXSYS, DBSNMP, LBACSYS, MDSYS, OLAPSYS, ORDPLUGINS, ORDSYS, OUTLN, SCOTT, WKSYS, WMSYS, XDB. Accordingly, it makes sense to look into the manuals of system administrators that you want to test.
Often, there are accounts in the systems that are very easy to calculate, for example, if the company has a training class, then the probability of having a teacher and student accounts is quite high. And how many systems in which, someone did not create an account test?
Step 2. Primary password selection
Understanding which accounts in which systems in the tested IT infrastructure we plan to compromise, we can determine the sequence of systems to attack:
| No | System class | Accounts | Passwords |
|---|---|---|---|
| one | Domain controller | Employee accounts, administrative, typical. | The most common. |
| 2 | Business applications | Employee accounts, administrative, typical. | The most common. |
| 3 | DBMS | Employee Accounts, Administrative, Sample, Default. | The most common, default |
| four | Special systems and services: backup, ftp, etc. | Administrative, default. | The most common, default. |
| five | Active network equipment | Administrative, default. | The most common, default. |
If in the systems account locking is turned on after several unsuccessful attempts (as a rule, the number 5 is chosen), and testing time is limited, and we cannot set a timeout between attempts to reset the counter, it makes sense to run through all users checking the following likely passwords:
- qwerty;
- matching account name;
- empty.
Step 3. Expanding the zone of influence
Having picked up passwords for accounts, the first thing an ethical hacker has to do is log in and see what he has access to.
If access is received to the file system, then the following files should be searched:
- configuration files that may contain information about IP addresses and accounts;
- backup systems, OS images for “rolling in” on new machines. Often, password hashes can be extracted;
- SQL scripts that also often contain useful information.
Selected passwords and accounts for one system need to be checked for others as well, since users, including administrators, like to use the same passwords in different systems.
An ethical hacker to note: in large organizations often there are environments for testing that use data recovered from a not very old backup copy of a combat system database. At the same time, test environments are usually poorly protected, for example, there may be several administrative administrator accounts and simple passwords. Compromising such a system results in testing specialists gaining access to user password hashes, which are often relevant to the combat system.
Tools and dictionaries for online password recovery
The thc-hydra command line utility is a classic tool for online password guessing , and for ethical hackers and administrators who love comfort, this functionality with an intuitive interface is available in our Scanner-VS complex :


Also, a key factor in the successful selection of a password is the availability of well-composed dictionaries, but with this there are problems. Dictionaries supplied with modern domestic security analysis tools do not always contain really useful sets of words. For example, include a standard dictionary distributed with one free utility. The solution, of course, is simple, but not very effective. Is it possible to imagine a Russian user who chose passwords such as: soccer, cutiepie, maganda or mustang. How many on average Russian city of lucky owners of a Ford Mustang? Sometimes they include a great dictionary, based mostly on passwords left by default, but they completely forget about regular users and their favorite passwords.
We decided to correct this annoying situation and compiled our password lists, which are now available not only to users of our Scanner-VS security testing suite, but also to everyone on the website of our solution in the Passwords section :
Password Lists:
Account Lists:
- Custom mens: first letter of the name + surname
- Custom masculine: first letter of name + dot + last name
- Custom men: name + dot + last name
- Custom women: the first letter of the name + surname
- Custom women: first letter of name + dot + last name
- Custom women: name + dot + last name
Conclusion
Hacker from the movie "Password" Swordfish "was lucky and, despite the distractions and the chaotic style of work, he was able to pick up a password and stay alive. Using a structured approach, ethical hackers increase their chances of success in penetration testing and rely less on luck. This approach will work until passwords are chosen by people.
')
Source: https://habr.com/ru/post/420017/
All Articles