How Tinder (slightly) hides your location
This year, you and your buddy Steve Stevington started a user tracking startup. The business is based on a leak of WhatsApp metadata that you discovered . You both would have to learn more about management, but still the company has grown into a powerful, though unstable company of 65 assorted trainees and students, freelancers and unpaid employees on probation. You recently moved to a dandy new office in the 19th century literature department of the San Francisco Public Library, and you have an enviable reputation in online marketing.
But under this glossy and dubious appearance lies rot. You suspect that your good friend, co-founder and co-chief executive Steve Stevington is plotting against you. He always runs out of the library at a strange time and disappears somewhere for hours on end. When you ask him where he is going, he builds a strange grimace, which he probably considers a malicious grin - and says not to worry. You instructed librarians to follow him several times, but they are all terrible in field work.
You have been living in Silicon Valley for a long time - and you know what merciless villains happen when a large amount of money and user data is at stake. Probably Steve Stevington is trying to convince investors to push you out of business. You think that Peter Thiel will support you, but it’s hard to say about Aunt Martha. So you need to figure out where Steve goes.
Fortunately, he is an avid Tinder user.
')
To determine the direction of the search, you looked at past leaks from Tinder users. There were several. In 2013, it was discovered that the Tinder servers send the exact coordinates of potential matches to the mobile application . Based on them, the application calculated the distance between users, but did not display coordinates in the interface. However, an attacker could easily intercept Tinder's own network traffic, check the raw data and determine the exact location of the target.
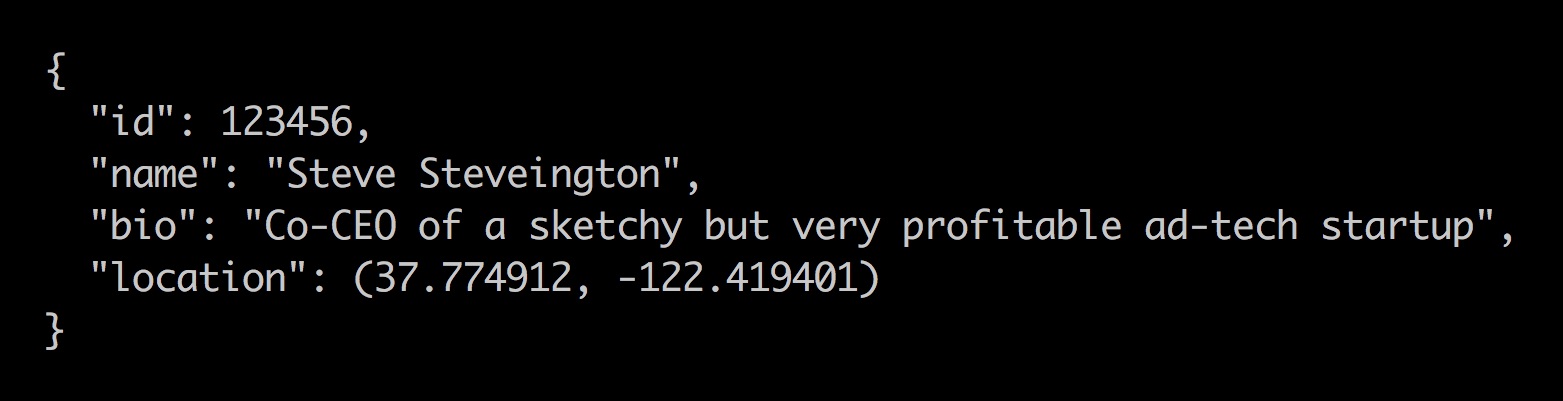
Tinder API response including exact location
Tinder tried to quietly fix the vulnerability by shifting the distance calculation to the servers instead of the application. After that, the network messages sent from the server to the application contained only these pre-calculated distances without actual locations. However, Tinder casually sent distances in the form of non-rounded numbers with 15 decimal places.
