DEFCON 23. “Confessions of a Professional Cyberstalker”. Ken westin
My name is Ken Westin, and I’ll tell you what it means to be a professional cyberstalker (cyberstalking means using the Internet to search for someone, a group of people, or an organization) .
I am the founder of the company GadgetTrak, in which I was a hacker and part-time general director, and a developer of technical tools that allow the return of devices stolen from people. I also created a search engine for searching EXIF data in images.
Now I don’t work at GadgetTrak and currently I’m a current senior security analyst at Tripwire Inc., I’m involved in many investigations, collecting information from social networks and other sources and sending bad people to jail.
')
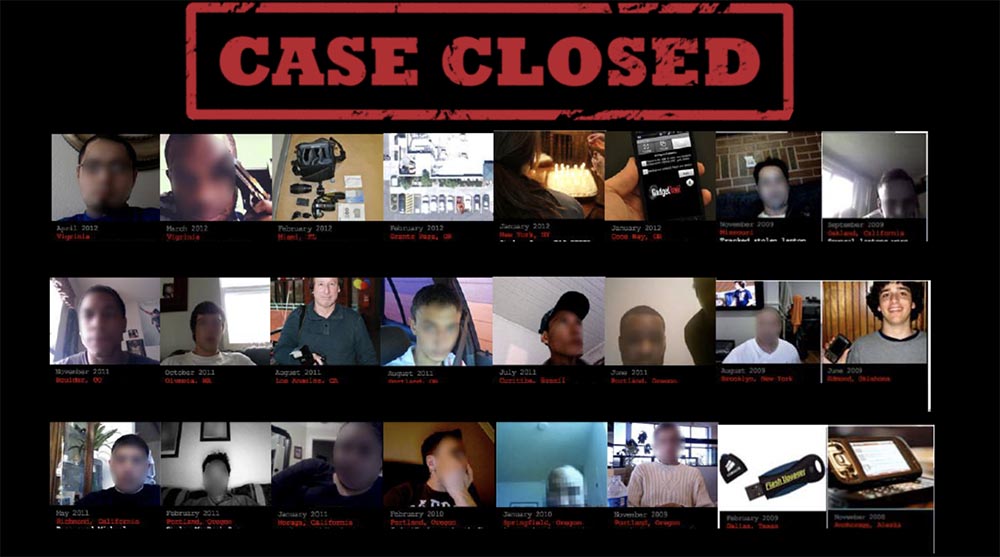
This slide shows “The Wall of Shame” - these are photographs of real people from real investigations in which I participated. You see a lot of photos taken with a webcam, I deliberately blurred the intruders' faces in order to preserve their anonymity. Some of these photos were taken from the devices I returned, and not from a webcam.
Interestingly, more than half of the time when I went to the police to recover stolen devices, they asked for help in other operations they carried out. Many times I happened to help in matters related to drugs, violent car theft, theft of laptops. Some of these cases were related to the use of Trojan devices that use virus vulnerabilities, malicious programs that spy on people, I will tell about this in more detail during the presentation. I developed tools that helped to monitor intruders while at the same time trying to maintain privacy.

You can imagine that part of my work causes criticism of people who do not understand that the spy methods I use serve to solve crimes and prevent their grave consequences.
The screen shows a slide from the Black Hat review review: “I think you should pay attention to the ethical side of using technology that you are so pleased to demonstrate.”
I want to note that many of the applications on the market are capable of doing more awful things with information than those that I use to return stolen devices.
I started using my tools when I was working for a company that specialized in locking USB devices. It was a long time ago, in 2006–2008.

