PKCS # 11 Cryptographic Cloud Service: From Myth to Reality
 In 2016, the article “Cloud token PKCS # 11 - myth or reality?” Was published. Half a year has passed and now a cloud (cloud service) has appeared on the Internet in which anyone can get a personal cloud token PKCS # 11 with the support of Russian cryptography.
In 2016, the article “Cloud token PKCS # 11 - myth or reality?” Was published. Half a year has passed and now a cloud (cloud service) has appeared on the Internet in which anyone can get a personal cloud token PKCS # 11 with the support of Russian cryptography.Foreword
Recall that PKCS # 11 (Cryptoki) is a standard developed by RSA Laboratories for interacting with cryptographic tokens, smart cards and other similar devices using a unified software interface that is implemented through libraries.
Cryptographic tokens provide both the storage of certificates and key pairs (public and private keys), and the execution of cryptographic operations in accordance with the PKCS # 11 standard.
 So, the LS11CLOUD cloud service appeared on the Internet, a cloud implementation of the PKCS # 11 v.2.40 standard, supplemented by the support of Russian cryptographic algorithms in accordance with the specifications developed by the Technical Committee on Standardization ( TC 26 ) "Cryptographic Information Security." The LS11CLOUD cloud service supports the algorithms of GOST R 34.10-2012, GOST R 34.11-2012, GOST R 34.12-2015 and GOST R 34.13-2015, as well as the associated algorithms and parameters defined by the guidance documents TC 26.
So, the LS11CLOUD cloud service appeared on the Internet, a cloud implementation of the PKCS # 11 v.2.40 standard, supplemented by the support of Russian cryptographic algorithms in accordance with the specifications developed by the Technical Committee on Standardization ( TC 26 ) "Cryptographic Information Security." The LS11CLOUD cloud service supports the algorithms of GOST R 34.10-2012, GOST R 34.11-2012, GOST R 34.12-2015 and GOST R 34.13-2015, as well as the associated algorithms and parameters defined by the guidance documents TC 26.')
The undoubted advantage of a cloud token is that now the user does not need to carry a token / smart card with him, to take care of his safety. Having a personal token in the cloud, a user can access it from his home computer, from a laptop, and from a mobile device.
Securing a secure remote interaction with a protected personal container of cryptographic objects (token) over an encrypted network channel is carried out using the authentication protocol SESPAKE (Security Evaluated Standardized Password-Authenticated Key Exchange) recommended by TC 26.
On the user side, the main functionality is provided by the ls11cloud dynamic library with the standard software interface pkcs # 11. To obtain a personal cloud token, the user must register on the LS11CLOUD cloud service, and then initialize and configure the personal token on the cloud service.
User registration on the cloud service
To begin with, we note that the cloud token LS11CLOUD is located at pkcs11.ru and receives requests for port 4444.
As already noted, the user is registered on the server and serviced his account using the ls11cloud_config utility:
bash-4.3$ ./ls11cloud_config LS11CLOUD User Utility usage: ./ls11cloud_config <command> [-p <password>] [-n <new password>] Commands: register <host> <port> <id> - register new user on the server duplicate <host> <port> <id> - duplicate user account on other computer change_pswd - change SESPAKE authentication password status - display current configuration data log - display server log file recreate - re-create token to initial empty state unregister - remove all user files from the server bash-4.3$ When registering a user, the location of the cloud service (the “host” field), the port (the “port” field) through which the user communicates with the outside world, and the nickname (the “id” field) of the user are indicated:
bash-4.3$ ls11cloud_config register pkcs11.ru 4444 habrahabr For registration from the MS Windows platform, there is a graphical shell with an intuitive LS11CLOUDGUI interface for this utility:

Get the distribution for the user here .
So, let's start testing the implementation of Russian cryptography in the PKCS # 11 cloud token. Testing will be conducted in MS Windows.