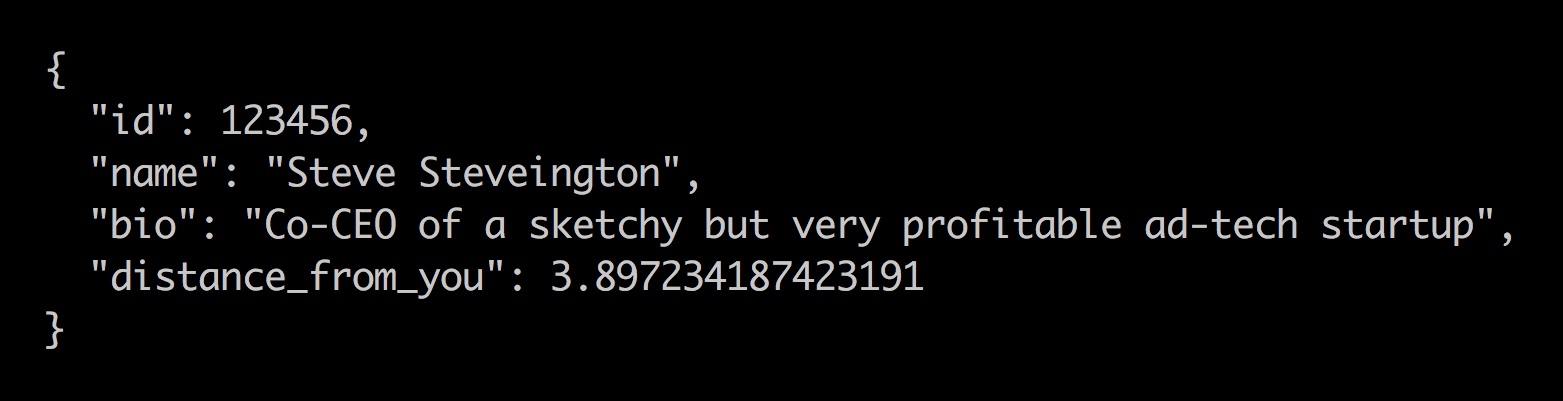
Tinder API response including exact distance
This negligence allowed the cunning researchers to again determine the exact location of the targets using an exploit for trilateration. The researchers sent three fake coordinates to Tinder with different locations of the user. At each new location, they asked Tinder how far the target was. Then three circles were drawn on the map with centers in fake coordinates and radii equal to the distances obtained. The point of intersection is the coordinates of the target with an accuracy of 30 meters.
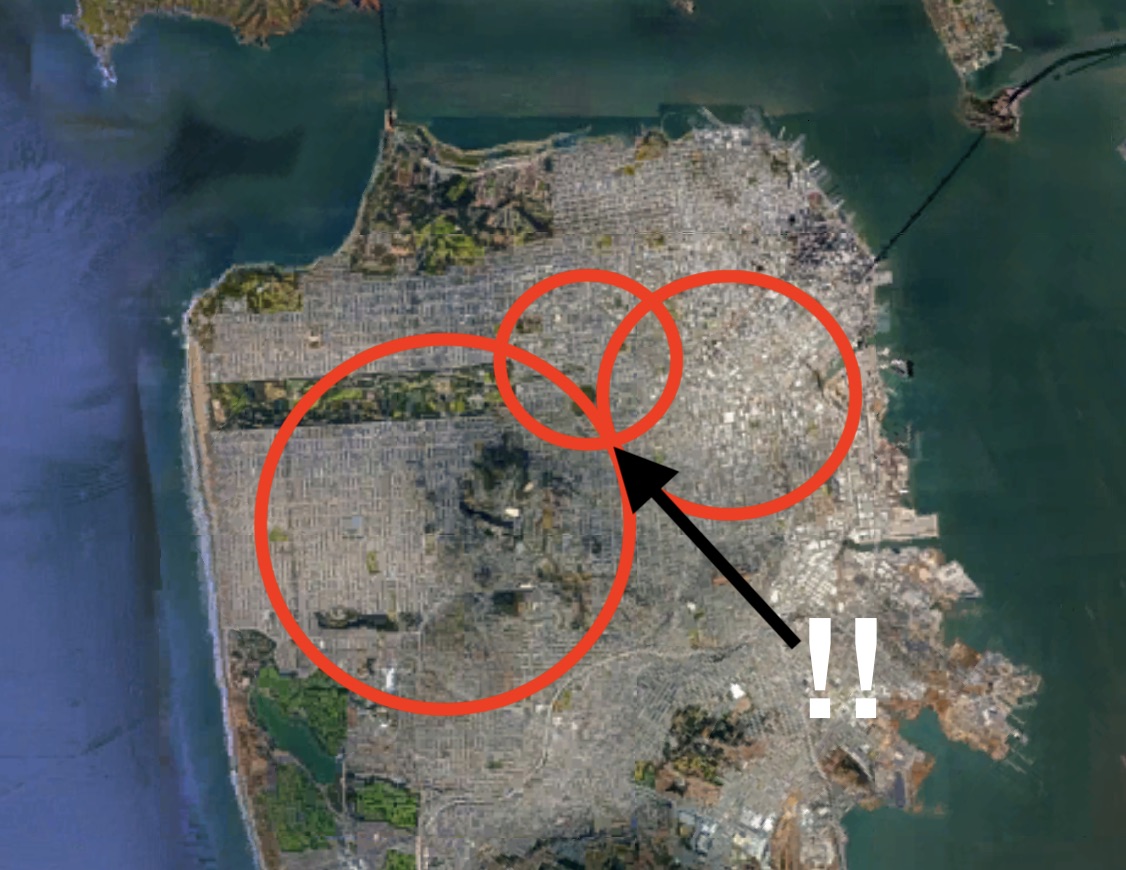
Tinder Trilateralization Example
The Tinder security team looked at these people, who constantly force them to work, sighed and quietly fixed the vulnerability. Now Tinder sends distance, rounded to kilometers, to the application. You can still use this trilateration procedure to determine the coordinates of a target within a kilometer or so. But in the densely populated city of San Francisco, this will not give an answer, where does the sneaky Steve Stevington go.
On Friday afternoon, a gloating grimace reappeared on Steve Stevington's face, indicating that he was ready to perform various actions in unknown places. You have to figure out where he goes before it’s too late. You are locked in a private office - in the reading room of the library on the 4th floor. After fifteen minutes of deep breathing and even deeper thoughts, you had a plan to reanimate the Tinder exploitation and try to find out where the Stephenator is going.
Suppose Tinder now calculates the exact distances on the servers, rounds them to the nearest whole number, and then sends the rounded numbers to your phone. You can launch a new attack in the same way as with trilateration. Ship the fake Tinder locations and ask how far the target is. Tinder can answer "8 kilometers", which in itself is of little use. But then you can move one pixel northward asking for the distance with each step. The server will respond "8 kilometers, 8 kilometers, 8 kilometers, 8 kilometers, 7 kilometers." If your assumption about the rounding process is correct, then the point at which the answer changes is the exact distance to the target of 7.5 kilometers. If you repeat this procedure three times and draw three circles, then we will again use the trilateration exploit.
