Cyber battles on PHDays, or How to hack urban infrastructure in 30 hours

For the third year in a row, the Main Competition of the Positive Hack Days Forum remains The Standoff , a cyber battle between the teams of attackers, defenders and expert centers of security (SOC). The games of 2016 and 2017 showed that the format of competitions as close as possible to reality is understandable and interesting not only to participants, but also to conference visitors. Therefore, the organizers did not have any doubts about doing or not doing The Standoff this year. A total of 19 teams participated in The Standoff 2018.
For almost 30 hours they fought for control of the city. The defenders steadfastly defended the objects entrusted to them, but the attacker still managed to hack something: some objects were deliberately left without protection by the rules. But the battle between the attacking teams themselves was hot: the standings changed dramatically literally half an hour before the end of the game. We tell what happened on the site for two days.
')
First day: the attackers test the ground
The day was not very eventful. The attackers took a long time to scout the situation and carefully examine the objects of the playing range. According to legend, the battle unfolded in the city, the whole economy of which is based on digital technology. The city had a CHP and substation, a railway, several offices, smart houses with energy recovery, banks with ATMs and self-service kiosks, cellular communications, the Internet and various online services.

Layout of the playing ground
To help the attackers, there was an internal portal that hosted general information about the infrastructure and a list of high-level goals that they needed to achieve. For successfully completed tasks, the organizers charged the teams with public (the virtual currency of the city). According to the rules of the game, the team of attackers that won the most of the posts won.
The first attacks were recorded closer to dinner. The victims were some objects of urban infrastructure, which included control systems for cameras, traffic lights and ventilation.
The “Antichat” team discovered vulnerabilities in the cameras and launched a denial of service attack. At 11:20 the team gained access to video surveillance systems and for two hours tried to disable them. As in life, simple passwords were installed on some cameras that could be easily picked up. As a result, some of the cameras were simply turned off by the attackers, while others were disabled by publicly available exploits.
Next "Antichat" aimed at the heating system. The team gained access to the controller that controls the heating and ventilation, and began to turn the heating on and off. However, the organizers partially counted this task in the bug bounty program, since under the conditions it was necessary to disable the ventilation and traffic light control systems.
At 12 o'clock, the team of "CARKA" discovered vulnerabilities in the software of the automated process control system, but could not navigate in time to use this chance and break into the infrastructure.
At about the same time, the Rostelecom SOC team, which monitored an unprotected office - according to legend, the engineering company Sputnik, made a report on the main stage of the forum. She said that one of the attacking teams managed to crack the office network using brute-force and exploitation of vulnerabilities and get domain administrator rights.
In the middle of the day, “CARKA” dropped the passwords of all the subscribers of the portal to the telecom operator and tried to sell the dumped records to the buyer on the black market, but he realized that they were fictitious and refused to buy. The telecom operator immediately after receiving complaints from subscribers, restored accounts from the backup and closed the hole in the portal. Then the team tried to hand over the bug bounty account, but for that she earned a penny. Note that this was not the omission of the protection team, as the organizers temporarily asked to disconnect WAF from the portal to install updates and test the new functionality, which the attackers took advantage of.
Telecom advocates - the team “You shall not pass” - noted that hackers were mainly aimed at hacking the portal and web interfaces. Most of the resources related to the telecom were controlled by advocates, but according to the organizers, some of the resources remained unprotected. For example, the team did not protect against theft of uchetok, resetting passwords in the personal account and intercepting SMS messages, and the SOC ANGARA team only recorded these incidents, which the opponents subsequently took advantage of. By the way, You shall not pass also told us about the attempts of the attackers to apply social engineering: some of the participants, remembering last year’s successful experience of the CARK team, tried to get data from the defenders, introducing themselves as journalists. But the defenders were not led to the cunning tricks of rivals.
Later in the evening, the attackers learned that the city F has its own cryptocurrency. Participants had the opportunity to earn additional publics on distributed DDoS attacks tied to the blockchain. The first team that decided to make some extra money turned out to be “CARK”: at about six o'clock in the evening they broke into one car to use it for mining.
At eight o'clock, “CARKA” discovered vulnerabilities in the automated process control system software, but could not navigate in time to use this chance and break into the infrastructure. Therefore, the team switched to other objects: at nine it became known that she had found the car using GPS coordinates. A little later, the teams of “CARK” and Sploit00n almost simultaneously hacked the subscribers of the telecom operator: they intercepted SMS messages with compromising information to the city’s top insurance company manager. Note that subscriber data security was not controlled by defense teams. For the successfully completed task, the attackers received 250,000 posts each.
At the end of the day, unknown attackers attempted to reset accounts from SIP telephony online, but due to timely editing by defenders of the Asterisk computer telephony application configuration, which complicates online brute force, this attack was not successful. The attacker apparently didn’t have enough time for preliminary preparation: they tried to get rid of non-existent phone numbers: valid numbers were 10-digit without a country or city code, and participants brutalized 9-digit ones.
A bit later, a report was made by the team of bank defenders Jet Antifraud Team, who said that during the day she managed to block 5 illegitimate transactions in the amount of 140 publications - one can say that it was a warm-up before night attacks.
At the end of the first day, the organizers, who watched the confrontation, noted that the participants were cautious at first and did not attempt to make serious attacks. If the attackers acted, it was very straightforward and their activity was very noticeable. By the end of the day, many attacks were still in the initial stage, since the attackers did not understand how to develop them further. For example, having hacked an unprotected office, they did not immediately guess that Sputnik was the management company of the technology segment, and the teams did not use the resources obtained to mine the local cryptocurrency.
Nevertheless, for all this time about a hundred bug bouncey vulnerability reports were submitted, accounting records and bank card data were stolen. For these tasks, the attackers also received money in the game currency - a little, but due to the number of some teams managed to collect a serious account (100 thousand - 200 thousand publishers).
Defenders, taught by the experience of past games, predicted that the attacks would begin closer to the night.
Night is a time for dark affairs

