Good Hajime worm protects Internet of Things devices
The malicious Mirai worm spreads over the network and adds new IoT devices to its botnet. But he has a strong adversary, the hajime security worm. First seen in October 2016 , this botnet has already taken over 10,000 network cameras, routers, set-top boxes and other devices connected to the Internet under protection.
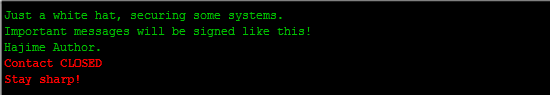
Every 10 minutes, Hajime displays a message in the terminal: “Just an ethical hacker, we are protecting some systems. Important messages will be signed in the same way as this! Author Hajime. Contact is CLOSED. Be carefull!"
')
Unlike other botnets, Hajime does not perform DDoS attacks, does not mine bitcoins, and does not do any malicious actions on an infected device, except for scanning the network in search of other vulnerable devices, which it also infects for protection. TCP / 23 (telnet) and TCP / 5358 ports (WSDAPI) are scanned. After infection, the worm blocks four ports that are used to spread Mirai and other similar malware: it is TCP / 23 (telnet), TCP / 7547 (TR-069), TCP / 5555 (TR-069) and TCP / 5358 (WSDAPI).
Hajime uses to infect the same list of 61 combinations of standard logins and passwords as Mirai (plus two additional combinations: root / 5up and Admin / 5up for routers and Atheros access points). In general, these are twin brothers, only one of them is on the dark side, and the other is on the light side.
Similar “good” malware has been encountered before. For example, in 2015, Symantec described Wifatch , a virus for Linux systems that acted in a similar way.
The initiative of the authors of such programs can be welcomed, but do not flatter yourself: their effect is only temporary. The malware is stored in the device’s memory, and after a reboot, it returns to the unprotected state again if the owner has not taken care of changing the password. With a standard password and open to the world Telnet device is still ready to install Mirai, writes Symantec.
A few days ago, Radware specialists published a Hajime technical analysis . They conclude that the author is a very qualified programmer who has spent a lot of time creating this program. This is not some simple hack. One simple example: unlike Mirai, when attempting to infect a device, this worm does not loop through logins and passwords stupidly through the list, but reads the text in the authorization form on the screen to determine the device manufacturer - and then uses standard passwords specifically for this manufacturer. So, when attacking a MikroTik router, it tries to log in with the username “admin” and an empty password. This is the default combination specified in the MikroTik documentation .
Next, Hajime is distributed via torrents. To transfer commands and update the program uses the uTP protocol BitTorrent - it also distinguishes it from Mirai and similar botnets. In addition, it reliably protects Hajime from blocking. The Hajime loader can download code from another node in the botnet - not from the one from which the infection was made. In addition, Hajime encrypts communications between its nodes, signing them with private and public keys. Communications are carried out on the UDP / 1457 port and another port with a random number greater than 1024 for TCP.
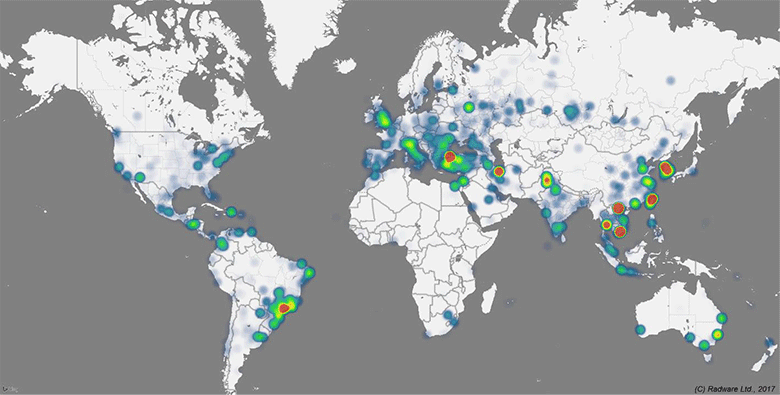
Hajime Infection Geography
Given all this, this is clearly a higher level program. I am glad that ethical hackers (white hat) surpass unethical (black hat) in their skills.
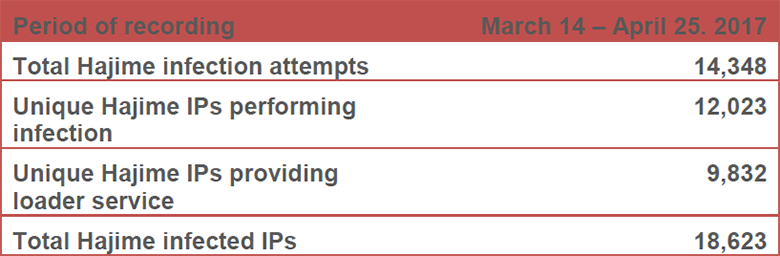
True, in October 2016, Rapidity Networks experts discovered a vulnerability in the implementation of the Hajime encryption protocol, but so far, the anonymous author of the program has closed this vulnerability. Now the worm continues to spread actively among the Internet of Things devices. Radware specialists set a honeypot to explore communications on the botnet. In the five weeks of the hanipot operation, 14,348 Hajime infection attempts were recorded with 12,023 unique IP addresses. This indicates a considerable scale of botnet distribution, although it is difficult to give a rough estimate of the size of the army of bots. But Hajime generated 50% of the activity of all the IoT botnets recorded on hanipot over the reporting period.
Among other interesting features of Hajime is the use of a backdoor in the backdoor of ARRIS cable modems; dynamic bootloader generation by hex strings based on manually written assembler programs optimized for each platform.
Security experts say that the "good" intentions of a hacker can change to unkind at any moment. It is enough to roll out one update for Hajime - it will quickly spread through the torrent network, and all tens or hundreds of thousands of bots can immediately start, for example, a DDoS attack. Judging by the quality of the software, Hajime can easily spread very widely and overtake Mirai in the number of bots. And it will not be surprising if it turns into a malicious tool in a year or two.
The hashes of Hajime binaries and files are added to the Github repository . From January 28 to March 5, the main binary has been updated six times.
Source: https://habr.com/ru/post/403469/
All Articles