Brian Krebs revealed the identity of the author of the Mirai worm

The Mirai worm and botnet (Jap. "Future") in cameras, digital set-top boxes (DVRs) and other devices of the Internet of things made a lot of noise in September-October last year. The worm automatically went through standard login-password combinations and managed to spread to hundreds of thousands of devices (security cameras, routers, digital set-top boxes and DVRs), from which it organized several DDoS attacks. The power of these attacks far exceeded the capabilities of standard PC botnets, because ordinary computers are much more difficult to infect in such numbers.

Standard login and password pairs for some devices used by the Mirai worm
Birth and death Mirai
In September last year, one of the first victims of the Mirai botnet was journalist Brian Krebs, who specializes in information security topics and deanonymization of hackers. The traffic to its provider in peak reached 665 Gbit / s, which was one of the most powerful DDoS attacks in the history of the Internet (see “ 600 Gbit / s DDoS as democratization of censorship ”). Brian had to translate the site offline, because Akamai brought the site out of DDoS protection so as not to put other clients at risk. A few days later, Brian Krebs used the services of Project Shield , a Google charity project designed specifically to protect journalists from DDoS attacks. Obviously, after that, the identity of the hackers became the object of close study for Brian Krebs. For him it became a matter of principle.
')
These events pushed Brian Krebs to philosophical reflections on the essence of Internet censorship. He recalls the famous words of the entrepreneur and libertarian John Gilmore about the impossibility of censoring the Internet. Gilmore said: "The network recognizes censorship as damage and bypasses it." But this principle is valid only in the case of "political" censorship, which is traditionally exercised by governments of different countries, limiting the free access of its citizens to information. In the case of a DDoS attack, we see another example - an attempt to "shut up" the opponent. The state is not involved here. Censorship is realized by the coordinated efforts of many people or bots. In this sense, it can be said that the DDoS attack is a “democratic” version of censorship, in which the majority imposes its will on the minority and silences its opponent. Brian Krebs believes that at present the actions of experienced professionals represent the greatest threat to censorship. The underground hacking community has quietly turned into a powerful transnational organization in whose hands huge computer resources were concentrated. Under certain conditions, these resources can turn into cyber weapons.
"Cyber weapons" Mirai has not yet fired.
In September-October 2016, the botnet was used to attack the French hosting provider OVH and for a powerful DDoS attack on Dyn , which provides network infrastructure and DNS services for key American organizations. In this case, the stream of garbage requests from tens of millions of IP addresses was about 1 Tbit / s. Users around the world have had problems accessing Twitter, Amazon, Tumblr, Reddit, Spotify, and Netflix and others. In fact, the Mirai botnet temporarily “put” a small segment of the American Internet.
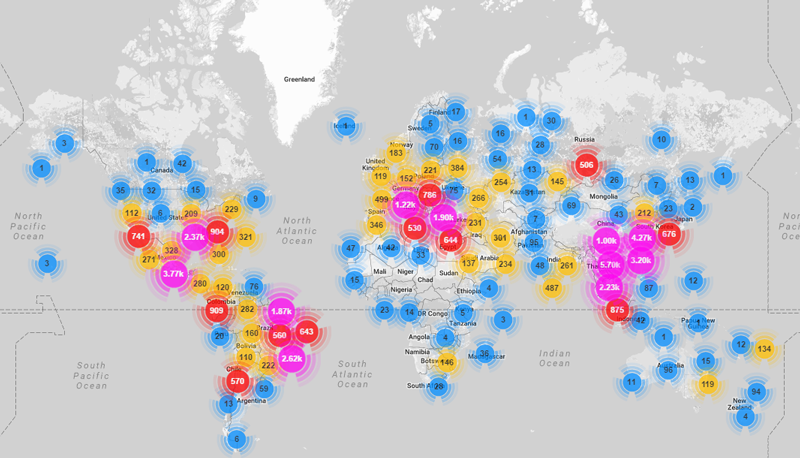
Map of the location of compromised devices that participated in the DDoS attack. Illustration: Incapsula
In November, a new version of Mirai attacked several models of Zyxel and Speedport routers , from users of the German Internet provider Deutsche Telekom. As the Kaspersky Lab's investigation showed, the modified version of the worm in this case used a new distribution method — through the specialized TR-064 protocol, which is used by providers to remotely control user devices. If the management interface (on port 7547) is accessible from the outside, you can either download and execute arbitrary code on the device or do the same, but through the stage of opening access to the traditional web interface.
