Vulnerability in the SS7 protocol for several years used to intercept SMS and bypass two-factor authentication
Attack scheme with SMS interception. Illustration: Positive Technologies
About critical vulnerabilities in the signal protocol SS7 known for several years. For example, in 2014, Russian Positive Technologies specialists Dmitry Kurbatov and Sergey Puzankov at one of the information security conferences vividly showed how such attacks occur. An attacker can listen to calls, set the location of the subscriber and forge it, conduct a DoS attack, transfer money from the account, intercept SMS. These attacks are described in more detail in the study SS7-Based Mobile Network Vulnerabilities and in the Statistics of Major Security Threats on Mobile SS7 Networks report.
And now the first evidence appeared that hackers from 2014 really use this technique to bypass two-factor authentication and transfer money from the accounts of banks' customers. The German newspaper Süddeutsche Zeitung has published its investigation.
The problem is that the SS7 signaling network was developed in 1975 (for routing messages when roaming) and protection mechanisms against such attacks were not originally incorporated into it. The implication was that this system was already closed and protected from outside connection. In practice, this is not so: you can connect to it. Theoretically, you can connect to it in any Congo or any other country - and then you will have access to switches of all operators in Russia, the USA, Europe and other countries. Including the interception of incoming SMS of any subscriber is carried out in the way described by the experts of Positive Technologies. At the same time, an attacker does not need sophisticated equipment: there is enough a Linux computer with an SS7 packet generator that can be found on the Internet.
')
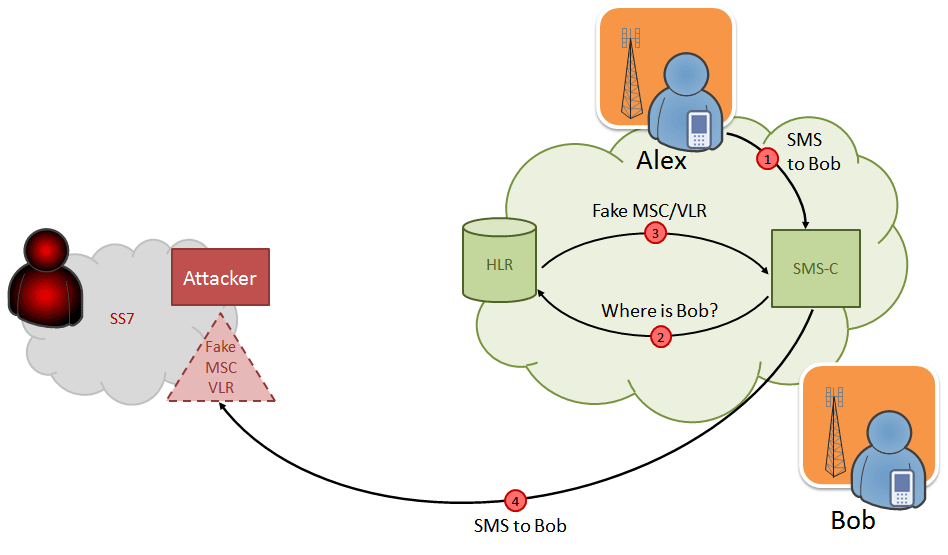
After the subscriber is registered at the “fake” MSC / VLR address, all SMS messages destined to the subscriber will be sent to the attacker's node.
The attacker can:
- send a reply about receiving the message (the sending party will have the impression that the SMS has been delivered to the recipient)
- do not send the receipt report and re-register the subscriber to the previous switch (in this case, in a few minutes the message will be sent to the recipient again);
- send a receipt report, re-register the subscriber to the old switchboard and send him a modified message.
This attack can be used for:
- interception of one-time mobile bank passwords;
- interception of recovered passwords from Internet services (mail, social networks, etc.);
- getting passwords for personal account on the site of mobile operator
We repeat, Kurbatov and Puzankov described all this in 2014 (!) Year, but only now the guys from Süddeutsche Zeitung found out that such attacks are in fact carried out, and two-time authentication via SMS no longer provides any security.
In fact, earlier only secret services could use this option, but now anyone who has a computer under Linux can use it. The Süddeutsche Zeitung newspaper writes that access to an SS7 switch can be bought here and there for 1000 euros. With the help of a bribe, you can still get the identifier of the global title (GT) of the mobile operator - this is also possible in some poor corrupt countries, where officials sometimes allow themselves to break the law for personal gain.
The attackers learned the bank details of the victims using phishing or malware, and then used the SS7 vulnerability to get a one-time transaction confirmation code (mTAN), which the bank sends via SMS.
The investigation of the German newspaper does not simply tell about the facts of the theft of money from bank accounts, but points to the fundamental vulnerability of SMS as an authentication factor: “I’m not surprised that hackers took money that they had under their hands. I’m just surprised that thieves in online banking took so long to join the espionage agents and also exploit the SS7 network vulnerabilities, ”said Karsten Nohl, another well-known mobile network and SS7 security specialist. At the same conference in 2014 in Russia, he read a report on attacks on mobile networks, and also repeatedly spoke on this topic at other conferences. In particular, he talked about SS7 vulnerabilities at the hacker conference of the Chaos Communication Congress in 2014 and even listened to calls by congressman Ted W. Lieu on his mobile phone (with his consent) for demonstration purposes. This congressman has now called on Congress to organize a hearing on critical vulnerabilities on the SS7 global signaling network.
It is very important that numerous online services, banks and other organizations immediately stop using SMS for authentication, because this channel has already been officially recognized as insecure (NIST recommendations) . For example, Google uses a more reliable mobile application Google Authenticator, but still sends codes via SMS to log in to the account, which completely undermines the security system, given the actively exploited vulnerabilities in SS7.
Source: https://habr.com/ru/post/403649/
All Articles