The Standoff members
As expected, all the fun happened at night. As soon as the game day ended, the hackers became more active and tried to exploit the vulnerabilities they discovered during the day. And at once in several points of the city became restless.
The Jet Antifraud Team recorded massive attacks aimed at stealing money from the accounts of city residents. By the way, a total of 500 accounts were opened in the city bank, the total amount was 3 million publ. The attackers tried to withdraw money — or rather, to drive them a little bit between accounts and test the bank antifraud for strength. Three major attacks occurred in the period from 10 pm to two in the morning. In total there were about 20 thousand attempts to commit fraudulent transactions on 19 fraudulent accounts. At the same time, 100 accounts were compromised, but the bank did not lose a single ruble at that time.
After midnight, the True0xA3 team decided to compete with "CARK" and hacked into one computer for mining cryptocurrency. During the night, both teams were able to organize a small mining botnet.
Toward morning, an unexpected temporary truce happened between the attackers and the defenders. Together they began to study the infrastructure of the technology segment. Note that since last year, the industrial sector has changed significantly. The layout included hydroelectric power stations and CHP, distribution substations, a refinery, transportation and storage of petroleum products, a railway and automated warehouses, a crane and installations for bottling liquid petroleum products, building automation BMS and life support, video surveillance systems, smart homes. Real software and hardware of such vendors were used: ABB, Advantech, Belden, GE, ICONICS, ICP DAS, Kepware, Loxone, Matrikon, Moxa, Schneider Electric, Siemens, Phoenix Contact, Rockwell, Prosoft. The organizers used software and firmware versions with known typical vulnerabilities and configuration errors, which in practice are most common.
When attempts to gain remote access to the automated process control systems did not succeed, the teams began to connect locally and, under the supervision of defenders, scanned to create a network topology, exploited known vulnerabilities, but did not carry out full-fledged attacks on industrial systems.
Second day: unexpected turn of events

