Vulnerability in Telegram can compromise secret chats.
Publication for the anniversary of Telegram
The secret telegram chats use “end-to-end encryption”, and so what? End to end encryption Telegram poorly protects user correspondence. A simple example: an attacker got a private key.pgp Alice, of course, to decrypt a message encrypted for Alice, you need a password from this key, which you cannot unlock by adhering to the modern doctrine of password protection. In Telegram end to end encryption on Android - this becomes possible with a probability of 100%. Bypassing two-factor authentication, pin-code recovery and hijacking secret chats in Telegram about this vulnerability will be an article.
In my work, I will try to describe a detailed manual on vulnerabilities in Telegram on Android devices, I will give examples on restoring local code Telegram on Android, Desktop Linux / Windows. I will compromise the secret chat Telegram. In this confrontation with the team of Durov, my company will help me: I (Root); Android 7.0; Android 6.0 (root); Android 4.4.2 (root); PC with OS GNU / Linux / Windows (root). At first glance, it seems the forces are not equal, let's see ...
IMHO. How it all began
In my case, I felt the power of a PR company around the Telegram platform. On the huge wheels of the “Cart”, the hyip rolled from month to month, having neither center nor boundaries. The influence of E. Snowden on the popularization of ubiquitous user encryption of correspondence. Recall the iconic ICQ messenger with its QIP 2005 application on the Desktop, all the correspondence was stored on a PC in open access in the .txt files. Telegram about the encryption of correspondence "who first began to encrypt private correspondence in large quantities" not immediately, but later said that the pioneer was him. The history of Telegram did not stand out in any way: the competition for the security of the MTProto protocol from durov ; Kolyma for artists and painters (drawing stickers); API to create bots / applications; ICO TON, which brought a lot of money to the owners of Telegram; blocking the messenger in Iran, the Russian Federation and again in Iran; as well as the inflow of rare online stuffing Telegram. In July 2018 "The cart sped along for me." When the “next Telegram” appeared on the mass messenger market with its own slogan and a small reservation (this is super fast, easy and free). "Telegram is a messaging application with an emphasis on speed and security." At the expense of the latter in such a steep slogan, durov and his team (at the expense of Nikolai Durov, the technical side of the team is strong) openly interact with security / bug specialists who find / try to find vulnerabilities in the MTProto protocol or bugs on the Telegram platform. Experts send their material to the security@telegram.org mail - this is the official method of such interaction between “head hunters” and Telegram developers, this is also mentioned here.
In fact, we welcome security experts to audit our system and will be grateful for any feedback (security@telegram.org)
The unofficial format of communication, when the letters are ignored by Telegram developers, and then specialists usually post their tweets in the microblogging, where some of them comment on durov .
At the service of the
')
Bypassing the end-to-end encryption Telegram of the messenger on Android, the bug report sent a letter to the above-mentioned e-mail. I received no answer, after a few days I wrote to Telegram volunteers for technical support. Volunteers answered me that they would bring my thought to the Telegram management, asking me for a clarification: from where and when I sent my letter. After two weeks of silence, I once again recalled my letter to the volunteers, this time the messenger volunteers completely ignored my reminder. A week later, I again repeated sending a letter to the official Telegram mail - there is no answer. What remains, what to do? bother with your bug report on Telegram via microblogging ?, besiege unofficial sources of communication team durov ? Or write and post an article for the media? Some kind of cyber bureaucracy was formed in the Telegram ranks. I can not fail to note w9w from habr.com, which, in my opinion, found the best vulnerability on the Telegram platform: vulnerability in telegra.ph. Essence - “any” user could edit someone else’s article on telegra.ph. With his vulnerability report w9w (he found several of them), he was also unable to reach security@telegram.org. After completing the bureaucratic quest, w9w received a small financial reward for the vulnerabilities found. I wonder if this is Telegram greed? or some other reason? Let's return to the Telegram, some reviews about it.

Many people have their own family photo album, the baghunters have their own track record of “found bugs / errors / vulnerabilities”. In my PS, at the end of the work on the article, I will indifferently paint the cell B30 red, thereby leaving my question to the Telegram team open.
