Conference DEFCON 19. "Steal everything, kill everyone, cause a complete financial collapse!" Jason I. Street
I want you to understand why I begin my speech from this slide. I want to say how little you know, if you think that bad always means mean, hateful, and good is always nice and fluffy. I want you to remember this kitten picture when I start telling you really awful things.

My presentation is called “Steal everything, kill everyone, cause a complete financial collapse, or how I entered and misbehaved!” Simply because it tells about the failure of the security system.
')
The signature on the picture with the kittens reads: “Army of darkness. Milder than you expected. ” The slide with the name of the presentation shows a sign with the inscription “The guard will return in 5 minutes”.

I am going to explain to you that physical security issues and everything related to them are our weakest point, because people oppose two-dimensional to three-dimensional and simple to complex, when they approach the entrance doors. You see that Jason I. Street has many more letters after the last name, so let me introduce myself first. I have a day job and a night job. My day job is that I serve as vice president of information security at financial company Stratagem 1 Solutions. I work in an office booth, surrounded by many interesting events. I watch the firewalls, watch the ID systems, I built our own infrastructure and I find more creative ways to protect it from those people who can “come for us”, and my main job is the “blue team”, that is, protection.
My night job is to perform the duties of the CIO - Director of Information Strategies, and I perform penetration testing about 3 times a year, this is my main job. I speak at such events around the world, I wrote the book “Dissecting the Hack: The F0rb1dd3n Network” in the genre of the documentary detective story, I write articles, and all this I do at night. During the day, I react to incidents, and at night I create incidents for other people, so it is more convenient for both parties.

I love to look at these photos. In this baseball cap and black glasses, I stood for an hour in front of the building of the protected industrial park, on Sunday, in the absence of other traffic, and a guard passed me twice, who did not even ask what I was doing on the sidewalk and why I was inspecting the protected building, and did not record this incident in the report.
In the second photo I’m wearing glasses, I’m just about to apply for a job, here I’m wearing a blackHat-colored shirt, because I like to go with “warning stickers”. I never got this job because I was not qualified enough, but I managed to get their data. That was my victory.
On the next slide, you see two more photos that I like too.

T-shirt with the inscription, I think the best, because in it I almost stole a car. I was in a hotel on the coast and the parking attendant provided me with a car, but I explained to him that I could not take this car right now, he asked why, and I answered - because I would steal it. Apparently, he bought the inscription on my T-shirt "I am the source of trouble," and decided to give me someone else's car. It took him a while to understand what I mean, so I had to say to him: “You have to take her back, because the owner may need it.”
The next shirt is my favorite. At one of the most guarded objects I’ve seen in life, directly opposite Ground Zero, the zero level of the World Trade Center in Manhattan, the SWAT squadron, these K9 with their machine guns, pass through the hall to the main elevator, which is guarded by 8 guards. the upper floors I go to myself in a shirt with the icon "Geek your company." Yes, I like this photo the most, and later I will tell you about this story a little more.
I have a CISSP (information security certificate from a non-profit organization International Information Systems Security Certificates Consortium), and I think that according to the ethical code I should mention that in my presentation I used quotes from the treatise “The Art of War” by Sun Tzu, a Chinese strategist and thinker of the V century.

So, my presentation consists of these parts:
Introduction;
Fact - one fact that we will encounter when discussing this topic;
Rules - 2 rules that I thought up while doing my job;
Results - we will have as many as 3 results arising from these 2 rules;
Conclusions and / or discussion.
So why this particular topic? I talked about this last year at the 36 CHARGE conference, I talked about the beginning of social engineering, about the things you could do to try to get into a protected building. It was the first part and, to be honest, I received some feedback after that, and I was approached with all sorts of difficult questions.
But I am not an expert in the field of social engineering, I do not know anything about neurolinguistic programming (NLP), I do not know the methods of face recognition or ninja technology. However, I have 100% success in entering buildings, I just go there when I use the skills of this very social engineering. But believe me, I’m not strong in it, it’s just our modern security.
I think you will not learn anything new from me, so this is rather an educational lecture that will show you the beginning of the path, but I hope that after it you will remember what will force you to look around and take a fresh look at things that you seem to know. and improve your perception of the environment.
But now I will not talk about social engineering, so this is all the damage I was able to do after your security guard let me go through the front doors.
So, fact number 1: I sneaked inside! I took this photo as soon as I opened the door and went up to the hall. I saw the door for the staff, this was the door to the protected area, and I just went through it by pressing buttons 1-3-5.

