Solar Dozor leads the investigation: 5 non-standard cases that DLP disclosed
DLP systems are used to protect confidential company data and identify employees who are merging this data. In most cases, implementation engineers encounter typical incidents like these on projects. But sometimes the DLP-system unexpectedly reveals violations, the detection of which is not even sharpened.
Under the cut - a selection of the most unusual investigations conducted with the help of DLP.

From the case file: “Company X ordered a pilot implementation of Solar Dozor. The pilot zone included ten employees. Endpoint Agent was installed on their computers - a module for controlling user activity on a workstation. ”
')
For some reason, the traffic went only from nine computers, the tenth "was silent". We have rechecked everything several times, the result is one: the agent is installed, the status is active, the system is working normally, but the traffic is not going. Moreover, according to the ACS, a person comes and goes from work on time, which means that he is exactly in the office.
Someone joked: "Maybe he's just sleeping there?" They laughed, but decided to check. We were lucky: the CCTV was installed in the office. Here is what we saw: the employee comes to work on time, goes to his office, puts on his sunglasses and ... really sleeps. In the middle of the day, he wakes up on an alarm clock and goes to lunch, communicates with his colleagues, gives instructions, even takes papers for a while and works with contracts, and then comes back to himself andworks asleep until the end of the working day.
It turns out that the person at work does not use the computer, so the traffic does not go. Since X is a large organization, without a DLP system in a huge data stream, management did not notice the problem.