Part 1. Restore local code Telegram on Android OS Linux / Windows Desktop. Based on real events
In July in the summer of 2018. On Github, one of the developers of the
The recovery scheme of the local code Telegram is a multi-step process :
Read the salt (32 bytes), encrypted data and sha1 of decrypted data from a file.
Compute a PKCS5_PBKDF2_HMAC_SHA1 on the UTF8 (passcode), using the salt, 4000 iterations, keysize of 256 bytes
Use a Telegram-specific KDF to get the AesKey and AesIV (Relatively cheap - bunch of memcpy and 4x sha1)
Perform an AES-IGE-DECRYPT on the encrypted data using the derived key and IV from step 3.
Compare sha1 of decrypted data with the sha1 read in step 1. If they match - passcode is correct.
For the JTR user, the “bleeding” operation is simplified to a two-step process: using the “telegram2john.py” module, “hash-pull” for the John's processor from the userconfing.xml file belonging to the Telegram application (instantaneous operation) and the brute force of this “hash” using JTR. With such an operation, the probability of recovery of the local code on Android is 100% success, the wait time is several milliseconds. The probability of recovery of the local code on the Linux-Windows Desktop-e is X% success, the waiting time is undefined. Why? Because, firstly, the local code is a normal digital pin code on a four-digit Telegram (10 ^ 4 of all possible pin-a combinations) no more nor less, and secondly, the local code Telegram encryption algorithm on Android is not cryptographic , hence high speed brute force password. The situation is different with Telegram's Desktop applications where there are no secret chats: in the Desktop application, encryption of local code is crypto-resistant (the speed of the Desktop / Telegram hash on the CPU is 10,000 times slower than the Anroid / Telegram hash search speed), and most importantly local code on Desktope / Telegram, you can set "any" length and use any characters.

The cryptographic strength of the local code Desktop Telegram is high, the brute force speed is 10k times slower than the brute force local code Android Telegram.
Personally, I get the impression that Telegram developers worked on creating a unique and secure MTProto protocol, and not on the user's overall confidentiality, for example, an open application cache stored in a non-Android root directory, or non-cryptographic local code, which, as it turns out, recovered with 100% probability.
At the time of this writing, the JTRs from the box in the new OS, Kali Linux and Parrot Security have not been updated since 2015, have bugs that do not allow to parse the local code Telegram (JTR jumbo-1-bleeding always has some bugs, but its functionality develops cooler than you think, if you think about Hashcat software). So, the sophisticated user Kali / Parrot cannot restore the local code Telegram, in Windows / Android the JTRs truncated by functionality are also not suitable. Therefore, you need to install on your OS JTR c Github (for Linux-based systems). In order to successfully compile JTR software, before compiling the program, deliver the package to your OS “libssl-dev”, further
git clone git://github.com/magnumripper/JohnTheRipper -b bleeding-jumbo john && cd john/src ./configure && make -s clean && make -sj4 john/run/telegram2john.py userconfing.xml > # "telegram2john.py" GNU/Linux , : python telegram2john.py userconfing.xml > JohnTheRipper/run/john --mask=?d?d?d?d # – local code Android Telegram . 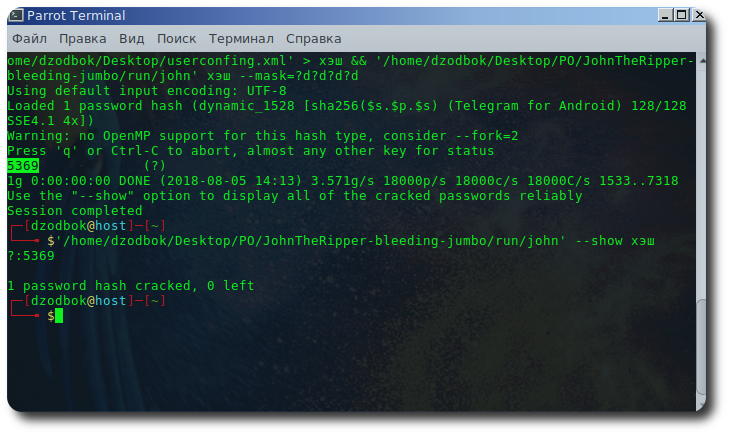
Restored local code Android Telegram. Pin 5369.