I could press 5-3-1, or 3-1-5, it does not matter, I would still open it, because I pressed the buttons, the surface of which was wiped from frequent use more than others. I returned from there 10 minutes before the beginning of our meeting, and no one found out that I was there.
Another fun occasion was when I went to get another job. I decided to be a bad guy, and when I signed my name at the reception, I stole a pen from them. Then I asked where their toilet is. This is not because I drink too much dietary cola, I just “get lost” in these large buildings and can wander for hours in search of this toilet, while looking around the entire building.

In search of a toilet, I unexpectedly came across a protected part of the working area and found an entrance for staff. It looked as if the guard of this object was showing off its security systems worth a million dollars, but when I looked at the door, I saw a little thing, a rod that holds the door latch. If I had a condom, I would adjust it to keep the door from closing. And then I remembered the stolen handle, screwed the cap off it and put it on the rod, and the door did not click. When I returned there 20 minutes after walking in the "forbidden" zone, the cap was still there. No one knew that I was on a guarded object, and it was fun!
So, I am not a locksmith of the highest category, and I do not need to be a master of locks so that people let me through the front door. I don't need to be a super ninja coder to just steal a hard disk with data from your computer. This video shows my hacker skills and a unique master key - the cover of a cardboard folder. I simply insert a sheet of cardboard between the doors of the closed door, take them up and down, and the doors open with such a simple “key”.
Next on the slide is another “key” - a fake email I placed on the iPad. If you just print it out, it will look like a fake, they will tell you: “you just printed it yourself!”, But seeing it on a tablet with these blue hyperlinks, they say: “oh, this is magic, it must be true”!

I had to get to a protected facility in New York, because the network administrator noticed that there was a lot of network traffic coming from the computer of the company's deputy CFO. Therefore, such a cool network specialist, like me, had to get on this object and figure out what was happening with the network. Such was the legend, and I spent 2 hours in Google Docs, writing this letter. So, it says here that the new owner of this company was very upset by this sad event and appealed to another company asking it to send its best network specialist, that is, me, to check their main server. Well, the second letter was addressed personally to me as if from the director of information security of the second company, and he wrote that I should give up all my affairs and arrive there by tomorrow. And that I have to do the job as “excellent”, because “many eyes” are looking at this project. In general, I made it so that it sounded urgent and politically, so that no one was particularly surprised at my arrival. I showed this letter to the “network guy”, he took me to the office, we talked to the director of information security for 10 minutes. And then this guy accompanied me on all the desktops with computers, but I could freely insert my flash drives wherever I wanted and do whatever I wanted. So I really loved this letter.
So, I don’t care about your credit cards, I don’t care about the Sarbanes-Oxley Act, the ISOs, that Leicester got Linux, I just want to fuck you, spoil your mood in the worst possible way, I want to be the worst may happen to you at the worst possible time. Remember the kittens?
So here are 2 of my rules that I took from the Serenity movie: “I want to go ugly” and “Let's be the bad guys.”

It's like a red team against a blue one, so don't be offended if I hit you below the belt. It’s like the bankers kidnapped and held hostage by their whole family until the robbers open the doors of the bank. This is not funny, it really is still happening. This is one of the things about which people say that there is nothing new in it. The concept of what we are doing is taken from the 1992 movie Sneakers. It’s as if people are hiring you to break into places to make sure no one can hack them.
Now this business has become better, but still, the concept is preserved, it is not new, and there are people who understand this better than me.
Another thing we need to understand is that management is a response, not a warning. I will quote the words of Dana Erwin, a security officer at Dow Chemical, in 2008: “The best way to draw management’s attention to a disaster plan is to burn the building across the street.”
Greetings to all present - I am that fire! And now we come to the fun part of the speech, in which I will talk about several ways of kindling such lights.

The inscription on the demotivator: “Prostaki. Even the ducklings know how to recognize them! ”
Next on the slides, what I call “use bad facts” is depicted, because I stole this phone, I “raped” this laptop, and 30 laptops in this office did not have anti-theft cables, because the management thought that they were already “ protected. " When I got there, they just equipped laptops with anti-theft cables, and one guy left his laptop with a cable and a screwdriver on the table, probably so that the thief would be comfortable unscrewing the cable if it were connected to a laptop. But since I was hungry, I stole only cookies from his table.