What is interesting, this employee is still working in company X. He himself is not going to leave, and he cannot be dismissed under the article: he comes to work on time, closes the tasks, since he sends them to his subordinates. And it is illegal to use records from cameras of the hidden video surveillance in court: they are established for fire safety, but not for control of employees.
When someone sends an electronic certificate or a sick leave to the personnel department, Solar Dozor alerts the security service. The document may be fake, it is better to check.
From the case file: “An employee of company Y provided a certificate of blood donation in electronic form. When checking, the security officer discovered that the certificate was dated tomorrow: the calendar was Thursday, and the blood was “donated” tomorrow.
Began investigating the incident. First of all, they checked the authenticity of the data about the clinic and the doctor. It turned out that neither such an organization nor such a specialist exists. It was clear: the certificate is fake. This was confirmed by the analysis of the donor’s traffic: the day before, he was searching the Internet for where to buy a certificate of blood donation, and placed an order on one of the sites. As the ACS showed, soon after that, he briefly left the office. Perhaps to meet with the courier?
In addition to data on violations, Solar Dozor keeps a history of employee communications. Interesting information was found in the archive: the “donor” ordered and printed out not only a certificate, but also two tickets for the train to the neighboring city, just for the day when “I donated blood”.
Also found a dialogue employee with his wife. They discussed how great it would be to walk away on Friday and go to relatives. Then they had the idea to forge a certificate, because the donor is legally allowed one day off.
This case was investigated thanks to the ability of Solar Dozor to analyze the service fields of the photos, which contain data about the device, the date of the survey, and geolocation.
From the case file: “At company Z, a pilot implementation of Solar Dozor was conducted. Suspicious activity on Avito was recorded from the workstation of one of the employees. ”
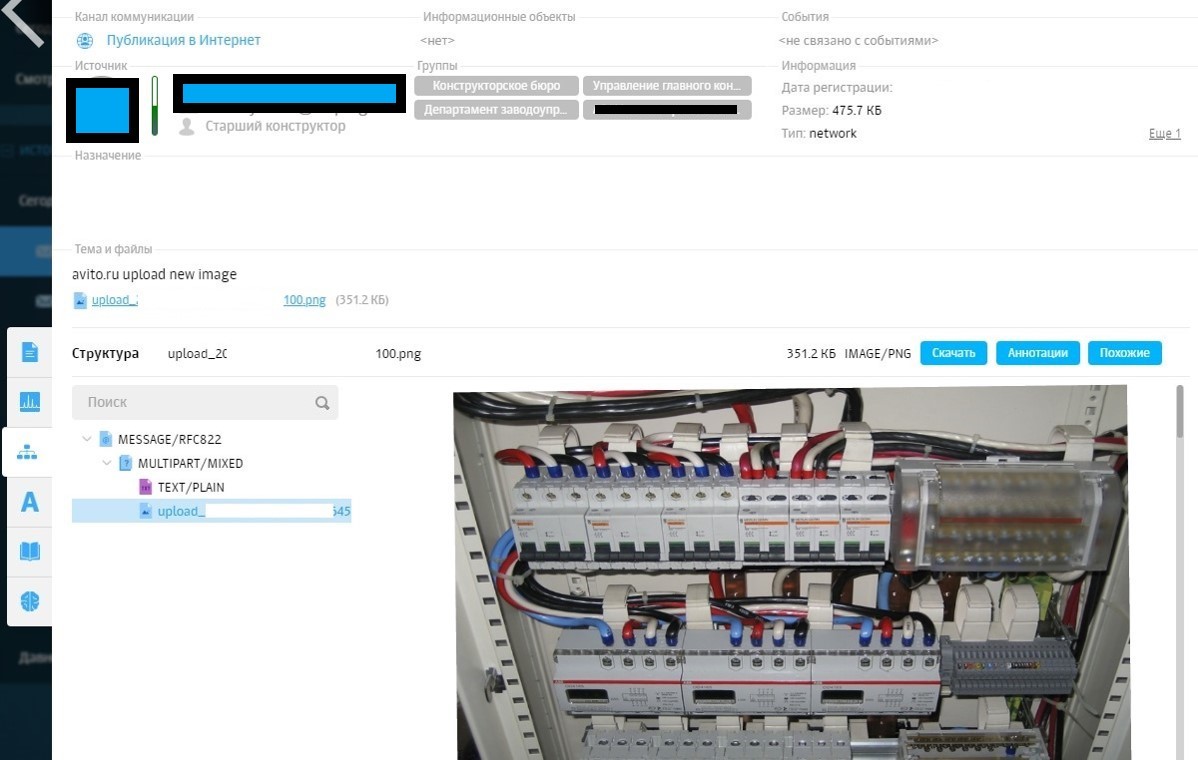
In itself, this is not a crime: a person could look for household appliances, clothing, children's things. Nevertheless, we decided to play it safe: we launched the Dozor File Crawler module and analyzed the contents of the employee’s workstation. Among other things, photographs of electrical boards were found.
Then the customer remembered that the company had cases of missing shields. Suspicions crept in, but more evidence was needed.
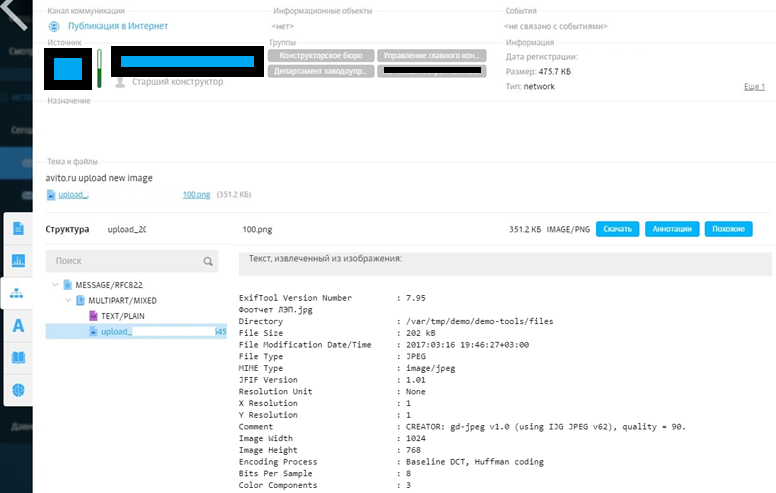
We found the same photos of shields on Avito, downloaded them and compared service fields. The serial number of the "suspect" phone completely coincided with the model and the serial number in the service fields of the photos. Other data was also identical. It means that the same photos are on the hard disk and on Avito. In the service fields, we looked at geolocation, scored the data in the navigator and found the same shields. As we thought, they were located at Z sites.
As it turned out, the employee laid out ads for the sale of shields, and when there was a buyer, he took out the equipment. So he managed to sell two shields and got caught on the third attempt.
From the materials of the case: “The system administrator of company B has already come across violations several times, therefore he fell into the special control group. Solar Dozor tracked all his actions. So his correspondence with the secretary got to the security service. ”