Installing LS11CLOUD_setup.exe includes the generation of the initial value of the random number generator:
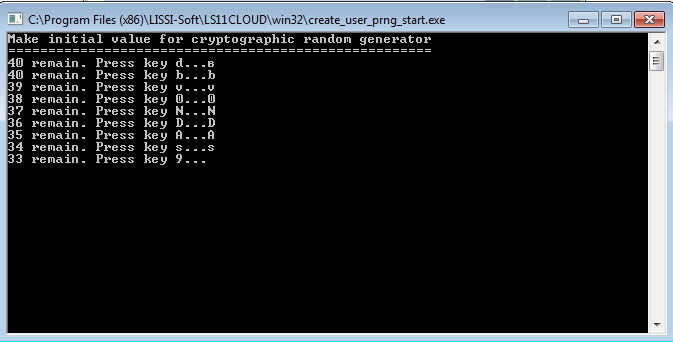
After downloading and installing the LS11CLOUD_setup.exe package, you need to run the ls11cloudgui graphical utility and click the "Registration" button:

The password is required to create a secure channel (SESPAKE protocol) from the user application to his personal token in the cloud. A password will be requested each time a user creates a session with a token:

In PKCS # 11 terminology, a session begins with the execution of the C_Initialize function and terminated by the execution of the C_Finalize function.
If you put a tick in the field “Save password”, it will be saved in the user’s configuration file on his computer and will not be requested when the session is established.
Upon successful user registration, a new token with a SO-PIN 87654321 will be created for it:

Token Initialization
After that, it is necessary to initialize the token (set a label, change the SO PIN, set a user PIN, etc.). To initialize the token, use the p11conf utility, which is included in the installation distribution:
bash-4.3$ p11conf usage: p11conf [-hitsmIupPred] -A APIpath [-c slotID -U userPin -S SOPin -n newPin -L label] -h display usage -i display PKCS11 info -t display token info -s display slot info -m display mechanism list -I initialize token -u initialize user PIN -p set the user PIN -P set the SO PIN -r remove all objects -e enumerate objects -d dump all object attributes bash-4.3$ For the MS Windows platform, there is a graphical shell with an intuitive P11CONFGUI interface for this utility:
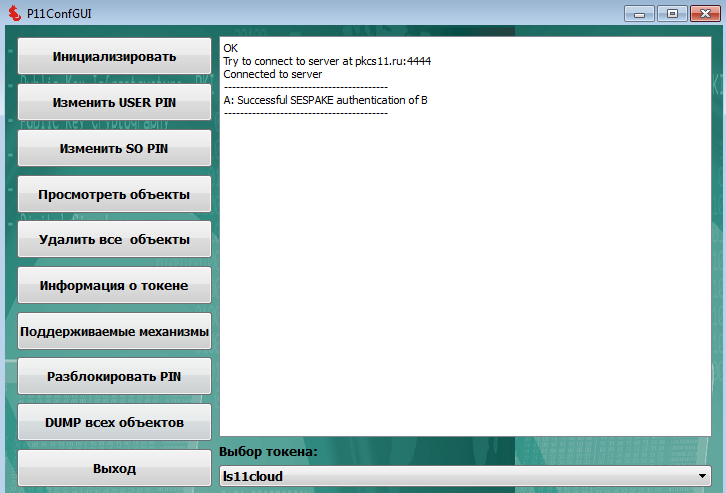
To initialize the personal cloud token, just run the utility P11CONGGUI.exe and click the "Initialize" button:

After pressing the “OK” button, the cloud token is ready for operation. If you want to use the created cloud token on another computer, then, of course, you also need to install on it the package LS11CLOUD_setup.exe. After that, you need to run the graphical utility ls11cloudgui and click the button "Duplicate token":

Installing the first personal certificate to the cloud token
Now that we have registered in the cloud and created our own personal cloud token in it, we can start using it. For testing, let's take the Redfox-52 browser and the Redfoxmail-52 email client, which are based on Mozilla Firefox and Mozilla Thunderbird, with support for Russian cryptography on tokens / smartcards PKCS # 11.
We will conduct testing on the WIN32 platform.
First you need to download and install Redfox-52. To install the Redfox browser, you need to download the archive firefox-52-gost and unpack it.
Unzipped Mozilla Firefox folder to move to a convenient place. Then create a shortcut to the executable file firefox.exe (located inside the Mozilla Firefox folder) and place it in any convenient place.
