Nmap scanner as the main tool for movie hackers
Nmap is a free utility designed for a variety of customizable scanning of IP networks with any number of objects, determining the state of objects of the scanned network (ports and their corresponding services). Initially, the program was implemented for UNIX systems, but now versions are available for a variety of operating systems.
Nmap also supports a large set of additional features, namely: determining the operating system of a remote host using TCP / IP stack fingerprints, invisible scanning, dynamic delay time and packet retry, parallel scanning, determining inactive hosts using the parallel ping method, scanning using false hosts, determining the presence of packet filters, direct (without using portmapper) RPC scanning, scanning using IP fragmentation, and also arbitrary indication of IP addresses and port numbers of scanned networks. In recent versions, the ability to write arbitrary scripts (scripts) in the Lua programming language has been added.
On the official website of the utility, a large collection of its use as an illustration of the work of hackers was made. Site owner Gordon Lyon, who for some reason chose the name Fyodor [Fyodor] with his pseudonym, is offered to anyone who first sees the use of the utility in the next movie, a gift T-shirt from their Zero Day Clothing Nmap Store.
')
Matrix Reloaded (Matrix: Reboot)
Although Nmap had previously flashed in various insignificant films, it was Matrix Reloaded ( Wikipedia , IMDB , Amazon ) that turned the utility into a screen star!
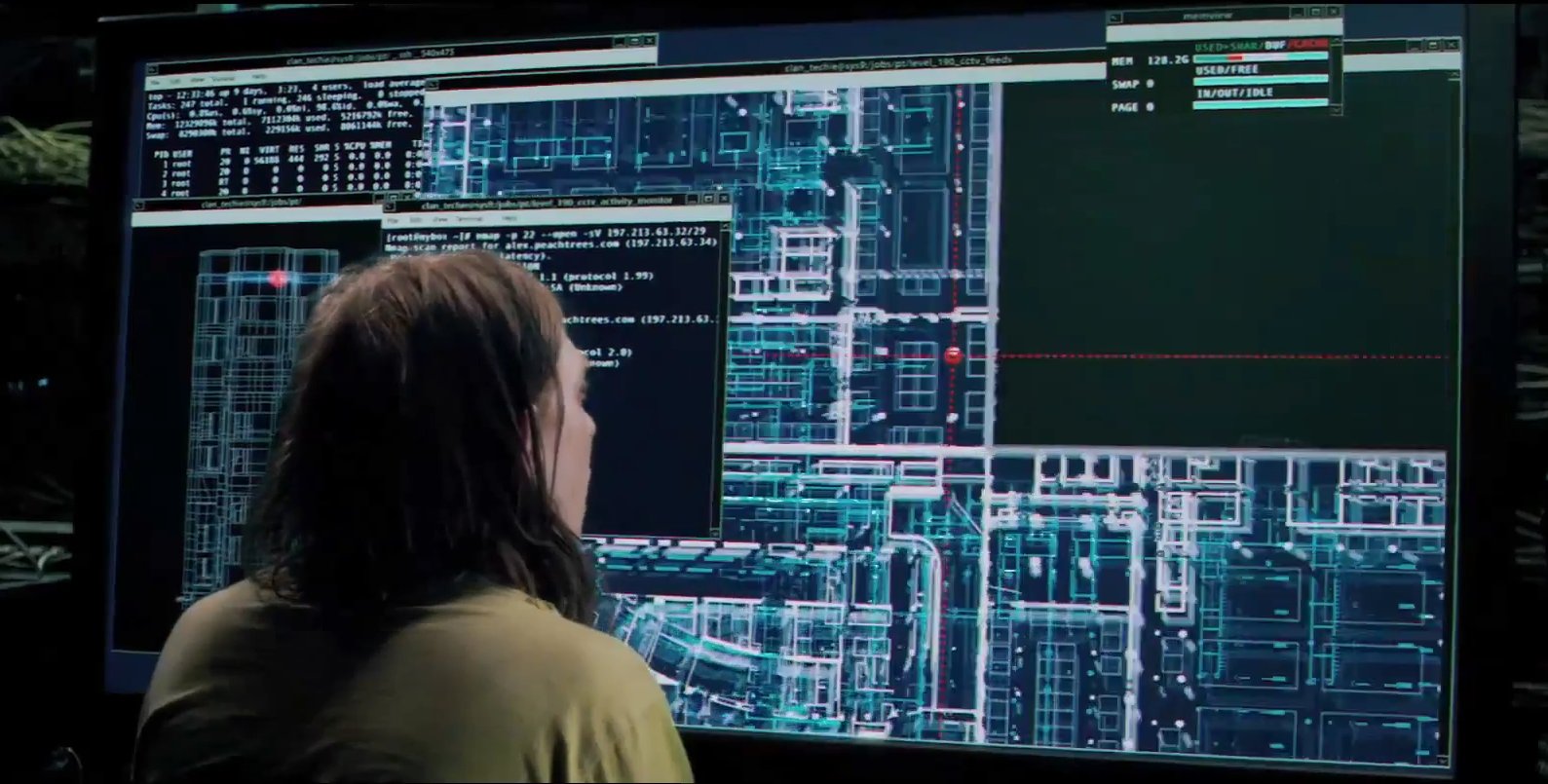
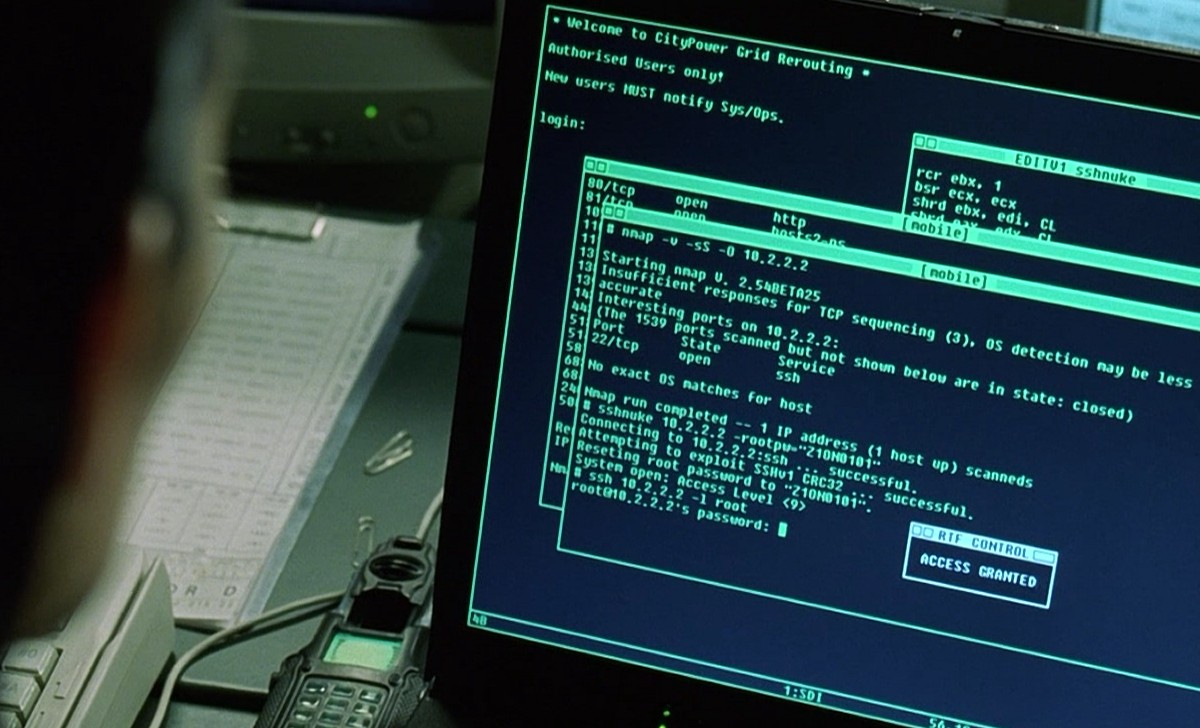
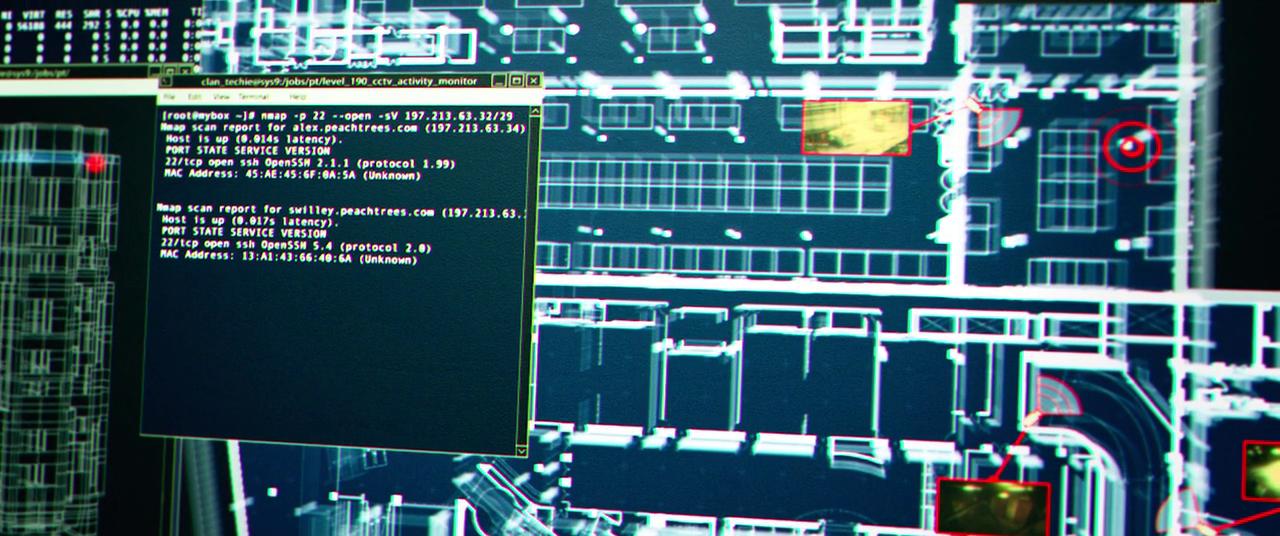
We all saw films like Hackers , in which the wacky colorful three-dimensional animations were trying to pass off as hacking tools. Therefore, Fedor was greatly surprised to see how the hacking was correctly shown in The Matrix Reloaded. In order to crack the city power system, Trinity launched Nmap v2.54BETA25, used it to search for a vulnerable SSH server, and launched the 2001 SSH1 exploit exploit exploit. Ay-yay-yay, city, is it possible?