You know, people believe that security should not be so thorough that they use anti-theft cables to protect their laptops. Because you have to attach it to the table, and this is difficult, you need to bend, so let's just run this cable over the table, because no one will pull it. And you know that most of the guards really don’t try to pull this cable to check, but I’m not a guard, I’m a thief, I’ll pull him to try to steal a laptop.

Some guys use a combination lock, but I assure you that if this code is 0-0-0-0, I will try to dial it, if it is 1-1-1-1, I will also try, and I will try to dial even 9-9- 9-9. And if you are so clever that you pick up 0-0-0-7, because people like you like to move only the last or only the first wheel of the lock, I will try this option and open the lock anyway.

I'm going to go through all the drawers of your desk and all the lockers, and I will look for all sorts of things there. A decent and honest colleague will not look at someone else’s table, what lies there, but I’m not like that. On the slide to the right, you see the laptop of one guy, he fixed the laptop perfectly, and thought that now that he has such a shiny cable, his laptop is protected from theft. But then he put the keys in the top drawer of his desk and crossed out all the security.
The next slide shows why I stole this iPod in a “retro” style, these car keys and driver's license. Because they were lying unattended.

Now imagine that I took her keys, went down to the parking lot, opened the car, and then put the keys in place. And after work, I would have been waiting for her in the back seat of a car with a gun in my hand. From the driver's license, I would have recognized her home address, and could have sent people who would have killed her family if she had not returned to work and stolen the necessary data for me.
Workers should know that their personal belongings belong only to them, but their theft can inflict a serious blow not only on them, but also on the company in which they work. Therefore, they themselves must ensure the safety of their belongings. Let's once again remember the cute kittens from the first slide.
Look at the next slide, do you know why there are so many sad emoticons? Because this is a complete “game over” for the owner of this wallet - there is an empty checkbook, credit cards, ID and social security card with the owner’s signature.

When I was going to steal my first car, there were too many people there, and then I came at 2 am and opened three Mercedes-Benz and one Beamer and it took me less than 60 seconds, as in the movie with Nicholas Cage You should have seen the security manager when I came to him and threw 4 keys from these cars on the table - the expression on his face was simply indescribable.

By the way, I included this slide in the presentation - this picture of the desktop in my home.
Therefore, I would like employees to take countermeasures against theft, to lock the boxes at work, even if they leave the workplace for a short time, not to leave wallets, credit cards, checkbooks on the tables, to ensure the safety of their property at work and at home, the safety of their property. machines. I want them to understand that it is impossible to pass by a “tail” to two people on one pass and explain to others that this threatens their own security. You can not send anyone a certificate issued by your company, you can not leave your computer, laptop and smartphone unattended. Finally, if you see a suspicious person, or someone who should not be inside or outside the building, immediately inform the security or the police.

Do you know what I did once? I appeared in a wheelchair with 4 books in my hands. “Jason, you are a jerk!”, And I’m all so — yes, I’m trying to rob you, you really think that I’m worried about my inferiority, because I don’t have to be in this wheelchair? I’m evil, I’m really going to do THAT, and you just let me pass inside the protected object with these 4 books.
I want to note that you don’t have to push the handicapped person out of the door yourself, or open the door in front of him if you are embarrassed or afraid to offend him. But if you saw something suspicious - say so. Remember that any employee is part of the company's security system. If you consider something suspicious, do not hesitate to report this to the guards, it is their job to check all suspicious visitors.
So, we figured out what it means to “steal everything”, so now let's talk on the topic “kill everyone”.
This slide shows a photo taken at 2:30 am on Sunday night in the hotel’s basement working area, I went there in my pajamas and barefoot because I took off all my clothes in the bathroom of the guest area and thought what I could do here and how It turned out I could do a lot. I entered the room with mechanical equipment and saw that there were no locks on any of the switches.

Imagine that I have something like OBS, obsessive-compulsive disorder, I'm crazy, and if these switches are turned off, I turn them on, if they turn on - I turn them off, if there is a red button, then I press it twice, but do not think that I am a complete moron. If there are any toxic chemicals there, they will catch fire and smoke will go into the ventilation and a fire alarm may be triggered. , , , , .
, , – , . , , 2-30 ! ! , .


, , . , , .

, . , , , .
, . - , . , , . . . : «, »!