At that time, my security impact was similar to how a network administrator tries to protect his web servers and site management. I was really interested in how these USB-based tools are used to hack networks. You know that it is quite difficult to access the network from the outside, but as a lazy hacker, you can use USB devices to hack the system and steal data. So I started working with these tools and even created usbhacks.com , where I started posting some of my tools, and the user community began to develop. Working with some members of the community was really interesting, and the interest in my development was on both sides of the law.
Then for the first time I received a small “call” from the FBI, but they nevertheless figured out my intentions to be of benefit, not harm. At that time, no one discussed or distributed such security testing tools. But now with the help of such tools, network administrators can really test their networks to see how they will react to such hacking tools.
Many security researchers are still asking me for these tools, so I link to my website usbhacks.com/USBHACKS.zip , where you can download them, just set up your antivirus so that it does not block these programs. You can adapt them to your needs by changing some of the scripts, and they will still work.
After I learned these USB devices, I thought about how to use them, making them more friendly, how to replace malicious Trojan software with something useful.
Usually, you connect a USB flash drive using autorun, run a binary file and can collect quite a lot of information. You can do a lot of things if you can intercept the hash. To return the stolen items, I think you know it, you can get an IP address, you can find out the internal network address, you can determine the geolocation on this IP address and find out what city it is located in. But more useful information was the name of the computer and the name of the user who works with this system.
I posted my tool online for free. Actually, it was a part of my master’s degree, a part of the system that I built, and I was curious about what people would do with it. I was very surprised how many people became interested in my resource and used the gadget located on the main page of the site. Within 2-3 days, about 20,000 people registered there. You can imagine that all this went through a central server and you could activate remote tracking, since after connecting the device it sent data to the owner. I managed to collect a huge amount of information about the devices with which my gadget worked.
The slide shows the text of the letter that was sent to users.
“Subject: Gadget Theft: Device detected.
A USB flash drive, which you reported as lost or stolen, was connected to a PC and we were able to retrieve the following information from the system for investigation:
- public IP address: xxx.xx.xxx.xxx,
- host: xxx.xx.xxx.xxx,
- internal IP address: xxx.xx.xxx.xxx,
- computer name: XXXXXXXXX,
- username: xxxxx
Country: USA
State: Oregon
City: Tialatin,
Postal Code: 97062
Area Code: 503
Latitude: 45.3653
Longitude: - 122,758 "
This concerned not only USB devices, I found out that my gadget works with external hard drives and GPS devices, because it happened just like updating maps. He also worked with the iPod, and if during this time on the tablet did not have time to change the software, then it was enough to connect a USB flash drive to it and get access. All this was very interesting.
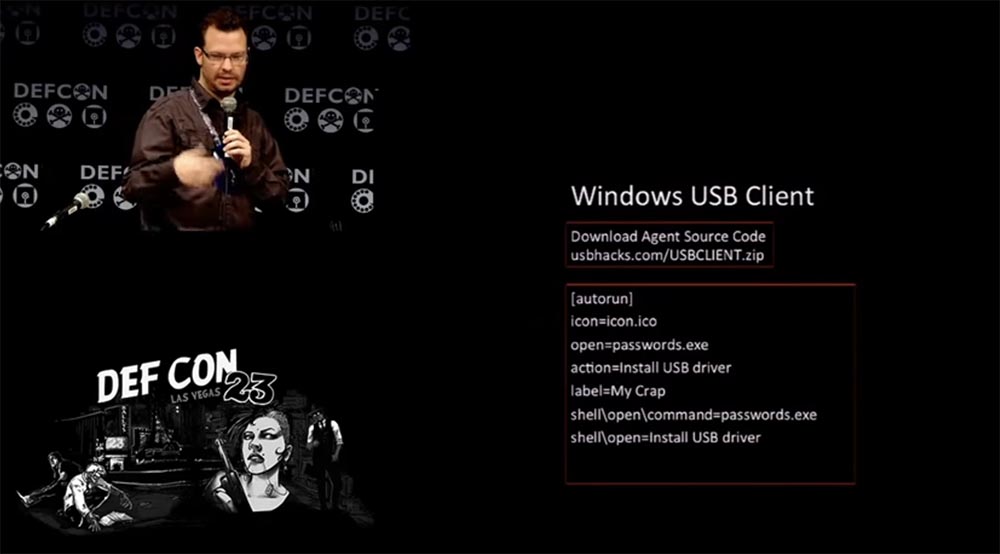
I also created a USB client for Windows, the code of which is shown on this slide, and you can download it via the link usbhacks.com/USBCLIENT.zip .

It is written in C ++, has autorun and exploits a Microsoft product vulnerability that exists until today. You can see computers running Windows XP in various institutions and medical centers that are still vulnerable to attacks of this type. Later I will give some examples. And although we all know how vulnerable USB devices are, even at the BlackHat conference this year there were a lot of people who "threw" around a bunch of their flash drives and became victims of such spyware devices by which data was stolen from their systems . And I’m not sure that if it were any of you, he wouldn’t take advantage of this opportunity.
Another thing I learned is the problem with getting an IP address. The authorship of such an attack is attributed to China, but it is difficult to unequivocally state where it was invented. You know, law enforcement agencies do not like messing about with papers, but when they have to deal with IP addresses, they have to issue a lot of papers in order to get a court order to get this information from an Internet service provider (ISP).
In addition, it is not possible to identify exactly who was in front of this computer or a stolen device during a crime. You can determine the owner of the IP, but he will say: "it was not me!", And you can not prove anything. In addition, he can change the IP-address or use an anonymizer. Because of the connection through the proxy server, the definition of the IP address is not particularly accurate.
In general, the process of determining IP takes a lot of time - from 2 weeks to 3 months, and this is a very big problem, so when searching for stolen devices, you need to act quickly, especially if the thief tries to protect them from detection. It should be noted that usually companies engaged in the search for stolen devices, using more "bold" methods of investigation. The next slide shows the iPod I have spotted.

There were many children who installed my gadget on their tablets. Once a certain guy stole such a tablet at school, and when he came home and connected to a computer, my device quickly determined all the necessary data, and luck was that the user name was “Kalpakis family”. Since there was only one child in the school with that last name, the school managed to get the iPod back to him.
The point of my idea was that if a stolen device could be traced, many people would have refused to steal such devices.
I also found out that all these devices could work in conjunction with a high-quality infrared camera that captures the thermal image. I turned to the company with a proposal to make a special software agent for them, which we could use to protect these cameras, each of which cost about $ 3000. It was quite simple, since the cameras recorded the image on the SD card, and I wrote a special code for the camera firmware.
The point of protection was that if someone pulls out the old card from the camera and inserts a new one, the code recorded in the camera firmware will be automatically installed on this new card, which will help to block it. This made it easier not only to search for abducted IR cameras, but also made it possible to control their illegal export to foreign countries. For example, if it were found that such a camera was connected to a computer somewhere in Iran, the camera seller would have big problems.

In addition, the software agent allowed the use of a file with an IR image as a password, such as this cat photo.
Then I will tell you how I tried to create a similar client for Apple products. The difficulty was that in Mac OS X there is no autorun feature, but you can fool people. The biggest vulnerability I enjoy is human greed and stupidity. I used the Apple script, and you can ask why it? Because such scripts are more trusted, they are suitable for most applications for the apple axis. There is an iTunes application here, which I tried to fool. I put my trojan in .mp3 file. But the fact is that OS X has such a feature: if you try to change the extension of an application by writing at the end of .mp3, the system will automatically drop the .app extension to the end of the file so that the user knows that this is actually a program and not a music file .