On the site of Scotland Yard, employees of the computer crime unit posted a warning to those who watch this film, demanding not to try to repeat what they saw and not to hack computers.
Snowden / Snowden
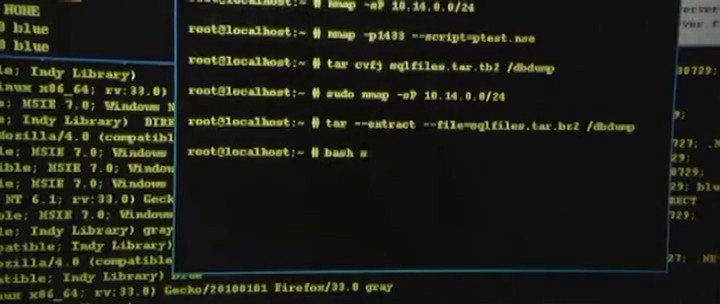
Oliver Stone's 2016 film ( Wikipedia , IMDB , Amazon ) adapts a massive leak of secret documents, initiated by Edward Snowden, who uncovered the truth about widespread wiretapping of US citizens conducted by the NSA. In one of the first scenes of Snowden in the training group, the CIA performs the task of network security, which should take students from 5 to 8 hours. But with the help of Nmap and a special script for Nmap NSE called ptest.nse, Snowden, to the surprise of the professor, passes the test in 38 minutes! Similar to the output of the program text is captured on the screens of other students, but in order to make out what is specifically written there, you will have to wait for the 4K version of the film.

