Meitu program accused of collecting personal information
 In recent days, the Web is rapidly spreading information about the Chinese mobile application Meitu - one of the many programs of the "beautiful" class (face enhancer) for selfie. The feature of Meitu is that among the filters there is anime, when the program enlarges the eyes, whitens the skin, tints the lips, eyelashes, etc. The program is very liked by many users who are happy to experience the anime filter . In the wake of the popularity of Meitu, security experts also drew attention to this application , since it collects an unusually large amount of information about users. If it is established by a significant part of the population, then such a large database of users may already have practical value for the one who collects it.
In recent days, the Web is rapidly spreading information about the Chinese mobile application Meitu - one of the many programs of the "beautiful" class (face enhancer) for selfie. The feature of Meitu is that among the filters there is anime, when the program enlarges the eyes, whitens the skin, tints the lips, eyelashes, etc. The program is very liked by many users who are happy to experience the anime filter . In the wake of the popularity of Meitu, security experts also drew attention to this application , since it collects an unusually large amount of information about users. If it is established by a significant part of the population, then such a large database of users may already have practical value for the one who collects it.So, what information does the program collect?
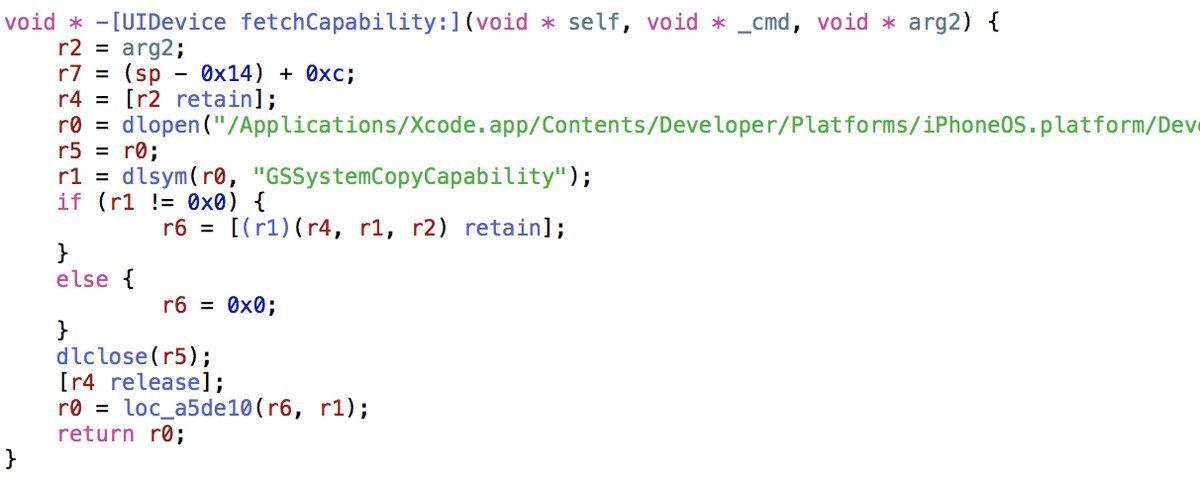
The IMEI ID is sent to the Chinese servers 110.173.196.36, 124.243.219.159 and 42.62.120.41 in the Android version. In the version for iOS with the latest updates, third-party applications do not have the ability to obtain the device's IMEI, IMSI, and MAC address, although the code of the iOS application has the corresponding code fragment that is prohibited from including programs in the App Store.