After launching the browser, you need to connect the created cloud token by adding the ls11cloud.dll library to the devices:
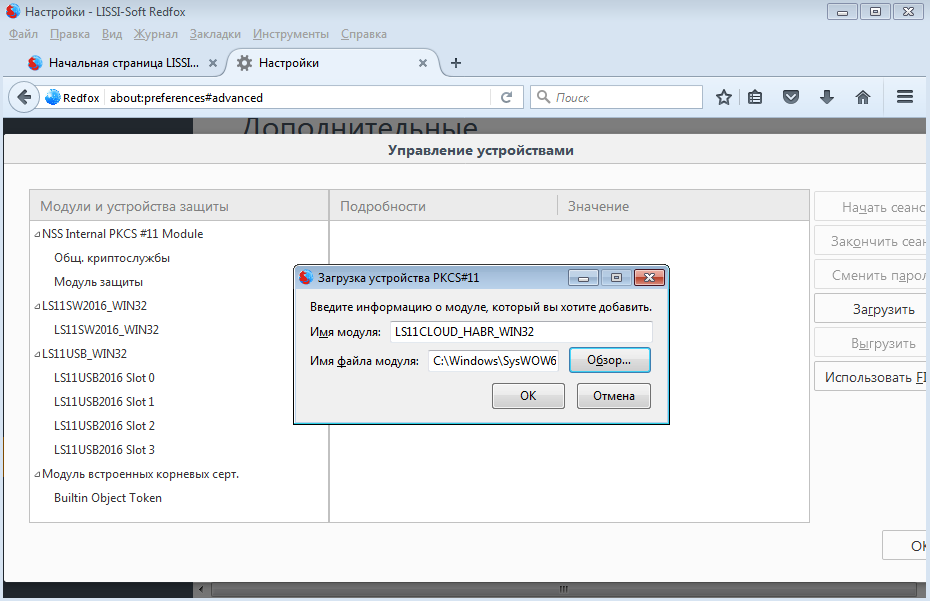
Please note that the distribution of the browser for MS Windows is built for the Win32 platform. Consequently, the ls11cloud.dll library should also be taken for the Win32 platform.
Once we have included the cloud token in the number of cryptographic devices with which the browser works, we can begin testing it. At the first stage it is necessary to obtain at least one personal certificate. To do this, use the services of one of the test CA :
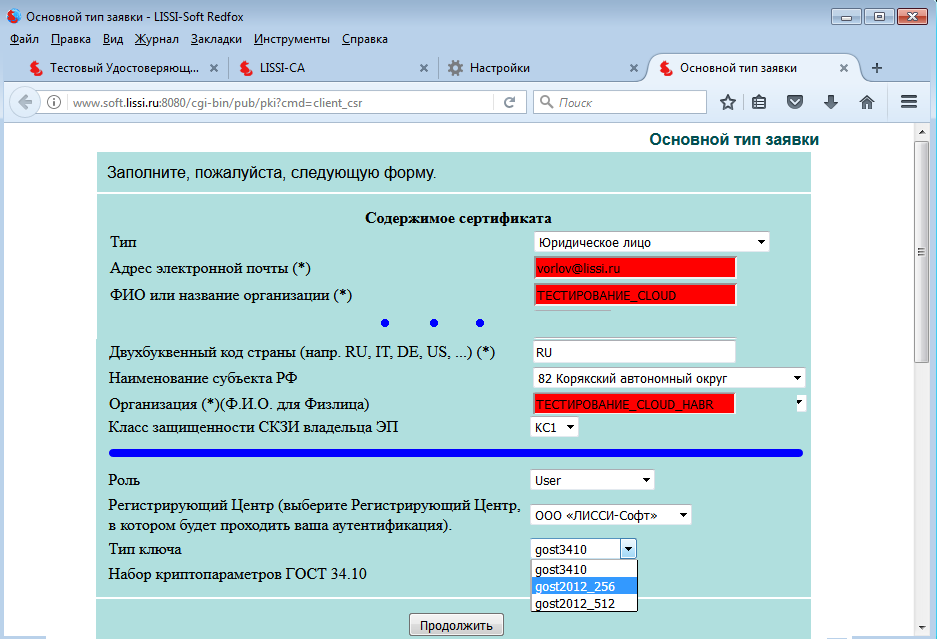