Mockup of the standoff
On the second day, the attackers got to another office - according to legend, it was an insurance company of the city F. At about 9:30, the SCS team managed to obtain personal data of the company's clients. As the teams of defenders SRV and SOC “Advanced Monitoring” reported, some services were hacked. One linuksovuyu machine long tested the strength of brute force passwords. In the end, using the advanced dictionary, SCS hacked accounts. Next, the attackers tried to gain a foothold in the system and attack internal services bypassing the NGFW, but activity was stopped. At about the same time, SCS selected a computer captured by “CARKA” for mining, but the defenders quickly discovered and eliminated the miner. In just one day, the WAF of the SRV defenders team repulsed about 1,500,000 attacks, and the Advanced Monitoring team opened up 30 security incidents.
After lunch, the teams SCS, EpicTeam and Level 8 tried to sell for 250,000 posts on the black market, compromising dirt on a top manager of the city’s insurance company, found in SMS messages. However, one of the teams was unable to document that this correspondence belongs to the top manager (this information was not available in the data), so she received only 100,000 publications for this. Another team was able to intercept only part of the correspondence. The buyer on the black market, of course, also paid for this information, but not as much as the attackers had expected - only 150,000 posts.
Meanwhile, the True0xA3 team began actively exploring energy facilities and sending the first vulnerabilities to bug bounty. The found exploit helped them at 15:19 to carry out an attack on the CHP substation: the team disabled the protection terminal, thereby creating an emergency.
In the middle of the day, a team of Jet Security Team defenders and RT SOC reported that the attackers had full control over the unprotected office of the Sputnik company: they found outlets to the automated process control system of the oil sector. At night, despite numerous attempts, the attackers failed to break through the defense systems, but during the day these attacks were developed. It turned out that Sputnik did not ensure the security of its Wi-Fi network, so the teams were able to access it. In addition, accounts were found for remote access via TeamViewer to the machine of the process control system engineer. Forwards, of course, used it for their own purposes and intercepted control over the session. By this time, no serious attacks were recorded, but the Jet Security Team and RT SOC teams predicted sabotage in the oil sector.
I did not have to wait long. By the end of the day, unknown attackers carried out a local attack on the oil supply systems from the tanker: approaching the equipment directly, the attackers made (possibly by accident) a loop in the local network, which led to a loss of communication with the programmable logic controller and SCADA simultaneously. Because of this, there was an oil spill on a tanker, but without serious consequences. Nevertheless, such a careful and attentive work on the protection of the automated process control system (from total monitoring to reconfiguration of networked industrial devices), which the Jet Security Team team demonstrated, is rarely seen in real life.
But the most interesting thing happened an hour before the end of the cyber battle. The city abandoned the antifraud system. This was quickly used by the Hack.ERS and invul: $ commands. However, only Hack.ERS were the first to automate operations and in 20 minutes to completely clean out the bank - in total, they brought out about 2.7 million posts. This allowed the team to rise from the 10th line of the tournament table and get into the winners, knocking out the CARK team (the winners of last year) from the leaders. In just 30 hours, the cyber-battles Jet Antifraud Team, which defended the city’s bank, successfully repulsed 22,500 fraudulent transactions for a total of 97,000 posts.
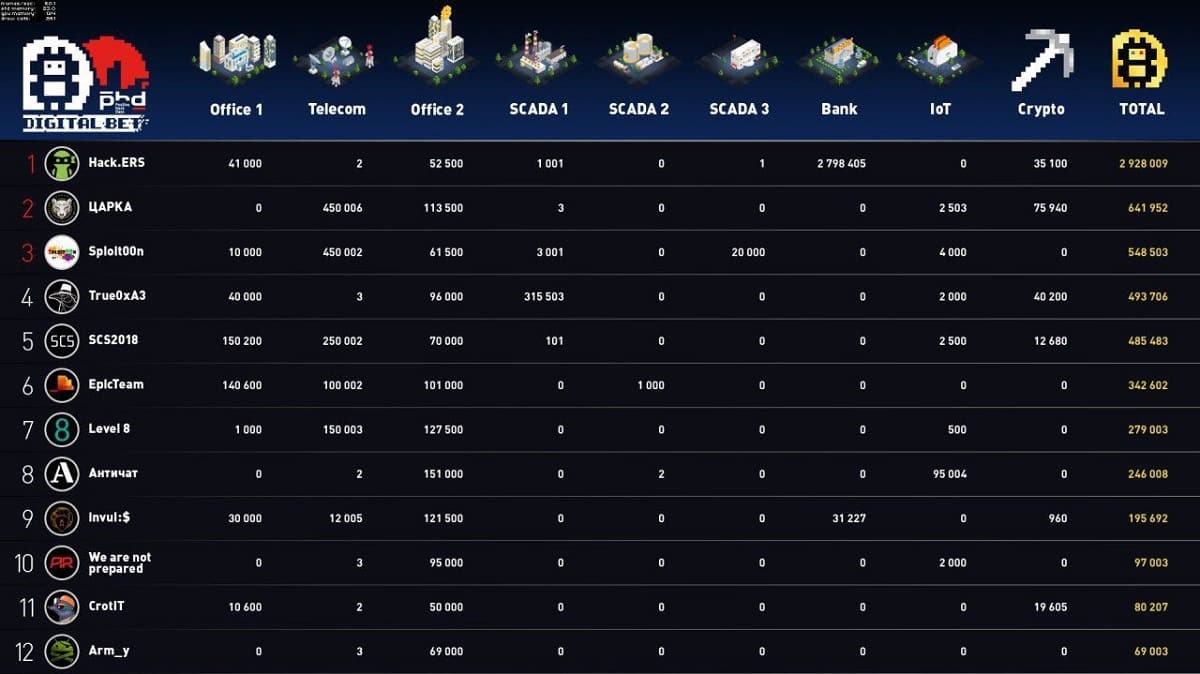
Final standings
Added heat and the situation on the cryptocurrency exchange. There are 6 main commands out of 12: “CART”, True0xA3, Hack.ERS, SCS, CrotIT, invul: $. As in real life, the course was constantly changing: the minimum was 5 boules per block, the maximum was 200 boules per block. In the last hour, the numbers have seriously changed. In total, participants named 1776 blocks: “CARK” - 620, True0xA3 - 515, Hack.ERS - 355, SCS - 133, CrotIT - 104, invul: $ - 48. In two days, the teams earned: “CARK” - 75940 posts, True0xA3 - 40,200 posts, Hack.ERS - 35,100 posts, SCS - 12,680 posts, CrotIT - 19605 posts, invul: $ - 960 posts.
Already in the last minutes of the competition, the True0xA3 team arranged a blackout in the city. This attack was a logical continuation of the actions taken by the team the day before. All this time, the participants studied the booth, read research on the safety of automated process control systems and searched for the necessary utilities. Using the vulnerabilities of the MMS protocol, they managed to cause a short circuit. By the way, the same attack was already carried out two years ago on PHDays VI. This was supposed to be prevented by the protection system, but True0xA3 could turn it off the day before. Finally, the railroad got: True0xA3 took control of the locomotive, but did not have time to do anything, and Sploit00n found several vulnerabilities in the automated railroad warehouse, which allowed the PLC logic to be changed, but the team also did not have time to make modifications.