Similarly, with the Linux code / Linux desktop application’s local code Telegram, the path to the Telegram directory is specified instead of the “userconfing.xml” file:
(Linux): ~ / telegram2john.py ~ / .local / share / TelegramDesktop;
(Windows): ~ / telegram2john.py "C: / Users / Name / AppData / Roaming / Telegram Desktop" (for the outdated Telegram application on Windows);
(Windows): ~ / telegram2john.py "Telegram Desktop" (for the updated Telegram application on Windows).
Note, if you want to re-parse the local code Telegram, JTR will issue “No password”. The reason - the password has already been found earlier. Johnny, never restores the password on the second and subsequent times, instead, use the “--show hash” option, but sometimes bugs can happen, and the “--show” option will not work as expected (with other hashes I have encountered such bugs, but all have already corrected the developers JTR). In this case, look in the file ~ / run / john.pot, all found passwords are stored in it, if you clear it, you can re-brush hashes with the found passwords.

John The Ripper is not going to re-"dirty hands
The userconfing.xml file , which is a target for JTR, is located under the Android root directory:
/data/data/org.telegram.messenger/shared_prefs/userconfing.xml So you can get to the file with root rights, either through TWRP or using digital forensics.
Detailed video manual for restoring local code Telegram on Android / Linux / Windows link at the end of the article.
Part 2. White starts and loses. Hijack secret chats in Telegram. Also based on real events.
How is Telegram protection based:
- Enter the phone number;
- Receive SMS, or code in the application on another device - if desired, enter the SMS code or the code received in the application on another device.
- Temporary account blocking with frequent (including successful) user login.
When intercepting such a text message, you can break into the user’s account, but you can’t get access to the
Optional, basic + enhanced Telegram protection:
- Enter the phone number;
- Receive SMS, or code in the application on another device - if desired, enter SMS code or code from the application;
- Enter the cloud code Telegram (stored on the Telegram server and in your mind, reset / bind via e-mail);
- Installation of local code (on Android, settings - privacy and security - password code);
- Checking the current / latest sessions of the entrance to the messenger;
- Exit from all sessions except the current one;
- Cleaning the contents of the midrange timer;
- The ban on the screen / screen recording midrange;
- Temporary account blocking with frequent (including successful) user login;