So I had to use such a thing as a homoglyph - a symbol with zero width, for this I took a Turkish letter called “organic”, and the system left. Mp3 at the end of my file, without trying to supply it with a “tail” .app. The next slide shows the code used in my script.
It allows you to get information about the system, user name, computer name and other information when running iTunes. This script allows you to learn about all the running applications, and this is cool, because you can write several scripts that embed in them and try to steal data. I made it so that iTunes collected the data I needed and sent them as music files to my URL, so that I could listen to music and do bad things in its background.
The great thing is that you can make shell scripts from Apple scripts, but be careful if you decide to run them on your system.
Know that USB devices are still the attack vector. It is known that with their help the Stuxnet virus got into the Iranian nuclear facilities system and in the same way spread to the Russian equipment. Malicious software - the W32.Gammima AG worm - penetrated the International Space Station (ISS) in 2008 using a USB device.
In 2012, the Computer Emergency Response Center at industrial and mission-critical facilities ICS-CERT reported that two US power plants suffered after an employee brought a “flash drive” infected by a virus to work. Many computers using Windows XP are still subject to such threats, as was noted at the Black Hat conference in 2015.
An IP address is one way to detect a loss, but I have to process information from many other sources. This slide shows the “crazy wall”, you have seen such in many television shows, in which the police are trying to solve the murder. They have all the evidence, and they draw all these lines correctly, trying to link the evidence. This is a kind of thinking process, which I adhere to. I also use tools like Multigo, it automates this process significantly. I'm not sure if you have ever used it, it’s quite a big tool and you can write for it all the specialized modules that help you do a lot of work.
I had a case with tracking of one missing "flash drive". We were able to get the original IP address, which was a strange user name, which did not give the opportunity to identify the person. We wanted to compare it with the names that were in the AT & T subscriber base, but you know how it happens with AT & T, we could lose track of this “flash drive” in three months. She was stolen from a professor and contained data on important studies, but we still could not convince the police to use all their resources in this investigation.
Therefore, we began to track any communication of the university and a specific computer lab, which was useful because we also received information from the internal network. She allowed us to advance further in the investigation. We visited the computer security department of the university, taking advantage of the fact that we had an IP address and a timestamp, and determined the internal address of the computer on the network. However, it was a “guest” computer that did not allow to identify the student ID who logged on to the system. I began to ask questions and found out that in order to gain access to computers, it is necessary to scan the student card, and the security system contains relevant records about it.
We linked this to the time stamp and got a list of everyone who was in this room during the theft. We learned that a year ago several desktop devices were stolen from this room, after which surveillance cameras were installed here. Not everyone knows that many of these cameras store data that is also recorded in a log file. We found out who was in this room with the professor and knew that the guard was outside the room at that time. As a result, we returned the “flash drive” to the professor, we did not even have time to erase the information on it.
I also wanted to find ways to help recover stolen items such as laptops. All existing search tools were mainly based on determining the IP address and user identification, which took a lot of time. More progressive were invasive methods of introduction, opening the "back door" into the system, which made it possible to install keyboard input interceptors. However, such methods in many cases made the system more vulnerable to real hackers, since they required changes to the original software.
I came to the conclusion that you should not resort to such extreme measures, but you need to adapt for this existing devices in laptops. For example, I would combine the use of a built-in webcam with Wi-Fi based geolocation. You know, there was a company that supplied MacBooks with cameras, but no one used Wi-Fi positioning. When the first iPhone came out, he already used this feature. I worked with the Skyhook system and it turned out that it is capable of being deployed so that we can get geolocation using the camera information. So it was a kind of "game converter" specifically for law enforcement.

However, there are some difficulties with the operation of this system. So, when you activate tracking on a remote server, it will check if the device is stolen and collect a lot of evidence. For example, track the movement of a laptop to another network with a change of IP address, check the login event, notice that the device’s registration location has changed on the network, and then send information.

But at that time I didn’t want to bother with such things as sending photos to the server, so you could go directly to Flickr photo hosting, register an account there and get control over all your data. In this case, you would receive a message of this nature: “We have determined that the person shown above in the photo tried to gain unauthorized access to your computer. The information below was collected from your missing MacBook. ” This was followed by data on the external IP address, internal host, user name, Ethernet ID, host name, Wi-Fi network name and access point coordinates obtained using geolocation.
, , .
, , , Wi-Fi, , 30 , .
, Skyhook wireless, – OS X, Windows, Android, iOS. , , Google Maps API. , .

Wi-Fi -. -, , «», , .
: «, , 10-20 ». : « ?» : « !», : « , !». - . , , -. «»: , , . , «», , , .
, « » . 3 , .

, . , . , , , . 4 5 . , , . , , , . 10 20 , , . , , , , , , .
. , «» , Russia. , «Russian pride». , , , .
, , . , , . 6 7 , , . , , , .
, . 2- , , , . , , , , .

. Myspace , Scion, , «» . eBay, .
, , . , , , , . .
, , , . , – , , . .
, . .

. , – . , , , , , , , . , , . , , , , , . . , .
, , IP- . , , . , , - , . , , .

, , , , , . « 8», .
:
. Washington Square Mall, . Sprint , , $500, .
, , , . GPS, . , , .
, « », , , , . , .
, , .
, , .