Trailer (nmap visible on the 34th second)
Dredd / Judge Dredd
Dredd ( Wikipedia , IMDB , Amazon ), an adaptation of the well-known comic strip Judge Dredd , was released in 2012, and nmap can be seen in many of its scenes.
In the large post-apocalyptic metropolis of Mega City One, the law rests solely on Judges from the Department of Justice - police officers with the right to judge, sentence and execute offenders. More than the other judges, the inexorable and ruthless Judge Dredd suggests fear on criminals. Together with Cadet Judge Cassandra Anderson, they penetrate the notorious skyscraper controlled by a former prostitute now drug dealer Ma-Ma. In order to study the computer network of a skyscraper and find its weak points, they use nmap! The trailer has a glimpse of nmap that scans TCP port 22 (SSH):

Elysium / Elysium: Paradise is not on Earth
In the 2013 sci-fi movie Elysium ( Wikipedia , IMDB , Amazon ) they play Matt Damon and Jodie Foster. The action takes place in 2154, when the overpopulated Earth suffers from poverty, crime and destruction, while the rich live on a luxurious space station. Nmap version 13 (here it is, the future) is used to scan ports in Damon’s computer-augmented brain before copying the data it carries around to attempt to crack the space station.

Fantastic Four / Fantastic Four
Fantastic Four ( Wikipedia , IMDB , Amazon ) - a large-budget adaptation of Marvel Comics comics from 2015. In the film, Sue Storm uses nmap skills to search for a companion. On her computer you can see “IPSCAN”, then “TRACEROUTE”, “PORTSCAN”, and as a result “NMAP”.


Who am i / who am i
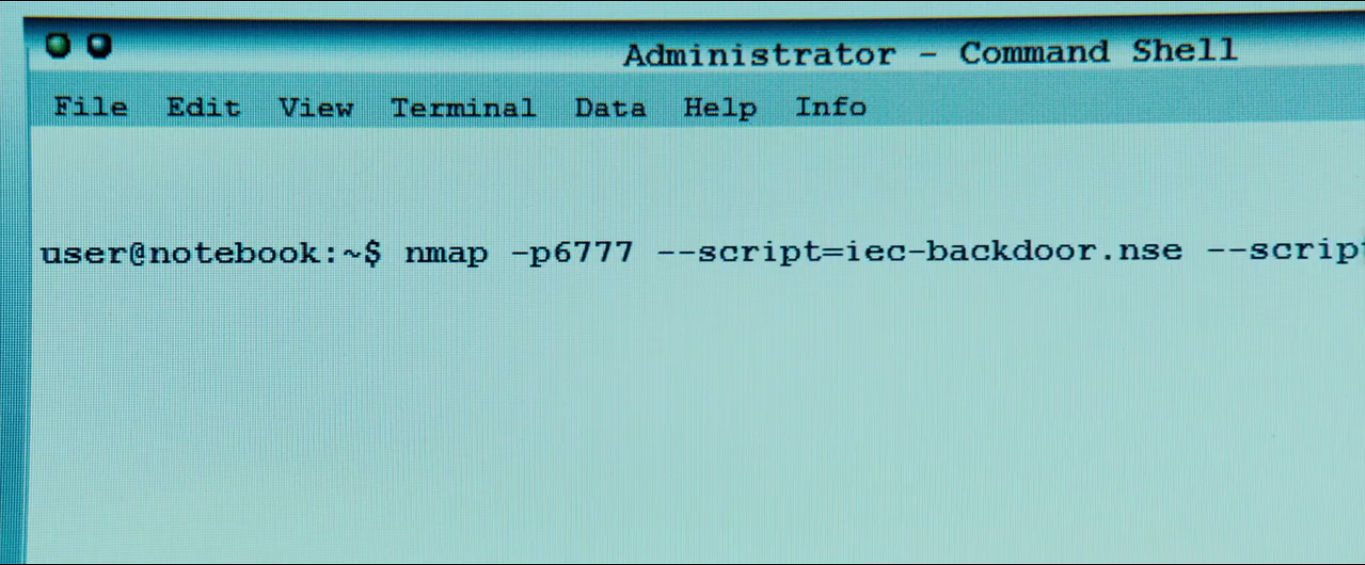
Who Am I — No System is Safe ( Wikipedia , IMDB , Amazon ) is a German cyber-thriller of 2014 telling about fighting hacker groups (retired from Anonymous) who are trying to outdo each other in bold hacking systems and various pranks. During the initiation scene (13:40), the protagonist, Benjamin, shows his skills by entering the electricity supplier’s network and launching a small blackout. He does this with his Nmap Scripting Engine ( NSE ) script. The script name, iec-backdoor.nse, refers to the standards of the International Electrotechnical Commission ( IEC ), which manages the power networks and their equipment. Such realism is an interesting touch!