Go to action. While Wilson has gone to the toilet, you lend his phone for testing - you know that he is using Tinder, and the unlock code is visible by the finger on the screen. Speak to your unpaid probationary probationers so they won't call you on the phone and say nothing to Wilson — and hurry to a secluded and deserted corner of your office in the fiction department for older school age. There you open Tinder on both phones. You continue svaypit until you get a match, and then write a short script in Python using pynder to spoof Tinder API calls. You place Wilson in the middle of San Francisco Bay, and then you try to determine its coordinates by changing your location pixel by pixel to find the point when the distance between you changes from one rounded number to another.
But something is wrong. Evening came, supper time passed, and you have not yet found Wilson. You seem to be getting close, but not enough. Circles are sometimes painfully close to the intersection, but usually do not give a meaningful answer where Wilson is. You begin to despair. Right at this moment Steve Stevington can sign a new contract with Peter Thiel and Aunt Martha. Perhaps he has already updated your company’s LinkedIn page, renamed you “advisor”, “assistant” or “former CEO”. The library closes - and you move to the pantry. Wilson continues to call, but probationers on probation do not pass you. Even a fleeting thought of giving them a job jumps.

Frustrated, you take a step back and hit your head on the bottom shelf. Getting out of a heap of cleaning products, you are considering the possibility that the assumptions may be wrong. Tinder may not just round off exact distances. You take a snack from a library employee's refrigerator to help the thinking process. Stop drawing circles and start walking along the lines around the true location of Wilson, putting a mark on each change of distance.
