Wi-Fi monitors you, or Wi-Fi as a monitoring system
People who live in cities, without even realizing it, are in Wi-Fi networks all day: home and city, at work and in the subway, in a shopping center and in a restaurant — they are everywhere. Only one conclusion: if you live in the city, you can’t hide from Wi-Fi.
Only the Moscow city Wi-Fi network covers 24 open areas: Moscow Zoo, VDNH, parks and pedestrian streets, 14 public spaces (libraries and cultural centers), 150 student dormitory buildings. In total, there are more than 8.5 thousand access points (hot spots) in the capital. Free Wi-Fi is available in metro and ground public transport (1).
Manufacturers of personal portable devices (smartphones, tablets) have long learned to use the wide distribution of Wi-Fi for their own purposes as an auxiliary tool to help the geolocation service to determine the location of the device.
')
Initially, the geolocation service of smartphones uses the GPS module to determine the location, the A-GPS technology, which accelerates the cold start of the GPS receiver by receiving almanac and ephemeris via the Internet (that is, via 3G / LTE / Wi-Fi), as well as GSM cell towers. If the position is successfully calculated, the device scans Wi-Fi-air and sends via the same Internet data on the geographical location of nearby Wi-Fi access points, which are collected into a common database of the operating system (OS) geolocation system manufacturer:
- for Android smartphones - to the Google database;
- for iPhone smartphones - into the Apple2 database (2).
This information is used both by Google and Apple applications, as well as by other applications installed on the smartphone (fitness trackers, etc.).
The manufacturer of the smartphone OS builds and maintains a global database on the location of all Wi-Fi access points. It helps to determine the location of the personal portable device in the case when there is Wi-Fi nearby, but there is no GPS signal. The smartphone sends data about nearby Wi-Fi access points via the Internet and receives data about its location in response. The benefit for the owner of the smartphone in this case is obvious: the smartphone quickly and accurately determines its location anywhere in the world.
The OS manufacturer collects and stores the movement history of each device. Not only geographic points are saved, but also detailed routes. The transmission of location data can be turned off, but in this case the routes will no longer be saved, but geographic points are still displayed. You can go to the website of the OS manufacturer and see (3)
The history of movement is not impersonal, but may be tied to a telephone number, which is sufficient for identification. Potentially, the GSM operator has access to the movement history on the basis of cell trilateralization (regardless of the phone type), as well as the smartphone OS manufacturers, whose geolocation service tracks the location in as much detail as possible and stores it in the database.
GPS is unavailable inside buildings and on subways, but GSM trilateration will work, albeit not with such high accuracy (after all, there is a signal from the cellular operator both in buildings and in the subway). Information about Wi-Fi points will be collected in the database of manufacturers of operating systems.
In many buildings, corporate and public Wi-Fi networks are fully functional. Manufacturers of Wi-Fi infrastructure and Wi-Fi service providers have long learned to position personal Wi-Fi devices in real time with an accuracy of up to 1 m.
Wi-Fi positioning systems are used by owners of shopping centers, airports, stadiums and subways for collection and analysis. This information can be used by urban Wi-Fi networks, which in Moscow, for example, cover almost the entire public space of a city.
If a person is authenticated only once in a Wi-Fi network, and this most often happens by receiving a password via SMS, from this moment the address of his Wi-Fi adapter to the phone number appears, that is, the person is identified. Even if he never connected to the network again, information about his movement will still be collected, as the binding remains, and the Wi-Fi adapter even in sleep mode with a certain frequency performs an active scan, at which it transmits its address. It is worth mentioning that in recent versions of the iPhone, with active scanning, the random address of the Wi-Fi adapter is indicated, which complicates the task of tracking the movement of a specific device.
A good example that demonstrates the capabilities of Wi-Fi analytics is the interactive map (4) of moving Wi-Fi users in the Moscow metro (Fig. 1). This Wi-Fi network was built by Maxima Telecom.
