90% of "smart" TVs can be hacked by malicious TV-broadcast and spy on TV viewers
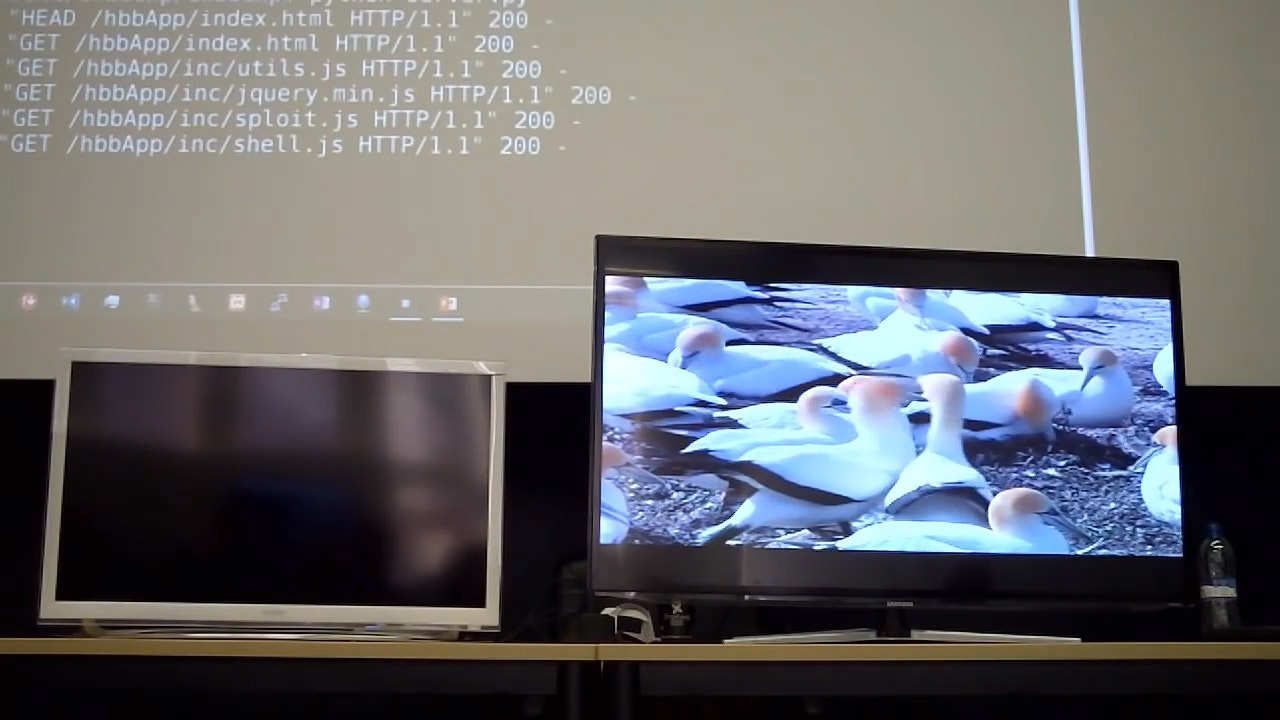
Download exploit for Array.prototype.sort () via the built-in TV browser, sent to the specified address by the DVB-T command. The attack takes place in the background while the victim watches a program about birds.
As you know, all “smart” TVs have a USB connector, where you can insert a USB flash drive and install malicious software on TV, which is exactly what CIA agents did (see the Weeping Angel exploit for Samsung TVs ). But there is an alternative way of hacking, when it is not necessary to get into the victim's apartment, and you can hack millions of TVs at the same time. True, this requires access to a television station, that is, the attack can be carried out at the state level in their own country. Alternatively, you can buy a DVB-T transmitter priced from $ 50 to $ 150 - and conduct an illegal broadcast, anyone can do it.
At a seminar on cybersecurity Media Cyber Security Seminar, a security specialist from the German company Oneconsult AG read a very interesting report about hacking smart TVs and even vividly showed the media industry how to remotely infect TVs using a standard DVB-T television signal (Digital Video Broadcasting). - Terrestrial), which they constantly broadcast on their frequencies.
The malicious TV program allows you to direct the built-in browser to an exploit that gets root rights on the TV, can set an arbitrary code there and use the TV in any way the attacker wishes: from spying to conducting DDoS attacks on remote targets when the TV becomes part of a botnet.
')
The central link for the attack is the technology Hybrid Broadcast Broadband TV ( HbbTV ) - the TV standard for the transfer of additional offers from the Internet to the TV. In fact, this is a special site adapted for TV that can be called up on the screen. This technology is supported by almost all modern "smart" TVs, it is compatible with the transmission of the TV signal via DVB-T, DVB-C and IPTV.
HbbTV supports javascript, css and dom. According to the standard, the TV must perform the commands received on HbbTV. Thus, information is transmitted in the background while the viewer is peacefully watching a TV show.
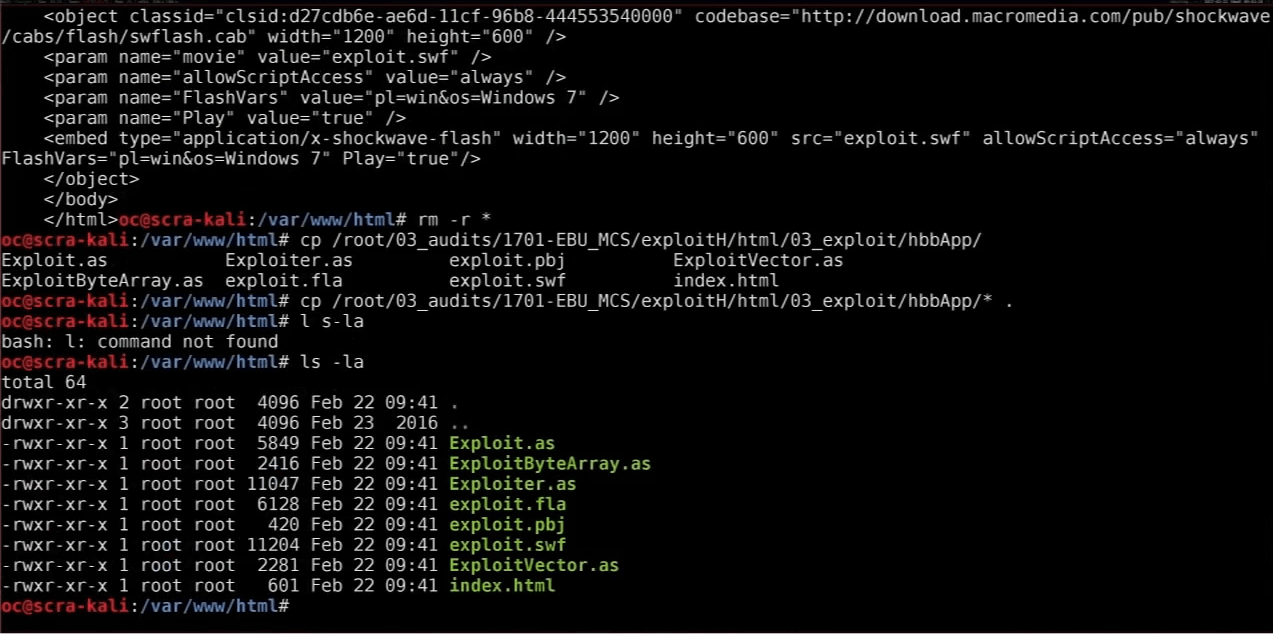
Rafael Scheel (Rafael Scheel) from the company Oneconsult AG has developed two exploits that, when loaded into the TV's built-in browser, execute malicious code, get root privileges and effectively take control of the device.
The first exploit exploits the CVE-2015-3090 vulnerability in Adobe Flash Player — one of those 0day vulnerabilities that became known after the hacking team was hacked in 2015.