At two o'clock in the morning everything becomes clear.
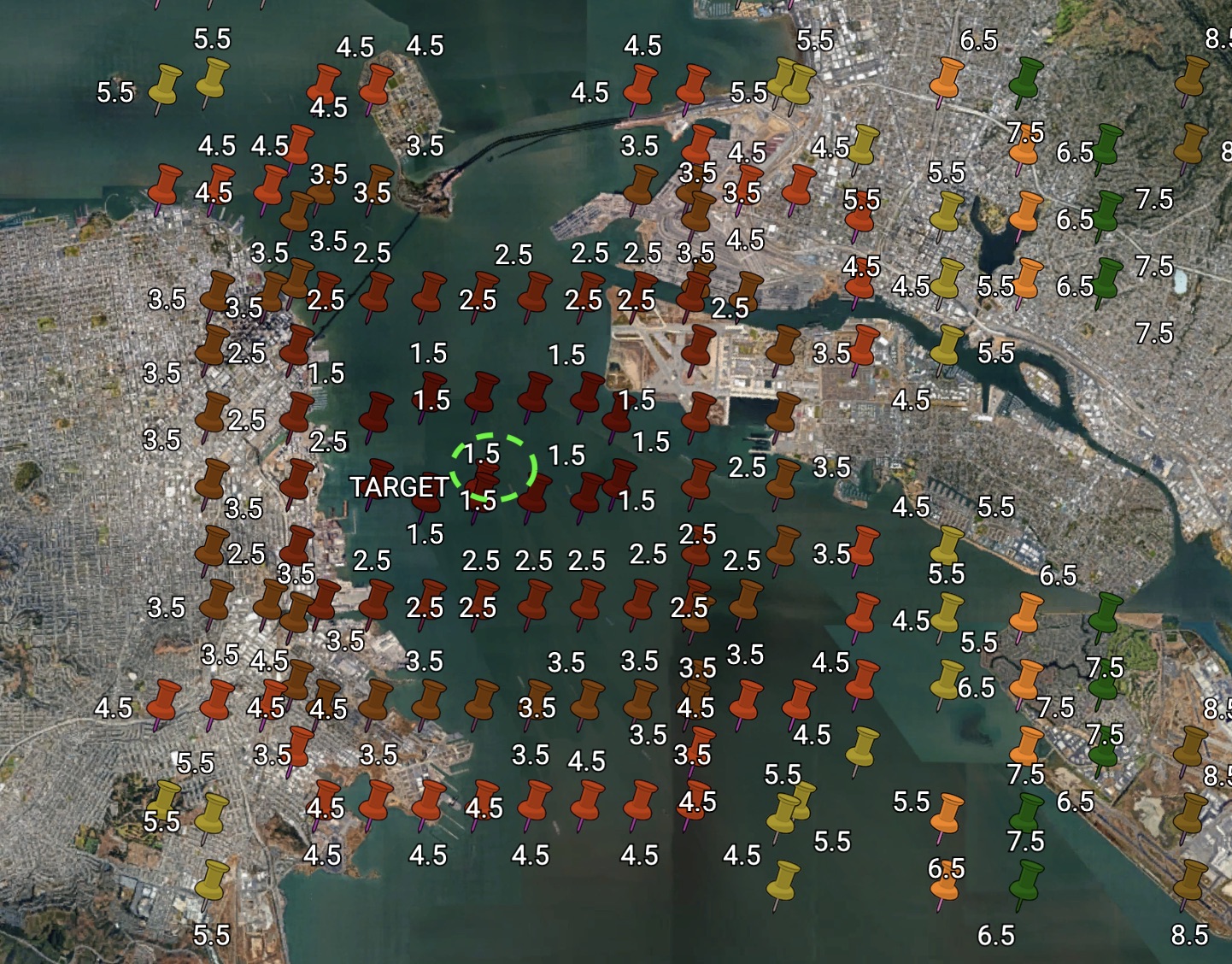
Placing Marks on a Map Based on Tinder Distances
Now Tinder so jealously protects the privacy of users, that it breaks the boring clips of ordinary geometry. He abandoned Euclid. He does not need the Haversinus formula . Instead, when calculating the distance between matches, Tinder uses two innovations.