Bourne Ultimatum / Bourne Ultimatum
In the movie The Bourne Ultimatum ( Wikipedia , IMDB , Amazon ), CIA employees need to hack the newspaper's mail server ( The Guardian UK ) in order to read the letters of the reporter they killed. To do this, they use Nmap and its new official Zenmap GUI ! Nmap reports that the server is running SSH 3.9p1, Posfix smtpd, and name server (apparently, bind). They also abundantly use Bash, a shell, so to speak "Bourne-again."


Die Hard 4 / Die Hard 4
Yupi-kai-her! In Die Hard 4: Live Free or Die Hard ( Wikipedia , IMDB , Amazon ), detective John MacLean is charged with arresting hacker Matthew Farrell, suspected by the FBI of infiltrating their system. Then they demand from him to prevent the genius terrorist-villain Thomas Gabriel, who is trying to destroy the whole world. In this scene, Farrell demonstrates nmap's skills.


The Girl with the Dragon Tattoo / The Girl with the Dragon Tattoo
The Girl with the Dragon Tattoo (Män som hatar kvinnor) - thriller of 2009 ( Wikipedia , IMDB , Amazon ), shot on bestseller Stieg Larsson. He tells the story of Lisbeth, a problem hacker girl who suffers from Asperger syndrome and the abuse of various bosses. She conducts a journalistic investigation into the murder of 40 years ago. In the list of the most profitable films of non-English origin in 2009, he ranked third.
A small scene with nmap occurs in the 6th minute of the movie. We are talking about the original - a big-budget Hollywood remake of the film was released in 2011 ( IMDB , Wikipedia , Amazon ), and, perhaps, lost a lot from the fact that there are no scenes with Nmap in it!


GI Joe: Retaliation / GI Joe: Throw Cobra 2
In the 2013 action movie GI Joe: Retaliation ( Wikipedia , IMDB , Amazon ), nmap is used to launch a nuclear weapon. The utility interface is odd, but apparently, they scan the launch shaft with nmap, log in ssh on each intercontinental ballistic missile found, they do su root and execute commands to bring it into combat readiness and launch.

