Bug Bounty Kyivstar: reward for admin access to Jira, AWS, Apple, Google Developer, Bitbucket services - $ 50
The story of coincidence, luck and reward.
Two years ago, a dinikin user wrote a post about how he found a vulnerability in the personal account of Ukraine’s largest mobile operator, Kyivstar. The vulnerability allowed to add to your account without verification any Kyivstar phone number and fully manage it:
The vulnerability was closed, and the author, in gratitude, waspaid a huge premium by connecting 4,000 megabytes of Internet for 3 months.
')

Later, habraprzovatel rewiaca in his post " Why in Ukraine there are no white hackers or history of hacking Kyivstar " described the situation with such a generous reward more emotionally.
Vitaly Sultan, Soultan , Chief Digital Officer of Kyivstar was noted in the comments then, promising to launch soon in the Bug Bounty company.
And now, after almost two years, Kyivstar announces the launch of its own Bug Bounty program. One of the first phrases in the announcement was as follows:
And in the evening I found in my Spam folder a letter from Kyivstar domain with an HTML attachment.
And here begins the most interesting.
Despite the fact that the sender's name coincided with the name of the employee who answered my previous request on the Bugcrowd platform, the e-mail came to the wrong box that was used for registration.
After checking the attachment for viruses, opening it with a notepad and googling the sender, I still could not believe such a coincidence: these were bookmarks from the browser of the working computer of the Kyivstar employee.
Ukraine’s largest mobile operator was lucky that a letter with an attachment of the form “Bookmarks_July.2018.html” didn’t get anywhere (sorry for tautology), but to someone who understands the value of such data and the consequences of losing it.
There were 113 bookmarks in the file. And among the various links, both for work (which did not open from the external network), and not very much, there was one, which opened my eyes to five kopecks.
The link led to an unprotected file, in which, among other things, were the following columns: "URL of the service", "Login" and "Password":