: « «» «-47», -4, , , . , ». , .
, , . . , : «!», , . , , , , , .
, , . , 2 , . : « ?», : «!», . , , . , , , . , , , . . , , – WI-Fi , , iPad , .
: , , . :
, , , . , « , , !», . Periwinkle () : « ? !» . , - , .
. , , . , , . , , . , , , , . , , . , – , . : « !». , , , .
– , . – , .

, ? ! , , ? , , , . ! , , .
, – . , , , .

, , , , , , . , ? ! , , , . .

, - , USB . , . , ? 25 , , , – ACCOUNTING . , .

, - – , .

, ? Linux, , . .

, .
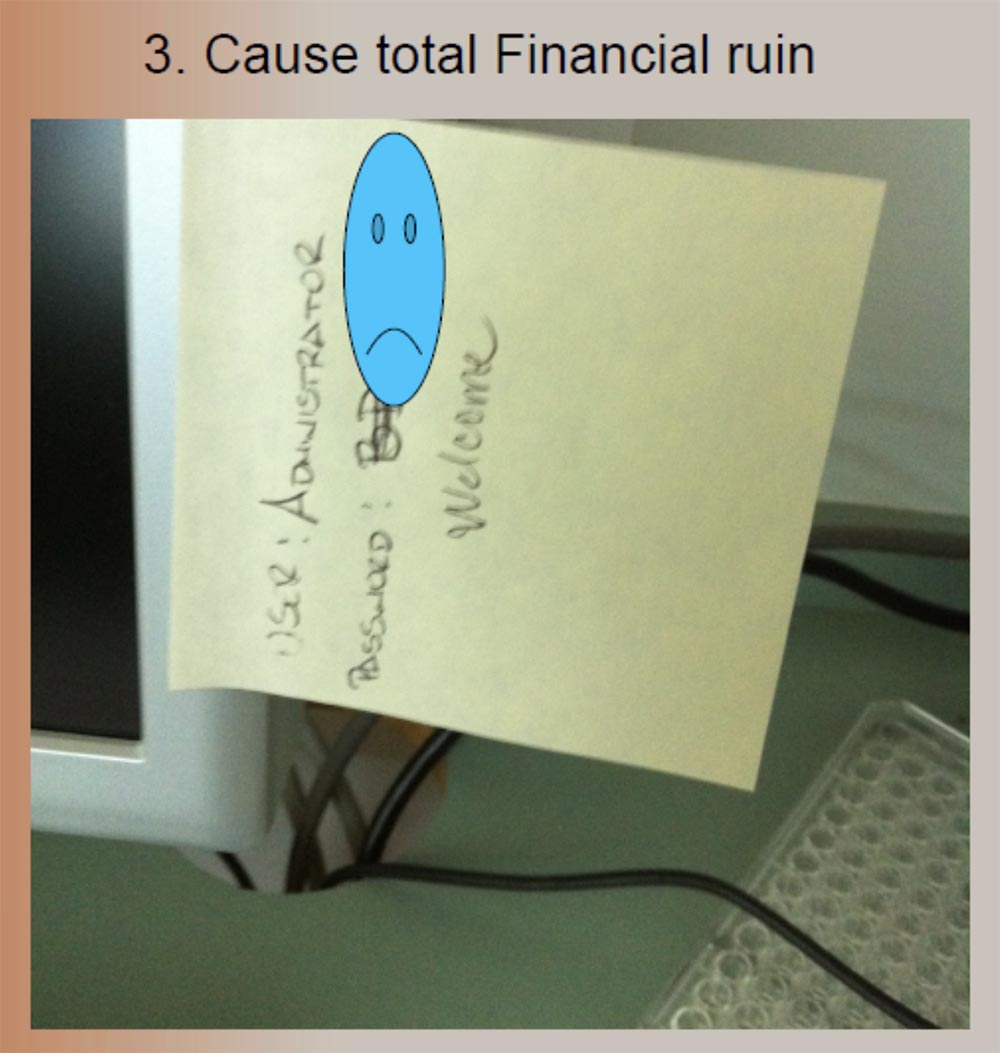
. , . , . - , , Welcome. , !
, – , . , , «».

– , Wasted Doom, « », , .

«», , Wasted Doom 2.0. USB, , , , .