. , , , .
, , , Samsung Epic. , , Washington Square Mall, , .
, GPS , , EXIF , . , , .
, , . EXIF , GPS- , , EXIF , . EXIF www.sno.phy.queensu.ca/~phil/exiftool . , exifscan.com , EXIF. , EXIF . .
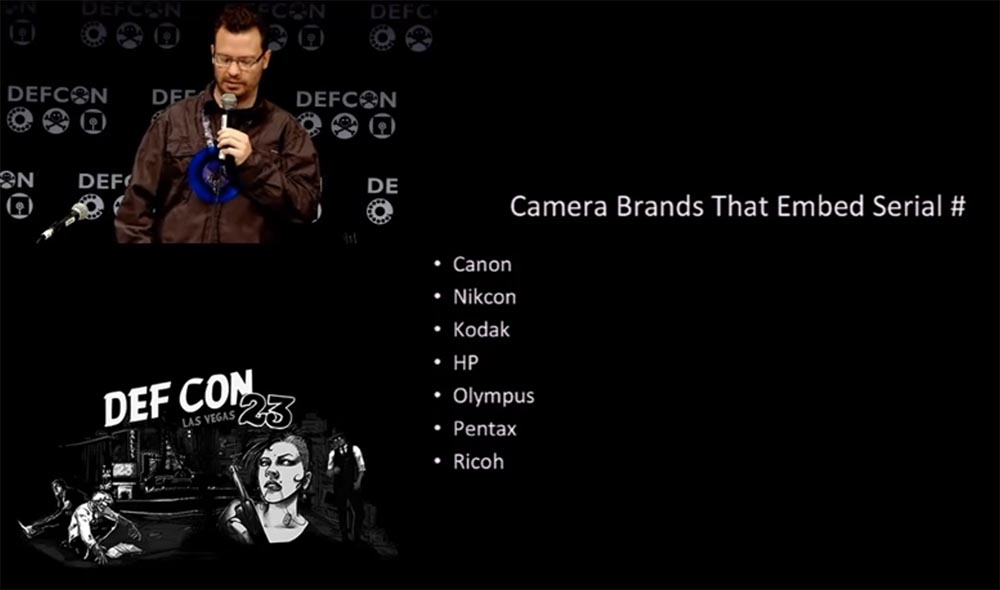
, , , . EXIF , , , . , , , , 10 .
, . , - Flickr, , .
- , , CP usage. , , . , - SETI.
Flickr API Flickr, IP . IP-, . , Yahoo, 200 Flickr. , EXIF 4- .
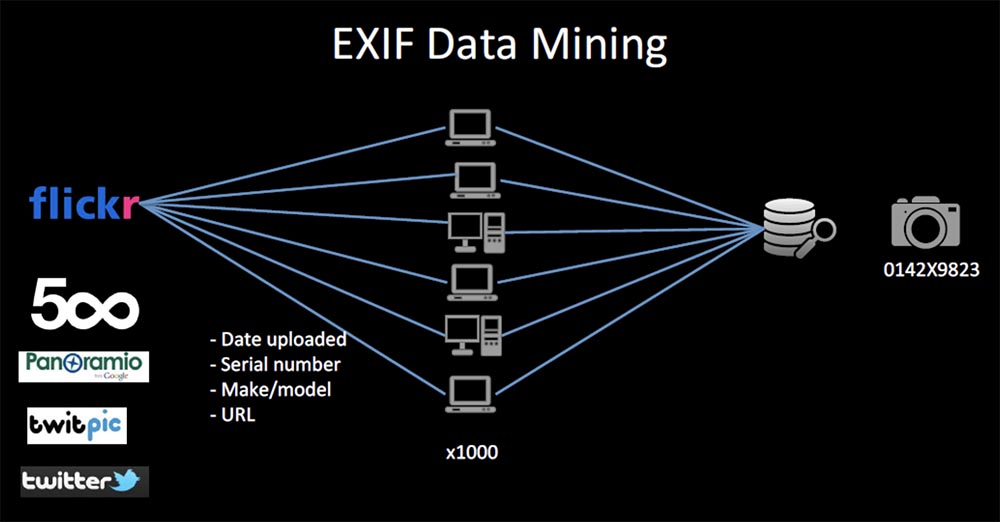
, . .
, «» EXIF, , , .
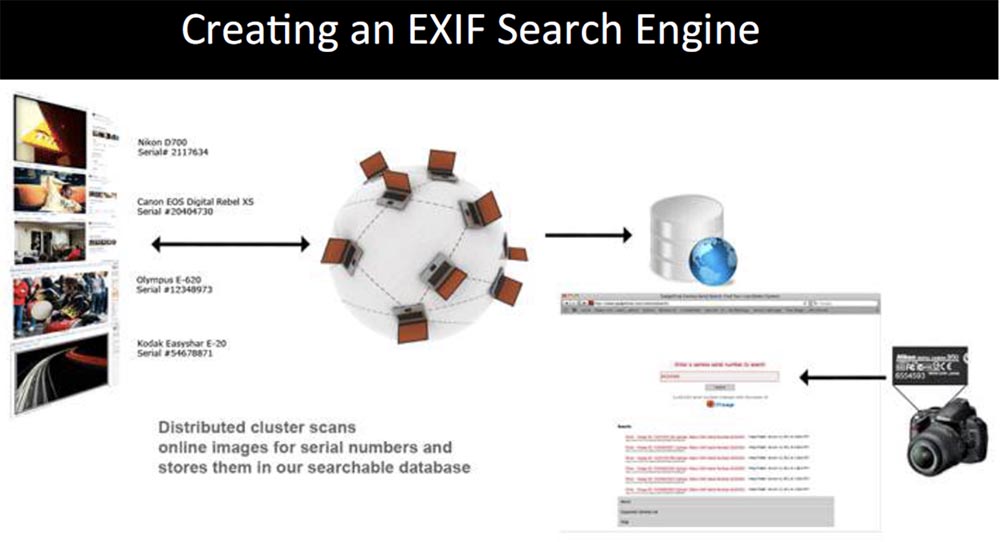
, , 3 - Flickr, , . , . , $9000 , .
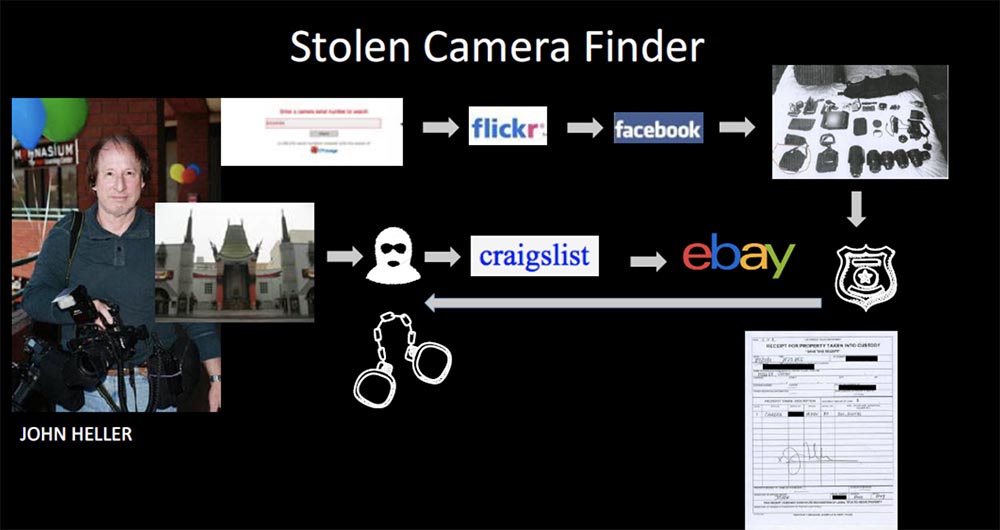
, 3 , Flickr , , Facebook , . -, , Craigslist, eBay , , . , eBay, . Craigslist , , , , , .
, .
, Craigslist ( Crimelist). - , , . , , , .
, , , . , , , , 110 .