When you click the "Continue" button, the CA will offer to check the application data, and then select a cryptographic device (token / smart card) to generate a key pair and store a personal certificate:
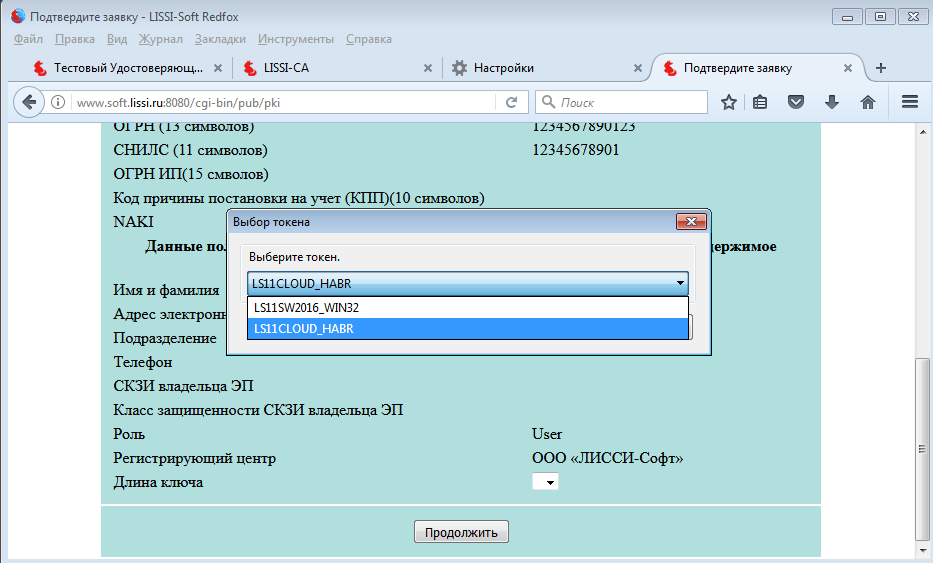
Naturally, a cloud token is selected and after clicking the “Continue” button you will be offered not only to get a personal certificate generated by your application, but also to install / save the CA root certificate:
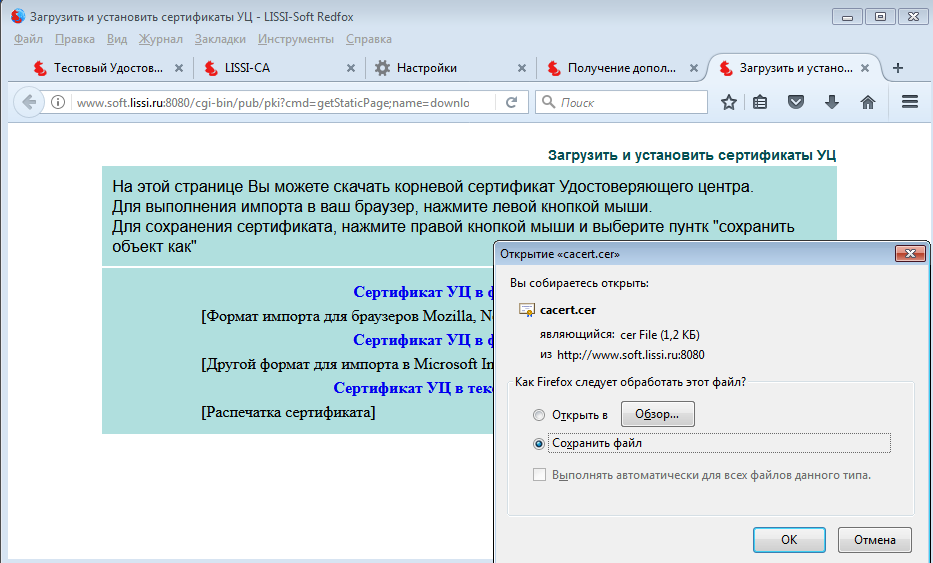
You can make sure that the certificate is installed by viewing the browser certificate stores:

Test HTTPS and PKCS # 12