– 8 USB, , , . , . 3- , , , , .
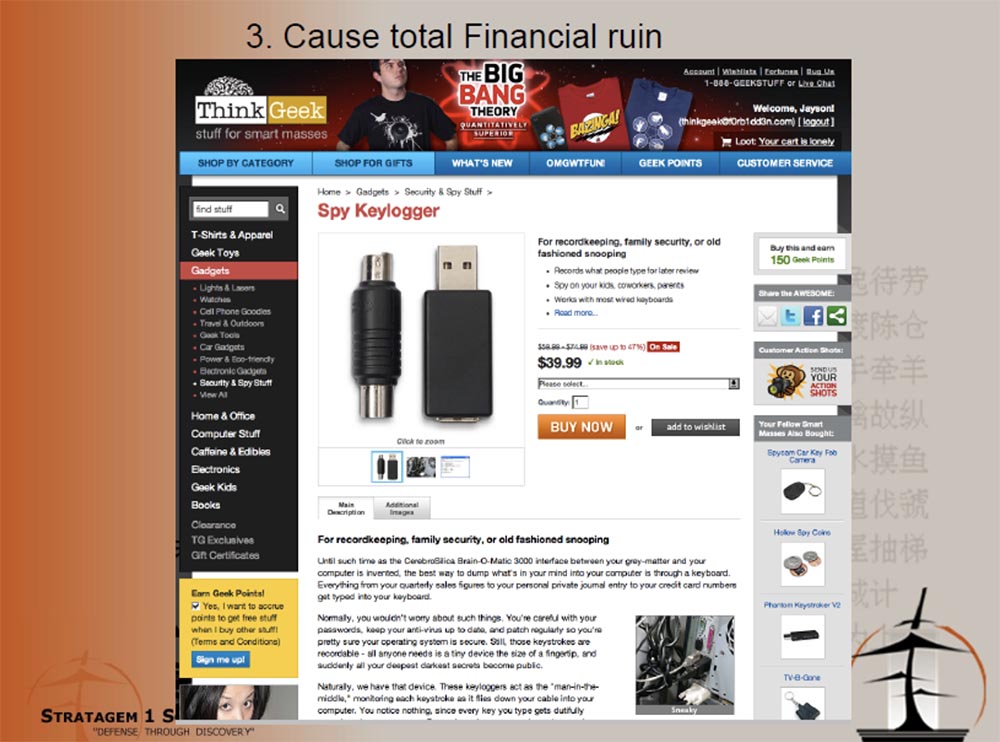
, , USB «». Spy Keylogger, , . , – 2 , USB PS2. , . Think Geek.
.

, Think Geek, – . , – , . , CEO, , .
, , . , , – . , ? !

, , , ? , , , , , . . – , ! , , , .
Pony Express . 4 , 4 , 4 . 4- , , . , , , .
DEFCON, , , , . , , , , , , , . , , , .

, - , , . , , , . , . , , , . , ! , , Pony Express. , , - .
:
, , , , , , . , , , : «, «» !», . – , , , ! , . , . . «», , , , .
, , , , , . , – , .
, 15 , , . «, », 16- . , , - , , . , . , : « , !», , , , . , - , .
You have a huge human potential to ensure safety, so just learn how to use it correctly! And as soon as you stop talking “stupid users” and start saying “my colleagues in the department of information security”, you will win!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

My presentation is called “Steal everything, kill everyone, cause a complete financial collapse, or how I entered and misbehaved!” Simply because it tells about the failure of the security system.
')
The signature on the picture with the kittens reads: “Army of darkness. Milder than you expected. ” The slide with the name of the presentation shows a sign with the inscription “The guard will return in 5 minutes”.

I am going to explain to you that physical security issues and everything related to them are our weakest point, because people oppose two-dimensional to three-dimensional and simple to complex, when they approach the entrance doors. You see that Jason I. Street has many more letters after the last name, so let me introduce myself first. I have a day job and a night job. My day job is that I serve as vice president of information security at financial company Stratagem 1 Solutions. I work in an office booth, surrounded by many interesting events. I watch the firewalls, watch the ID systems, I built our own infrastructure and I find more creative ways to protect it from those people who can “come for us”, and my main job is the “blue team”, that is, protection.
My night job is to perform the duties of the CIO - Director of Information Strategies, and I perform penetration testing about 3 times a year, this is my main job. I speak at such events around the world, I wrote the book “Dissecting the Hack: The F0rb1dd3n Network” in the genre of the documentary detective story, I write articles, and all this I do at night. During the day, I react to incidents, and at night I create incidents for other people, so it is more convenient for both parties.

