How to buy the illusion of security in the form of children's smart watches
This story is about how I wanted to make my child's life a little safer with the help of new technologies and what came of it. Although the title, I think, you already guessed what it was about.
Approaching September 1, and I, as the father of the future first-grader, wondered how to make the first days of my children in school pass as calmly as possible both for him and for my wife and me.
I think that there will be no person who has not heard of such a new gadget as a children's smart watch. The market is simply flooded with numerous versions of devices, usually made in China. Prices and functionality of these devices vary, but the best of them include such a wide range of functions, such as a phone, GPS tracker, messenger, camera, pedometer, and of course the clock. According to the manufacturers, this gadget was created specifically for children and includes child safety devices. So I thought, so I began to choose the appropriate option on the Internet. As a result, I bought a FixiTime 3 watch from Elari .
The functionality of this watch was impressive:
- GPS / LBS / Wi-Fi Tracking
- 2 cameras, access to the camera clock from a connected smartphone
- support incoming and outgoing voice calls, including hidden
- voice chat
- pedometer
- Well, and Fixiki inside, as without them

All this rich set of watch capabilities convinces parents that they get, if not full, then sufficiently substantial control over their child. But, on the other hand, devices with such functionality must reliably protect the data of their users. Moreover, such users are children. It is terrible to imagine what can happen if an attacker gains access to the child’s device and is able to monitor it.
Tormented by such thoughts, I decided to check how safe is the use of the hours I bought.
After I installed the Elari SafeFamily app from the Apple Store and added a clock to it using QR code, I ran Fiddler on a laptop and started analyzing traffic. The application sent data to the server http://wherecom.com . The first thing I noticed was that the usual HTTP protocol was used, there was no traffic encryption, neither HTTPS nor SSL Pinning . I had a worrying thought that this would not end the matter.
So it turned out. Continuing to analyze the requests and replacing the parameters in them, I discovered the first vulnerability. So, request at
http://api.wherecom.com:8099/umeox/api/holder/detail.json?holderId=111111&monitorId=222222 : , , , , , , , — QR . , , . , monitorId , .
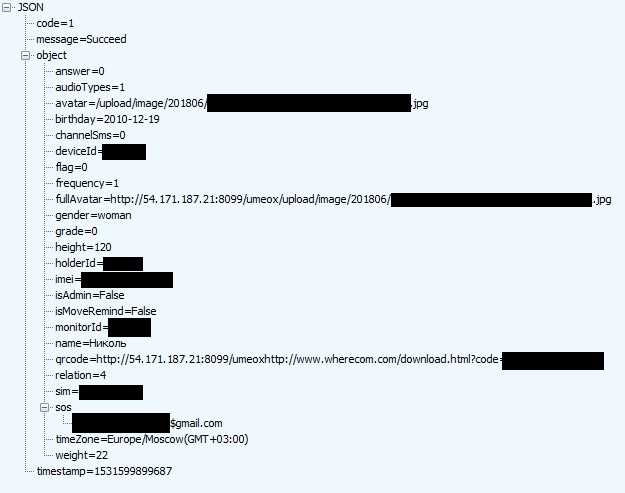
, , .

, , , GPS , (, , ). QR . , QR , , . , .
, , API , .
, , , , , . Elari, , Wherecom.
, , phpMyAdmin, phpinfo.
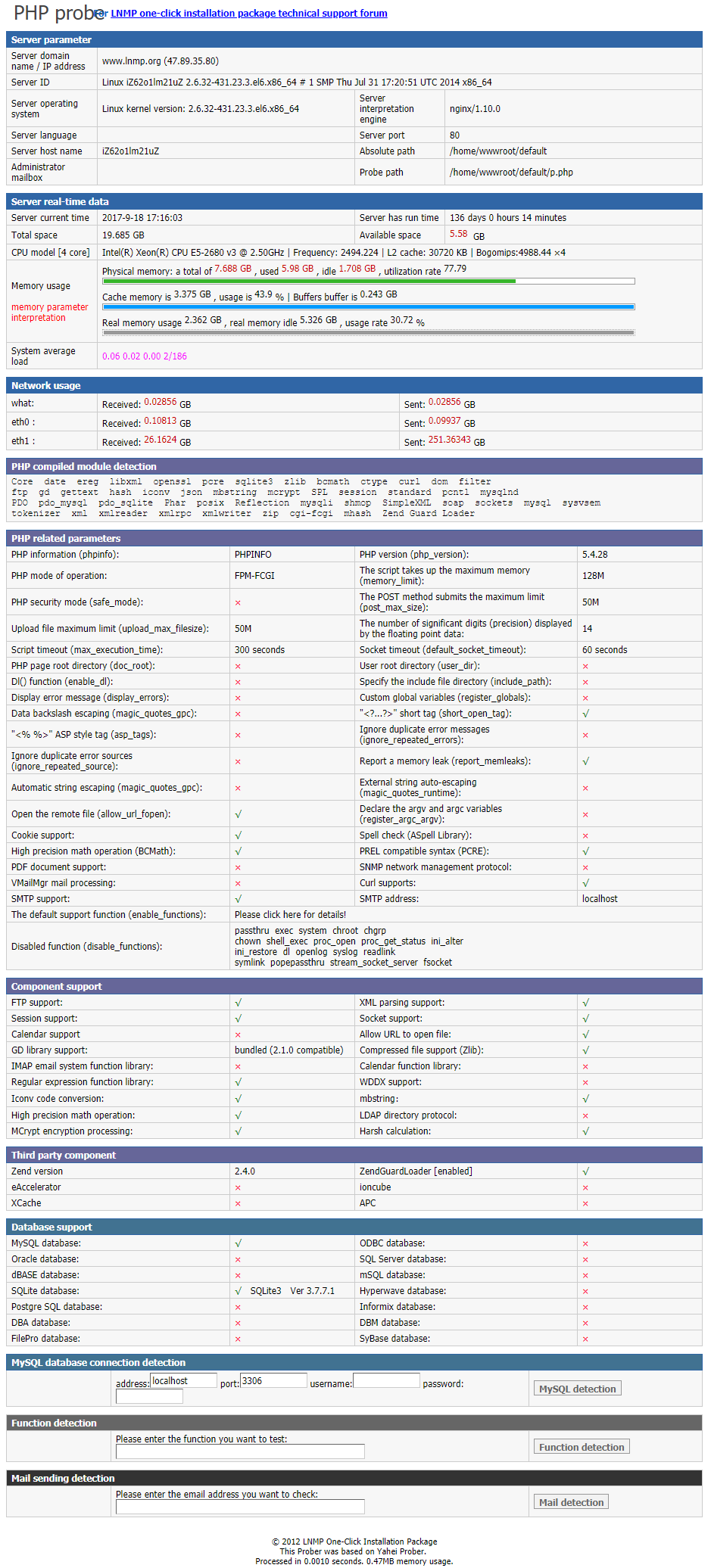
. , , . , , ? , . , , , .
, , Wherecom technology limited. , , Science & Technology Development Institute of China. , , , , . , , , . , .
, . Elari. , , .

Wherecom, . Facebook Wherecom, -, Linkedin Wherecom. , , , .
. API. , - , .
, , , HTTPS SSL Pinning . , . , . . .
Upd. 04.09.2018
HTTPS, SSL Pinning .
')
Source: https://habr.com/ru/post/418851/
All Articles