So, cloud token mechanisms work. Now let's check the operation of the cloud token in the authorized https mode on Russian ciphers:
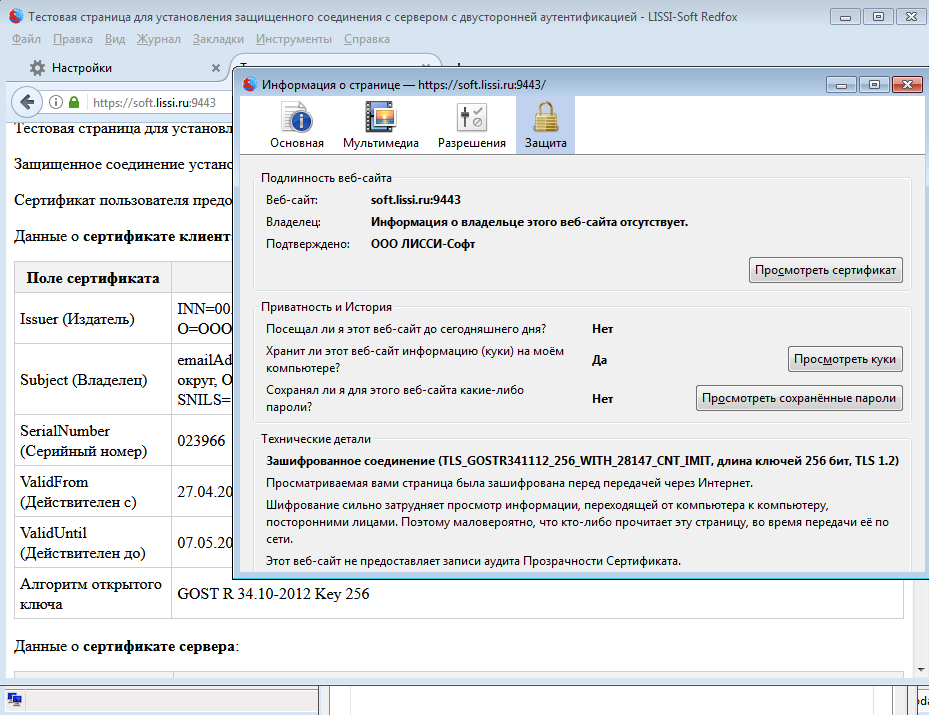
To verify the operation of the cloud token on the CryptoPro test pages, we will use the previously received test certificate of the CryptoPro center and the test certificate unloaded into the PKCS # 12 container. First you need to download the certificate in the PKCS # 12 format and install it on the cloud token (the password for the PKCS # 12 container is 01234567):
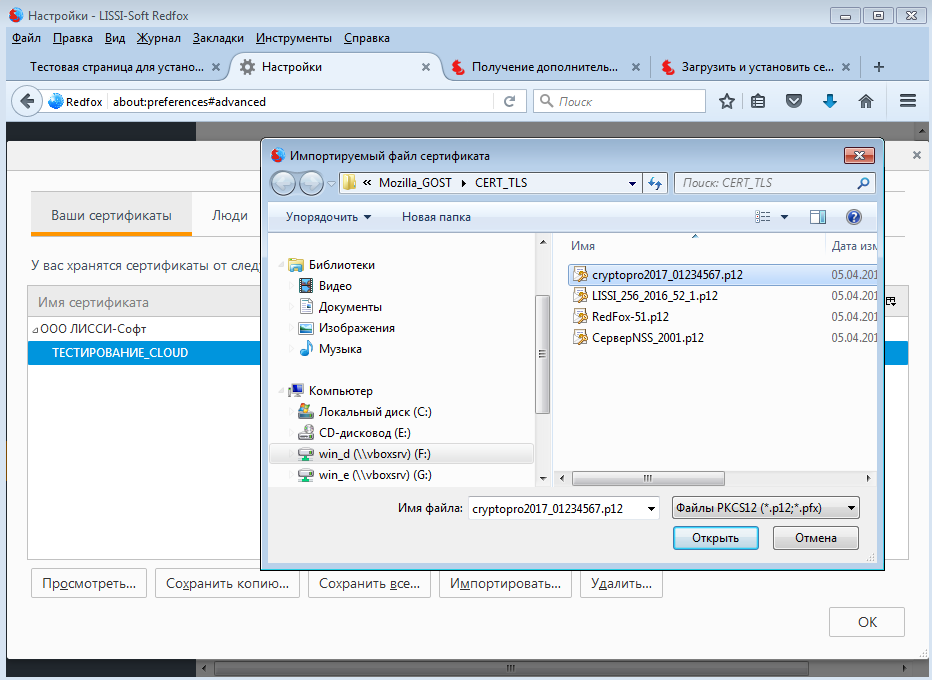
As a storage device, you must select a cloud token:
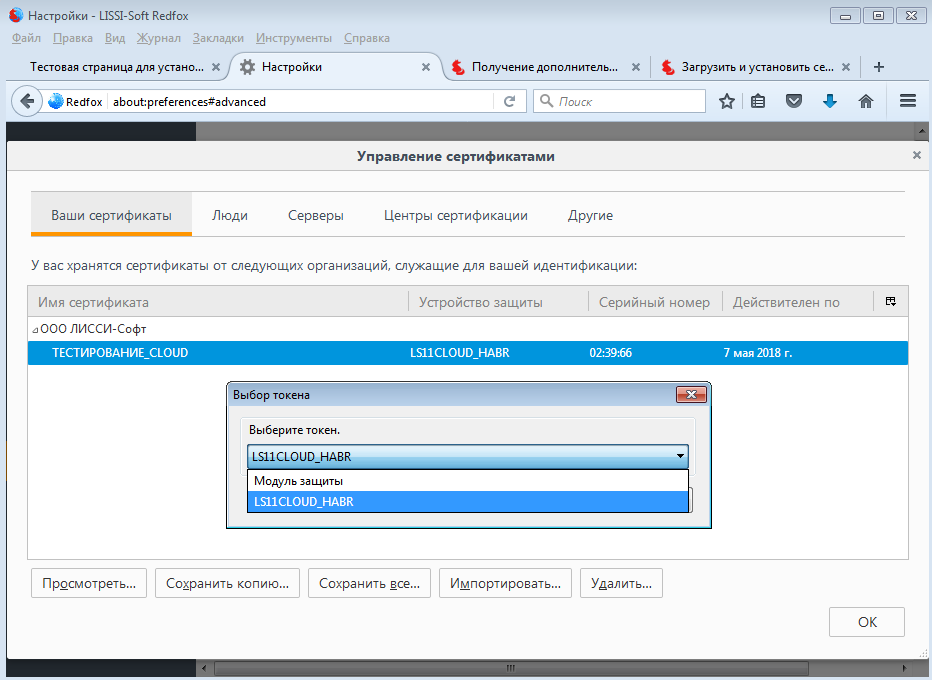