I love to look at these photos. In this baseball cap and black glasses, I stood for an hour in front of the building of the protected industrial park, on Sunday, in the absence of other traffic, and a guard passed me twice, who did not even ask what I was doing on the sidewalk and why I was inspecting the protected building, and did not record this incident in the report.
In the second photo I’m wearing glasses, I’m just about to apply for a job, here I’m wearing a blackHat-colored shirt, because I like to go with “warning stickers”. I never got this job because I was not qualified enough, but I managed to get their data. That was my victory.
On the next slide, you see two more photos that I like too.

T-shirt with the inscription, I think the best, because in it I almost stole a car. I was in a hotel on the coast and the parking attendant provided me with a car, but I explained to him that I could not take this car right now, he asked why, and I answered - because I would steal it. Apparently, he bought the inscription on my T-shirt "I am the source of trouble," and decided to give me someone else's car. It took him a while to understand what I mean, so I had to say to him: “You have to take her back, because the owner may need it.”
The next shirt is my favorite. At one of the most guarded objects I’ve seen in life, directly opposite Ground Zero, the zero level of the World Trade Center in Manhattan, the SWAT squadron, these K9 with their machine guns, pass through the hall to the main elevator, which is guarded by 8 guards. the upper floors I go to myself in a shirt with the icon "Geek your company." Yes, I like this photo the most, and later I will tell you about this story a little more.
I have a CISSP (information security certificate from a non-profit organization International Information Systems Security Certificates Consortium), and I think that according to the ethical code I should mention that in my presentation I used quotes from the treatise “The Art of War” by Sun Tzu, a Chinese strategist and thinker of the V century.

So, my presentation consists of these parts:
Introduction;
Fact - one fact that we will encounter when discussing this topic;
Rules - 2 rules that I thought up while doing my job;
Results - we will have as many as 3 results arising from these 2 rules;
Conclusions and / or discussion.
So why this particular topic? I talked about this last year at the 36 CHARGE conference, I talked about the beginning of social engineering, about the things you could do to try to get into a protected building. It was the first part and, to be honest, I received some feedback after that, and I was approached with all sorts of difficult questions.
But I am not an expert in the field of social engineering, I do not know anything about neurolinguistic programming (NLP), I do not know the methods of face recognition or ninja technology. However, I have 100% success in entering buildings, I just go there when I use the skills of this very social engineering. But believe me, I’m not strong in it, it’s just our modern security.
I think you will not learn anything new from me, so this is rather an educational lecture that will show you the beginning of the path, but I hope that after it you will remember what will force you to look around and take a fresh look at things that you seem to know. and improve your perception of the environment.
But now I will not talk about social engineering, so this is all the damage I was able to do after your security guard let me go through the front doors.
So, fact number 1: I sneaked inside! I took this photo as soon as I opened the door and went up to the hall. I saw the door for the staff, this was the door to the protected area, and I just went through it by pressing buttons 1-3-5.

I could press 5-3-1, or 3-1-5, it does not matter, I would still open it, because I pressed the buttons, the surface of which was wiped from frequent use more than others. I returned from there 10 minutes before the beginning of our meeting, and no one found out that I was there.
Another fun occasion was when I went to get another job. I decided to be a bad guy, and when I signed my name at the reception, I stole a pen from them. Then I asked where their toilet is. This is not because I drink too much dietary cola, I just “get lost” in these large buildings and can wander for hours in search of this toilet, while looking around the entire building.

In search of a toilet, I unexpectedly came across a protected part of the working area and found an entrance for staff. It looked as if the guard of this object was showing off its security systems worth a million dollars, but when I looked at the door, I saw a little thing, a rod that holds the door latch. If I had a condom, I would adjust it to keep the door from closing. And then I remembered the stolen handle, screwed the cap off it and put it on the rod, and the door did not click. When I returned there 20 minutes after walking in the "forbidden" zone, the cap was still there. No one knew that I was on a guarded object, and it was fun!
So, I am not a locksmith of the highest category, and I do not need to be a master of locks so that people let me through the front door. I don't need to be a super ninja coder to just steal a hard disk with data from your computer. This video shows my hacker skills and a unique master key - the cover of a cardboard folder. I simply insert a sheet of cardboard between the doors of the closed door, take them up and down, and the doors open with such a simple “key”.
Next on the slide is another “key” - a fake email I placed on the iPad. If you just print it out, it will look like a fake, they will tell you: “you just printed it yourself!”, But seeing it on a tablet with these blue hyperlinks, they say: “oh, this is magic, it must be true”!

