Is it difficult to steal a copter? Several already implemented methods of interception control

Quadcopters are now becoming more and more, they are gradually "getting smarter", becoming more functional. Drones of this type already serve not only as entertainment, they help athletes, photographers, scientists and, of course, various kinds of intruders. With the help of copters, unauthorized monitoring of people, industrial and other objects is often conducted.
Some companies began to create protective equipment from drones, allowing to plant the device or to take control over it. It is clear that manufacturers of drones are trying to somehow protect their devices from interception. But this is far from always possible, especially if real experts in their field take charge. The situation is aggravated by the fact that even the most advanced copters install the simplest traffic encryption systems.
The other day there was information that the team of researchers created a system that allows you to take control over almost any drone. And this does not require an electromagnetic gun, the permission of the authorities or something else. It is enough to use a specially modified control panel. Specifically, this type of hacking allows you to take control of any copter with DSMx data transfer protocol. The protocol is used not only for data exchange with copters, it is also used to work with radio-controlled cars, boats, helicopters, etc.
')
The method proposed by specialists allows not only to intercept control, but also to form a “digital fingerprint”, unique for each device. This fingerprint can be used to distinguish "your" device from "alien" and form a list of trusted systems. Thus, the developed technology can be used for the benefit of - for example, use in your organization a list of “your own” drones, the digital imprint of which is entered into the database.
The technology does not involve the use of a jammer blocking the connection of the copter with the control device. Instead, it is practiced a complete interception of control while preserving the functionality of an alien drone. Details were presented this week at the PacSec 2016 conference in Tokyo. Jonathan Adersson, head of Trend Micro's information security research group (a division of TippingPoint DVLab), talked about it.
According to him, the method is not something new. It has been used for some time by some intruders and information security experts, without betraying the way it is widely publicized. At the conference, this method was described for the first time, providing almost a complete technical description of it.
So, to seize control of someone else's drone Anderssen uses a timing attack (timing attack), synchronizing the frequency of the transmitter's emitter with the frequency of the drone's radio module in automatic mode. After that, a malicious packet is sent to the drone, which causes someone else's device to ignore commands from the “native” controller, and start listening to commands from the attacker's controller.
It is clear that now devices like the one that Andersson has shown are not well known to the general public. But an expert in radio engineering can easily create such a device, knowing the peculiarities of the communication protocol of the kopter and the controller. Perhaps after this demonstration, there will be companies and individual craftsmen who will sell controllers to intercept foreign drones. According to experts, there is nothing particularly difficult in this. Vulnerability, which opens the possibility of controlling other people's devices, is found in the systems of almost all radio-controlled devices that support the DSMx protocol.
Of course, this method can be used not only by attackers. Militiamen, having noticed violation from any radio-controlled device, can also use this method to intercept a kopter-intruder. Similarly, owners of any property (houses, plots of land, etc.) can do this, seizing control over the drone or drones that have invaded other people's possessions.
According to Andersson, the situation with the interception of drones now cannot be solved - this vulnerability is relevant for many models of radio-controlled devices. Their manufacturers will not be able to quickly change the protocol or the type of radio-controlled module that is installed in the device. The solution could be the release of such modules, the firmware of which can be updated. But it is expensive and long.
Experts also claim that all modern radio-controlled systems are subject to the time attack demonstrated by Anderssen. To carry out such an attack, you need a little knowledge about the device of radio-controlled devices and protocols that are used to transmit data over a wireless network, as well as electronic components worth about $ 100. The most interesting thing is that the second attacker can use a similar system in order to hack the first one, which, in turn, took control over someone's drone.
Other ways to intercept drones
The way to seize control over other people's drones, shown by Andersson, is interesting. But he is not the only one . Back in 2013, Samy Kamkar was able to learn how to control other people's drones by scanning radio frequencies with the help of his drone, which had a Raspberry Pi and a WiFi transceiver installed on it. The hacking method used is Aircrack-ng .
With the help of this utility, a specialist hacked into a wireless network, and the quadcopters of this network were detected by the peculiarities of their MAC address. As it turned out, copters of this type have the same type of addresses, which distinguish them from all other devices.
After hacking the network, the MAC addresses of WiFi networks in the signal coverage area are blocked by a spy drone, and other people's devices are disconnected from their controllers. After that, the hacker received the opportunity to fully control someone else's copter, and also received an image from their cameras.
A similar method was used by the shellntel information security team. She developed a robust copter control interception scheme. This method exploits the exploitation of the vulnerability in the MAVlink telemetry protocol. Such a protocol usually transmits data in unencrypted form. The copter and the controller recognize each other by a digital identifier. Specialists have assembled a circuit from a miniature computer Raspberry Pi and a radio communication module, using it as a sniffer.