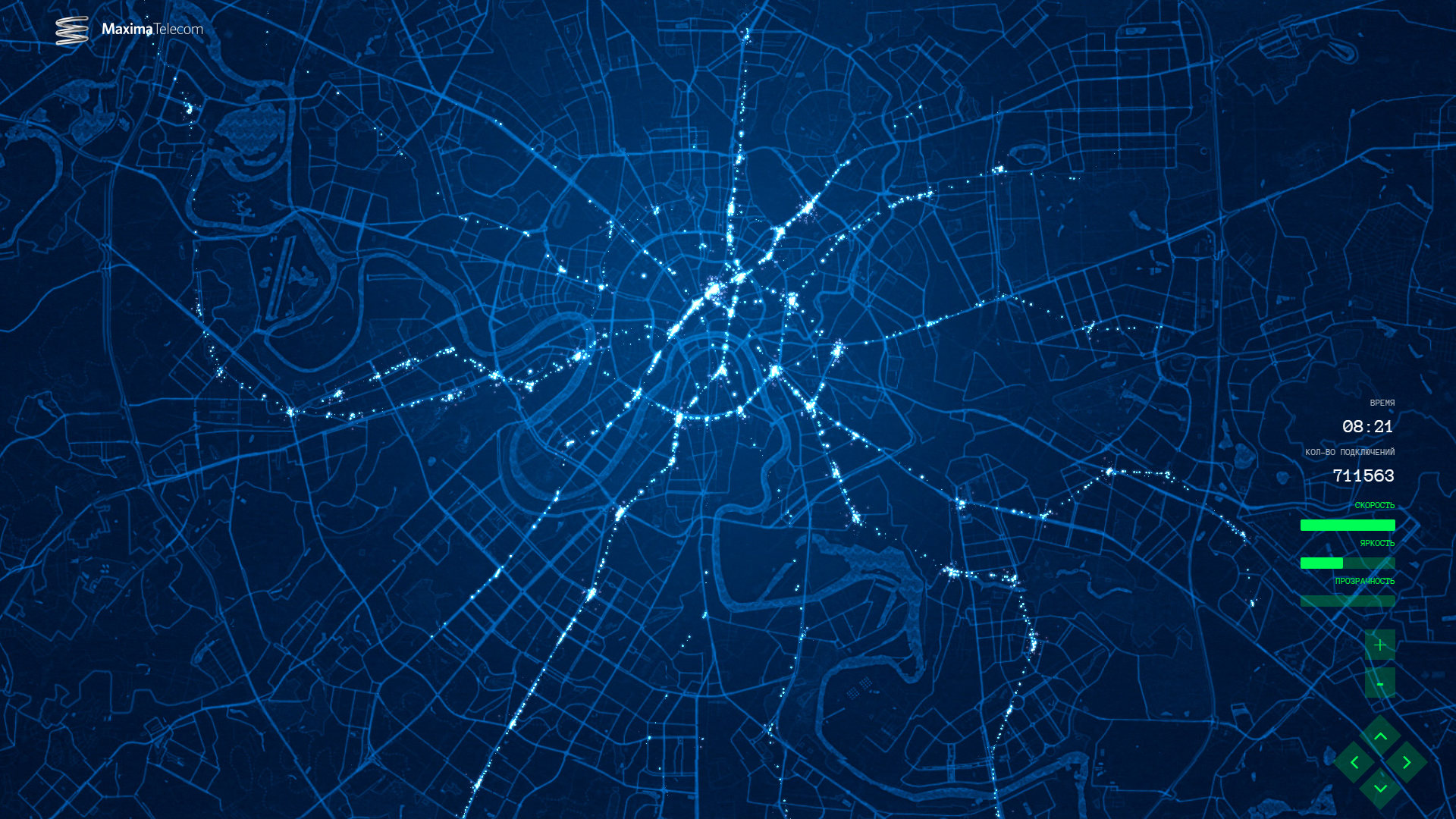
Fig. 1. Interactive map of the movement of Wi-Fi users in the Moscow metro
In general, we can talk about very wide opportunities from mobile operators, smartphone OS manufacturers and Wi-Fi service providers for collecting and analyzing the history of user movement with the possibility of identification.
Collecting the history of a person’s movement in real time can be considered not only as a goal, but also a means for other analytics tools.
W-Fi works in the 2.4 and 5 GHz range, waves with such a frequency are very well absorbed by the human body, which is 70% water. This creates significant problems in terms of information transfer, but opens up vast possibilities for monitoring human movement (5).
In August 2016, a group of researchers from Northwestern Polytechnic University of China posted in an archive of research (6) an article (7) describing the FreeSense system, which can identify a person (in a group of 6 people) passing through an imaginary line between Wi-Fi Fi-point and Wi-Fi-client with an accuracy of 89% (Fig. 2).