The girl is not the first time complains that the computer slows down. By correspondence it is clear: we are talking about antivirus. It is updated regularly or runs a scan, which is why the computer starts to freeze. The system administrator, even without trying to solve the problem, simply "blows down" the antivirus. It is evident that he is not doing this for the first time.
It would seem just negligence, but the consequences are very serious: the car is vulnerable, there is a gap in the perimeter of the company, about which the security man knows nothing.
From the case file: “A is a large organization that deals with the support and repair of power transmission lines, substations and other electrical equipment. There are inspectors in it who go to sites to assess their condition. If there is a problem, they take a picture of it with a service camera and request repair. After that, a contract is formed, a tender is held and money is allocated. ”
One application caused suspicions. The contracting officer was confident that this section had already been repaired several years ago. We decided to check it out and looked into the service field of the sent photo.
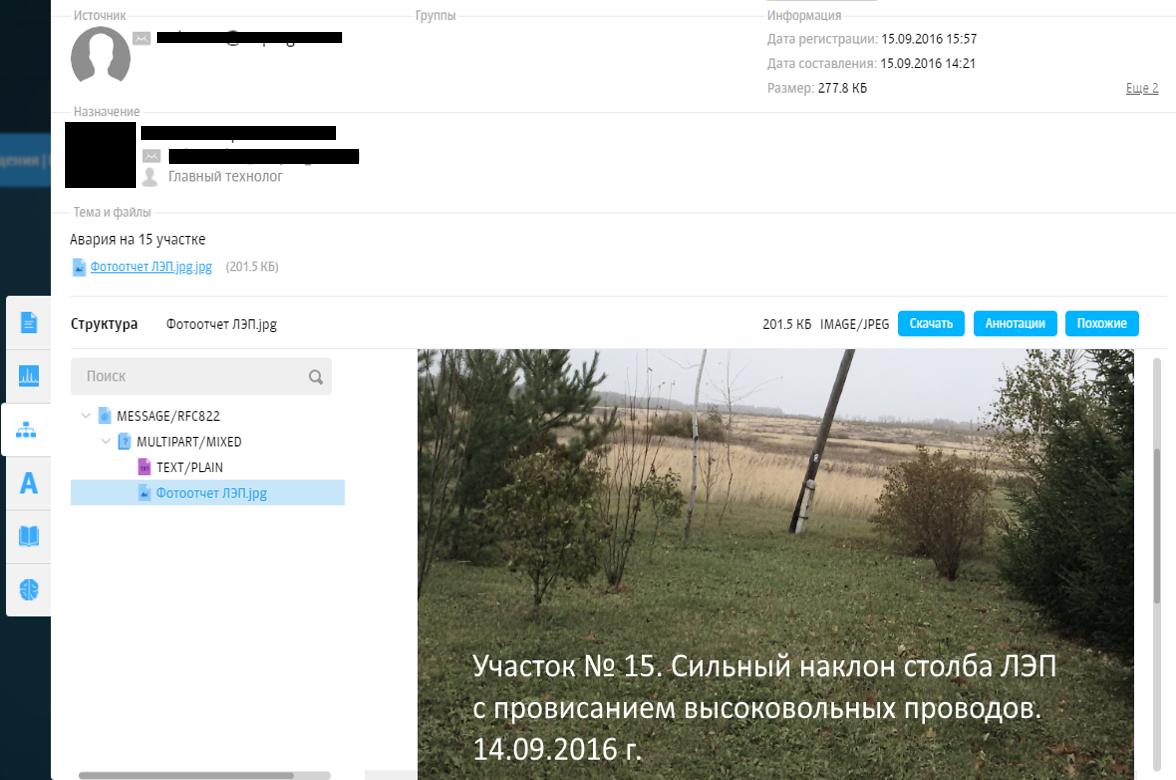
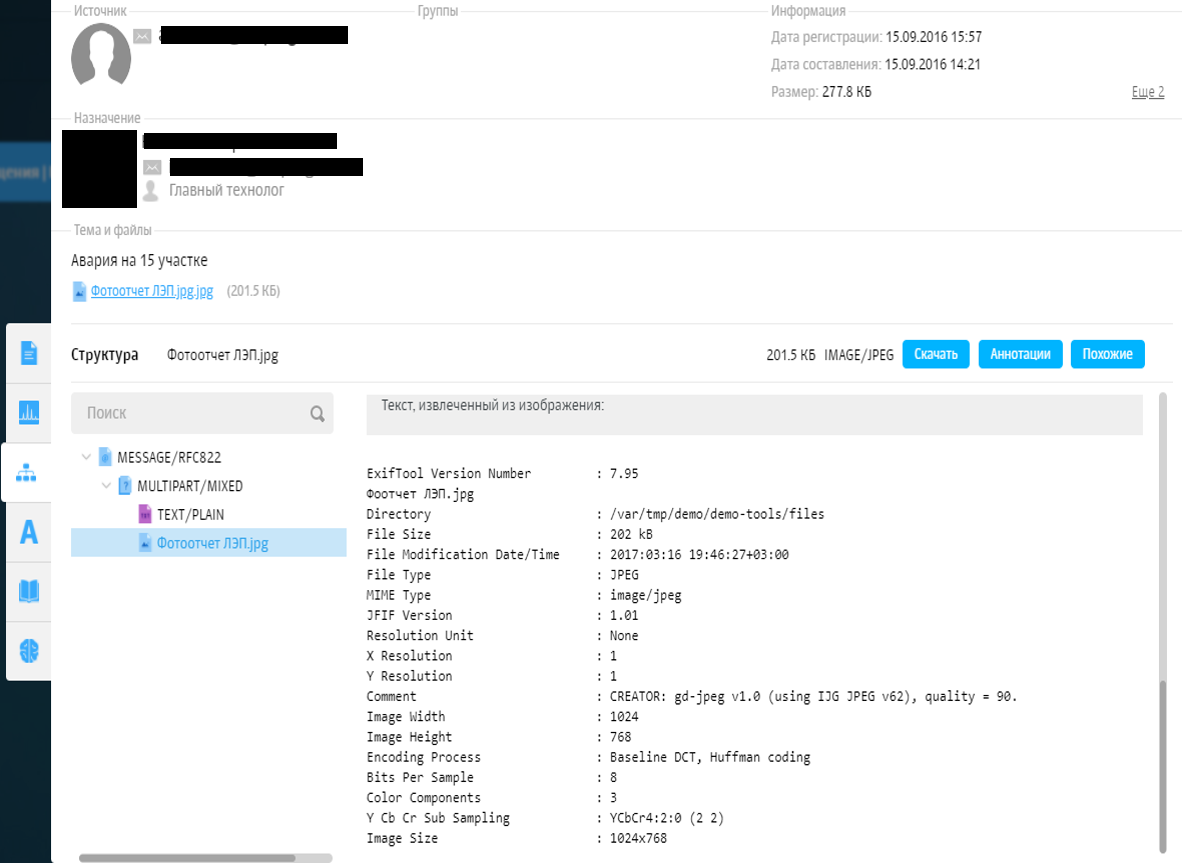
It turned out that the picture was taken a year ago, the coordinates of the point do not coincide with those indicated in the application, the serial number of the camera also does not correspond to the service one. Most likely, the photo was taken from the Internet and had no relation to real objects. At first glance, such a deception is not easy to see, because all the pillars in the field look the same.
The information was transferred to the customer’s own security service. During the investigation, it turned out that the same company won the tender over and over again, no repairs were made, and the money was simply shared.
In these cases, there was no cyber attack or confidential information. And yet, thanks to the attention to seemingly insignificant anomalies in the actions of users, it was possible to prevent theft, to detect forgery of documents, to detect unscrupulous employees. So do not ignore the minor oddities reported by the DLP - sometimes they mean no less than direct alerts about leaks.
Under the cut - a selection of the most unusual investigations conducted with the help of DLP.

