Cloud token PKCS # 11 - myth or reality?
PKCS # 11 (Cryptoki) is a standard developed by RSA Laboratories for interacting with cryptographic tokens, smart cards and other similar devices using a unified software interface that is implemented through libraries.
The PKCS # 11 standard for Russian cryptography is supported by the technical committee for standardization "Cryptographic Information Security" ( TC 26 ).
If we talk about tokens with the support of Russian cryptography, then we can talk about software tokens , software and hardware tokens and hardware tokens .
Cryptographic tokens provide both the storage of certificates and key pairs (public and private key), and the execution of cryptographic operations in accordance with the PKCS # 11 standard. The weak link here is storing the private key. If the public key is missing, you can always restore it by the private key or take it from the certificate. Lossing / destroying a private key has dire consequences, for example, you cannot decrypt files encrypted on your public key, you cannot put an electronic signature (ES). To generate electronic signature, you need to generate a new key pair and, for some money, obtain a new certificate at one of the certification authorities.
')
Above, we mentioned software, hardware and software tokens. But you can consider another type of cryptographic token - cloud.
Today you will not surprise anyone with a cloudy flash drive . All the advantages and disadvantages of a cloud flash drive are almost one-on-one inherent in a cloud token.
The main thing here is the security of data stored in the cloud token, first of all, of private keys. Can this cloud token provide? We say - YES!
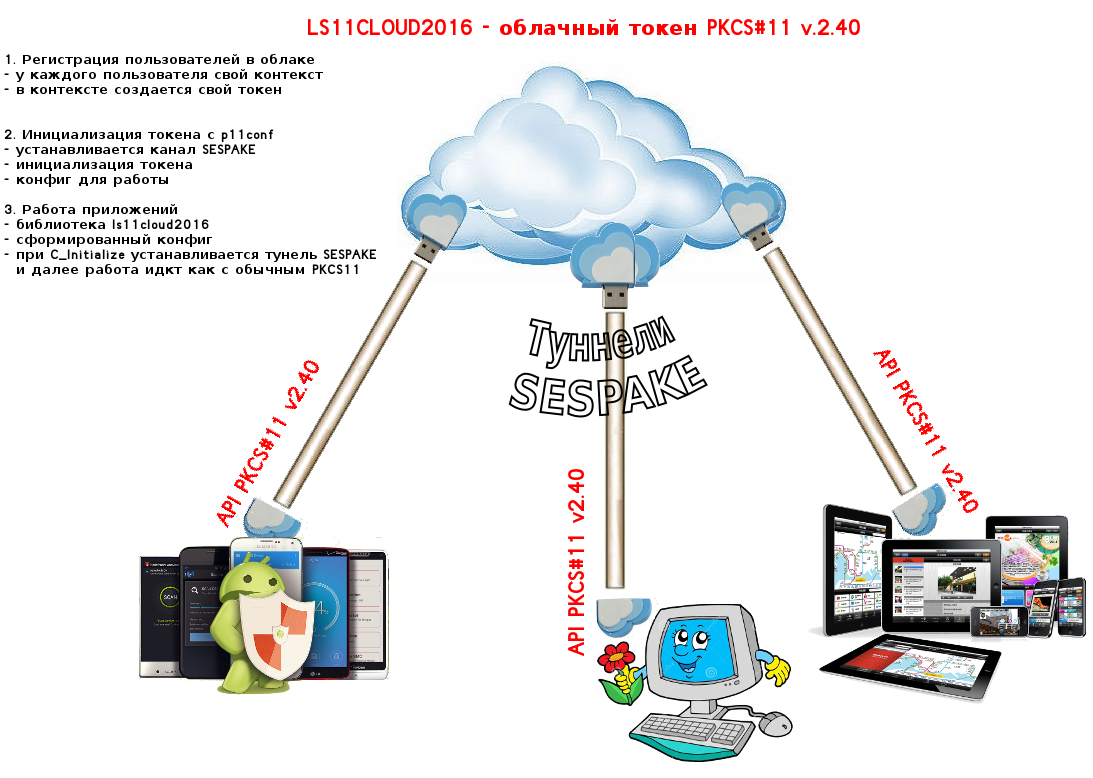
And so how does a cloud token work? The first step is to register the client in the token cloud. For this, a utility must be provided that allows you to access the cloud and register your login / nickname in it.
After registering in the cloud, the user must initialize his token, namely, set the token label and, most importantly, set the SO-PIN and user PIN. These operations should be carried out only over a secure / encrypted channel. To initialize the token, the pk11conf utility is used . To encrypt the channel, it is proposed to use the Magma-CTR encryption algorithm (GOST R 34.13-2015).
In order to generate a consistent key, on the basis of which traffic between the client and the server will be protected / encrypted, it is proposed to use the SESPAKE protocol recommended by TC 26 — a shared key generation protocol with password-based authentication .
As a password, on the basis of which the common key will be generated, it is proposed to use the one-time password mechanism . Since we are talking about Russian cryptography, it is natural to generate one-time passwords using the CKM_GOSTR3411_12_256_HMAC, CKM_GOSTR3411_12_512_HMAC or CKM_GOSTR3411_HMAC mechanisms .
Using this mechanism ensures that access to personal token objects in the cloud via SO and USER PIN codes is available only to the user who installed them using the pk11conf utility.
Everything, after performing these actions, the cloud token is ready for use. To access the cloud token, simply install the LS11CLOUD library on the PC. When using a cloud token in applications on Android and iOS platforms, an appropriate SDK is provided. It is this library that will be specified when connecting to the cloud token in the Redfox browser or written in the pkcs11.txt file for google-chrome . The LS11CLOUD library communicates with the token in the cloud also via a secure channel based on SESPAKE, created by calling the PKCS # 11 function C_Initialize!
That's all, now you can order a certificate, install it in your cloud token and go to the website of public services .
PKCS # 11 Cryptographic Cloud Service: From Myth to Reality :