Fig. 2. Diagram of the Chinese FreeSense system for human identification
The system must be pre-trained: it must study the shape of the human body and create a Wi-Fi pattern to identify it further.
Another group of researchers from Australia and the UK in March 2016 presented a similar system called Wi-Fi ID (8). Wi-Fi ID uses the same pattern: each person has both an individual walk and an individual Wi-Fi pattern. This system with an accuracy of 93% identifies a person in a group of 2 people and with an accuracy of 77% - in a group of 6 people.
Identification systems via Wi-Fi require preliminary training, and data on the movement of a person in real time can help. By identifying a person when crossing an imaginary line, it is potentially possible to create for him a unique Wi-Fi pattern in automatic mode. In the future, to determine its location does not need to have a working smartphone. Thus, identification via Wi-Fi is starting to look like a video surveillance system.
A couple of researchers at the Massachusetts Institute of Technology in 2013 published a paper (9), where they use a conventional Wi-Fi router located behind a wall to determine the number of people in a room, detect some basic gestures, and even recognize text written in air by hand .
Using more sensitive sensors, the same researchers developed a system that can distinguish between two people behind a wall (10) and remotely monitor a person’s breathing and heartbeat with an accuracy of 99% (11).
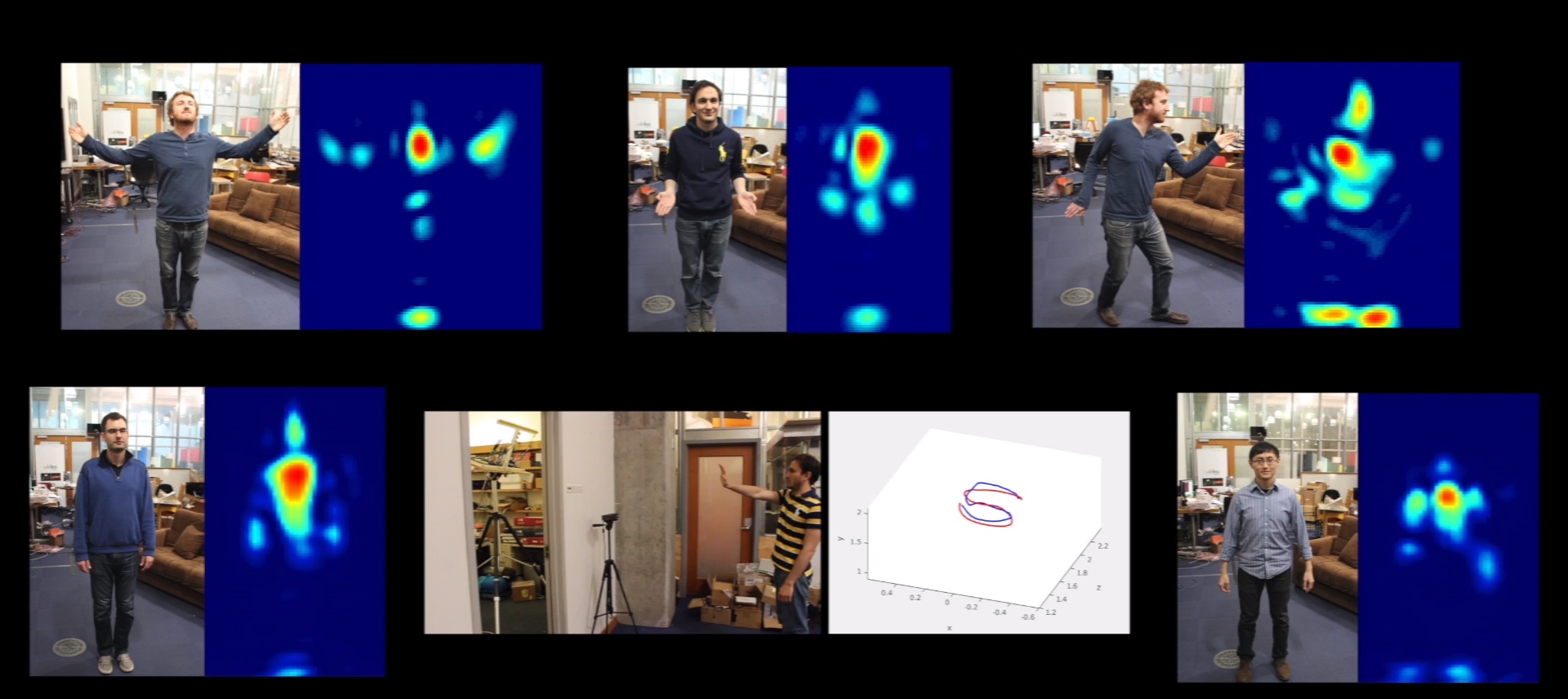
Fig. 3. Determine the number of people in a room, recognize gestures, monitor breathing and heartbeat via Wi-Fi
The Emerald device (12) is focused on the elderly, it is installed in the center of an apartment or house and, studying the physical activity of a person, can determine its fall. The device not only recognizes, but also tries to predict the fall before it happened, exploring the motion model.