The Listening
In the 2006 film The Listening ( Wikipedia , IMDB , Amazon ) about a former NSA employee who escaped from an agency and opened a secret anti-wiretap station in the Italian Alps, Nmap and NmapFE are used.
Justice League: Doom / Justice League: Doom
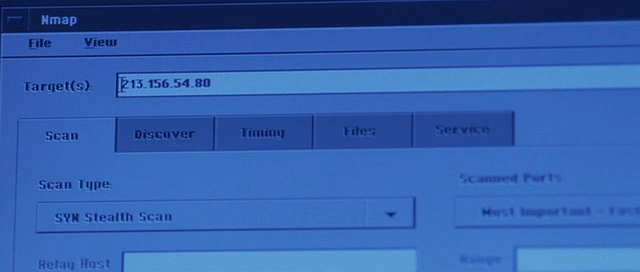
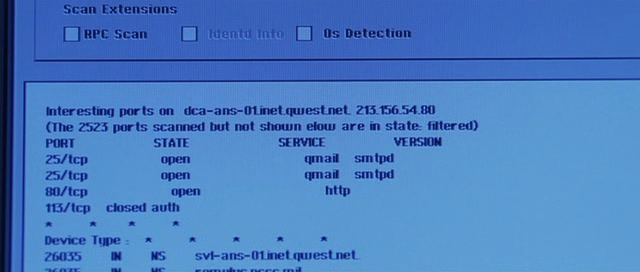
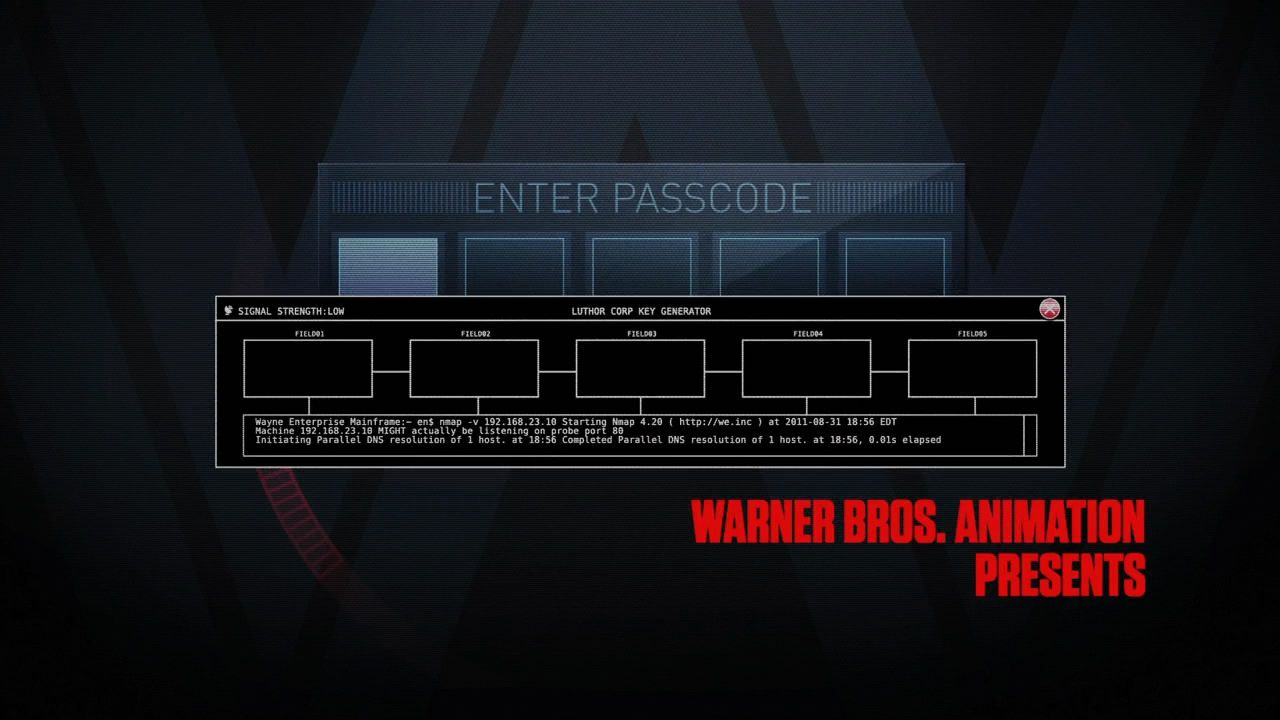
In the 2012 Justice League: Doom cartoon ( Wikipedia , IMDB , Amazon ), nmap is used during opening credits. In the movie, Batman, Superman, Wonder Woman, and Green Lantern confront a team of supervillains. Interestingly, in most cases, filmmakers have changed the link from nmap.org to we.inc (Wayne Enterprises) in the utility output. In addition, in August 2011, Nmap (4.20) of 2006 was used. Batman, of course, needs to do all sorts of important and heroic things, but really, it’s impossible to take five minutes to install the latest version of nmap!

Abduction / Chase
Abduction ( Wikipedia , IMDB , Amazon ) - 2011 thriller. A teenager is trying to discover the truth about himself by finding his infant photo on the site to search for missing children. In the process, a Serbian hacker using nmap is chasing him, as part of other villains. If the nmap backgrounds in the screenshots seem familiar to you, it’s because the filmmakers simply pulled them off from The Matrix Reloaded.