Then you will need to enter a PIN for access to the token, password for PKCS # 12. As a result, the certificate will be on the token:
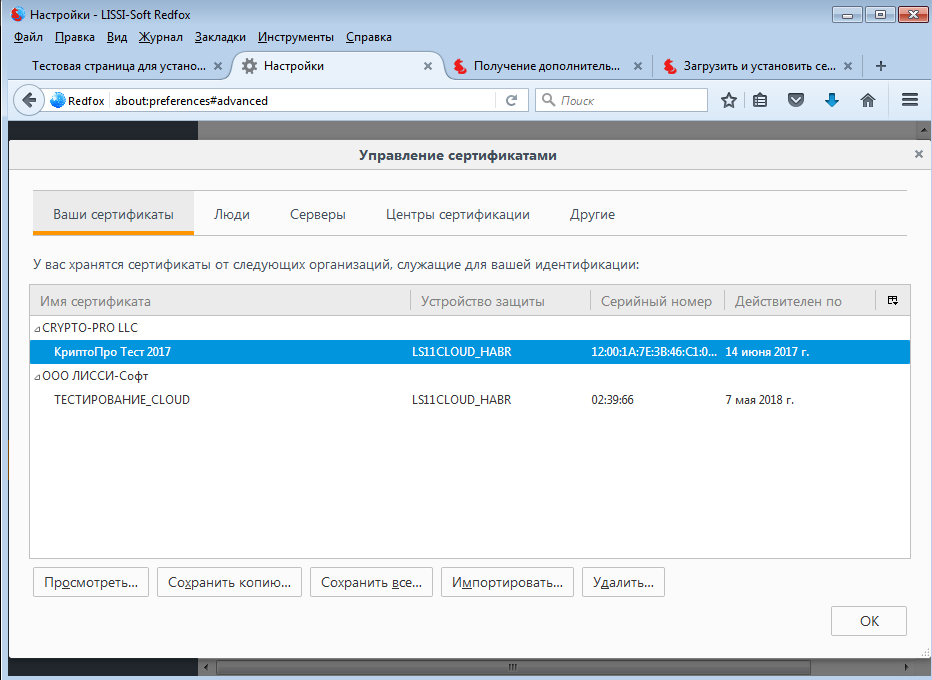
Do not forget to set the trust level of the CryptoPro CA root certificate:

Now you can safely go to the CryptoPro test pages, for example , here :

Using a cloud token to organize secure mail correspondence
Now let's see how the cloud token works in the Redfoxmail / Thunderbird mail client.
To install the Mozilla Thunderbird email client on the WIN32 platform, you need to download the thunderbird-52.0-gost archive and unpack it. Unzipped Mozilla Thunderbird folder to shift to a convenient place.