, .
(3).

, . , , , , , , . , .
, « », , . , , , .
, - , . , , . , - SMS-, , , , 20 , .

, . ? ? , 30% entry-level , : VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $20 ? ( RAID1 RAID10, 24 40GB DDR4).
Dell R730xd 2 ? 2 Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 $249 ! . c Dell R730xd 5-2650 v4 9000 ?

I am the founder of the company GadgetTrak, in which I was a hacker and part-time general director, and a developer of technical tools that allow the return of devices stolen from people. I also created a search engine for searching EXIF data in images.
Now I don’t work at GadgetTrak and currently I’m a current senior security analyst at Tripwire Inc., I’m involved in many investigations, collecting information from social networks and other sources and sending bad people to jail.
')

This slide shows “The Wall of Shame” - these are photographs of real people from real investigations in which I participated. You see a lot of photos taken with a webcam, I deliberately blurred the intruders' faces in order to preserve their anonymity. Some of these photos were taken from the devices I returned, and not from a webcam.
Interestingly, more than half of the time when I went to the police to recover stolen devices, they asked for help in other operations they carried out. Many times I happened to help in matters related to drugs, violent car theft, theft of laptops. Some of these cases were related to the use of Trojan devices that use virus vulnerabilities, malicious programs that spy on people, I will tell about this in more detail during the presentation. I developed tools that helped to monitor intruders while at the same time trying to maintain privacy.

You can imagine that part of my work causes criticism of people who do not understand that the spy methods I use serve to solve crimes and prevent their grave consequences.

The screen shows a slide from the Black Hat review review: “I think you should pay attention to the ethical side of using technology that you are so pleased to demonstrate.”
I want to note that many of the applications on the market are capable of doing more awful things with information than those that I use to return stolen devices.
I started using my tools when I was working for a company that specialized in locking USB devices. It was a long time ago, in 2006–2008.

At that time, my security impact was similar to how a network administrator tries to protect his web servers and site management. I was really interested in how these USB-based tools are used to hack networks. You know that it is quite difficult to access the network from the outside, but as a lazy hacker, you can use USB devices to hack the system and steal data. So I started working with these tools and even created usbhacks.com , where I started posting some of my tools, and the user community began to develop. Working with some members of the community was really interesting, and the interest in my development was on both sides of the law.
Then for the first time I received a small “call” from the FBI, but they nevertheless figured out my intentions to be of benefit, not harm. At that time, no one discussed or distributed such security testing tools. But now with the help of such tools, network administrators can really test their networks to see how they will react to such hacking tools.
Many security researchers are still asking me for these tools, so I link to my website usbhacks.com/USBHACKS.zip , where you can download them, just set up your antivirus so that it does not block these programs. You can adapt them to your needs by changing some of the scripts, and they will still work.
After I learned these USB devices, I thought about how to use them, making them more friendly, how to replace malicious Trojan software with something useful.

Usually, you connect a USB flash drive using autorun, run a binary file and can collect quite a lot of information. You can do a lot of things if you can intercept the hash. To return the stolen items, I think you know it, you can get an IP address, you can find out the internal network address, you can determine the geolocation on this IP address and find out what city it is located in. But more useful information was the name of the computer and the name of the user who works with this system.
I posted my tool online for free. Actually, it was a part of my master’s degree, a part of the system that I built, and I was curious about what people would do with it. I was very surprised how many people became interested in my resource and used the gadget located on the main page of the site. Within 2-3 days, about 20,000 people registered there. You can imagine that all this went through a central server and you could activate remote tracking, since after connecting the device it sent data to the owner. I managed to collect a huge amount of information about the devices with which my gadget worked.
The slide shows the text of the letter that was sent to users.
“Subject: Gadget Theft: Device detected.
A USB flash drive, which you reported as lost or stolen, was connected to a PC and we were able to retrieve the following information from the system for investigation:
- public IP address: xxx.xx.xxx.xxx,
- host: xxx.xx.xxx.xxx,
- internal IP address: xxx.xx.xxx.xxx,
- computer name: XXXXXXXXX,
- username: xxxxx
Country: USA
State: Oregon
City: Tialatin,
Postal Code: 97062
Area Code: 503
Latitude: 45.3653
Longitude: - 122,758 "
This concerned not only USB devices, I found out that my gadget works with external hard drives and GPS devices, because it happened just like updating maps. He also worked with the iPod, and if during this time on the tablet did not have time to change the software, then it was enough to connect a USB flash drive to it and get access. All this was very interesting.
I also created a USB client for Windows, the code of which is shown on this slide, and you can download it via the link usbhacks.com/USBCLIENT.zip .