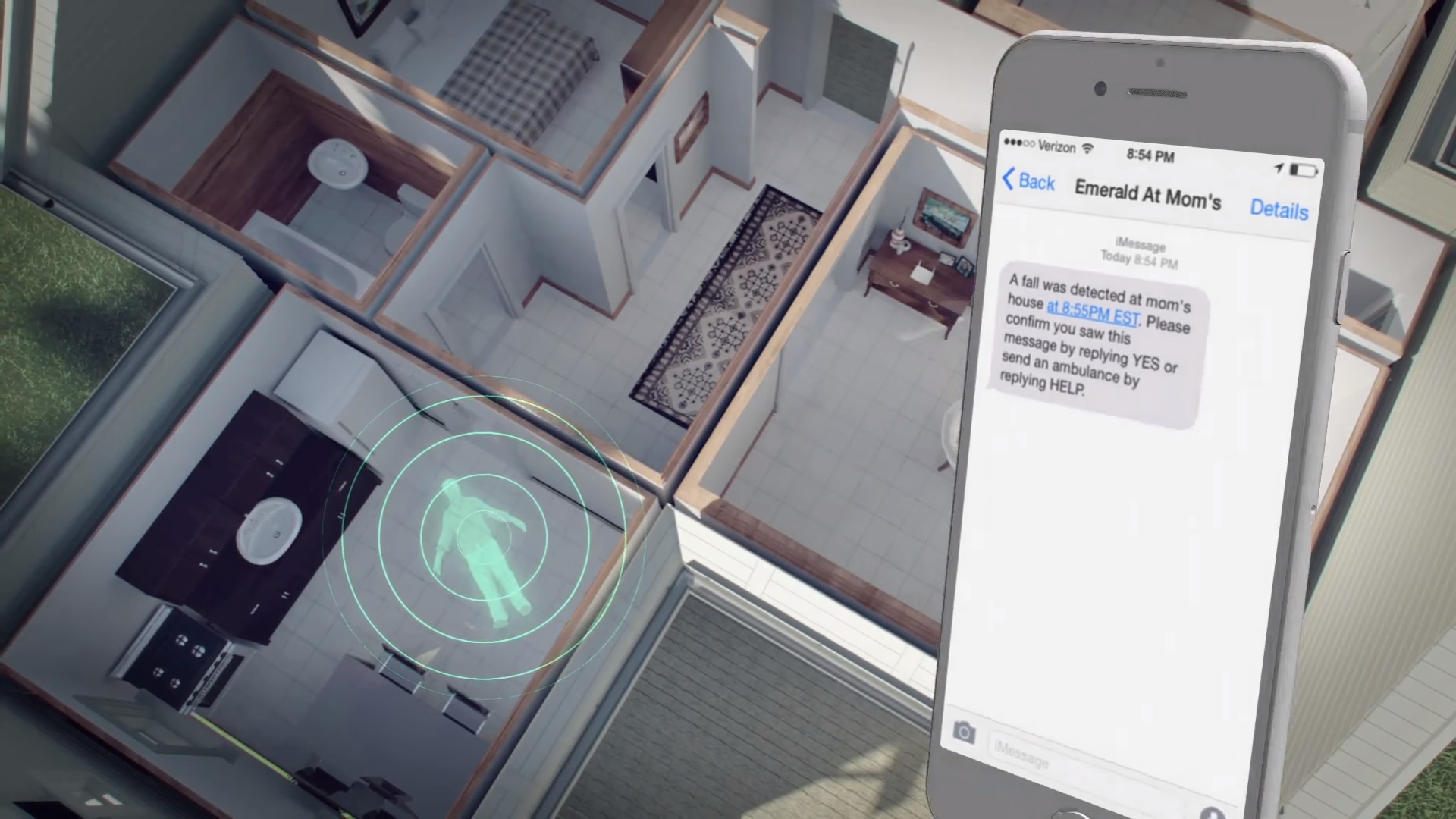
Fig. 4. Emerald device recognizing the fall of a person
Wi-Fi signal can be used to distinguish much smaller movements.