First, and most importantly, it divides the city into squares of approximately 1 × 1 mile. When calculating the distance, the location of the target is tied to the center of the current grid square. Then, the approximate distance between you and this anchored location is calculated and returned.
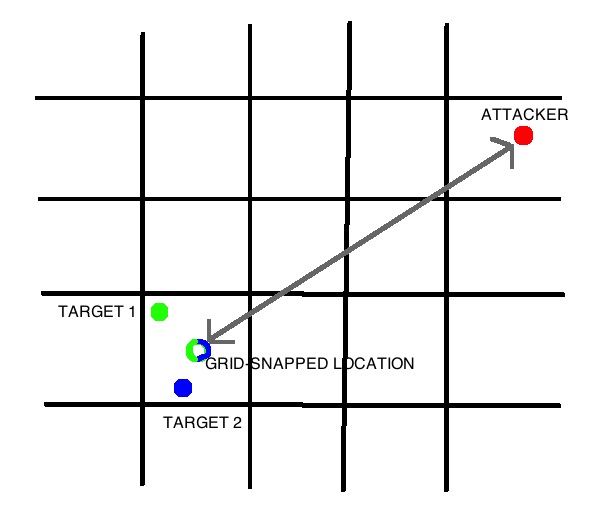
Tinder binds user locations to the grid
Secondly, it calculates distances as if by its unique formula. For this, a map of coarse, predetermined distances is taken - and superimposed on the center of the square of the target. Tinder looks up the attacker's location in this overlay and returns the appropriate distance. In the normal calculation of the Euclidean distance, this would be a set of concentric circles.

But Tinder seems to use a concentric squares overlay with strange curves at the corners as it moves away from the target.
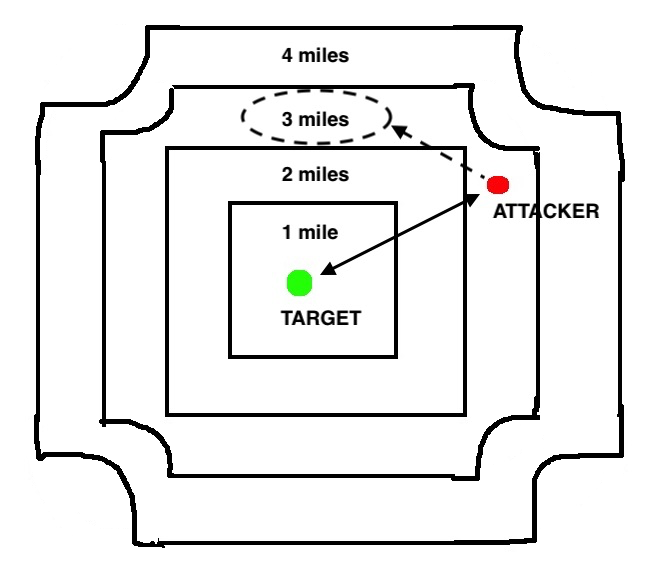
Among other things, this means that Tinder often returns slightly wrong distances. You suspect that rounding corners are necessary to adjust for too irregular distances, which are northeast of each other.
Mesh snapping is a key innovation in the Tinder approach. This means that Tinder will always return the same distance if the target is located anywhere within the specified grid square. Your trilateration exploit will not work. And if Tinder correctly implemented the grid binding, then no purely remote exploit will ever work. There is no way to find the location of a target with greater accuracy than the edges of one of the grid squares (approximately) 1 × 1 mile. Even such crude surveillance can make Tinder users think. But in fact, this is quite a reasonable behavior for the application, the main function of which is to tell strangers about where you are.
You really do not know why Tinder applies such a strange layer of squares with rounded corners. As long as user locations are tied to the grid, Tinder could use the normal Euclidean distance without risking privacy. Perhaps, just a new metric is calculated faster, and despite the testaments of Gordon Moore, computers are still limited. However, all this leads to the conclusion that Tinder is safe - in this very narrow aspect - and you screwed up.