I had to get to a protected facility in New York, because the network administrator noticed that there was a lot of network traffic coming from the computer of the company's deputy CFO. Therefore, such a cool network specialist, like me, had to get on this object and figure out what was happening with the network. Such was the legend, and I spent 2 hours in Google Docs, writing this letter. So, it says here that the new owner of this company was very upset by this sad event and appealed to another company asking it to send its best network specialist, that is, me, to check their main server. Well, the second letter was addressed personally to me as if from the director of information security of the second company, and he wrote that I should give up all my affairs and arrive there by tomorrow. And that I have to do the job as “excellent”, because “many eyes” are looking at this project. In general, I made it so that it sounded urgent and politically, so that no one was particularly surprised at my arrival. I showed this letter to the “network guy”, he took me to the office, we talked to the director of information security for 10 minutes. And then this guy accompanied me on all the desktops with computers, but I could freely insert my flash drives wherever I wanted and do whatever I wanted. So I really loved this letter.
So, I don’t care about your credit cards, I don’t care about the Sarbanes-Oxley Act, the ISOs, that Leicester got Linux, I just want to fuck you, spoil your mood in the worst possible way, I want to be the worst may happen to you at the worst possible time. Remember the kittens?
So here are 2 of my rules that I took from the Serenity movie: “I want to go ugly” and “Let's be the bad guys.”

It's like a red team against a blue one, so don't be offended if I hit you below the belt. It’s like the bankers kidnapped and held hostage by their whole family until the robbers open the doors of the bank. This is not funny, it really is still happening. This is one of the things about which people say that there is nothing new in it. The concept of what we are doing is taken from the 1992 movie Sneakers. It’s as if people are hiring you to break into places to make sure no one can hack them.
Now this business has become better, but still, the concept is preserved, it is not new, and there are people who understand this better than me.
Another thing we need to understand is that management is a response, not a warning. I will quote the words of Dana Erwin, a security officer at Dow Chemical, in 2008: “The best way to draw management’s attention to a disaster plan is to burn the building across the street.”
Greetings to all present - I am that fire! And now we come to the fun part of the speech, in which I will talk about several ways of kindling such lights.

The inscription on the demotivator: “Prostaki. Even the ducklings know how to recognize them! ”
Next on the slides, what I call “use bad facts” is depicted, because I stole this phone, I “raped” this laptop, and 30 laptops in this office did not have anti-theft cables, because the management thought that they were already “ protected. " When I got there, they just equipped laptops with anti-theft cables, and one guy left his laptop with a cable and a screwdriver on the table, probably so that the thief would be comfortable unscrewing the cable if it were connected to a laptop. But since I was hungry, I stole only cookies from his table.


You know, people believe that security should not be so thorough that they use anti-theft cables to protect their laptops. Because you have to attach it to the table, and this is difficult, you need to bend, so let's just run this cable over the table, because no one will pull it. And you know that most of the guards really don’t try to pull this cable to check, but I’m not a guard, I’m a thief, I’ll pull him to try to steal a laptop.

Some guys use a combination lock, but I assure you that if this code is 0-0-0-0, I will try to dial it, if it is 1-1-1-1, I will also try, and I will try to dial even 9-9- 9-9. And if you are so clever that you pick up 0-0-0-7, because people like you like to move only the last or only the first wheel of the lock, I will try this option and open the lock anyway.

I'm going to go through all the drawers of your desk and all the lockers, and I will look for all sorts of things there. A decent and honest colleague will not look at someone else’s table, what lies there, but I’m not like that. On the slide to the right, you see the laptop of one guy, he fixed the laptop perfectly, and thought that now that he has such a shiny cable, his laptop is protected from theft. But then he put the keys in the top drawer of his desk and crossed out all the security.
The next slide shows why I stole this iPod in a “retro” style, these car keys and driver's license. Because they were lying unattended.

Now imagine that I took her keys, went down to the parking lot, opened the car, and then put the keys in place. And after work, I would have been waiting for her in the back seat of a car with a gun in my hand. From the driver's license, I would have recognized her home address, and could have sent people who would have killed her family if she had not returned to work and stolen the necessary data for me.
Workers should know that their personal belongings belong only to them, but their theft can inflict a serious blow not only on them, but also on the company in which they work. Therefore, they themselves must ensure the safety of their belongings. Let's once again remember the cute kittens from the first slide.
Look at the next slide, do you know why there are so many sad emoticons? Because this is a complete “game over” for the owner of this wallet - there is an empty checkbook, credit cards, ID and social security card with the owner’s signature.