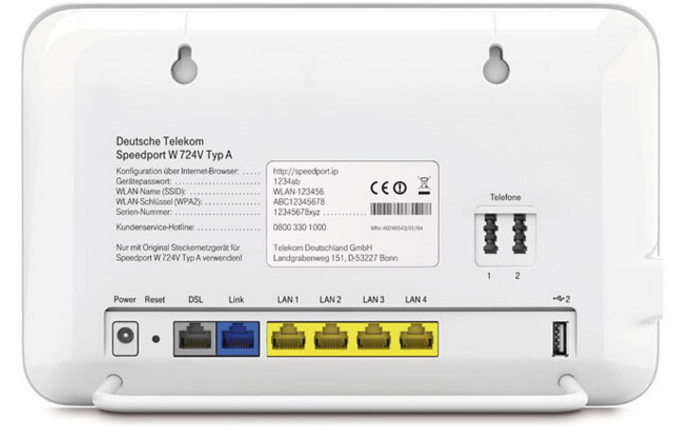
One of the vulnerable routers on the Deutsche Telekom network
The attack on Dyn may have already been carried out by other hackers, not those personal enemies of Brian Krebs. The fact is that in September-October a real war broke out between hackers for the control of the Mirai botnet after a vulnerability was discovered in the worm's code. So it is not entirely clear under whose control he was in November.
As reported in the media, after the discovery of vulnerabilities, hackers under BestBuy and Popopret nicknames took control of most of the Mirai botnet and added new devices to it. Thus, the new botnet swallowed the original Mirai and defended itself against new contenders for the capture of bots.
Vulnerability in the Mirai worm was found after the user of Hackforums forum Anna-senpai posted the source code of the components of the Mirai botnet at the end of September (see screenshot at the beginning of the article). This software continuously scans the entire range of IP addresses to search for devices with standard login and password combinations, the location of which sends a message to the command center, from where DDoS is coordinated. It is interesting that in one fragment of the source code there is a text in Russian .
cnc/admin.go: this.conn.Write([]byte("\033[34;1m\033[33;3m: \033[0m")) cnc/admin.go: this.conn.Write([]byte("\033[34;1m\033[33;3m: \033[0m")) cnc/admin.go: this.conn.Write(append([]byte("\r\033[37;1m … \033[31m"), spinBuf[i % len(spinBuf)])) Brian Krebs, twice injured by Mirai, decided to by all means deanonymize the authors of this worm . The investigation took several months, but in the end Brain managed to establish the real identity of Anna Senpai, as well as the identity of at least one of his accomplices.
Investigation of Brian Krebs
As a result of the investigation, Brian Krebs discovered that Mirai was not some kind of extraordinary worm, but just another incarnation of the worm that infected routers and Internet of Things devices with standard logins and passwords and standard vulnerabilities. In fact, there were many such worms and botnets. They belong to representatives of the profitable "stressor" industry - services that carry out DDoS-attacks for money. Among the botnets for the Internet of things that appeared before Mirai are the families Bashlite, Gafgyt, Qbot, Remaiten and Torlus. All these worms spread in a similar way, from one infected device to another.
Typically, the owners of botnets of this type did not “shine” in public, but in 2014 a group of Internet hooligans called lelddos publicly performed a major attack, as a result of which a number of websites went offline. The most common targets of lelddos attacks were Minecraft servers. Owners of such servers can earn up to $ 50 thousand per month, so this is an acceptable goal for a stressor. If the server is unavailable for several days, then many players will simply go to other servers, and the owner will lose good profits: there is a lot of competition here. In June 2014, an attack with the lelddos attack had to be dealt with by the company ProxyPipe, which specializes in protecting Minecraft servers from DDoS, using Verisign anti-DDoS- “roof”. In a quarterly report in 2014, Verisign called the 300 Gbps attack “the largest in its history.”
