Mikrotik RoMON Guide
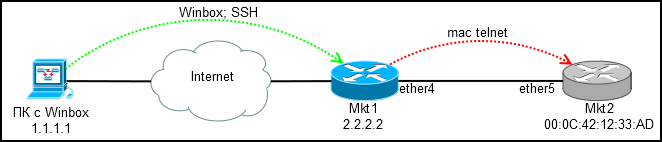
Everyone had situations when it was necessary to set up remote equipment (sometimes new), and access was only available to other network devices, no PCs / Laptops and users with phones. In the case of Mikrotik, this problem can be solved in two ways: Mac-telnet and RoMON embedded in RouterOS. About them will be discussed below.
Mac Telnet from router
For those who have forgotten: Mac telnet works on Layer2, so the connection is possible within the same network segment.
')
We connect via winbox or ssh to the configured router (Mkt1) and through it via mac-telnet to the new (Mkt2).
Where to find mac-telnet:
* [IP] -> [Neighbors] - if neighbor detection is enabled
* [IP] -> [ARP] - if there is some ip on the new router and it is resolved in mac
* [Tools] -> [Telnet] - here besides mac-telnet there is the usual telnet and ssh
* / tool mac-telnet - from console
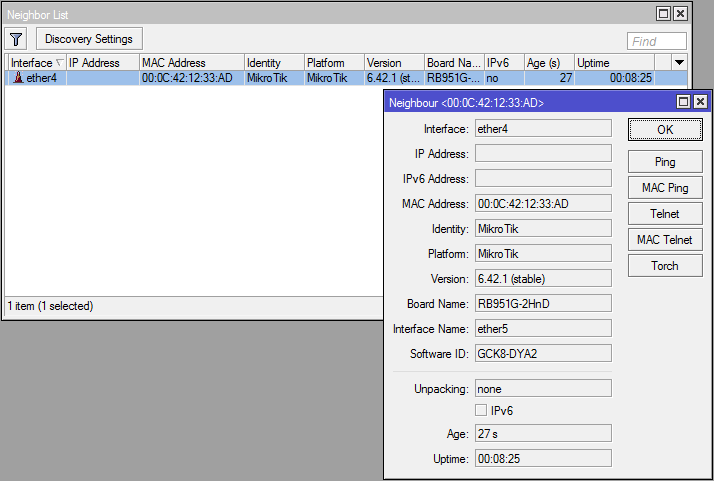
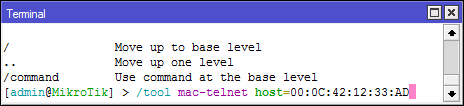
What is worth remembering: if the default configuration is present on the device, then mac-telnet will only be available on lan ports (all except ether1, usually), so you clearly tell installers where to connect the cable, otherwise no mac-telnet and RoMON will help you.
Access is, you can customize, but you want convenience? Especially when setting up queue trees and a large number of firewall rules.
Connect via RoMON
RoMON (Router Management Overlay Network) - Ability to use one mikrotik device that is accessible via ip as a transit for connecting to a device via mac.
RoMON is disabled by default . The client part is built into the winbox, so you do not need to reinstall anything.
Setup on a transit router (Mkt1):
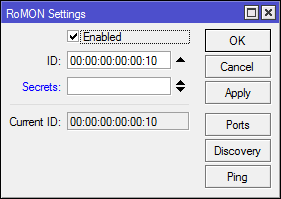
[Tools] -> [RoMON]
* Enabled - Enable RoMON
* ID - Manual installation of RoMON ID, one of the mac addresses of the router is selected by default.
* Secrets - A set of passwords for RoMON authentication, used if the port password is not explicitly specified. The wiki has a detailed password selection procedure.