It is written in C ++, has autorun and exploits a Microsoft product vulnerability that exists until today. You can see computers running Windows XP in various institutions and medical centers that are still vulnerable to attacks of this type. Later I will give some examples. And although we all know how vulnerable USB devices are, even at the BlackHat conference this year there were a lot of people who "threw" around a bunch of their flash drives and became victims of such spyware devices by which data was stolen from their systems . And I’m not sure that if it were any of you, he wouldn’t take advantage of this opportunity.
Another thing I learned is the problem with getting an IP address. The authorship of such an attack is attributed to China, but it is difficult to unequivocally state where it was invented. You know, law enforcement agencies do not like messing about with papers, but when they have to deal with IP addresses, they have to issue a lot of papers in order to get a court order to get this information from an Internet service provider (ISP).

In addition, it is not possible to identify exactly who was in front of this computer or a stolen device during a crime. You can determine the owner of the IP, but he will say: "it was not me!", And you can not prove anything. In addition, he can change the IP-address or use an anonymizer. Because of the connection through the proxy server, the definition of the IP address is not particularly accurate.
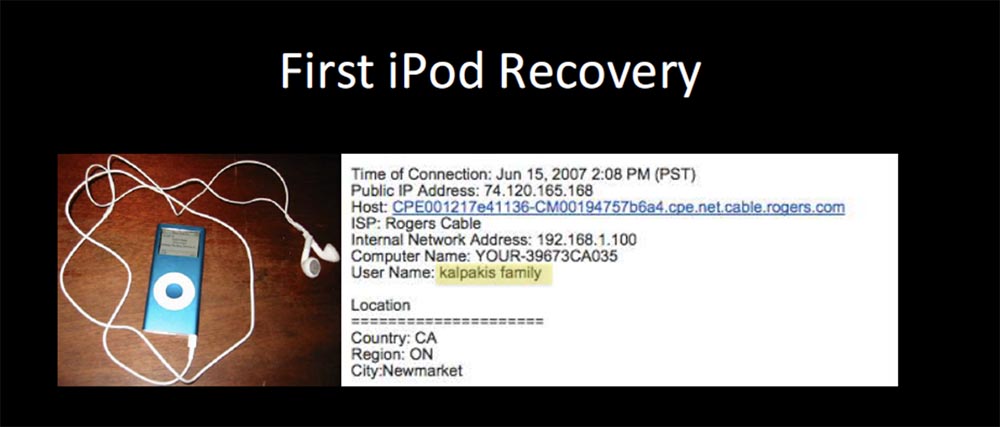
In general, the process of determining IP takes a lot of time - from 2 weeks to 3 months, and this is a very big problem, so when searching for stolen devices, you need to act quickly, especially if the thief tries to protect them from detection. It should be noted that usually companies engaged in the search for stolen devices, using more "bold" methods of investigation. The next slide shows the iPod I have spotted.

There were many children who installed my gadget on their tablets. Once a certain guy stole such a tablet at school, and when he came home and connected to a computer, my device quickly determined all the necessary data, and luck was that the user name was “Kalpakis family”. Since there was only one child in the school with that last name, the school managed to get the iPod back to him.
The point of my idea was that if a stolen device could be traced, many people would have refused to steal such devices.
I also found out that all these devices could work in conjunction with a high-quality infrared camera that captures the thermal image. I turned to the company with a proposal to make a special software agent for them, which we could use to protect these cameras, each of which cost about $ 3000. It was quite simple, since the cameras recorded the image on the SD card, and I wrote a special code for the camera firmware.
The point of protection was that if someone pulls out the old card from the camera and inserts a new one, the code recorded in the camera firmware will be automatically installed on this new card, which will help to block it. This made it easier not only to search for abducted IR cameras, but also made it possible to control their illegal export to foreign countries. For example, if it were found that such a camera was connected to a computer somewhere in Iran, the camera seller would have big problems.

In addition, the software agent allowed the use of a file with an IR image as a password, such as this cat photo.
Then I will tell you how I tried to create a similar client for Apple products. The difficulty was that in Mac OS X there is no autorun feature, but you can fool people. The biggest vulnerability I enjoy is human greed and stupidity. I used the Apple script, and you can ask why it? Because such scripts are more trusted, they are suitable for most applications for the apple axis. There is an iTunes application here, which I tried to fool. I put my trojan in .mp3 file. But the fact is that OS X has such a feature: if you try to change the extension of an application by writing at the end of .mp3, the system will automatically drop the .app extension to the end of the file so that the user knows that this is actually a program and not a music file .

So I had to use such a thing as a homoglyph - a symbol with zero width, for this I took a Turkish letter called “organic”, and the system left. Mp3 at the end of my file, without trying to supply it with a “tail” .app. The next slide shows the code used in my script.