- As it turned out when hijacking the MF (logging into someone else’s account from another ip), a temporary ban of a real / compromised account ~ in 5 minutes and cancellation of the MF in a Telegram. In the same network of real / compromised accounting, Telegram forgets to ban the account hijacking.
Below I will show that the MFs are vulnerable, I’m hijacking one of these MFs (my test account in the Telegram) and will impersonate the user "Master"
After successfully restoring the local code Telegram, I decided to touch the files next to the userconfing.xml file on Android. Created a secret chat, looked at which files and in which subdirectories are updated in time. I tried to copy these files from OS Android 4.4.2 to another gadget with OS Android 6.0 (transfer files between gadgets through the rar; zip archives). Installed with GP the latest version of Telegram on Android 6.0. Transferred from Android 4.4.2> Android 6.0 updated files to similar directories
/data/data/org.telegram.messenger/shared_prefs /data/data/org.telegram.messenger/files /data/data/org.telegram.messenger/no_backup According to the
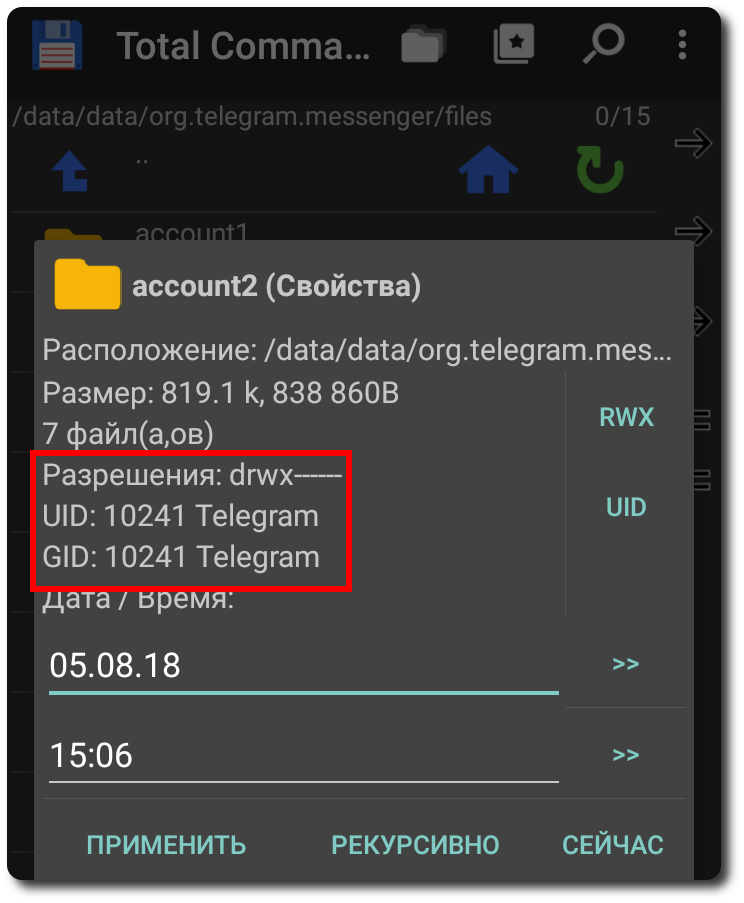
Launched the application. Immediately all the stolen files were updated in time, and the “new user” screen greeted me. Telegram behaved as if I were a new user and offered to login or log in via the phone (standard procedure when Telegram was initially installed on Android). That is, I could not break into someone else's account. Sneaked up more and more times from different sides, but in the end - Fail .
I tried another way - backup Telegram test account via Titanium backup.
I made a backup of the application on Android 4.4.2, I deployed a backup of 4.4.2. on Android 6.0.

You do not need the rights to the “stolen” application, changing the UID / GID - Titanium Bacup will do everything. I launch Telegram of the compromised account on Android 6.0 and the magic! I get a request to enter the local code of the user "Master". Such a middle game with a backup provided a two-factor authentication bypass without victims and frills. Telegram, for its part, requested only the local code from the stolen account. Sending a stolen file
/data/data/org.telegram.messenger/shared_prefs/userconfing.xml on VDS with the installed OS Kali Linux, where JohnTheRipper no longer slept in the running processes, it was time for him to act. The next moment hell hit the local code! Hash could not stand a second, gave a crack.

Red highlighted (top to bottom) received:
- Hash for JTR using the telegram2john.py module;
- Restored local code Android Telegram;
- Johnny full time job (indecent-high speed brute force password, option - - -mask =? D? D? D? D, telling Johnny to pick up the 4-digit numeric code did not turn on, so that the JTR overclocked and showed its
ragespeed); - Request to JTR of the restored local code.
Cool Johnny! is not it?