Then create a shortcut to the thunderbird.exe executable file (located inside the Mozilla Thunderbird folder) and place them in any convenient place. After starting the mail client, we connect a cloud token, in the same way as we did for the Redfox browser:
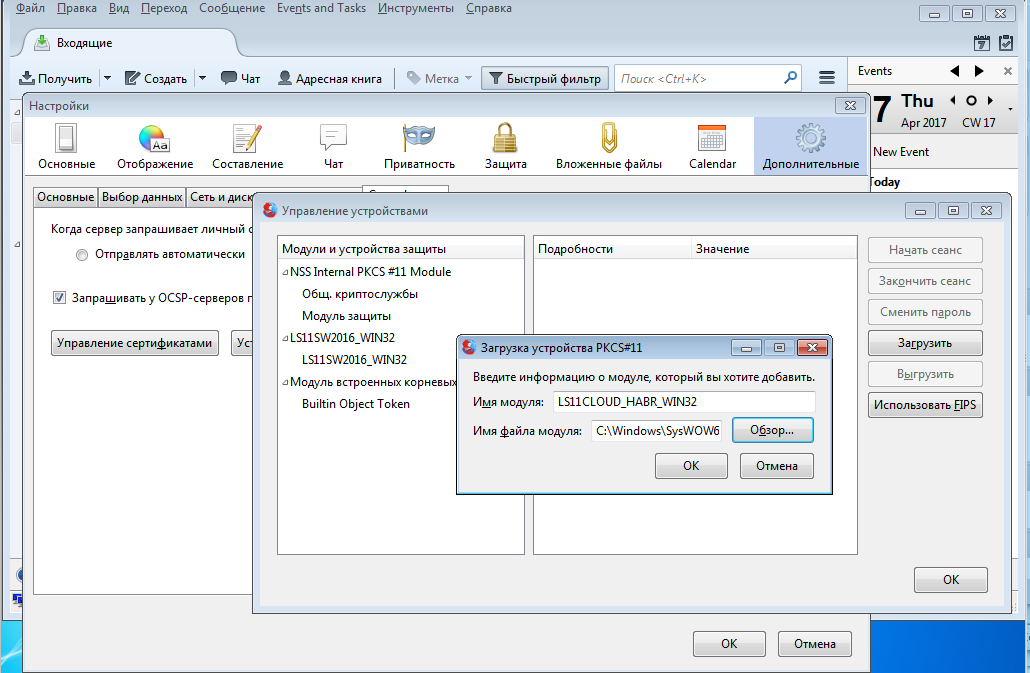
After connecting the cloud token, certificates stored on it will be available. But this may not be enough - you need to install the CA root certificates, on which personal certificates are issued. That's why we saved the root certificate when releasing:
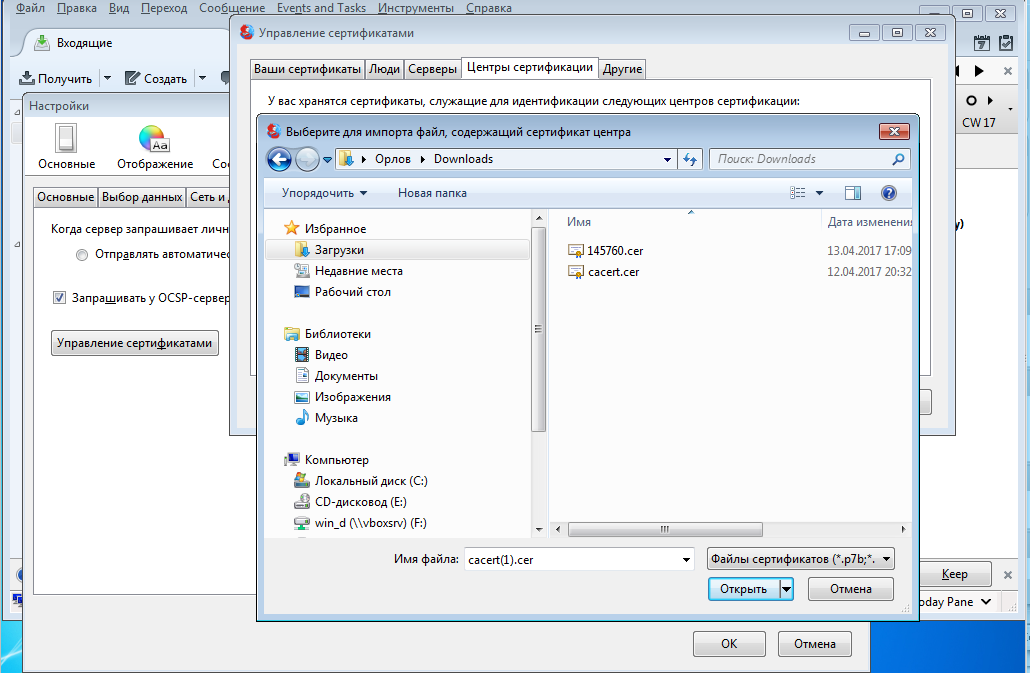
Now in the account settings you need to install a certificate that will be used to sign and encrypt emails:

Now you can safely sign your posts:
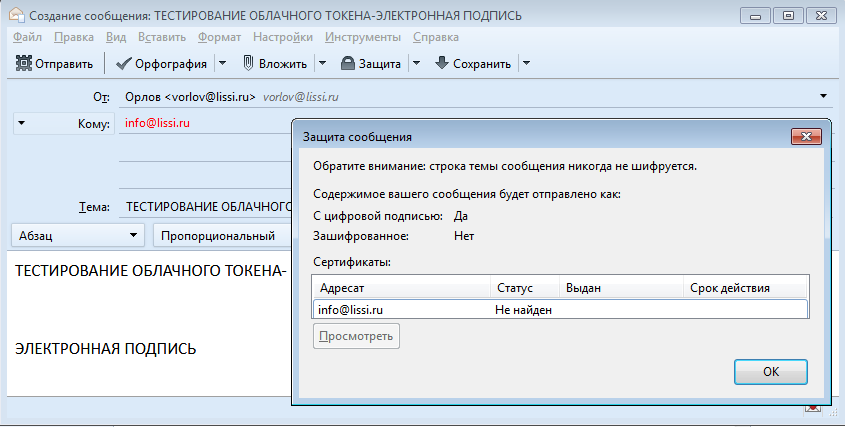