')
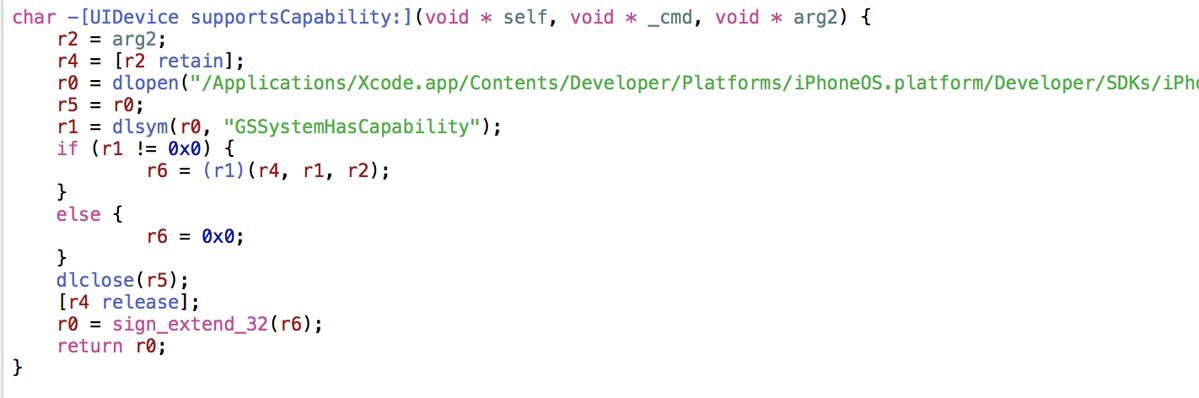
The iOS version contains at least three smartphone checks for jailbreak.

The function for collecting information about the provider of cellular communication is as follows.
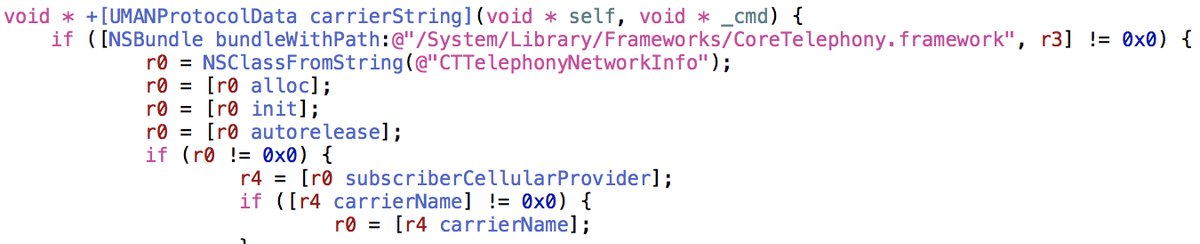
In addition, Meitu is a unique device profile , including taking into account the MAC address of the smartphone.
The application has code that allows dynamic loading of private frameworks while the program is running. However, while there is no evidence that this code is used. Apparently, this code was compiled as part of the iOS Facebook SDK.
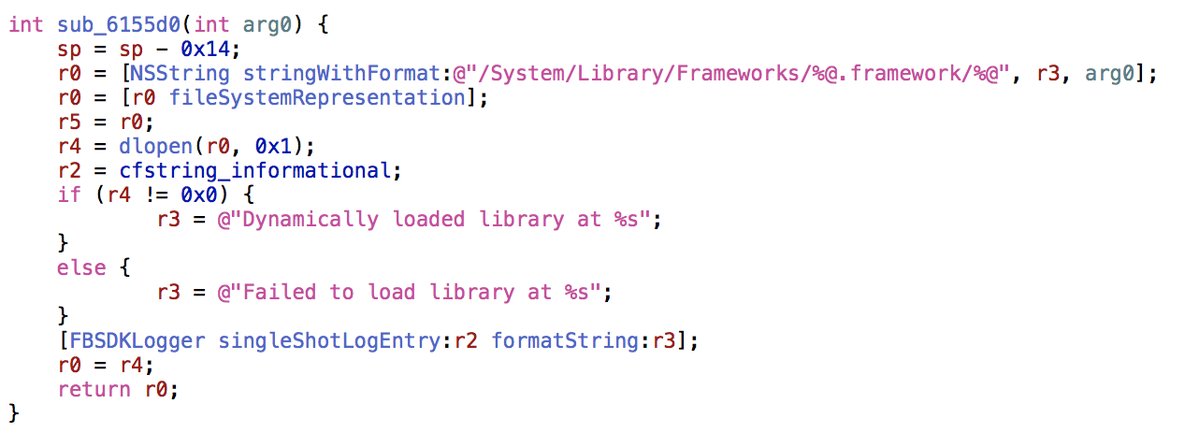
Analysis of the Meitu version for iOS shows that the application sends some of the information gathered to the servers of partners, mainly analytical companies. For example, the name of the mobile operator is sent to the server of the analytical company Umeng / Youmi (alogs.umeng.com). The iOS version number, smartphone model name, network type (for example, WiFi), device language, device localization information, mobile country code, and a randomly generated unique identifier are sent to the Meitu analytical server.