The library is in complete darkness, not counting the green glow of the copier. You sadly, but carefully cover the tracks. You clean the storeroom and throw Wilson's phone into an industrial library shredder. You leave through the main entrance, steal a badly fastened bicycle and sadly roll home.
The next morning, Steve Stevington gives you one of a couple of co-directors, who he worked on in his secret daytime pottery classes. This is absolutely disgusting. It would be better if he gave you one of a pair of ten-dollar bills and stayed in the office. He worked a little and poorly, but you had to hold many meetings and lie a lot - usually this is his job. But at least he didn't steal your company. You pour Wilson's coffee into your ridiculous mug and wish health to your good friend.
When you fall asleep at night, thoughts come to mind what is happening with the Tinder grid at the North Pole ...
Your code from this article is published on Github . Please inform yourself if you have any questions or find any errors.
But under this glossy and dubious appearance lies rot. You suspect that your good friend, co-founder and co-chief executive Steve Stevington is plotting against you. He always runs out of the library at a strange time and disappears somewhere for hours on end. When you ask him where he is going, he builds a strange grimace, which he probably considers a malicious grin - and says not to worry. You instructed librarians to follow him several times, but they are all terrible in field work.
You have been living in Silicon Valley for a long time - and you know what merciless villains happen when a large amount of money and user data is at stake. Probably Steve Stevington is trying to convince investors to push you out of business. You think that Peter Thiel will support you, but it’s hard to say about Aunt Martha. So you need to figure out where Steve goes.
Fortunately, he is an avid Tinder user.
')
To determine the direction of the search, you looked at past leaks from Tinder users. There were several. In 2013, it was discovered that the Tinder servers send the exact coordinates of potential matches to the mobile application . Based on them, the application calculated the distance between users, but did not display coordinates in the interface. However, an attacker could easily intercept Tinder's own network traffic, check the raw data and determine the exact location of the target.

Tinder API response including exact location
Tinder tried to quietly fix the vulnerability by shifting the distance calculation to the servers instead of the application. After that, the network messages sent from the server to the application contained only these pre-calculated distances without actual locations. However, Tinder casually sent distances in the form of non-rounded numbers with 15 decimal places.

Tinder API response including exact distance
This negligence allowed the cunning researchers to again determine the exact location of the targets using an exploit for trilateration. The researchers sent three fake coordinates to Tinder with different locations of the user. At each new location, they asked Tinder how far the target was. Then three circles were drawn on the map with centers in fake coordinates and radii equal to the distances obtained. The point of intersection is the coordinates of the target with an accuracy of 30 meters.

Tinder Trilateralization Example
The Tinder security team looked at these people, who constantly force them to work, sighed and quietly fixed the vulnerability. Now Tinder sends distance, rounded to kilometers, to the application. You can still use this trilateration procedure to determine the coordinates of a target within a kilometer or so. But in the densely populated city of San Francisco, this will not give an answer, where does the sneaky Steve Stevington go.
On Friday afternoon, a gloating grimace reappeared on Steve Stevington's face, indicating that he was ready to perform various actions in unknown places. You have to figure out where he goes before it’s too late. You are locked in a private office - in the reading room of the library on the 4th floor. After fifteen minutes of deep breathing and even deeper thoughts, you had a plan to reanimate the Tinder exploitation and try to find out where the Stephenator is going.
Suppose Tinder now calculates the exact distances on the servers, rounds them to the nearest whole number, and then sends the rounded numbers to your phone. You can launch a new attack in the same way as with trilateration. Ship the fake Tinder locations and ask how far the target is. Tinder can answer "8 kilometers", which in itself is of little use. But then you can move one pixel northward asking for the distance with each step. The server will respond "8 kilometers, 8 kilometers, 8 kilometers, 8 kilometers, 7 kilometers." If your assumption about the rounding process is correct, then the point at which the answer changes is the exact distance to the target of 7.5 kilometers. If you repeat this procedure three times and draw three circles, then we will again use the trilateration exploit.
