The thermal camera can read newly collected passwords from the smartphone screen.

If you have installed a lock screen on your phone, you can hide the password from prying eyes by simply covering your gadget with your hand. But as soon as you unlock the phone, you will surely relax and leave the display in sight, especially if the device is turned off.
According to researchers from the University of Stuttgart and their colleagues from the University of Munich Ludwig-Maximilians , this is very unwise. At the upcoming conference on the interaction of man and computer, they will present their research. In their work, they explain how attackers armed with a thermal imaging camera easily read the access code from a smartphone.
')
However, the attacker must be very agile and agile - he has no more than 30 seconds to remove the trail. In a short video, the researchers presented a possible attack. The guy enters the code to unlock the phone, and then turns off the screen and puts it on the table. Then he gets up to pick up a cup of coffee, and the attacker quietly passes by, for a moment directs the portable thermal imaging camera towards the phone and is hastily removed.
What happens next is a bit like a slightly more high-tech version of the attack, when a foe takes a smartphone’s display camera and then examines the oil marks left by the owner. Thus, using a conventional photo editor, you can find out the password or read fingerprints. For the first time, this method was described by scientists from the University of Pennsylvania in 2010.
Most successfully managed to decipher the passwords of Android-devices on which the pattern was set to lock. The trace that remains after unlocking can even show the direction of movement of the finger, which makes its decoding elementary. It is more difficult to recognize a digital PIN code: you can find out which numbers it contains, but not the input sequence.
However, this will not save the attack from the thermal imaging camera: by entering a four-digit code, the user will leave four thermal tracks with different temperatures behind him: the first digit will be less pronounced, the last one - brighter. If the image has only three or two thermal footprints, the attacker will come to the conclusion that one of the numbers is encountered more than once. In this case, the password can not be recognized immediately, but with three attempts, you can guess.
The process of extracting the password from the thermal image also takes some time - one glance at the photo will not be enough. The researchers, together with colleagues from the University of Stuttgart and the University of Ludwig Maximilian in Munich, developed a six-point plan.
First, the thermal imaging camera must make an image of the display at a temperature of 15 ° to 32 ° degrees. Then, using the program, you must convert the color image to black and white and apply a filter to reduce noise. Further, the two-step operation completely removes the background and leaves only traces of heat. The main ones are isolated and extracted, resulting in one to four circles. At the final stage, each circle is analyzed to determine the most likely combination of numbers in the password.

Thermal attack is also successful when working with devices protected by a graphic key: you can trace the finger on the screen and find out the direction, depending on the relative temperature of the beginning of the movement and its end.
If you make an image within 15 seconds after the victim has entered the code, then success is achieved in 90% of cases. After 30 seconds, the accuracy drops to 80%, after 45 and more - no more than 35%.
If we talk about deciphering the pattern, the thermal attack helps to guess the correct form in 100% of cases, even 30 seconds after entering, provided that the key lines do not overlap. One such overlap "kills" accuracy up to 17%, and two overlaps - down to zero. Conversely, a PIN with repeated numbers can be decoded easier and faster.
It is relatively easy to defend against such attacks: just after unlocking the screen, talk on the phone, write a message or use some application, or simply hold your hand - additional spots can easily be confused by the ill-wisher with a thermal imaging camera. However, the authors of the study are confident that a more complex algorithm could distinguish the input of the unlock code from other actions with a smartphone.
They also offered several smartphone security tools against the threat. If you briefly increase the brightness of the screen to the maximum or cause a short surge in processor activity, then when the smartphone warms up, it will become more difficult to find the password.
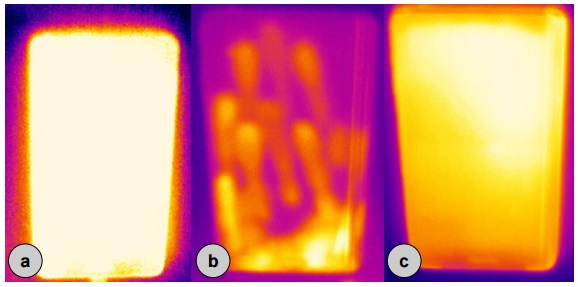
Hardware protection methods. A - increase the brightness of the screen for three seconds, B - random swipe across the screen, C - increase the load on the processor.
The researchers found that some people were predisposed to natural protection from the very beginning - cold hands do not allow attackers to quickly detect traces of heat from entering a password, because the difference in temperature between the display glass and fingers is less pronounced. On the other hand, warm hands prolong detractors time to attempt to remove the password.
If you enter a long password containing letters, numbers and symbols, then theoretically the attacker will have less time to capture traces of heat after the user finishes typing it. Presumably, this reduces the time of contact with the surface of the screen, which will affect the amount of heat transferred. In addition, after receiving the finished image, a long and complex password will be more difficult to calculate.
Source: https://habr.com/ru/post/402269/
All Articles