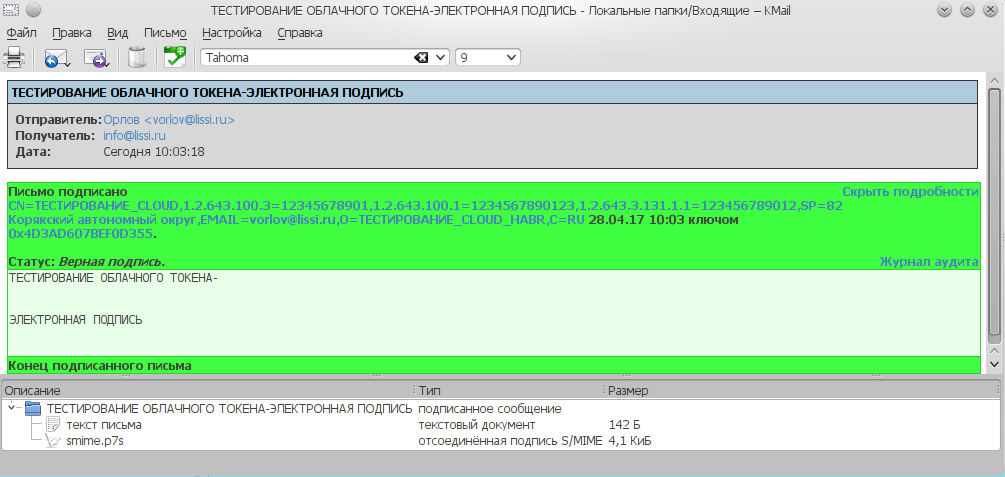
This message can be received by any email client with support for Russian cryptography , for example, KMail :
Conclusion
So, we can say that the myth becomes reality. The main scope of the cloud token LS11CLOUD can be internal corporate document flow, secure mail, banking.
The cloud service LS11CLOUD with its cloud tokens can be very useful for application developers using tokens / smartcards PKCS # 11.
 PS I put my personal certificate in a cloud token, connected it to a public services plug-in and paid the tax debt through the GOSISLUG portal . OC - Linux.
PS I put my personal certificate in a cloud token, connected it to a public services plug-in and paid the tax debt through the GOSISLUG portal . OC - Linux.Source: https://habr.com/ru/post/403563/
All Articles