Go to action. While Wilson has gone to the toilet, you lend his phone for testing - you know that he is using Tinder, and the unlock code is visible by the finger on the screen. Speak to your unpaid probationary probationers so they won't call you on the phone and say nothing to Wilson — and hurry to a secluded and deserted corner of your office in the fiction department for older school age. There you open Tinder on both phones. You continue svaypit until you get a match, and then write a short script in Python using pynder to spoof Tinder API calls. You place Wilson in the middle of San Francisco Bay, and then you try to determine its coordinates by changing your location pixel by pixel to find the point when the distance between you changes from one rounded number to another.
But something is wrong. Evening came, supper time passed, and you have not yet found Wilson. You seem to be getting close, but not enough. Circles are sometimes painfully close to the intersection, but usually do not give a meaningful answer where Wilson is. You begin to despair. Right at this moment Steve Stevington can sign a new contract with Peter Thiel and Aunt Martha. Perhaps he has already updated your company’s LinkedIn page, renamed you “advisor”, “assistant” or “former CEO”. The library closes - and you move to the pantry. Wilson continues to call, but probationers on probation do not pass you. Even a fleeting thought of giving them a job jumps.

Frustrated, you take a step back and hit your head on the bottom shelf. Getting out of a heap of cleaning products, you are considering the possibility that the assumptions may be wrong. Tinder may not just round off exact distances. You take a snack from a library employee's refrigerator to help the thinking process. Stop drawing circles and start walking along the lines around the true location of Wilson, putting a mark on each change of distance.
At two o'clock in the morning everything becomes clear.

Placing Marks on a Map Based on Tinder Distances
Now Tinder so jealously protects the privacy of users, that it breaks the boring clips of ordinary geometry. He abandoned Euclid. He does not need the Haversinus formula . Instead, when calculating the distance between matches, Tinder uses two innovations.
First, and most importantly, it divides the city into squares of approximately 1 × 1 mile. When calculating the distance, the location of the target is tied to the center of the current grid square. Then, the approximate distance between you and this anchored location is calculated and returned.

Tinder binds user locations to the grid
Secondly, it calculates distances as if by its unique formula. For this, a map of coarse, predetermined distances is taken - and superimposed on the center of the square of the target. Tinder looks up the attacker's location in this overlay and returns the appropriate distance. In the normal calculation of the Euclidean distance, this would be a set of concentric circles.

But Tinder seems to use a concentric squares overlay with strange curves at the corners as it moves away from the target.

Among other things, this means that Tinder often returns slightly wrong distances. You suspect that rounding corners are necessary to adjust for too irregular distances, which are northeast of each other.
Mesh snapping is a key innovation in the Tinder approach. This means that Tinder will always return the same distance if the target is located anywhere within the specified grid square. Your trilateration exploit will not work. And if Tinder correctly implemented the grid binding, then no purely remote exploit will ever work. There is no way to find the location of a target with greater accuracy than the edges of one of the grid squares (approximately) 1 × 1 mile. Even such crude surveillance can make Tinder users think. But in fact, this is quite a reasonable behavior for the application, the main function of which is to tell strangers about where you are.
You really do not know why Tinder applies such a strange layer of squares with rounded corners. As long as user locations are tied to the grid, Tinder could use the normal Euclidean distance without risking privacy. Perhaps, just a new metric is calculated faster, and despite the testaments of Gordon Moore, computers are still limited. However, all this leads to the conclusion that Tinder is safe - in this very narrow aspect - and you screwed up.
The library is in complete darkness, not counting the green glow of the copier. You sadly, but carefully cover the tracks. You clean the storeroom and throw Wilson's phone into an industrial library shredder. You leave through the main entrance, steal a badly fastened bicycle and sadly roll home.
The next morning, Steve Stevington gives you one of a couple of co-directors, who he worked on in his secret daytime pottery classes. This is absolutely disgusting. It would be better if he gave you one of a pair of ten-dollar bills and stayed in the office. He worked a little and poorly, but you had to hold many meetings and lie a lot - usually this is his job. But at least he didn't steal your company. You pour Wilson's coffee into your ridiculous mug and wish health to your good friend.
When you fall asleep at night, thoughts come to mind what is happening with the Tinder grid at the North Pole ...
Your code from this article is published on Github . Please inform yourself if you have any questions or find any errors.
Source: https://habr.com/ru/post/417877/
All Articles