Layout of the railway
For two days, events at the site were also monitored using Positive Technologies products: MaxPatrol SIEM system, network security solution for analyzing network traffic, detecting and investigating incidents PT Network Attack Discovery, multithreaded system for detecting malicious content PT MultiScanner. For all the time only one PT Network Attack Discovery registered 11,769,526 attacks. About what attacks recorded the decisions of Positive Technologies, and their detailed technical analysis - in our next article.
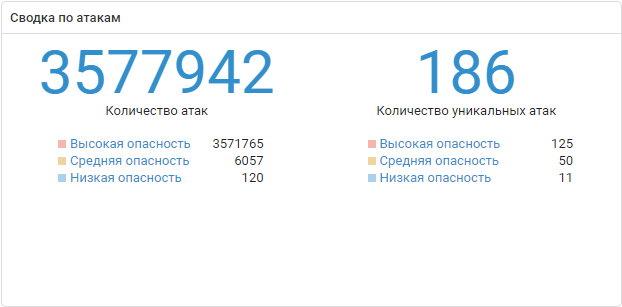
The number of attacks on objects of the city F in two days
Results: friendship won
At the end of two days, we can say that friendship has won. The Standoff 30-hour cyber battle has once again confirmed that the information security specialists are able to provide the highest level of protection without affecting the business logic and technological processes of the systems. The attackers did not succeed in breaking into the protected objects; nevertheless, the teams demonstrated what the negligence of information security could lead to. Some facilities and infrastructures were left completely unprotected (as is sometimes the case in real life) in order to make the competition more realistic and visual. Well, so that the defenders did not abuse their position and did not affect the work of the objects entrusted to them (for example, did not turn off services for the sake of security), the organizers launched special programs to check their availability.
The first three prizes were taken by Hack.ERS, CART, Sploit00n. The remaining results are in the final ranking .

The Standoff Winners - Team Hack.ERS
Ilya Karpov, an expert on the safety of the automated process control systems and one of the organizers of the stands of industrial facilities, believes that the defenders won, despite the fact that the attackers were able to sabotage and lower the grounding knife to the ground at the CHP substation.
“The oil sector, despite various embedded vulnerabilities, configuration errors, access points and even the possibility of physical access, was reliably protected by the Jet Security Team. We didn’t see the complex vectors of attacks with a change in the logic of work this year: nobody got to the controllers, because the defenders worked 100% and took everything under control. Nevertheless, the True0xA3 team was able to figure out on the move how the substation works - their attack was the most difficult in all two days, ”said Ilya. “For the second year in a row, we expect attacks on network equipment, since it is they that occur everywhere in real life, but at the competition they are still without proper attention.”
According to the member of the PHDays organizing committee, Mikhail Pomzov, the attackers could achieve more:
“This year all the tasks that hackers faced were designed for logic. The game had hidden goals that appeared after performing certain actions or upon the occurrence of an event. For example, by gaining access to an account on one portal, it was possible to penetrate into other segments. The attackers also acted more straightforwardly and did not promote the attack - they handed over tasks and received money. Perhaps they just did not have enough time. "
PHDays organizing committee member Mikhail Levin summed up:
“The annual goal of our event is to pay attention to the problems of information security, to demonstrate modern attack scenarios and ways to counter them. I think that this year we succeeded. It is impossible not to note the turning point of the game, when the attackers and defenders joined forces to study the technological segment of our cyberpolygon and learn how industrial organizations work. Still, in real life, team members are information security specialists who build security systems every day, resist attacks and investigate incidents. In order to protect these objects in practice, they need to understand how it works. Our The Standoff gave them the opportunity to exchange experience and master modern penetration testing equipment and tools in conditions as close as possible to real ones. ”

Defense teams
Source: https://habr.com/ru/post/417927/
All Articles