The WiKey system (13) determines which keys the user presses on the keyboard and tracks the movement of the fingers. Having trained, this system recognizes the written text with an accuracy of 93.5%, using an exclusively public Wi-Fi router and a special program code.
A group of researchers from the Shenzhen University of China in 2014 introduced the technology (14), which “hears” what people say when analyzing the distortions in the Wi-Fi signal generated by the movement of the mouth. The system identifies words from the dictionary of recognizable words with an accuracy of 91%, if one person speaks, and with an accuracy of 74%, if two speakers.
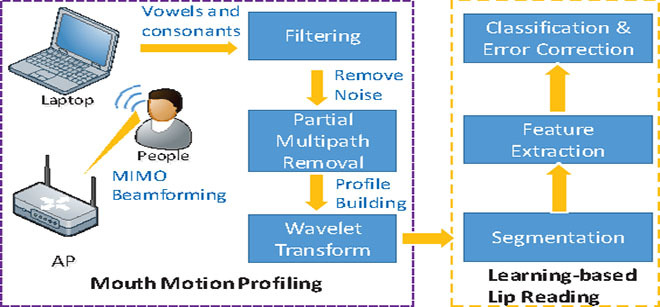
Fig. 5. Technology that recognizes speech over Wi-Fi
All of these studies reverse the concept of Wi-Fi as a vehicle only for information transfer. These systems work so far only with preliminary training, but if you can automate it, using, for example, information obtained via GPS / GSM / Wi-Fi, then very serious possibilities for monitoring human actions open up.
You can start by adding a personal Wi-Fi template to a person’s data. Then move on to learning to recognize his gestures, breathing, heartbeat and posture. Then - to learn the movement of the fingers and the mouth to distinguish the written text and the spoken words.
The beauty of this technology lies in the fact that all this is potentially possible when using a conventional home Wi-Fi router. Such methods are likely to bring great benefits: they will provide additional security for children and the elderly, make the smart home even smarter, and perhaps in the future, video surveillance systems will be built on Wi-Fi routers.
However, if this tool falls into the hands of intruders, they will get access to a huge amount of information. It will be quite unnoticeable to install malicious code on your home Wi-Fi router and send the collected data via the Internet, and the owner will never know about it.
Only the Moscow city Wi-Fi network covers 24 open areas: Moscow Zoo, VDNH, parks and pedestrian streets, 14 public spaces (libraries and cultural centers), 150 student dormitory buildings. In total, there are more than 8.5 thousand access points (hot spots) in the capital. Free Wi-Fi is available in metro and ground public transport (1).
The global base of the location of all access points Wi-Fi
Manufacturers of personal portable devices (smartphones, tablets) have long learned to use the wide distribution of Wi-Fi for their own purposes as an auxiliary tool to help the geolocation service to determine the location of the device.
')
Initially, the geolocation service of smartphones uses the GPS module to determine the location, the A-GPS technology, which accelerates the cold start of the GPS receiver by receiving almanac and ephemeris via the Internet (that is, via 3G / LTE / Wi-Fi), as well as GSM cell towers. If the position is successfully calculated, the device scans Wi-Fi-air and sends via the same Internet data on the geographical location of nearby Wi-Fi access points, which are collected into a common database of the operating system (OS) geolocation system manufacturer:
- for Android smartphones - to the Google database;
- for iPhone smartphones - into the Apple2 database (2).
This information is used both by Google and Apple applications, as well as by other applications installed on the smartphone (fitness trackers, etc.).
Why does the geolocation service with a GPS module need a Wi-Fi module?