It allows you to get information about the system, user name, computer name and other information when running iTunes. This script allows you to learn about all the running applications, and this is cool, because you can write several scripts that embed in them and try to steal data. I made it so that iTunes collected the data I needed and sent them as music files to my URL, so that I could listen to music and do bad things in its background.
The great thing is that you can make shell scripts from Apple scripts, but be careful if you decide to run them on your system.
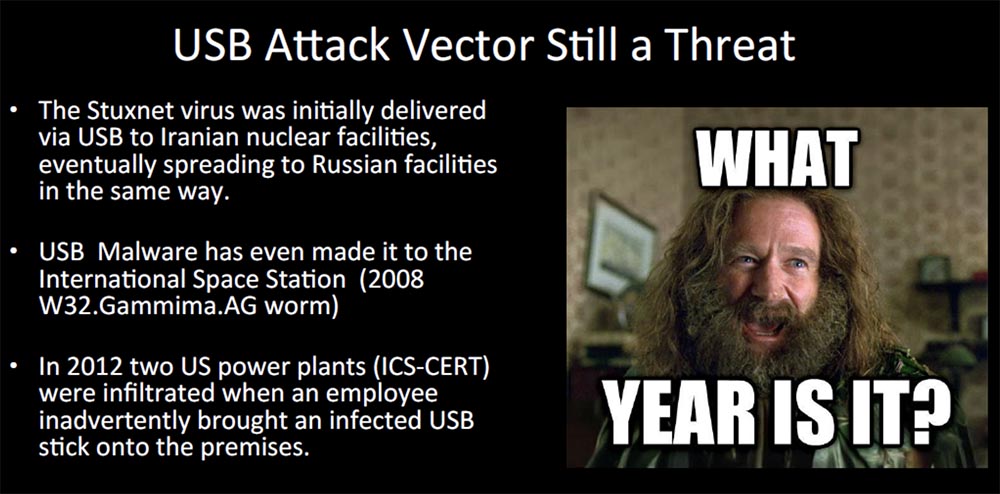
Know that USB devices are still the attack vector. It is known that with their help the Stuxnet virus got into the Iranian nuclear facilities system and in the same way spread to the Russian equipment. Malicious software - the W32.Gammima AG worm - penetrated the International Space Station (ISS) in 2008 using a USB device.
In 2012, the Computer Emergency Response Center at industrial and mission-critical facilities ICS-CERT reported that two US power plants suffered after an employee brought a “flash drive” infected by a virus to work. Many computers using Windows XP are still subject to such threats, as was noted at the Black Hat conference in 2015.
An IP address is one way to detect a loss, but I have to process information from many other sources. This slide shows the “crazy wall”, you have seen such in many television shows, in which the police are trying to solve the murder. They have all the evidence, and they draw all these lines correctly, trying to link the evidence. This is a kind of thinking process, which I adhere to. I also use tools like Multigo, it automates this process significantly. I'm not sure if you have ever used it, it’s quite a big tool and you can write for it all the specialized modules that help you do a lot of work.
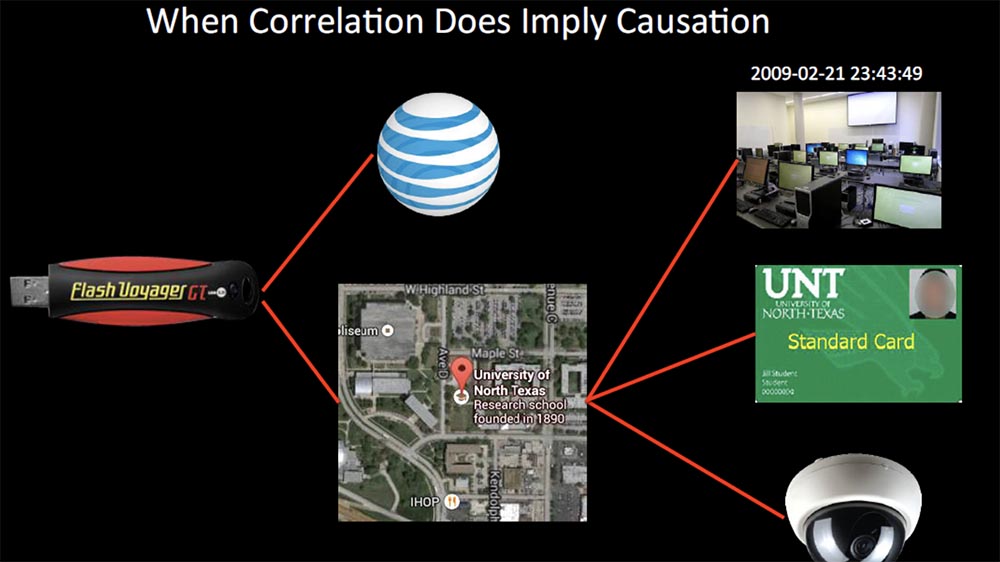
I had a case with tracking of one missing "flash drive". We were able to get the original IP address, which was a strange user name, which did not give the opportunity to identify the person. We wanted to compare it with the names that were in the AT & T subscriber base, but you know how it happens with AT & T, we could lose track of this “flash drive” in three months. She was stolen from a professor and contained data on important studies, but we still could not convince the police to use all their resources in this investigation.