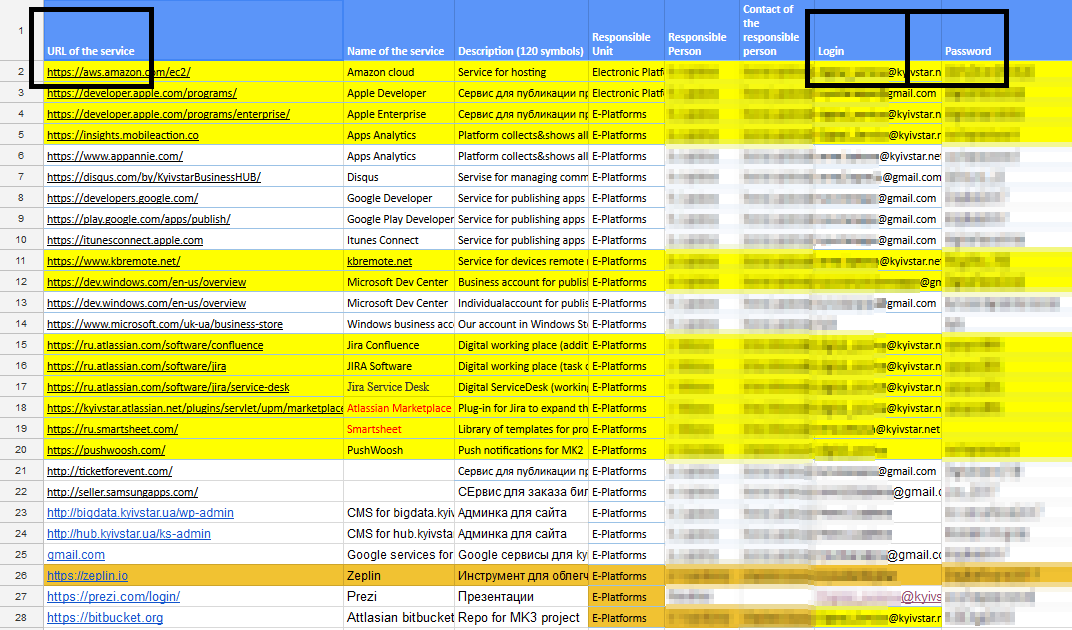
(to enlarge the image, open it in a new tab)
Once again, I thought, is it a fake, not a honeypot , I tried to enter several of the services, waiting for a barrier in the form of two-factor authentication. But she was not there, and I entered. Logged in as admin:
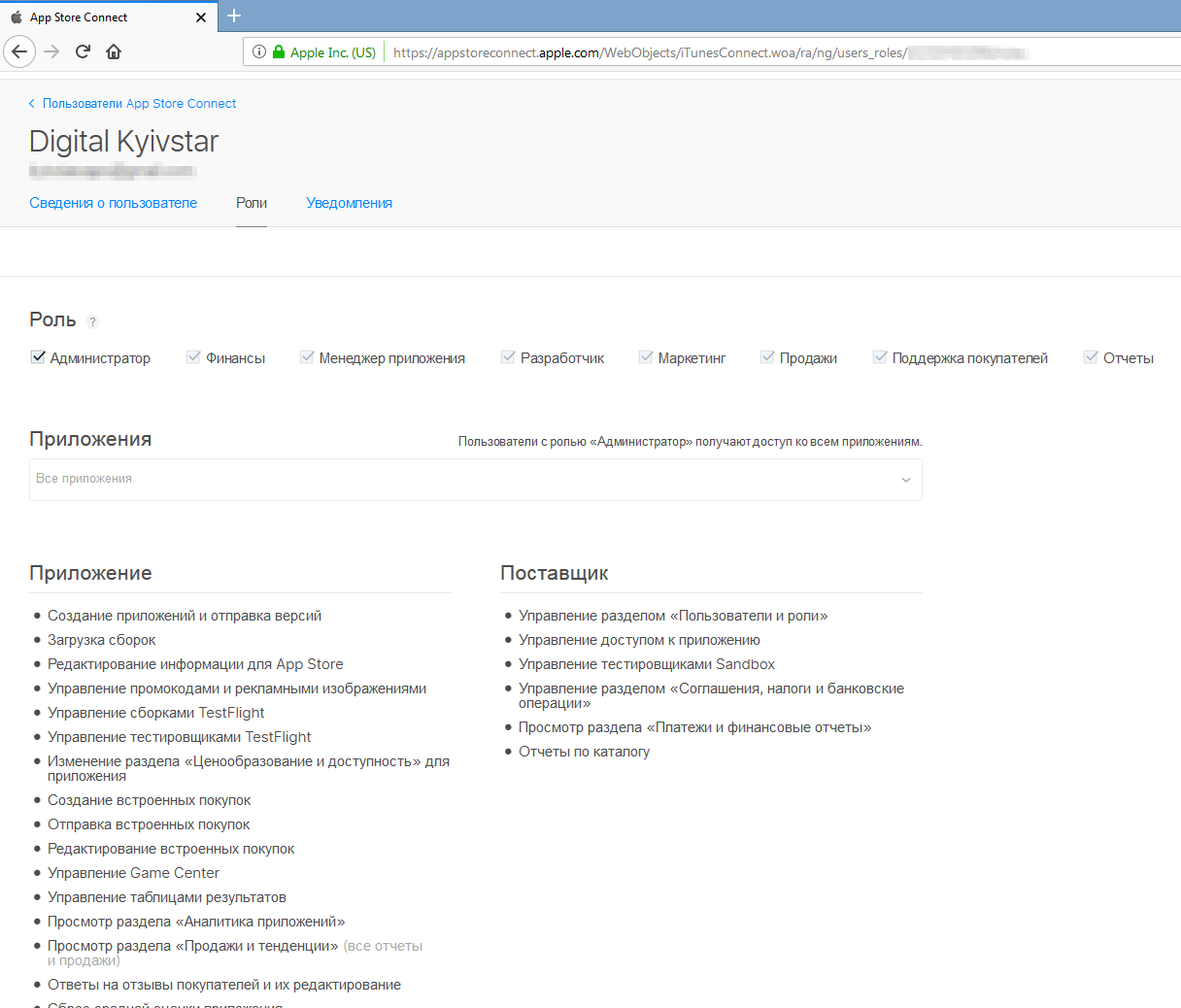

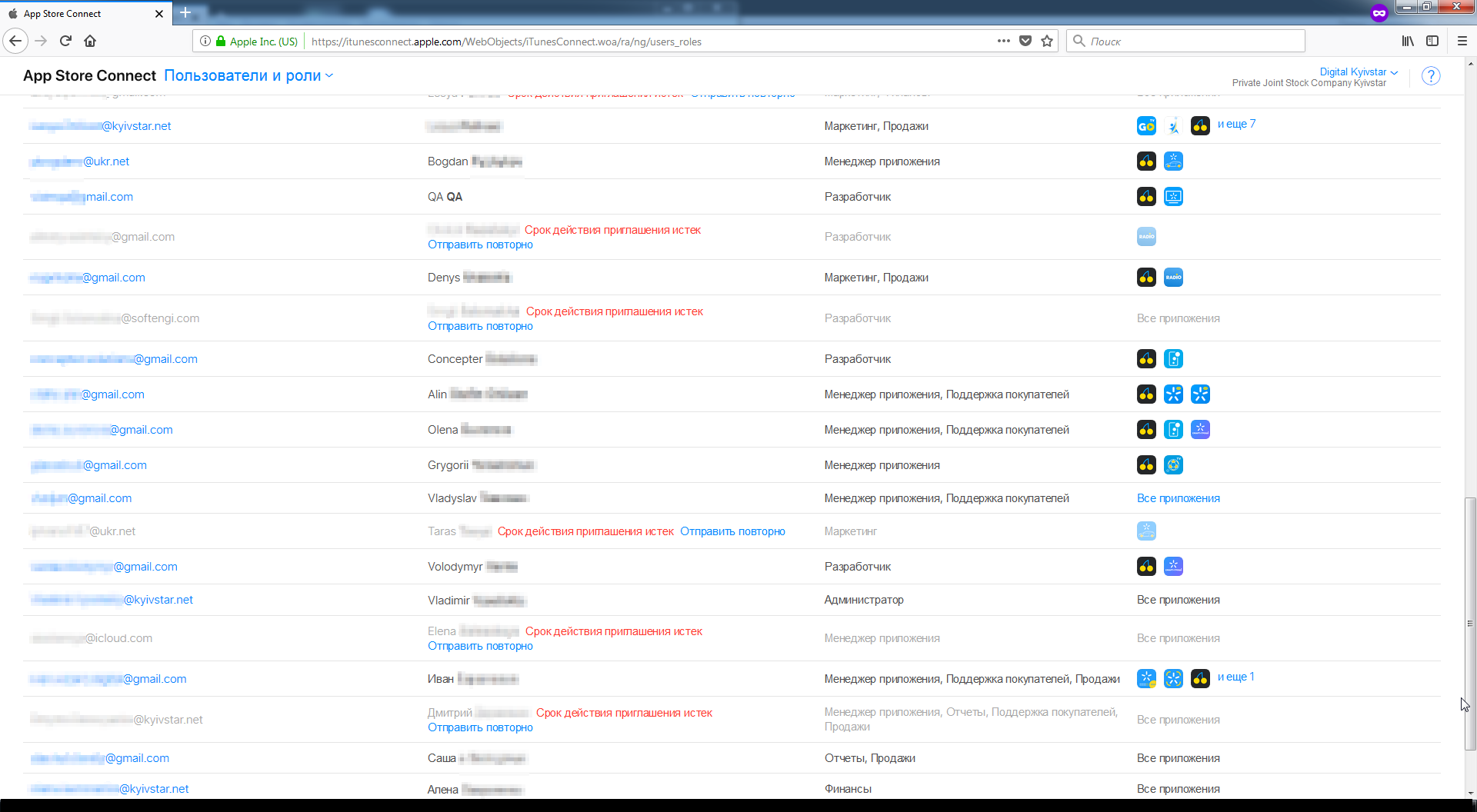
Understanding that administrator access is critical, the next day I quickly created and sent a request to Kievstar on the same Bugcrowd. Later I received a thank you, reputation points and $ 50 in response.
$ 50 for access to accounts, the total value of which officially is more than $ 5,800.
I wrote that access to services from the list with administrator rights:
Amazon Web Services
Apple Developer
Mobile Action
App annie
Disqus
Google Developers
Windows dev center
KBRemote
Jira
Smartsheet
PushWoosh
TicketForEvent
Samsung Developers
CMS for bigdata.kyivstar.ua and hub.kyivstar.ua
Gmail
Zeplin
Prezi
Bitbucket
This is a critical issue; it is access to almost the entire structure of the company and the services it uses.