 In mid-2015, ProxyPipe customers came under attack from the Qbot botnet, which used Internet of things devices. Tellingly, just before the attack, customers were threatened by a certain 17-year-old Christopher Sculti (Christopher “CJ” Sculti, Jr., pictured), the owner and the only employee of the competitor company Datawagon, which also specializes in allegedly protecting against DDoS attacks. This method of "protection" is well known in the territory of the former USSR in the 1990s. Either we protect you, or you fall under DDoS.
In mid-2015, ProxyPipe customers came under attack from the Qbot botnet, which used Internet of things devices. Tellingly, just before the attack, customers were threatened by a certain 17-year-old Christopher Sculti (Christopher “CJ” Sculti, Jr., pictured), the owner and the only employee of the competitor company Datawagon, which also specializes in allegedly protecting against DDoS attacks. This method of "protection" is well known in the territory of the former USSR in the 1990s. Either we protect you, or you fall under DDoS.In turn, Datawagon worked under the auspices of ProTraf Solutions, also a DDoS protection provider.
Vice President of ProxyPipe Robert Coelho (Robert Coelho) told Brian Krebs that the young rival Christopher Sculti even threatened to disable his Skype account after finding a vulnerability in Skype and exiting the corresponding exploit. A few minutes after that, the Skype accounts of the Vice President and several employees actually disconnected. Then a powerful DDoS attack on the company's clients began.
ProTraf Solutions repeatedly launched attacks on ProxyPipe in order to lure Minecraft servers from under its protection to itself. The management of ProxyPipe warned customers that ProTraf Solutions was carrying out the attack, but despite this, some of the customers still turned to a competitor.
After this story, Brian Krebs recalled that Christopher Skulty contacted him, too, via Skype several times, discussing vulnerabilities in the Internet of things devices, and also expressed displeasure at the article in which Brian Krebs mentioned the name of a teenager. Brian did not attach importance to these conversations and simply blocked his Skype account.
Six months after that conversation, a 620 Gbps DDoS attack came to him.
It was likely to assume that Christopher Skulti is a member of the lelddos group that specialized in Minecraft server attacks. Another company FastReturn, which specializes in protecting Minecraft servers from DDoS attacks, participated in the attacks on ProxyPipe through a botnet from devices of the Internet of things. Coincidentally, the owner of this company, a young man from Dubai named Anmar Zuberi (Ammar Zuberi) soon went to work at ProTraf as a programmer and transferred his assets to the new employer (address space). Zuberi told Krebs that he is not a member of the lelddos group, but his colleague Christopher Skulty is, like the other two co-founders of ProTraf. Other sources have also confirmed the rumors that the 19-year-old co-founder of the company, Josiah White, is the main author of the Bashlite / Qbot worm. In the summary of this programmer it is written that he is a specialist in DDoS protection. This specialist has been known for many years in the hacker forums Hackforums under the nickname LiteSpeed. It is on those forums where trade in the services of stressors was active .
In an interview with Krebs, the guy confirmed that he did write some components of Bashlite / Qbot, but never used the worm for illegal purposes and did not offer its services for money.
However, Josiah White recalled one hacker under the nickname Vyp0r, who forced him to publish the source code online under the threat of publishing private information about him and svatting online (calling the special forces attire to the victim after an anonymous call).
In the end, Brian Krebs collected information about the president of ProTraf, a certain programmer named Paras Jha.