Extracted / Extract
The 2012 NF thriller Extracted ( IMDB , Amazon ) talks about the scientist who invented the technology of viewing human memories, but gets into trouble, penetrating the consciousness of a heroin addict suspected of murder. Here nmap is used as part of the system to enter the human mind (maybe it's an NSE script).
13: Game of Death / 13
Nmap was used in the Thai thriller 13: Game of Death ( Wikipedia , IMDB , Amazon ) 2006, also known as "13 Beloved" and "13 game sayawng." The film tells the story of a man performing 13 tasks in order to win $ 100,000,000. Assignments are becoming harder, more dangerous, more illegal and grotesque. What would you do for $ 100 lyams? One of the friends of the main character, a sysadmin, begins to worry about his friend and demonstrates the skills of using nmap by hacking the website of this perverted game.

Battle Royale / Royal Battle
Battle Royale ( Wikipedia , IMDB , Amazon ), also known as Batoru Rowaiaru, is a very strange and controversial Japanese film about ninth-graders sent by the government to a deserted island. They were supplied with exploding collars and forced to kill each other as part of a perverse game of survival. One of them turned out to be a hacker, and in scenes with it you can see the source codes nmap.


Broken Saints / Broken righteous
Broken Saints ( Wikipedia , IMDB , Amazon ), the award-winning video mix series of 24 chapters, first published online from 2001 to 2003. Then it was distributed on DVD by 20th Century Fox. This is a tangled 12-hour story about four strangers from remote corners of the Earth, connected by a common vision of the coming evil.
One of them, Raimi, a young security software developer, uses nmap to hack systems and uncover his employer's corporate plots. The scene with nmap is in the second chapter.



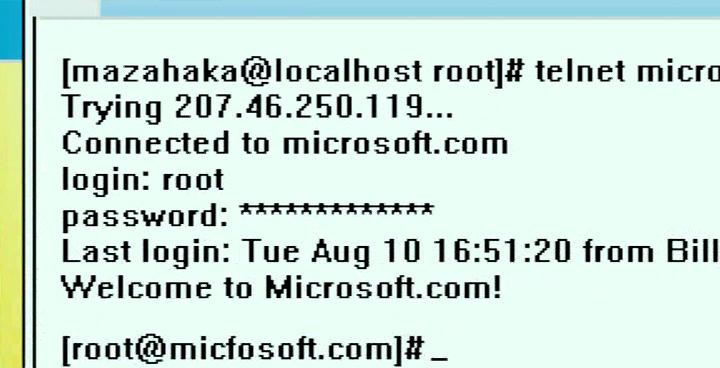
Hottabych
Nmap and telnet are used by the teenage hacker Gena to hack microsoft.com in the 2006 Russian movie Hottabych ( Wikipedia , IMDB , Film Search ). Microsoft and the US intelligence services were very upset as a result, and in order to disclose it, an attractive hacker girl Annie was sent to Russia. The film also features an epic battle between the jinn for power over Earth.


HaXXXor: No Longer Floppy
Nmap appeared even in a series of low-cost soft-porn "HaXXXor". “HaXXXor Volume 1: No Longer Floppy” includes a rather long scene with a training session on using the nmap model E-Lita. In the pictures she is still dressed.




Bloody Monday / Bloody Monday
In the Japanese drama series Bloody Monday (2008 - 2010), a hacker named Falcon is forced to use his computer skills to uncover the mysterious project “Bloody Monday” and prevent biological terrorists from attacking Tokyo. After Falcon hacks into the security bases of Japan, he is arrested, but he easily gets off with a father working in this department and ties him up with hacking.
Two years later, the security service received information that a group of terrorists that destroyed the population of a small city in Russia, plans to spray a deadly dangerous virus in Tokyo, but the agent investigating this case died. To get data on the occasion in Russia, the head of the security service asks for help Falcon. Realizing that he has no choice, Takagi agrees, not knowing how his life and the lives of the people around him will change drastically, since the terrorists also have their own plans for a talented teenager
Nmap is used in several episodes, starting with the first episode of the first season. Also on the series are other real-life utilities related to computer security, including Netcat, Rainbow Crack, and the Sadmind exploit.


Source: https://habr.com/ru/post/399375/
All Articles