Case number 1: "The soldier sleeps, the service goes"
From the case file: “Company X ordered a pilot implementation of Solar Dozor. The pilot zone included ten employees. Endpoint Agent was installed on their computers - a module for controlling user activity on a workstation. ”
')
For some reason, the traffic went only from nine computers, the tenth "was silent". We have rechecked everything several times, the result is one: the agent is installed, the status is active, the system is working normally, but the traffic is not going. Moreover, according to the ACS, a person comes and goes from work on time, which means that he is exactly in the office.
Someone joked: "Maybe he's just sleeping there?" They laughed, but decided to check. We were lucky: the CCTV was installed in the office. Here is what we saw: the employee comes to work on time, goes to his office, puts on his sunglasses and ... really sleeps. In the middle of the day, he wakes up on an alarm clock and goes to lunch, communicates with his colleagues, gives instructions, even takes papers for a while and works with contracts, and then comes back to himself and
It turns out that the person at work does not use the computer, so the traffic does not go. Since X is a large organization, without a DLP system in a huge data stream, management did not notice the problem.

What is interesting, this employee is still working in company X. He himself is not going to leave, and he cannot be dismissed under the article: he comes to work on time, closes the tasks, since he sends them to his subordinates. And it is illegal to use records from cameras of the hidden video surveillance in court: they are established for fire safety, but not for control of employees.
Case 2: "Honored Donor"
When someone sends an electronic certificate or a sick leave to the personnel department, Solar Dozor alerts the security service. The document may be fake, it is better to check.
From the case file: “An employee of company Y provided a certificate of blood donation in electronic form. When checking, the security officer discovered that the certificate was dated tomorrow: the calendar was Thursday, and the blood was “donated” tomorrow.
Began investigating the incident. First of all, they checked the authenticity of the data about the clinic and the doctor. It turned out that neither such an organization nor such a specialist exists. It was clear: the certificate is fake. This was confirmed by the analysis of the donor’s traffic: the day before, he was searching the Internet for where to buy a certificate of blood donation, and placed an order on one of the sites. As the ACS showed, soon after that, he briefly left the office. Perhaps to meet with the courier?
In addition to data on violations, Solar Dozor keeps a history of employee communications. Interesting information was found in the archive: the “donor” ordered and printed out not only a certificate, but also two tickets for the train to the neighboring city, just for the day when “I donated blood”.
Also found a dialogue employee with his wife. They discussed how great it would be to walk away on Friday and go to relatives. Then they had the idea to forge a certificate, because the donor is legally allowed one day off.
Case number 3: "Sale before theft"
This case was investigated thanks to the ability of Solar Dozor to analyze the service fields of the photos, which contain data about the device, the date of the survey, and geolocation.
From the case file: “At company Z, a pilot implementation of Solar Dozor was conducted. Suspicious activity on Avito was recorded from the workstation of one of the employees. ”
In itself, this is not a crime: a person could look for household appliances, clothing, children's things. Nevertheless, we decided to play it safe: we launched the Dozor File Crawler module and analyzed the contents of the employee’s workstation. Among other things, photographs of electrical boards were found.
Then the customer remembered that the company had cases of missing shields. Suspicions crept in, but more evidence was needed.
We found the same photos of shields on Avito, downloaded them and compared service fields. The serial number of the "suspect" phone completely coincided with the model and the serial number in the service fields of the photos. Other data was also identical. It means that the same photos are on the hard disk and on Avito. In the service fields, we looked at geolocation, scored the data in the navigator and found the same shields. As we thought, they were located at Z sites.
As it turned out, the employee laid out ads for the sale of shields, and when there was a buyer, he took out the equipment. So he managed to sell two shields and got caught on the third attempt.


Case 4: “Why do you need an antivirus? You are so beautiful
From the materials of the case: “The system administrator of company B has already come across violations several times, therefore he fell into the special control group. Solar Dozor tracked all his actions. So his correspondence with the secretary got to the security service. ”

The girl is not the first time complains that the computer slows down. By correspondence it is clear: we are talking about antivirus. It is updated regularly or runs a scan, which is why the computer starts to freeze. The system administrator, even without trying to solve the problem, simply "blows down" the antivirus. It is evident that he is not doing this for the first time.
It would seem just negligence, but the consequences are very serious: the car is vulnerable, there is a gap in the perimeter of the company, about which the security man knows nothing.
Case number 5: Falsification of repair documents
From the case file: “A is a large organization that deals with the support and repair of power transmission lines, substations and other electrical equipment. There are inspectors in it who go to sites to assess their condition. If there is a problem, they take a picture of it with a service camera and request repair. After that, a contract is formed, a tender is held and money is allocated. ”
One application caused suspicions. The contracting officer was confident that this section had already been repaired several years ago. We decided to check it out and looked into the service field of the sent photo.

It turned out that the picture was taken a year ago, the coordinates of the point do not coincide with those indicated in the application, the serial number of the camera also does not correspond to the service one. Most likely, the photo was taken from the Internet and had no relation to real objects. At first glance, such a deception is not easy to see, because all the pillars in the field look the same.

The information was transferred to the customer’s own security service. During the investigation, it turned out that the same company won the tender over and over again, no repairs were made, and the money was simply shared.
In these cases, there was no cyber attack or confidential information. And yet, thanks to the attention to seemingly insignificant anomalies in the actions of users, it was possible to prevent theft, to detect forgery of documents, to detect unscrupulous employees. So do not ignore the minor oddities reported by the DLP - sometimes they mean no less than direct alerts about leaks.
Source: https://habr.com/ru/post/417673/
All Articles