[Tools] -> [RoMON] -> [Ports]
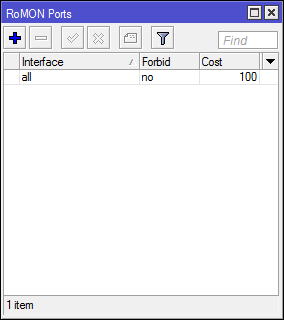
By default, ALL ports are turned on, which is not very safe and it is not possible to disable all, so we set Forbid = yes to it , more precise rules for interfaces will block all.
Create a rule for ether4:
* Interface - the port for which we make settings
* Forbid - prohibit the work of RoMON on the interface
* Cost - taken into account when building a path in large Gerland
* Secrets - Set passwords for authentication.
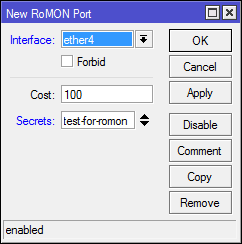
Console option:
Setup on a remote router (Mkt2):
Here we have a mac-telnet connection, so the settings will be console:
Now in [Tools] -> [RoMON] -> [Discovery] on Mkt1 we see a neighbor:
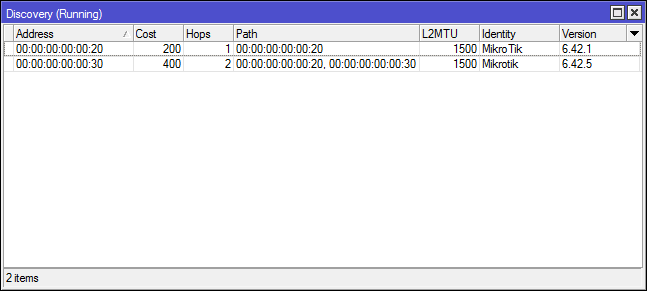
And one more neighbor who is connected by transit through Mkt2, I leave the setting of this connection as an independent task, everything is the same.
Connection
We start Winbox and connect to 2.2.2.2 in RoMON mode using a regular account and password, the secrets in RoMON refers only to communication between routers:
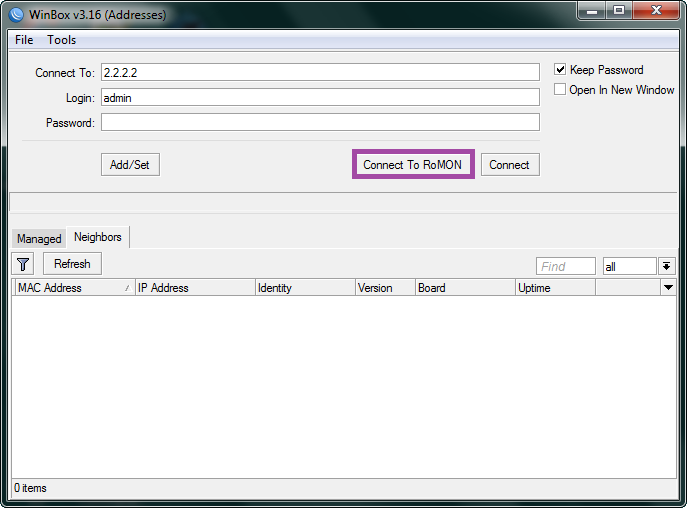
And here we see the most interesting - all the routers in the RoMON chain are available for connection through the only transit Mikrotik.
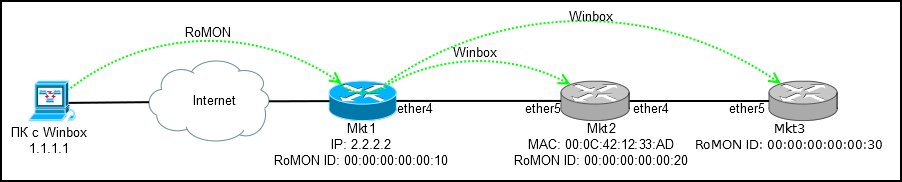
We select one of the addresses (RoMON ID) and connect to the router of interest.
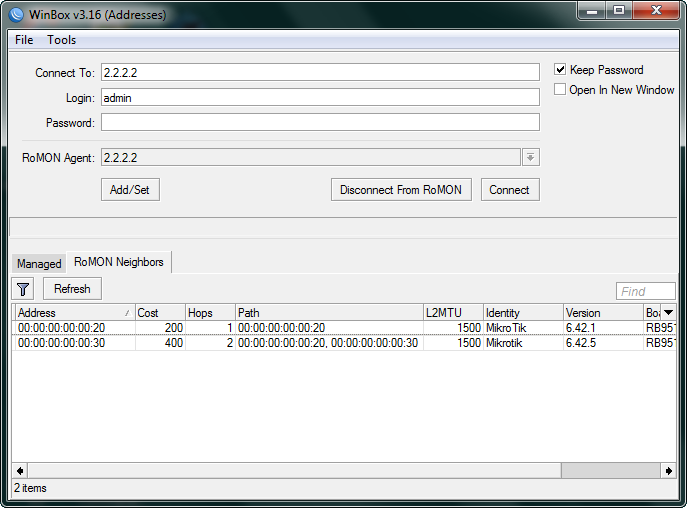
Bottom line: We get transparent access to all routers in the chain, without the need for a consistent login via mac-telnet.
Additionally
[Tools] -> [RoMON] -> [Ping] - utility for ping routers by RoMON ID.
Regular mac-telnet is not a secure communication channel, if you have RoMON, you can establish an ssh connection by RoMON ID.
Connection via RoMON in command line mode (for shortcuts):
That's all. The functionality is not for everyday use, but it is useful to remember and know how to configure it.
Mac Telnet from router
For those who have forgotten: Mac telnet works on Layer2, so the connection is possible within the same network segment.

