Security Week 29. Hacking Reddit, a cryptocurrency wallet and MikroTik routers
 There was no info security last week worthy of a detailed description in the digest. This does not mean that nothing happened - such a situation, it seems, is altogether impossible. Who just did not hack. Well, as compensation for the previous opus about the theoretical network Specter-like attack today we will focus on two real attacks and one circus with horses with the participation of John McAfee.
There was no info security last week worthy of a detailed description in the digest. This does not mean that nothing happened - such a situation, it seems, is altogether impossible. Who just did not hack. Well, as compensation for the previous opus about the theoretical network Specter-like attack today we will focus on two real attacks and one circus with horses with the participation of John McAfee.Reddit hacked is easy. That is, no, not so. Reddit as a rather specific community, and, moreover, quite popular, is surely subjected to absolutely all possible types of cyber attacks and in fact is quite well protected. This conclusion can be drawn both from an absolutely honest story about a recent successful attack, and from the fact that there seemed to be no such stories in the past. The attack was difficult, but it's easy to describe the reason for a successful hack: bypassing two-factor authentication.
Reddit posted a detailed description of the incident (captain!) On Reddit . Here you can read the retelling in Russian. Employees of the company became aware of the attack on June 19. From June 14 to June 18, attackers had partial access to the organization’s internal infrastructure by hacking several employee accounts. All accounts that have access to important information were protected by the 2FA system, but it was managed to be circumvented using SMS interception.
Details of this interception are not disclosed, although a note on the site Wired suggested that there was a issuance of a duplicate SIM card. Such an attack could be detected quickly as well, especially if several accounts were hijacked. Anyway, hackers got partial access to cloud storage. There they accessed the database with logins, addresses, and salt-hashed passwords of Reddit users until 2007 (Reddit was launched in 2005). All messages from users, including private messages, were also stored there, but only in the first two years of the site’s existence.
')
Thus, early Reddit users suffered the most. In addition, access to the mail server logs was obtained. From them you can find out who received the mailing list of the site from June 3 to 17, 2018. The problem is that using these logs you can associate the username on Reddit with the email address: this information can be used later - for example, for phishing attacks. What was done? Measures have been taken to prevent re-attacks, including the transition to two-factor authentication using physical tokens. Thanks to authorization using tokens since the beginning of 2017, Google has not recorded a single successful phishing attack.

200 thousand MikroTik routers are infected with a miner
→ News
In April of this year, zero-day vulnerability was discovered and closed in MikroTik routers. The error in the implementation of the Winbox remote control system made it possible to retrieve a user database in which there was enough information to gain complete control over the router. Vulnerability at that time was already exploited by hackers, but the scale of the attack was small. A patch covering the problem was released within 24 hours, but everyone knows how quickly the owners of routers, even professional ones, update the software.
Last week, the BleepingComputer website gathered information from three different sources and counted up to two hundred thousand Mikrotik routers hacked using the April vulnerability and embedding the miner code of the Coinhive cryptocurrency into web pages. That is, all users connected to the hacked router begin to lease their computing power for mining. The attack works in both directions: if a website is hosted “behind the router”, its visitors also receive a harmful load in the site code. In some cases, the miner code was inserted not into all web pages, but only into those generated by the router itself, for example, an error message about access to the site. The Shodan IoT search engine indexes 1.7 million Mikrotik routers visible from the network. Based on this figure, it can be noted as a fairly significant proportion of already infected devices, and the possibility of expanding a cryptocurrency botnet.
Saga of unbreakable cryptocurrency wallet
Okay, this is not a saga, rather an anecdote. Any sphere of national economy becomes more fun if John McAfee participates in it. On July 27, the founder of McAfee Security, who recently switched all its attention from information security to cryptocurrency, announced a reward of $ 100,000 for breaking into a Bitfi cryptocurrency wallet.
The Bitfi wallet is advertised as an absolutely safe, but also convenient device for storing and working with cryptocurrency access keys. And John McAfee himself is actively promoting Bitfi as an absolutely unbreakable device, hence the reward. McAfee’s statement caused, let's say, increased frustration among the community of security experts - for two reasons. First, to say that something is impossible to crack is a moveton. Secondly, the conditions proposed by the manufacturer of Bitfi wallets are far from the standard Bug Bounty program. Participants are invited to buy Bitfi with a key filled with it, giving access to money. If this key can be stolen, both the “stolen” cryptocurrency and one hundred thousand dollars from above are relied on as a reward.
