Google's neural network has invented its own encryption protocol

Employees of Google Brain , one of the divisions of Google corporation, dealing with in-depth training, created a neural network that developed its own encryption protocol. Researchers Martin Abadi and David Andersen have shown that neural networks are able to develop simple ways to encrypt messages.
In an experiment conducted by experts, the neural network was able to create its own form of encryption through machine learning. This system was not taught the principles of encryption or special algorithms. Computer-developed encryption has proven to be quite simple, especially when compared with methods developed by humans. Nevertheless, this is a very interesting result of the study, where, according to the authors, "it was not supposed to demonstrate strong encryption."
During the experiment, the Google Brain team did not work with one neural network, but with three at once. They were named Alice, Bob and Eve. Each system was trained to communicate with the other two. Alice's job was to send secret messages to Bob. “He”, in turn, had to decrypt the message sent by Alice. And the task of the neural network Eve, in turn, was to monitor the communication of the other two networks.
')
In order to hide the meaning of the original message, Alice had to convert the plaintext so that Eve did not understand it. The modified text, however, must be understood by Bob, and only him. Initially, Alice and Bob agreed on how to change the text so that they could understand each other, and Eve would not understand anything.
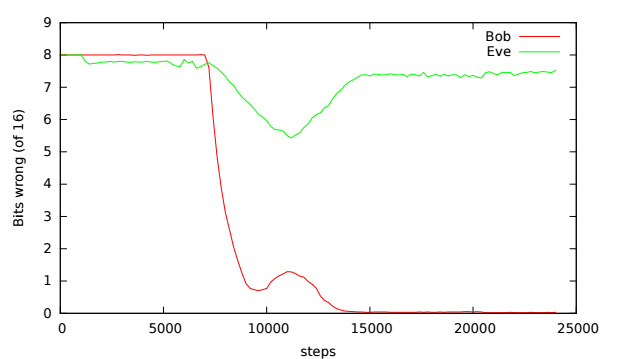
This graph shows the number of errors in deciphering Alice messages by the Bob and Eve neural networks. In the process of learning, Bob made fewer mistakes. Eva also studied, but after each successful attempt the encryption system changed, and Eve could not do anything about it.
The first encryption attempts were not very successful. Bob at first could not do anything with Alice's encrypted messages. But over time, Alice developed a reasonably reliable method that Bob understood. At the same time, Eve could not decipher the message in order to understand what was going on here. Sometimes she managed to uncover the message encryption system of two other neural networks, but after each successful attempt, Eva changed the encryption system.
The authors of the project decided to choose symmetric cryptosystems as the basis for the operation of their neural networks. Symmetric cryptosystems (eng. Symmetric-key algorithm) is an encryption method in which the same cryptographic key is used for encryption and decryption. Symmetric encryption was the only encryption method until the invention of the asymmetric encryption scheme. The algorithm key must be kept secret by both parties. The encryption algorithm is chosen by the parties prior to the exchange of messages.
After the script was played back more than 15 thousand times, Bob learned to convert Alice's ciphertext text into plain text without a single mistake. At the same time, Eva could guess only 8 of the 16 data bits contained in the message. Since each bit is 1 or 0, then, in fact, Eve could guess only purely by chance. Attempt to decrypt the message of Alice Eva, according to researchers, is more like guessing by means of a coin flip. The research results are published here .
We do not understand exactly how this encryption method works, because machine learning has allowed us to get results without demonstrating the way it is developed. In practice, this means that we will not be able to get a human-readable encryption method, if it is rather complicated. The practical application of this technology is thus limited.
“Methods of working with neural networks have begun to evolve at the current level in the last few years, so we are only at the beginning of the journey,” said Joe Sturonas, a cryptographic specialist from PKWARE. So far, a person can easily hack the information protection system developed by neural systems. After some time, it is possible for a machine to learn how to create more reliable data encryption systems, for which a person will have to spend a lot of time hacking if he is able to understand the result of the operation of machines.
 The researchers plan to try to continue to work not only with symmetric data encryption. Perhaps steganography will be involved. Scientists believe that neural networks appear to be not very strong in cryptanalyst, but they can be very effective in analyzing metadata and analyzing traffic transmitted over the network. In addition, the researchers say that neural networks can be effective not only to protect data, but also to attack.
The researchers plan to try to continue to work not only with symmetric data encryption. Perhaps steganography will be involved. Scientists believe that neural networks appear to be not very strong in cryptanalyst, but they can be very effective in analyzing metadata and analyzing traffic transmitted over the network. In addition, the researchers say that neural networks can be effective not only to protect data, but also to attack.Google Brain is a project for working with neural networks that has “split off” from the long-term research department at Google X. Google Brain employees work exclusively with machine learning technologies and neural networks. According to Google management, these technologies can provide vast opportunities for computer systems. Systems based on machine learning are likely to be able to change a lot - from the speed and correctness of making a medical diagnosis to driving a car. As a result, according to representatives of Google Brain, all this can change humanity itself.
Source: https://habr.com/ru/post/398645/
All Articles