')
We connect via winbox or ssh to the configured router (Mkt1) and through it via mac-telnet to the new (Mkt2).
Where to find mac-telnet:
* [IP] -> [Neighbors] - if neighbor detection is enabled
* [IP] -> [ARP] - if there is some ip on the new router and it is resolved in mac
* [Tools] -> [Telnet] - here besides mac-telnet there is the usual telnet and ssh
* / tool mac-telnet - from console


What is worth remembering: if the default configuration is present on the device, then mac-telnet will only be available on lan ports (all except ether1, usually), so you clearly tell installers where to connect the cable, otherwise no mac-telnet and RoMON will help you.
Access is, you can customize, but you want convenience? Especially when setting up queue trees and a large number of firewall rules.
Connect via RoMON
RoMON (Router Management Overlay Network) - Ability to use one mikrotik device that is accessible via ip as a transit for connecting to a device via mac.
RoMON is disabled by default . The client part is built into the winbox, so you do not need to reinstall anything.
Setup on a transit router (Mkt1):
[Tools] -> [RoMON]
* Enabled - Enable RoMON
* ID - Manual installation of RoMON ID, one of the mac addresses of the router is selected by default.
* Secrets - A set of passwords for RoMON authentication, used if the port password is not explicitly specified. The wiki has a detailed password selection procedure.
[Tools] -> [RoMON] -> [Ports]
By default, ALL ports are turned on, which is not very safe and it is not possible to disable all, so we set Forbid = yes to it , more precise rules for interfaces will block all.
Create a rule for ether4:
* Interface - the port for which we make settings
* Forbid - prohibit the work of RoMON on the interface
* Cost - taken into account when building a path in large Gerland
* Secrets - Set passwords for authentication.



Console option:
/tool romon set enabled=yes id=00:00:00:00:00:10 /tool romon port set [ find default=yes ] forbid=yes add disabled=no interface=ether4 secrets=test-for-romon Setup on a remote router (Mkt2):
Here we have a mac-telnet connection, so the settings will be console:
/tool romon set enabled=yes id=00:00:00:00:00:20 /tool romon port set [ find default=yes ] forbid=yes add disabled=no interface=ether5 secrets=test-for-romon Now in [Tools] -> [RoMON] -> [Discovery] on Mkt1 we see a neighbor:

And one more neighbor who is connected by transit through Mkt2, I leave the setting of this connection as an independent task, everything is the same.
Connection
We start Winbox and connect to 2.2.2.2 in RoMON mode using a regular account and password, the secrets in RoMON refers only to communication between routers:

And here we see the most interesting - all the routers in the RoMON chain are available for connection through the only transit Mikrotik.

We select one of the addresses (RoMON ID) and connect to the router of interest.

Bottom line: We get transparent access to all routers in the chain, without the need for a consistent login via mac-telnet.
Additionally
[Tools] -> [RoMON] -> [Ping] - utility for ping routers by RoMON ID.
Regular mac-telnet is not a secure communication channel, if you have RoMON, you can establish an ssh connection by RoMON ID.
/tool romon ssh <romon id> Connection via RoMON in command line mode (for shortcuts):
winbox.exe --romon <RouterIP> <RoMON ID> <user> <password> That's all. The functionality is not for everyday use, but it is useful to remember and know how to configure it.
Source: https://habr.com/ru/post/419149/
All Articles