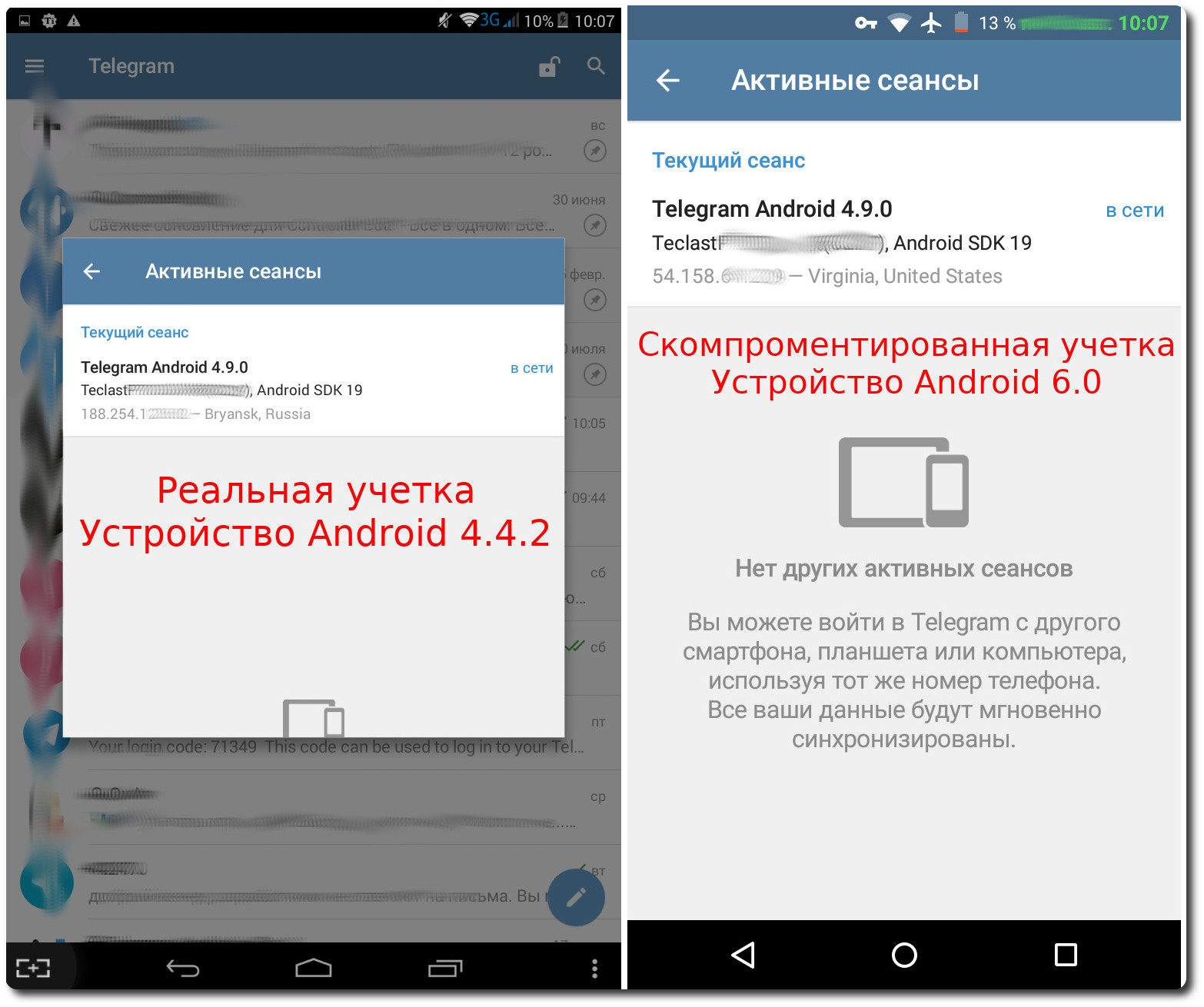
A real user through active sessions does not see that he is compromised. In the history of the last sessions are not recorded entry point of the attacker. Moreover, in the real account of the “Host” I clicked “exit from all sessions except the current one”. The attacker is not thrown out of the session, regardless of the online / offline status of the attacker.
I tried the same operation regarding the compromised account - the result is similar: the “Host” was not thrown out of the Telegram, the session keys are the same. Incredible, yes?
Can graphic keys mean security indicator? The keys of secret chats are not a security indicator, in this experiment they are all three fighting among themselves.