The manufacturer of the smartphone OS builds and maintains a global database on the location of all Wi-Fi access points. It helps to determine the location of the personal portable device in the case when there is Wi-Fi nearby, but there is no GPS signal. The smartphone sends data about nearby Wi-Fi access points via the Internet and receives data about its location in response. The benefit for the owner of the smartphone in this case is obvious: the smartphone quickly and accurately determines its location anywhere in the world.
Can Google and Apple keep moving history?
The OS manufacturer collects and stores the movement history of each device. Not only geographic points are saved, but also detailed routes. The transmission of location data can be turned off, but in this case the routes will no longer be saved, but geographic points are still displayed. You can go to the website of the OS manufacturer and see (3)
Identification by phone number
The history of movement is not impersonal, but may be tied to a telephone number, which is sufficient for identification. Potentially, the GSM operator has access to the movement history on the basis of cell trilateralization (regardless of the phone type), as well as the smartphone OS manufacturers, whose geolocation service tracks the location in as much detail as possible and stores it in the database.
Geolocation inside buildings and subways
GPS is unavailable inside buildings and on subways, but GSM trilateration will work, albeit not with such high accuracy (after all, there is a signal from the cellular operator both in buildings and in the subway). Information about Wi-Fi points will be collected in the database of manufacturers of operating systems.
Wi-Fi positioning
In many buildings, corporate and public Wi-Fi networks are fully functional. Manufacturers of Wi-Fi infrastructure and Wi-Fi service providers have long learned to position personal Wi-Fi devices in real time with an accuracy of up to 1 m.
Wi-Fi positioning systems are used by owners of shopping centers, airports, stadiums and subways for collection and analysis. This information can be used by urban Wi-Fi networks, which in Moscow, for example, cover almost the entire public space of a city.
It is necessary to connect once, and you will not be forgotten
If a person is authenticated only once in a Wi-Fi network, and this most often happens by receiving a password via SMS, from this moment the address of his Wi-Fi adapter to the phone number appears, that is, the person is identified. Even if he never connected to the network again, information about his movement will still be collected, as the binding remains, and the Wi-Fi adapter even in sleep mode with a certain frequency performs an active scan, at which it transmits its address. It is worth mentioning that in recent versions of the iPhone, with active scanning, the random address of the Wi-Fi adapter is indicated, which complicates the task of tracking the movement of a specific device.
Wi-Fi analytics examples
A good example that demonstrates the capabilities of Wi-Fi analytics is the interactive map (4) of moving Wi-Fi users in the Moscow metro (Fig. 1). This Wi-Fi network was built by Maxima Telecom.

Fig. 1. Interactive map of the movement of Wi-Fi users in the Moscow metro
In general, we can talk about very wide opportunities from mobile operators, smartphone OS manufacturers and Wi-Fi service providers for collecting and analyzing the history of user movement with the possibility of identification.
Collecting the history of a person’s movement in real time can be considered not only as a goal, but also a means for other analytics tools.
W-Fi works in the 2.4 and 5 GHz range, waves with such a frequency are very well absorbed by the human body, which is 70% water. This creates significant problems in terms of information transfer, but opens up vast possibilities for monitoring human movement (5).
Wi-Fi Identification
In August 2016, a group of researchers from Northwestern Polytechnic University of China posted in an archive of research (6) an article (7) describing the FreeSense system, which can identify a person (in a group of 6 people) passing through an imaginary line between Wi-Fi Fi-point and Wi-Fi-client with an accuracy of 89% (Fig. 2).

Fig. 2. Diagram of the Chinese FreeSense system for human identification
The system must be pre-trained: it must study the shape of the human body and create a Wi-Fi pattern to identify it further.
Another group of researchers from Australia and the UK in March 2016 presented a similar system called Wi-Fi ID (8). Wi-Fi ID uses the same pattern: each person has both an individual walk and an individual Wi-Fi pattern. This system with an accuracy of 93% identifies a person in a group of 2 people and with an accuracy of 77% - in a group of 6 people.
Identification systems via Wi-Fi require preliminary training, and data on the movement of a person in real time can help. By identifying a person when crossing an imaginary line, it is potentially possible to create for him a unique Wi-Fi pattern in automatic mode. In the future, to determine its location does not need to have a working smartphone. Thus, identification via Wi-Fi is starting to look like a video surveillance system.
Gesture recognition, tracking of breath and heartbeat via Wi-Fi
A couple of researchers at the Massachusetts Institute of Technology in 2013 published a paper (9), where they use a conventional Wi-Fi router located behind a wall to determine the number of people in a room, detect some basic gestures, and even recognize text written in air by hand .