Therefore, we began to track any communication of the university and a specific computer lab, which was useful because we also received information from the internal network. She allowed us to advance further in the investigation. We visited the computer security department of the university, taking advantage of the fact that we had an IP address and a timestamp, and determined the internal address of the computer on the network. However, it was a “guest” computer that did not allow to identify the student ID who logged on to the system. I began to ask questions and found out that in order to gain access to computers, it is necessary to scan the student card, and the security system contains relevant records about it.
We linked this to the time stamp and got a list of everyone who was in this room during the theft. We learned that a year ago several desktop devices were stolen from this room, after which surveillance cameras were installed here. Not everyone knows that many of these cameras store data that is also recorded in a log file. We found out who was in this room with the professor and knew that the guard was outside the room at that time. As a result, we returned the “flash drive” to the professor, we did not even have time to erase the information on it.
I also wanted to find ways to help recover stolen items such as laptops. All existing search tools were mainly based on determining the IP address and user identification, which took a lot of time. More progressive were invasive methods of introduction, opening the "back door" into the system, which made it possible to install keyboard input interceptors. However, such methods in many cases made the system more vulnerable to real hackers, since they required changes to the original software.
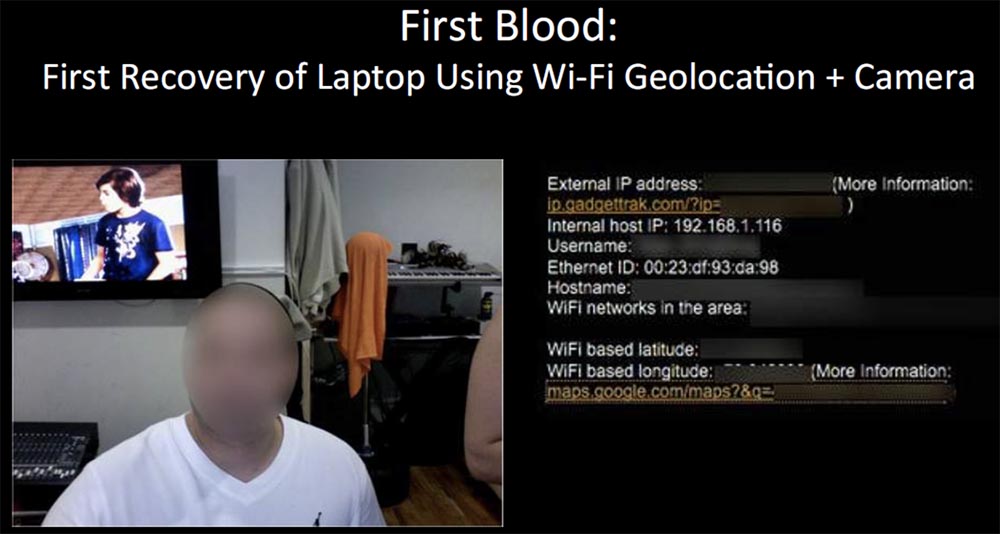
I came to the conclusion that you should not resort to such extreme measures, but you need to adapt for this existing devices in laptops. For example, I would combine the use of a built-in webcam with Wi-Fi based geolocation. You know, there was a company that supplied MacBooks with cameras, but no one used Wi-Fi positioning. When the first iPhone came out, he already used this feature. I worked with the Skyhook system and it turned out that it is capable of being deployed so that we can get geolocation using the camera information. So it was a kind of "game converter" specifically for law enforcement.

However, there are some difficulties with the operation of this system. So, when you activate tracking on a remote server, it will check if the device is stolen and collect a lot of evidence. For example, track the movement of a laptop to another network with a change of IP address, check the login event, notice that the device’s registration location has changed on the network, and then send information.

But at that time I didn’t want to bother with such things as sending photos to the server, so you could go directly to Flickr photo hosting, register an account there and get control over all your data. In this case, you would receive a message of this nature: “We have determined that the person shown above in the photo tried to gain unauthorized access to your computer. The information below was collected from your missing MacBook. ” This was followed by data on the external IP address, internal host, user name, Ethernet ID, host name, Wi-Fi network name and access point coordinates obtained using geolocation.
, , .
, , , Wi-Fi, , 30 , .
, Skyhook wireless, – OS X, Windows, Android, iOS. , , Google Maps API. , .

Wi-Fi -. -, , «», , .

: «, , 10-20 ». : « ?» : « !», : « , !». - . , , -. «»: , , . , «», , , .
, « » . 3 , .

, . , . , , , . 4 5 . , , . , , , . 10 20 , , . , , , , , , .
. , «» , Russia. , «Russian pride». , , , .
, , . , , . 6 7 , , . , , , .
, . 2- , , , . , , , , .

. Myspace , Scion, , «» . eBay, .
, , . , , , , . .
, , , . , – , , . .
, . .

. , – . , , , , , , , . , , . , , , , , . . , .
, , IP- . , , . , , - , . , , .

, , , , , . « 8», .
:
. Washington Square Mall, . Sprint , , $500, .
, , , . GPS, . , , .
, « », , , , . , .
, , .
, , .

. , , , .
, , , Samsung Epic. , , Washington Square Mall, , .
, GPS , , EXIF , . , , .
, , . EXIF , GPS- , , EXIF , . EXIF www.sno.phy.queensu.ca/~phil/exiftool . , exifscan.com , EXIF. , EXIF . .

, , , . EXIF , , , . , , , , 10 .
, . , - Flickr, , .
- , , CP usage. , , . , - SETI.
Flickr API Flickr, IP . IP-, . , Yahoo, 200 Flickr. , EXIF 4- .

, . .
, «» EXIF, , , .

, , 3 - Flickr, , . , . , $9000 , .

, 3 , Flickr , , Facebook , . -, , Craigslist, eBay , , . , eBay, . Craigslist , , , , , .
, .
, Craigslist ( Crimelist). - , , . , , , .
, , , . , , , , 110 .

, .
(3).

, . , , , , , , . , .
, « », , . , , , .
, - , . , , . , - SMS-, , , , 20 , .

, . ? ? , 30% entry-level , : VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $20 ? ( RAID1 RAID10, 24 40GB DDR4).
Dell R730xd 2 ? 2 Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 $249 ! . c Dell R730xd 5-2650 v4 9000 ?
Source: https://habr.com/ru/post/418357/
All Articles