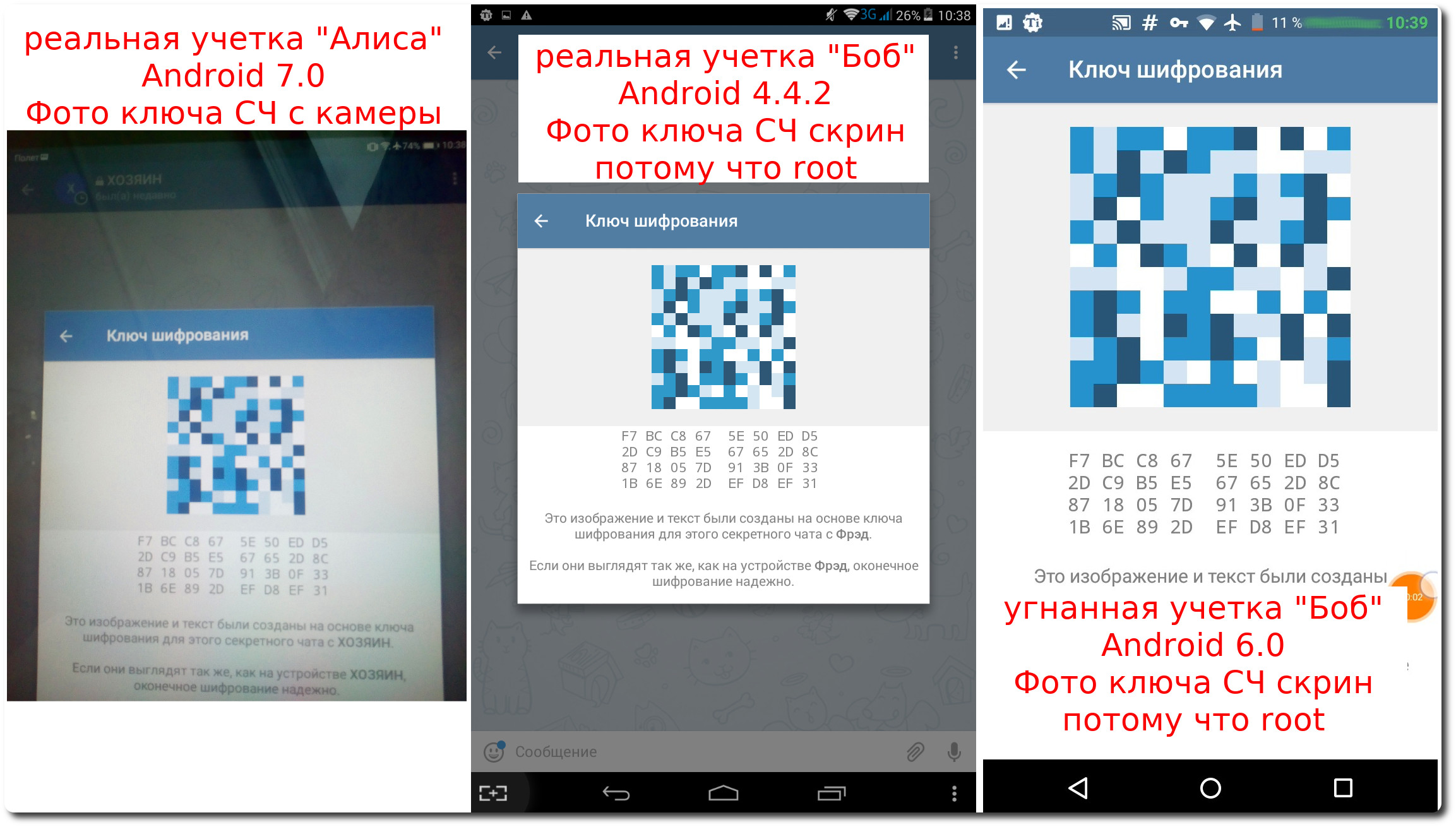
All keys are the same, including the compromised account.
Telegram declares that if keys are beating on 2 devices, you are safe - this is not so. (Retreat. I still need to verify the keys, after installing Telegram on Android and creating the very first midrange, the midrange users lacked key replicas, and the graphic images of the keys differed on the devices. The midrange worked as usual, which I did not understand, and It was an isolated case when the keys did not fight among themselves).
Returned to the first method of "copy-paste", which I initially failed.
I repeated all my previous steps, adding an intermediate 3rd action.
1) Install the latest version of Telegram from GP.
2) Transferred directories from OS 4.4.2 to another gadget with OS 6.0 (transferred only sensitive data. Telegram and its other directories did not copy)
/data/data/org.telegram.messenger/shared_prefs /data/data/org.telegram.messenger/files /data/data/org.telegram.messenger/no_backup 3) Delete the folder on Android 6.0 , check
/data/data/org.telegram.messenger/code_cache 4) I did not restore the rights personally; instead, I distributed “recursive” rights 777 (full access) to all the above directories. I assigned the owner and owner of the group (UID / GID) “Telegram” to the same directories (in fact, “recursively” in the root directory does not work well in TC, so I had to recheck the assignment of rights).