Relying on potential damage to business, reputation and customers, and simply looking at the Kyivstar reward table, where my signal was given priority P1 (Sensitive Data Exposure: Critically Sensitive Data - Password Disclosure), I expected more:
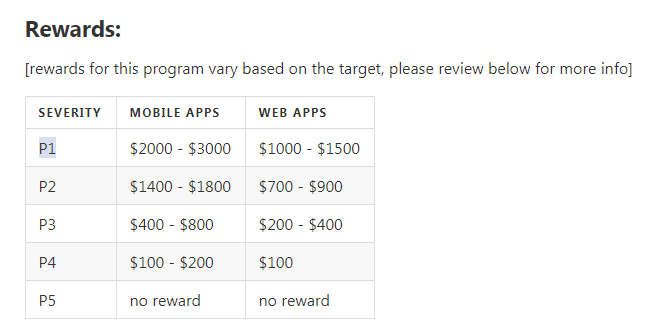
Losing access to such services of any digital company is a significant blow to business and reputation. This is much worse than just some kind of vulnerability, this is full access. This is Klondike useful information for any criminal.
Using only one account, for example, in Apple Developer, an attacker can change the username and password and upload their application builds or simply add themselves to the administrators, leaving the backdoor.
However, Kyivstar was adamant: “Thank you, here is $ 50 for you, this finding is beyond the scope of the program”.
It is a pity that because of such decisions of corporations, honest people will wonder where to report this: official channels, like me, or it is better to find someone who offers more information for this information. Companies themselves are pushing people to bad thoughts and actions.
And it's not about the money, but about the company’s disrespect towards me. While in one of the banks I found opportunities to get receipts from other customers and I was paid a little more than $ 300 for each opportunity found, there are also payment services that paid less than $ 20 for the same vulnerability - and nothing, I am not angry at the second 500 UAH also money. But here ...
Perhaps I was mistaken in that I expected a greater reward. Please select in the survey options below the correct in your opinion remuneration in this situation. You can voice your opinion right here in the comments.
PS: every rule has an exception.
UPD from 01/09/2019: posted answers to questions arising from reading this post + new Kyivstar problem - https://habr.com/post/435074/
Two years ago, a dinikin user wrote a post about how he found a vulnerability in the personal account of Ukraine’s largest mobile operator, Kyivstar. The vulnerability allowed to add to your account without verification any Kyivstar phone number and fully manage it:
- view the balance and call details;
- view the PUK-code and the serial number of the SIM-card, which allows you to replace the SIM-card;
- add new services and change the tariff plan;
- and most importantly - transfer money from phone to phone.
The vulnerability was closed, and the author, in gratitude, was
')

Later, habraprzovatel rewiaca in his post " Why in Ukraine there are no white hackers or history of hacking Kyivstar " described the situation with such a generous reward more emotionally.
Vitaly Sultan, Soultan , Chief Digital Officer of Kyivstar was noted in the comments then, promising to launch soon in the Bug Bounty company.
And now, after almost two years, Kyivstar announces the launch of its own Bug Bounty program. One of the first phrases in the announcement was as follows:
Kyivstar noted that they decided to launch the program after they found a vulnerability during the beta testing of the updated My Kyivstar system.As you can see, the company is cunning, because it is the user of Habrahabr.ru dinikin who found a vulnerability in the “My Kyivstar” system.
Some lyrics
Even before the launch of Bug Bounty, I found an opportunity on Kyivstar's website to get information about the solvency of the company's customers by phone number, as well as whether this or that number is active.
And knowing how much a subscriber spends, dishonest people can use such numbers for dialing, or simply collect and sell a base of numbers for mailing.
However, the reward payment program for vulnerabilities was launched only for 2 weeks, after which it went into private mode, and I did not have time to inform them about the problem (and what happens if you send a signal via communication channels that are not intended to submit such applications, described at the end the same post about Kyivstar).
Communicating with w9w on other issues, it turned out that he has the opportunity to send a report to the Kyivstar private program. It was decided to try to pass the problem through a colleague. But while I was making a description and picking up screenshots, the mobile operator again opened access to Bug Bounty for everyone.