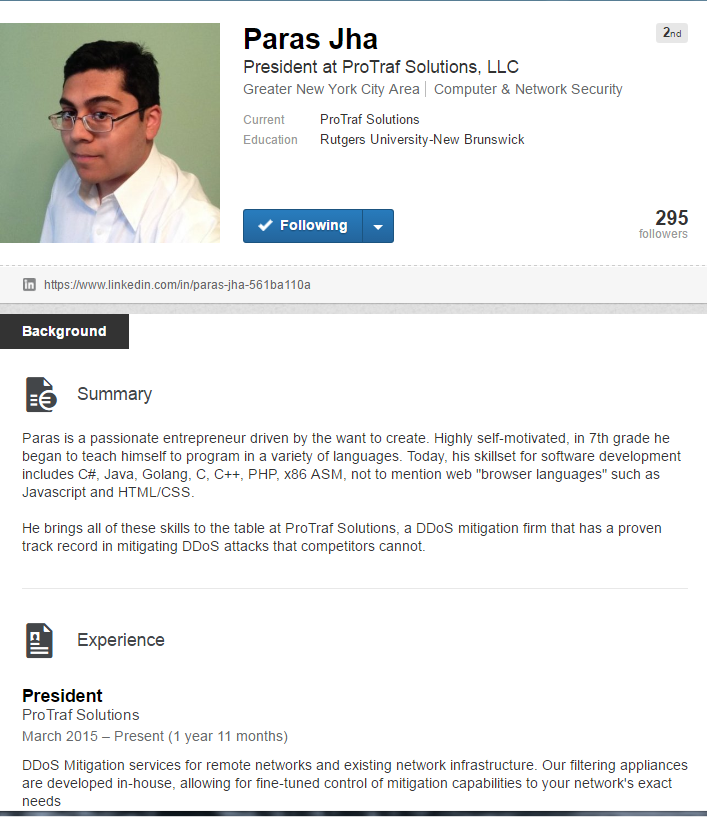
He is not only an experienced programmer, but also worked for several years at Minetime, which owned one of the popular Minecraft servers for its time.
During the study of the Paras Jah profile on Brian Krebs, the illumination came down: exactly the same profile with a combination of programmer qualities and programming languages corresponds to the Anna Senpai virtual! The high professionalism of Anna Senpai became clear even after the message on the July 10, 2016 forum about a “bot killer”, which infects the Internet of things devices and blocks the telnet port, preventing control from other worms. Then no one believed the hacker, but in the end, the bot killer really spread on the Web , burying Mirai and other clones.
The most obvious proof of Paras Jah’s and Anna Senpai’s identity is the great similarity of programming experience in Paras’s LinkedIn profile and in the forum application submitted by Anna Senpai (ASM, C, Go, Java, C # and PHP, the experience also coincides).

And the Mirai botnet was also written in the Go programming language.
Brian Krebs conducted a thorough investigation and collected additional evidence that indicates the identity of Paras Jah and Anna Senpai. In the online archive, he found a website on the parasjha.info domain, which Father Parasa Jah registered for his son. Little Paras wrote that he is interested in Minecraft games and dreams of working in this industry when he grows up. There, the student also mentioned his nickname dreadiscool .
Starting dokds on this nickname, Brian Krebs found a number of accounts and began to spin the online personality of Paras, in which he discussed everything: from technical programmers to DDoS attacks. In some of his posts, even then, the anime theme skipped, as seen in this edited photo, which dreadiscool set as an avatar on the maynkraftovskom forum spigotmc.org.

The theme from “Pulp Fiction” demonstrates how the criminal personality of Paras was born, and the anime girl shows the birth of the virtual Anna Senpai.
Not surprisingly, the user dreadiscool is registered on the anime website MyAnimeList.net. It lists the names of ten TV shows that he watched - among them is the TV series Mirai Nikki .
The puzzle has developed.
Brian Krebs publishes other evidence he has collected, including the name of the Ukrainian host BlazingFast.io, through which the Mirai botnet and other botnets were managed. Moreover, Anna Senpai entered into a correspondence with Robert Coelho after the latter managed to achieve the blocking of the Mirai management servers on the Ukrainian hosting. By the way, during the conversation he mentioned that he recently revised Mirai Nikki ( chat log , Robert Coelho under the nickname katie.onis ).
In the end, Brian Krebs received final proof: Anmar Zuberi reported that in November 2016, Jha admitted to committing an attack through the Mirai botnet. He made a confession under the pressure of Zuber. He made a complaint to the former partner why the Mirai code was published through the domain santasbigcandycane.cx, registered through the secret registrar Namecentral, about which only five people knew, including two of them. He smilingly admitted that he really is, and proudly showed text messages from an FBI agent who is investigating the Mirai case.
At liberty anime lover will not last long.
Source: https://habr.com/ru/post/400877/
All Articles