5) Forward! I launch Telegram in another network with another ip - failure, again this greeting of a new user in English.
6) Forward! Restart Telegram, check and checkmate! Telegram issued a warning to enter the user's local code, which was on Android-e 4.4.2 (and which recovers with 100% probability), while there were no requests from Telegram for a cloud code or SMS and is still completely missing. Bypass two-factor authentication, no! End to end encryption Telegram was successful.
Result: the attacker's messages in the MF were also successfully sent on behalf of the real user, and all the MF correspondence was also available. After ~ 400 beats of my anxious heart, the fears were confirmed: the hijacked account was blocked by Telegram from the attacker and from the real user; SC - canceled.
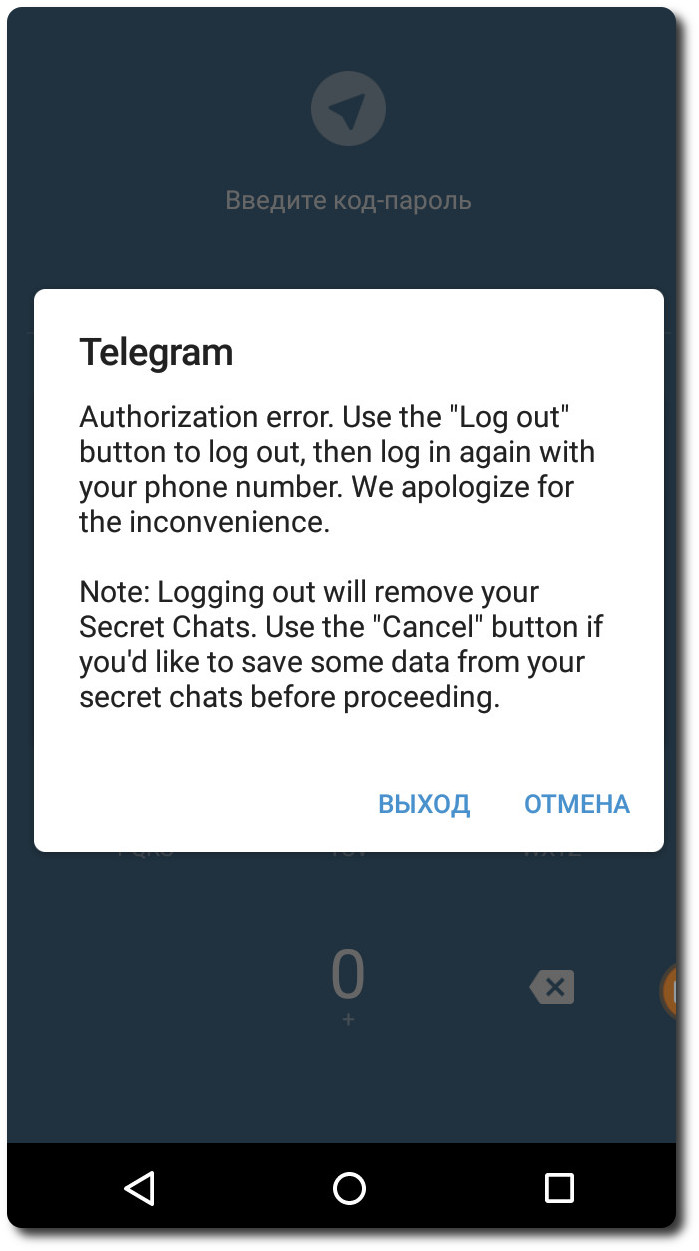
Temporary blocking of Telegram account.
After logging in to Telegram again (sometimes a ban happens for a day, but I was lucky, for some reason all the bans were given out on that day for seconds), the real user had everything as usual, and the attacker couldn’t sniff the compromised account (session keys were updated).