When I was going to steal my first car, there were too many people there, and then I came at 2 am and opened three Mercedes-Benz and one Beamer and it took me less than 60 seconds, as in the movie with Nicholas Cage You should have seen the security manager when I came to him and threw 4 keys from these cars on the table - the expression on his face was simply indescribable.

By the way, I included this slide in the presentation - this picture of the desktop in my home.
Therefore, I would like employees to take countermeasures against theft, to lock the boxes at work, even if they leave the workplace for a short time, not to leave wallets, credit cards, checkbooks on the tables, to ensure the safety of their property at work and at home, the safety of their property. machines. I want them to understand that it is impossible to pass by a “tail” to two people on one pass and explain to others that this threatens their own security. You can not send anyone a certificate issued by your company, you can not leave your computer, laptop and smartphone unattended. Finally, if you see a suspicious person, or someone who should not be inside or outside the building, immediately inform the security or the police.

Do you know what I did once? I appeared in a wheelchair with 4 books in my hands. “Jason, you are a jerk!”, And I’m all so — yes, I’m trying to rob you, you really think that I’m worried about my inferiority, because I don’t have to be in this wheelchair? I’m evil, I’m really going to do THAT, and you just let me pass inside the protected object with these 4 books.
I want to note that you don’t have to push the handicapped person out of the door yourself, or open the door in front of him if you are embarrassed or afraid to offend him. But if you saw something suspicious - say so. Remember that any employee is part of the company's security system. If you consider something suspicious, do not hesitate to report this to the guards, it is their job to check all suspicious visitors.
So, we figured out what it means to “steal everything”, so now let's talk on the topic “kill everyone”.
This slide shows a photo taken at 2:30 am on Sunday night in the hotel’s basement working area, I went there in my pajamas and barefoot because I took off all my clothes in the bathroom of the guest area and thought what I could do here and how It turned out I could do a lot. I entered the room with mechanical equipment and saw that there were no locks on any of the switches.

Imagine that I have something like OBS, obsessive-compulsive disorder, I'm crazy, and if these switches are turned off, I turn them on, if they turn on - I turn them off, if there is a red button, then I press it twice, but do not think that I am a complete moron. If there are any toxic chemicals there, they will catch fire and smoke will go into the ventilation and a fire alarm may be triggered. , , , , .
, , – , . , , 2-30 ! ! , .


, , . , , .

, . , , , .
, . - , . , , . . . : «, »!

: « «» «-47», -4, , , . , ». , .
, , . . , : «!», , . , , , , , .
, , . , 2 , . : « ?», : «!», . , , . , , , . , , , . . , , – WI-Fi , , iPad , .
: , , . :
- ;
- , ;
- , / , , / , ;
- , , ;
- ;
- , , , , , .
, , , . , « , , !», . Periwinkle () : « ? !» . , - , .
. , , . , , . , , . , , , , . , , . , – , . : « !». , , , .
– , . – , .

, ? ! , , ? , , , . ! , , .
, – . , , , .

, , , , , , . , ? ! , , , . .

, - , USB . , . , ? 25 , , , – ACCOUNTING . , .

, - – , .

, ? Linux, , . .

, .

. , . , . - , , Welcome. , !
, – , . , , «».

– , Wasted Doom, « », , .

«», , Wasted Doom 2.0. USB, , , , .

– 8 USB, , , . , . 3- , , , , .
, , USB «». Spy Keylogger, , . , – 2 , USB PS2. , . Think Geek.

.

, Think Geek, – . , – , . , CEO, , .
, , . , , – . , ? !

, , , ? , , , , , . . – , ! , , , .
Pony Express . 4 , 4 , 4 . 4- , , . , , , .
DEFCON, , , , . , , , , , , , . , , , .

, - , , . , , , . , . , , , . , ! , , Pony Express. , , - .
:
- , , .
- . , .
- , , , .
- . , .
- , .
- , . , .
- — . , . , .
, , , , , , . , , , : «, «» !», . – , , , ! , . , . . «», , , , .
, , , , , . , – , .
, 15 , , . «, », 16- . , , - , , . , . , : « , !», , , , . , - , .
You have a huge human potential to ensure safety, so just learn how to use it correctly! And as soon as you stop talking “stupid users” and start saying “my colleagues in the department of information security”, you will win!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/418291/
All Articles