Using more sensitive sensors, the same researchers developed a system that can distinguish between two people behind a wall (10) and remotely monitor a person’s breathing and heartbeat with an accuracy of 99% (11).

Fig. 3. Determine the number of people in a room, recognize gestures, monitor breathing and heartbeat via Wi-Fi
Wi-Fi Drop Detection
The Emerald device (12) is focused on the elderly, it is installed in the center of an apartment or house and, studying the physical activity of a person, can determine its fall. The device not only recognizes, but also tries to predict the fall before it happened, exploring the motion model.


Fig. 4. Emerald device recognizing the fall of a person
Distinction of small movements
Wi-Fi signal can be used to distinguish much smaller movements.
Recognition of written text
The WiKey system (13) determines which keys the user presses on the keyboard and tracks the movement of the fingers. Having trained, this system recognizes the written text with an accuracy of 93.5%, using an exclusively public Wi-Fi router and a special program code.
Speech recognition
A group of researchers from the Shenzhen University of China in 2014 introduced the technology (14), which “hears” what people say when analyzing the distortions in the Wi-Fi signal generated by the movement of the mouth. The system identifies words from the dictionary of recognizable words with an accuracy of 91%, if one person speaks, and with an accuracy of 74%, if two speakers.

Fig. 5. Technology that recognizes speech over Wi-Fi
Wi-Fi as a monitoring system
All of these studies reverse the concept of Wi-Fi as a vehicle only for information transfer. These systems work so far only with preliminary training, but if you can automate it, using, for example, information obtained via GPS / GSM / Wi-Fi, then very serious possibilities for monitoring human actions open up.
You can start by adding a personal Wi-Fi template to a person’s data. Then move on to learning to recognize his gestures, breathing, heartbeat and posture. Then - to learn the movement of the fingers and the mouth to distinguish the written text and the spoken words.
The beauty of this technology lies in the fact that all this is potentially possible when using a conventional home Wi-Fi router. Such methods are likely to bring great benefits: they will provide additional security for children and the elderly, make the smart home even smarter, and perhaps in the future, video surveillance systems will be built on Wi-Fi routers.
However, if this tool falls into the hands of intruders, they will get access to a huge amount of information. It will be quite unnoticeable to install malicious code on your home Wi-Fi router and send the collected data via the Internet, and the owner will never know about it.
Sources
1 According to the official website of the mayor of Moscow www.mos.ru/news/item/14867073 .
2 According to Apple support, support.apple.com/ru-ru/HT203033 .
3 maps.google.com/locationhistory .
4 map.maximatelecom.ru .
5 Using material www.theatlantic.com/technology/archive/2016/08/wi-fi-surveillance/497132 .
6 arxiv.org/abs/1608.03430 .
7 arxiv.org/pdf/1608.03430v1 .
8 ieeexplore.ieee.org/document/7457075 .
9 people.csail.mit.edu/fadel/wivi .
10 rfcapture.csail.mit.edu .
11 witrack.csail.mit.edu/vitalradio .
12 www.emeraldforhome.com .
13 dl.acm.org/citation.cfm?id=2790109 .
14 ieeexplore.ieee.org/document/7384744
Article published in the journal "Security Systems" № 5/2016 of the company "Grotek"
secuteck.ru/imag/ss-5-2016
2 According to Apple support, support.apple.com/ru-ru/HT203033 .
3 maps.google.com/locationhistory .
4 map.maximatelecom.ru .
5 Using material www.theatlantic.com/technology/archive/2016/08/wi-fi-surveillance/497132 .
6 arxiv.org/abs/1608.03430 .
7 arxiv.org/pdf/1608.03430v1 .
8 ieeexplore.ieee.org/document/7457075 .
9 people.csail.mit.edu/fadel/wivi .
10 rfcapture.csail.mit.edu .
11 witrack.csail.mit.edu/vitalradio .
12 www.emeraldforhome.com .
13 dl.acm.org/citation.cfm?id=2790109 .
14 ieeexplore.ieee.org/document/7384744
Article published in the journal "Security Systems" № 5/2016 of the company "Grotek"
secuteck.ru/imag/ss-5-2016
Source: https://habr.com/ru/post/399149/
All Articles