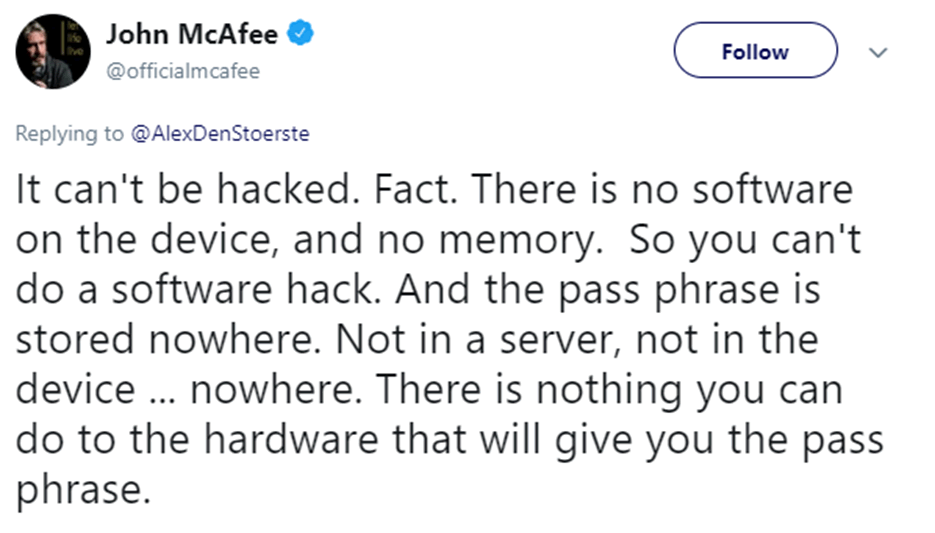
But real security is nothing to do with it! You can encrypt the data, put it on a USB flash drive, and without a key, no one will decrypt it. The bottom line is how reliably the device works in practice when secret data is accessed. Is it possible to intercept the secret during the transfer? Is it possible to steal a pin code to access the wallet? In theory, it is necessary to answer the question of how the device will work in real conditions, and not how well encrypted crypto money will lie on it.
Not that John McAfee and Bitfi as a whole have stopped it. A couple of days after the announcement, the reward for breaking the wallet was increased to 250 thousand dollars while maintaining the conditions. On the claims of researchers from the company PenTestPartners twitter Bitfi accused them of working for competitors. In response, PenTestPartners bought the device and disassembled it. Inside, a slightly trimmed MediaTek smartphone platform with a modified Android was found, with all the built-in “almost” backdoors typical of a cheap Chinese smartphone. When an independent Dutch researcher found a fairly simple way to get superuser rights on a device, the issue of wallet security could be considered closed. But Bitfi did not give up:
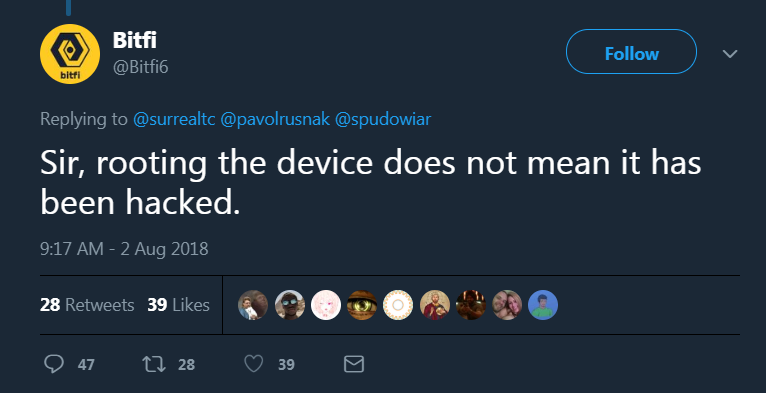
So we have a device that does not have software and memory. That the rights of the root do not allow to hack the wallet. We must pay tribute: at some point Twitter Bitfi apologized for the behavior of some of his employee responsible for tweets, stopped responding to everyone using the “fool himself” pattern, but it didn’t get any better. At the time of publication, the story continues to evolve: researchers disassemble the cryptographic network and find new problems, Bitfi and McAfee ride on the HYIP trolley in a circle.
All this, of course, is incredibly ridiculous, if it were not a little sad to lower the quality of the discussion on security to the level of a rural disco. The standards of security devices, from cryptographic walks to smart locks and cars, are not specifically defined by anyone. Although the majority of those involved in information security observe the standards of decency, sometimes such “unbreakable” wallets, “super-reliable” locks and other fruits of marketing fantasies appear. However, the reality usually puts everything in its place.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/419425/
All Articles