As it turned out, to intercept the control of the drone enough to send one specially formed packet. Initially, you need to intercept the identifier, and then you can control the functions of the device. Experts say that in theory for the copters, working with the MAVLink protocol, you can set the GPS-coordinates, and "fit" all the devices in one place almost automatically.
Another method was proposed by Rahul Sasi. He was able to take control over devices such as the Parrot AR.Drone 2.0 and DJI Phantom. To achieve this goal, he used reverse engineering for the proprietary software AR Drone program.elf. As a result, he was able to successfully use a combination of attacks such as Maldrone and Skyjack. Sasy argues that his method allows not only to manage other people's drones, but also to receive video traffic from their cameras, as in the previous case.
The problem with this method is that at first the drone completely loses control for a few seconds, and starts working only after the software that has been loaded by the attacker is activated. If the drone is high enough, there is no problem. But if the ground is only a few meters away, the device can simply break.
In April of this year, Nils Rodday from IBM showed an almost universal way of hacking the control system of the copter. At the Black Hat Asia conference, he demonstrated how to crack the expensive police drone, which cost tens of thousands of US dollars. But to hack such devices using the electronic system, the cost of which - a few tens of dollars.
The hacking process exploits two vulnerabilities. The first is hacking a wireless Wi-Fi network. Usually, the data received and transmitted by the drone is encrypted, but in most cases the encryption protocol is WEP. It has long been learned to crack in a split second. This is the simplest encryption, which is practically not used anywhere else, but the developers of the drones decided to implement just such a protocol. After hacking and connecting to the attacker's network, they are sent a command to the drone, which disconnects the device from its network. After that, the hacker gets the opportunity to control all the functions of the drone.
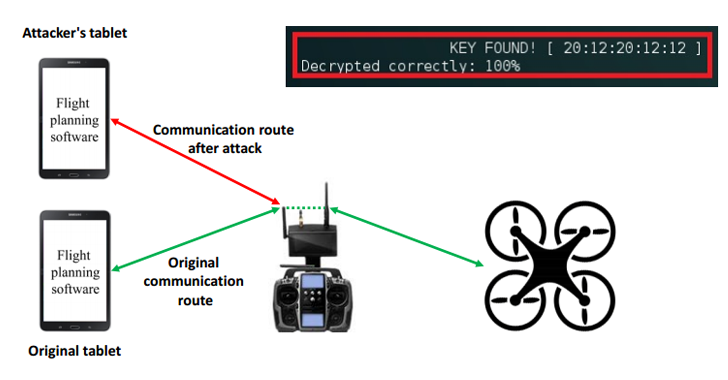
Another type of hacking is used, based on the vulnerability of Xbee chips. They are installed in a large number of different models of radio-controlled devices. Chip data encryption is supported, but in many cases, developers disable it. That is why an attacker can hack a drone with such a chip from a distance of several kilometers.
The only way to protect, according to the author of this method of hacking - the use of data encryption.
Electronic guns
A simpler way to influence the copter is a radio-electronic gun. Batelle has already created several such devices. The most effective can be called a gun DroneDefender. It can be used to create a radio silence zone around the drone. The gun generates a powerful radio signal that interrupts the flow of signals from the operator. In addition, the positioning by GPS or GLONASS is disturbed.

This year, the company also presented a “radio pistol”, which also creates powerful interferences throughout the radio spectrum around the drone. The difference between the gun and DroneDefender is the ability to determine the type of signal that is transmitted by the drone, creating interference only for the radio frequency used.
The gun can even transfer commands, including “home” and “land”. Commands are suitable for a large number of models of drones.
The most unusual way to neutralize the drone, perhaps, is to “hunt” for a kopter using another kopter and network. The "police" copter carries a network that he throws at the copter intruder. In the case of a successful maneuver, the offender can be neutralized.
There is a similar method, only here the copter carries a gun loaded with a net. Once the target is identified, a police copter rises into the air and shoots a net at the intruder. The network is attached to the drone guard with a long and strong thread so that the intruder, entangled in the network, does not fall to the ground and does not break. Collected "harvest" police drone carries to the landing site.
Of course, catching a network of copters is a way of intercepting from the “against scrap there is no reception” area. Taking control using an electronic system is a much more interesting option. As mentioned above, this method is applicable to almost all Copters, now produced by different manufacturers. Solving the problem of burglary and interception of drones is possible only if a reliable encryption system is embedded in the radio module.
The fact that the drones are not yet intercepted in large quantities is only a matter of time. It is probably uninteresting and unprofitable to steal simple devices, and more functional devices are not yet widespread. But as soon as their number reaches a certain limit, you can be sure that massive hijackings will begin. After all, the costs in this case are minimal, and the temptation is great.
Source: https://habr.com/ru/post/398603/
All Articles