The PKCS # 11 standard for Russian cryptography is supported by the technical committee for standardization "Cryptographic Information Security" ( TC 26 ).
If we talk about tokens with the support of Russian cryptography, then we can talk about software tokens , software and hardware tokens and hardware tokens .
Cryptographic tokens provide both the storage of certificates and key pairs (public and private key), and the execution of cryptographic operations in accordance with the PKCS # 11 standard. The weak link here is storing the private key. If the public key is missing, you can always restore it by the private key or take it from the certificate. Lossing / destroying a private key has dire consequences, for example, you cannot decrypt files encrypted on your public key, you cannot put an electronic signature (ES). To generate electronic signature, you need to generate a new key pair and, for some money, obtain a new certificate at one of the certification authorities.
')
Above, we mentioned software, hardware and software tokens. But you can consider another type of cryptographic token - cloud.
Today you will not surprise anyone with a cloudy flash drive . All the advantages and disadvantages of a cloud flash drive are almost one-on-one inherent in a cloud token.
The main thing here is the security of data stored in the cloud token, first of all, of private keys. Can this cloud token provide? We say - YES!
And so how does a cloud token work? The first step is to register the client in the token cloud. For this, a utility must be provided that allows you to access the cloud and register your login / nickname in it.
After registering in the cloud, the user must initialize his token, namely, set the token label and, most importantly, set the SO-PIN and user PIN. These operations should be carried out only over a secure / encrypted channel. To initialize the token, the pk11conf utility is used . To encrypt the channel, it is proposed to use the Magma-CTR encryption algorithm (GOST R 34.13-2015).
In order to generate a consistent key, on the basis of which traffic between the client and the server will be protected / encrypted, it is proposed to use the SESPAKE protocol recommended by TC 26 — a shared key generation protocol with password-based authentication .
As a password, on the basis of which the common key will be generated, it is proposed to use the one-time password mechanism . Since we are talking about Russian cryptography, it is natural to generate one-time passwords using the CKM_GOSTR3411_12_256_HMAC, CKM_GOSTR3411_12_512_HMAC or CKM_GOSTR3411_HMAC mechanisms .
Using this mechanism ensures that access to personal token objects in the cloud via SO and USER PIN codes is available only to the user who installed them using the pk11conf utility.
Everything, after performing these actions, the cloud token is ready for use. To access the cloud token, simply install the LS11CLOUD library on the PC. When using a cloud token in applications on Android and iOS platforms, an appropriate SDK is provided. It is this library that will be specified when connecting to the cloud token in the Redfox browser or written in the pkcs11.txt file for google-chrome . The LS11CLOUD library communicates with the token in the cloud also via a secure channel based on SESPAKE, created by calling the PKCS # 11 function C_Initialize!

That's all, now you can order a certificate, install it in your cloud token and go to the website of public services .
PKCS # 11 Cryptographic Cloud Service: From Myth to Reality :

Source: https://habr.com/ru/post/398677/
All Articles