BrickerBot malware turns IoT gadgets into "brick"
What is a "brick", which sometimes turn into gadgets, they know firsthand many geeks. We are talking about devices that work normally and suddenly just do not turn on and do not show signs of life. For example, unsuccessful firmware of the device, problems with the software of the gadget or malicious programs can lead to such a disastrous result. Information security specialists from Radware discovered the other day a malicious program that turns vulnerable smart devices into "bricks". Researchers say that attacking gadgets is malicious software started from March 20 this year.
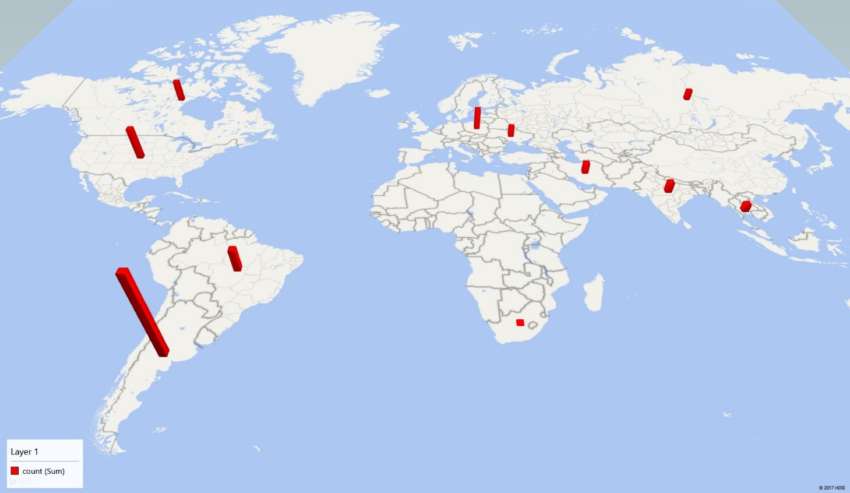
This is BrickerBot, a malicious program that exists in two incarnations at once. The first is BricketBot.1, the second, respectively, BricketBot2. Both software versions attack only those systems that run based on Linux BusyBox. In just four days last month, Radware employees recorded 2,250 PDoS attacks (Permanent Denial of Service, “Permanent Denial of Service”) against a specially designed snag that skillfully portrayed itself as an IoT device.
As it turned out, the attacks came from separate sites located around the world. BrickerBot.1 after a certain number of attacks was silent, but BrickerBot.2 was more active. He tried to attack the infidels about every two hours for several days. The malware attacks poorly protected IoT systems via Telnet and really turns them into “bricks”. BrickerBot selects those gadgets that can be accessed by default with a username / password. So far it is unclear exactly how the attack takes place and why the malware is trying to disable various gadgets in general.
')
In the first stage of the attack, BrickerBot acts in the same way as other IoT malware, including Mirai. There is a brute force on Telnet, with the selection of access to the management functions of the compromised device. According to experts who discovered BrickerBot, its code contains the most popular login / password combinations for admin of various device models.

If the attack succeeds and the malware gains access to the system, attempts will begin to deactivate the attacked gadget. To do this, the malware uses several different methods. The two versions of BrickerBot have different methods. But they have one goal - the transformation of the gadget into a "brick".
Among other methods of working with vulnerable gadgets, for example, rubbing up data on the drives of the device is used. In addition, the value is set to net.ipv4.tcp_timestamps = 0, after which the IoT gadget cannot connect to the Internet. The malware also tries to set the value of kernel.threads-max = 1 instead of the standard 10,000. This leads to the fact that ARM-based gadgets simply fail due to the stopping of kernel operations.
Experts indicate that the compromised gadget stops working a few seconds after infection. Interestingly, BrickerBot.1 attacks IoT devices from different IP addresses around the world, as already mentioned. But the second version of the botnet works through the elements of the Tor network, so it’s very difficult to track the work of this software, if at all possible.
Unusual difference of this malware from others is that it does not try to connect the attacked devices in the botnet. In fact, the corruption of IoT gadgets is the only visible goal of BrickerBot. Experts suggest that the creators of the bot may be dissatisfied with inattention to the problem of cybersecurity hackers who decided to teach the unwary owners a lesson.
Perhaps this malware will really attract more attention to this problem than the usual words about the need to be careful and change your account after purchasing a network device in the store. Nevertheless, this method of “learning the basics of info” can be simply dangerous. For example, such software can disable many CCTV cameras that serve some good purpose. As a result, the same surveillance cameras that keep order on the streets of cities may one day stop working.
“Try to imagine that the surveillance camera at the embassy was disconnected. How should this be considered - as an act of aggression against a certain state? Such attacks are very easy; I believe that this is only the beginning. I would not like to say that this is bad, but I think that there are less destructive ways to achieve the same goal. For example, you can start simply fixing device vulnerabilities. But this requires more professionalism, ”said Victor Gevers, head of GDI.foundation.
In addition, he asked the authors of the malware to contact him in order to try to plan any measures to correct the current situation and develop ways to remove unsafe IoT gadgets from the blow while at the same time correcting their problems.
Source: https://habr.com/ru/post/402995/
All Articles