Rafael demonstrated the work of the exploit by conducting a malicious broadcast on DVB-T, sending the TV browser to the specified address on the Internet, from where the code that uses the specified vulnerability is executed.
After that we get full access to the TV remotely.

As it turned out, almost none of the manufacturers of TV did not bother to close this vulnerability in their browsers for TV. True, few Adobe Flash TVs are enabled by default, so Raphael developed a second exploit that exploits an older vulnerability in the JavaScript function
Array.prototype.sort() .
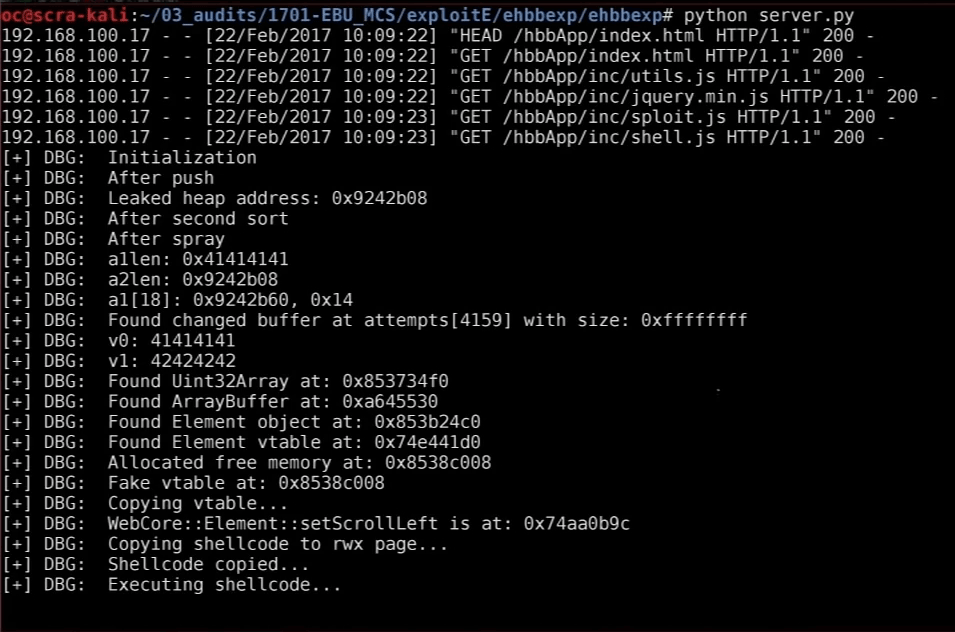
Now JavaScript is supported on all "smart" TVs, and the vulnerability, as usual, is not closed. The second exploit does everything the same as the first, but does not require the work of the Flash plugin.
According to Raphael, about 90% of the models of "smart" TVs that have been sold on the market in recent years are vulnerable to this attack. The researcher points out that DVB-T is a one-way communication channel, it is completely anonymous from the attacker. There are no traces left. In this case, there are several different ways how to send a DVB-T signal to the victim's TV. It is clear that a television company or special services can do this on a national scale, but if a private person is involved in this, then you have to be more inventive. Here are three options:
- attack on broadcasters;
- DVB-T dubbing with its more powerful signal (for example, broadcasting from a drone): the TV should switch to a stronger signal source by default;
- interference with DVB-C (IPTV), for example, via the Internet.
Maybe it makes sense XSS-attack on the site broadcaster.

Drone with DVB-T transmitter
Shil said that he developed an exploit for smart TVs even before he learned about the developments of the CIA.
Source: https://habr.com/ru/post/402733/
All Articles