Several telegram approvals I managed to refute
telegram.org/faq - “Midrange can only be on midrange origin devices”.I - "As you can see, the midrange can be not only on devices of origin of the midrange, but also on devices where there is a root key and the midrange, regardless of the Android OS version."
telegram.org/faq - “You can compare this image (note: the image of the MF key) with the one your friend has - if both images are the same, you can be sure that the secret chat is safe”I - “Yes, it is safe, but only in the Telegram-Dubai world”; "You can not be sure that the chat is safe."
telegram.org/faq - “We also recommend that you enable two-step authentication and set a strong access code to block your application, you will find both options in the settings - Privacy and Security.”I - “Strong access code can be set only in Telegram Desktop Linux / Windows applications, but not pin /“ password ”in the Android application”
telegram.org/faq - “A user with root access can easily bypass security functions built into the operating system, read the process memory, or access restricted areas, such as internal storage. Once the attacker has access to the root, any threat mitigation efforts become useless. No application can be called safe in these circumstances, no matter how strongly encrypted. ”I - “Or restore the Android local code and get / clone the account. With each new incorrect attempt to enter a pin, Telegram increases the waiting time between attempts to enter a pin. Apparently, with this algorithm, Telegram is satisfied in protecting the user from manual brute force 10 ^ 4 various pin combinations, but is the user satisfied when it is easy to compromise him? If the Telegram developers would like to mitigate the threats in these circumstances, they could implement this as a temporary lock for a few seconds for incorrect input of the local code, and replace the Android function with the Telegram function with a pin for password, with PBKDF2 encryption - this will slow down the brute attack force. As an example of good protection - the password at the entrance to the encrypted password database Keepass2Android.
telegram.org/faq “You can access secret chat messages from your device of origin. They are safe as long as your device is safe in your pocket. "I - "That's where it turns out to be true!"
findings
- Local code Telegram (pin) on Android is hacked into JTR instantly and with a probability of 100%, this leads to the following consequences: hijacking secret chats, breaking the midpoint correspondence, passing off an intruder as a real user. Protection against this "trick" - a temporary ban from Telegram and new session keys for a real user.
- The operation to steal the MF is similar to theft cookie + hacking pin + "zamochka with rights" if you use the method of "copy-paste".
- To restore Telegram pin on Android, you need to work with the messenger application file located in
/data/data/org.telegram.messenger/shared_prefs/userconfing.xml
You can get to sensitive files with root rights, either through TWRP or using digital forensics. - For an intruder, hijacking a uchetka is an opportunity not only to drop the correspondence, but also an opportunity to cause damage to the real account owner: for example, to clear "your" cloud. In this case, the real user will irrevocably lose their data in the "favorites".
- Often, users put the local code on the Telegram Desktop-e the same as the pin on the Android-e is a trap, 4-digit local code Telegram on Windows / Linux gets <1 minute, and access to a PC is often easier than access to a gadget.
- Telegram developers should replace “pin” with Android with “password”, with crypto-resistant encryption (as implemented on Telegram Desktop-e or in other mobile applications, such as Keepass ...) using PBKDF2, thus the problem will actually be solved.
- security@telegram.org, and in general, technical support in Telegram, as a user-developer service for responding and interacting, is not up to par.
- During the period of "silence", Telegram released an update to the GP, but the update was planned and was related to the Passport telegram, another update also came out, but the vulnerability that I demonstrated in this article is still valid, and anyone can take advantage of it.
- Telegram did not respond to the bug report (the discovered vulnerability). The answer is likely and will not follow.
spoiler

Demonstration of restoring local code Telegram on Android / Linux / Windows.
Demonstration of the vulnerability of Telegram secret chats.
PS: the date / time on individual screens or screen videos may not be the same, as Telegram experiments and screenshots were made as the article was being written, and because of the distribution of bans by Telegram, the article was written for several days.
PPS: in the comments of some users, the root-rights properties are of interest. On many gadgets, users have root (see spoiler), and more tech-savvy users tend to get full root over their device. , GNU/Linux « » (Android — Linux GNU ). Windows «» ? Android- , .
: gpg/pgp , keepassdroid, rar. «» / root . Telegram Android pin, 100% .
...

local code Android-e «password» «pin». ( / ),
Source: https://habr.com/ru/post/419551/
All Articles