Therefore, I independently designed the case I discovered. Having received the answer that this is part of the logic of work and the risks were taken at the stage of their implementation, I did not argue.
And knowing how much a subscriber spends, dishonest people can use such numbers for dialing, or simply collect and sell a base of numbers for mailing.
However, the reward payment program for vulnerabilities was launched only for 2 weeks, after which it went into private mode, and I did not have time to inform them about the problem (and what happens if you send a signal via communication channels that are not intended to submit such applications, described at the end the same post about Kyivstar).
Communicating with w9w on other issues, it turned out that he has the opportunity to send a report to the Kyivstar private program. It was decided to try to pass the problem through a colleague. But while I was making a description and picking up screenshots, the mobile operator again opened access to Bug Bounty for everyone.
Therefore, I independently designed the case I discovered. Having received the answer that this is part of the logic of work and the risks were taken at the stage of their implementation, I did not argue.
And in the evening I found in my Spam folder a letter from Kyivstar domain with an HTML attachment.
And here begins the most interesting.
Despite the fact that the sender's name coincided with the name of the employee who answered my previous request on the Bugcrowd platform, the e-mail came to the wrong box that was used for registration.
After checking the attachment for viruses, opening it with a notepad and googling the sender, I still could not believe such a coincidence: these were bookmarks from the browser of the working computer of the Kyivstar employee.
Ukraine’s largest mobile operator was lucky that a letter with an attachment of the form “Bookmarks_July.2018.html” didn’t get anywhere (sorry for tautology), but to someone who understands the value of such data and the consequences of losing it.
There were 113 bookmarks in the file. And among the various links, both for work (which did not open from the external network), and not very much, there was one, which opened my eyes to five kopecks.
The link led to an unprotected file, in which, among other things, were the following columns: "URL of the service", "Login" and "Password":

(to enlarge the image, open it in a new tab)
Once again, I thought, is it a fake, not a honeypot , I tried to enter several of the services, waiting for a barrier in the form of two-factor authentication. But she was not there, and I entered. Logged in as admin:



Understanding that administrator access is critical, the next day I quickly created and sent a request to Kievstar on the same Bugcrowd. Later I received a thank you, reputation points and $ 50 in response.
$ 50 for access to accounts, the total value of which officially is more than $ 5,800.
I wrote that access to services from the list with administrator rights:
Amazon Web Services
Apple Developer
Mobile Action
App annie
Disqus
Google Developers
Windows dev center
KBRemote
Jira
Smartsheet
PushWoosh
TicketForEvent
Samsung Developers
CMS for bigdata.kyivstar.ua and hub.kyivstar.ua
Gmail
Zeplin
Prezi
Bitbucket
This is a critical issue; it is access to almost the entire structure of the company and the services it uses.
Relying on potential damage to business, reputation and customers, and simply looking at the Kyivstar reward table, where my signal was given priority P1 (Sensitive Data Exposure: Critically Sensitive Data - Password Disclosure), I expected more:

Losing access to such services of any digital company is a significant blow to business and reputation. This is much worse than just some kind of vulnerability, this is full access. This is Klondike useful information for any criminal.
Using only one account, for example, in Apple Developer, an attacker can change the username and password and upload their application builds or simply add themselves to the administrators, leaving the backdoor.
However, Kyivstar was adamant: “Thank you, here is $ 50 for you, this finding is beyond the scope of the program”.
It is a pity that because of such decisions of corporations, honest people will wonder where to report this: official channels, like me, or it is better to find someone who offers more information for this information. Companies themselves are pushing people to bad thoughts and actions.
And it's not about the money, but about the company’s disrespect towards me. While in one of the banks I found opportunities to get receipts from other customers and I was paid a little more than $ 300 for each opportunity found, there are also payment services that paid less than $ 20 for the same vulnerability - and nothing, I am not angry at the second 500 UAH also money. But here ...
Perhaps I was mistaken in that I expected a greater reward. Please select in the survey options below the correct in your opinion remuneration in this situation. You can voice your opinion right here in the comments.
PS: every rule has an exception.
UPD from 01/09/2019: posted answers to questions arising from reading this post + new Kyivstar problem - https://habr.com/post/435074/
Source: https://habr.com/ru/post/418591/
All Articles