Perhaps the Chinese creators of this ridiculous program did not have any kind of backward thought about collecting a large array of private information about users. At least, now there is no evidence that the program is actually malicious. For example, it may be required to collect IMSI under Chinese law . But still, the Meitu example shows what kind of base a potential attacker can assemble. After all, this program is established by quite respectable citizens - your colleagues, your boss, who pays your salary, your friends and relatives. Information from their phones is collected and sent to a remote server.
After profiling the phone, Meitu continues to collect private data. Information about the geographical location of the user is drawn not only through the standard function of determining the coordinates of GPS, but also from the EXIF data of photographs that are stored on the smartphone.
Even during installation, the program asks for an extensive list of permissions, including access to the device and history, exact location, phone status, USB, photos and storage (write and read), camera, WiFi connection, device ID in call information, full access to the network, run at boot, prevent going to sleep, etc. For a complete list of permissions, see the screenshots below.
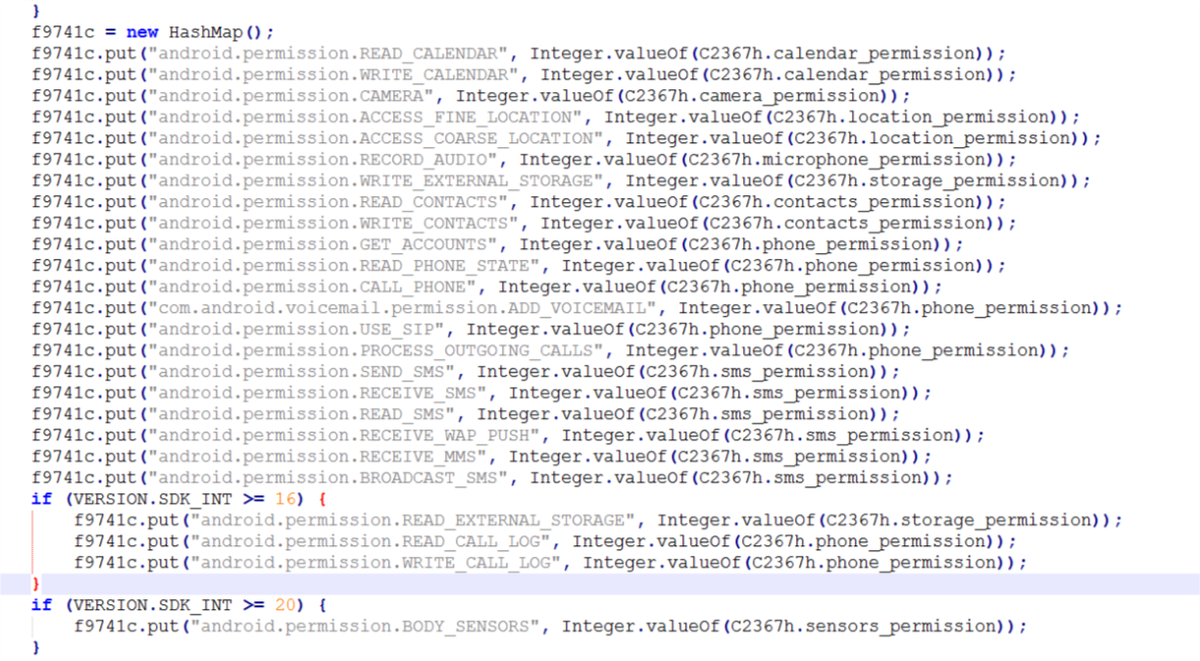
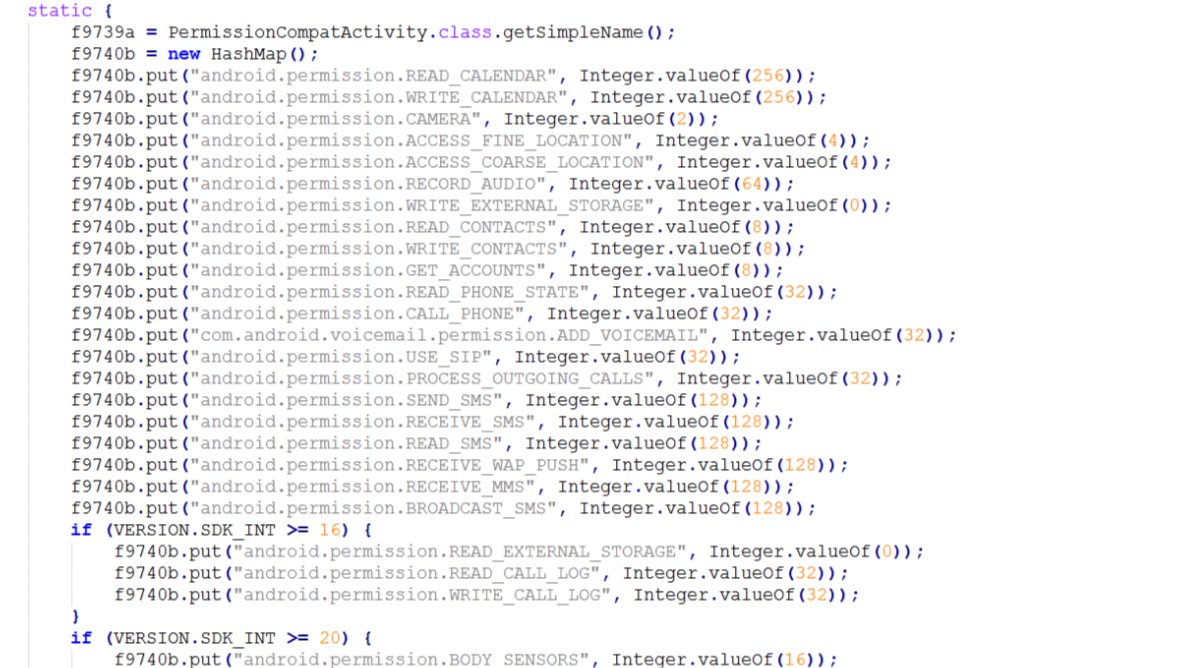
- App Key
- App Version
- OS Type
- IMEI
- MAC Address
- OS Version
- Device model
- Resolution
- Carrier
- Network type
- Language
- Country
- City
- Longitude
- SIM ICCID
- Local IP Address
- Root Status or Jail brake Status (in iOS)
In principle, the program collects on the phone literally all the information that it can collect. Perhaps this can be regarded as a fee for her free status, so many users agree, while others do not pay attention. In the end, this is the standard business model for the modern Internet: the company provides the service to the audience for free, and uses the audience itself as a product that is offered to the advertiser for money.
The program also includes a large number of third-party analytic modules and advertising trackers, including AppsFlyer, Crashlytics, Fabric, Umeng / Youmi.
“If you want to become a target for targeting and data mining, be sure to install Meitu. I’m sure whoever bought the data from them, he will thank you, ” comments security expert Jonathan Zdziarski.
Representatives of Meitu do not comment on the fact of collecting a large amount of private information, but emphasize that Meitu is the official Google Play partner and participates in the prestigious Sand Hill program from Google for applications that has viral potential. As part of this program, Google provides developers with advice and assistance on how to improve the work of the program in various markets around the world.
Some experts say that the Meitu program is generally not particularly different from many other popular iOS and Android applications, for example, from the same Pokemon Go program.
According to statistics today, Meitu applications have more than 1.1 billion installations, 456 million active users worldwide, 6 billion self-made and more than 490 million videos uploaded to the Meitu servers.
Source: https://habr.com/ru/post/400923/
All Articles