Not a bug, but a feature of Vkontakte
Vkontakte exists since 2006. At that time, as on all other sites, authorization occurred by entering mail and a password. But email and password can be stolen by intruders, there are a lot of ways, mostly phishing sites are used.

Entered the password on the left site, and in an hour “you” you will already be asking your VKontakte friends to throw 1000 rub to the modem.
When there were too many hacks, and it happened on February 11, 2011 , Vkontakte improved security in the social network: every time they try to log in from a new country under a user account, the login attempt is blocked by a message prompting you to enter the digits of the phone number to which it is registered page.

')
Of course, this did not prevent hacking, but it became more difficult for attackers, because before each entrance, it was necessary to watch from which country the victim and set up their own proxy or VPN to a specific country.
Time passed, and Vkontakte faced a huge number of bots and fakes. The solution to the problem turned out to be simple, getting a new number is more difficult than a new mail, so from November 21, 2012 all users of Vkontakte were forced to bind a mobile phone number.
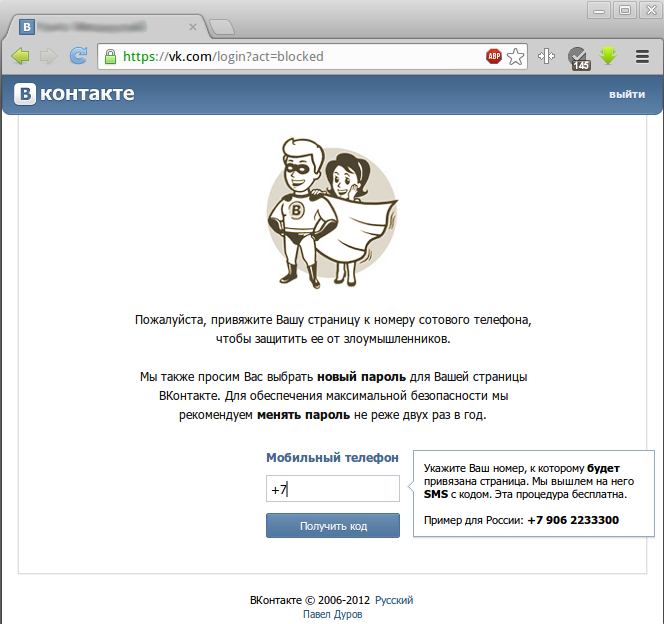
And since each user has a mobile phone attached, then let's open the entrance using a mobile phone? Vkontakte does everything for the convenience of users.

Don't you notice anything strange? If a user on a phishing site has entered his phone and password, and not mail and password, then checking the input of phone numbers becomes meaningless.
On sites where they sell accounts, the prices of "mail: password" and "number: password" vary greatly. This tells us that attackers prefer the “number: password” because they do not like to bother with a VPN and a proxy.

As you can see, checking the numbers of the phone is now ineffective.
In this regard, it is worth changing the verification of the user who logs in from ip of another country.
For example:
PS
Use two-factor authentication, it allows you to completely eliminate account hacking using phishing.
If suddenly you decide to enter your data on a phishing site, then enter the mail, not the phone number.

Entered the password on the left site, and in an hour “you” you will already be asking your VKontakte friends to throw 1000 rub to the modem.
Security enhancement
When there were too many hacks, and it happened on February 11, 2011 , Vkontakte improved security in the social network: every time they try to log in from a new country under a user account, the login attempt is blocked by a message prompting you to enter the digits of the phone number to which it is registered page.

')
Of course, this did not prevent hacking, but it became more difficult for attackers, because before each entrance, it was necessary to watch from which country the victim and set up their own proxy or VPN to a specific country.
Authorization: "email and password" or "number and password"
Time passed, and Vkontakte faced a huge number of bots and fakes. The solution to the problem turned out to be simple, getting a new number is more difficult than a new mail, so from November 21, 2012 all users of Vkontakte were forced to bind a mobile phone number.

And since each user has a mobile phone attached, then let's open the entrance using a mobile phone? Vkontakte does everything for the convenience of users.

Problem
Don't you notice anything strange? If a user on a phishing site has entered his phone and password, and not mail and password, then checking the input of phone numbers becomes meaningless.
Current state of affairs
On sites where they sell accounts, the prices of "mail: password" and "number: password" vary greatly. This tells us that attackers prefer the “number: password” because they do not like to bother with a VPN and a proxy.

Solution to the problem
As you can see, checking the numbers of the phone is now ineffective.
In this regard, it is worth changing the verification of the user who logs in from ip of another country.
For example:
- If with ip of another country enter the mail and password, then ask the phone numbers.
If you enter a phone number and password, then ask for part of the mail. - Ask for a first or last name, not phone numbers
PS
Use two-factor authentication, it allows you to completely eliminate account hacking using phishing.
If suddenly you decide to enter your data on a phishing site, then enter the mail, not the phone number.
Source: https://habr.com/ru/post/400129/
All Articles