Keystrokes can be heard by Skype

Keyboard can listen. In the past, pressing on the usual mechanical "sniffing" waves of Wi-Fi , the virtual touch-keypad of the smartphone - accelerometer . According to a new study by scientists from the University of California at Berkeley, attackers can record acoustic signals during a Skype conversation.
Previously, the attacker had to seriously prepare before the attack. In order to get the necessary information, the hacker had to be close to the target, know exactly the typing style on the keyboard, and much other information about the victim. Today, these conditions can hardly be considered real, and the result - effective. The University of California study explores a new type of attack, called Skype & Type. It can be a serious privacy issue.
')

When connected to Skype, attackers can record the sound of keystrokes. Knowing some of the features of a person’s input style, researchers could determine which keys he pressed with an accuracy of 91.7%. The research team recorded sound using microphones, accelerometers in mobile devices and other sensors. After collecting the audio stream, the data was analyzed using the methods of controlled and uncontrolled machine learning. In the end, they received a user data reconstruction. The researchers note that to conduct an attack, you do not need to install any malware on the computer of the potential victim. You just need to listen to the sound of IP-telephony systems.
“Skype is used by millions of people around the world,” said Gene Tsudik, a professor at the UCI Computer Science Department and one of the authors of the new study. “We showed that during a Skype conversation or a video conference, your keystrokes can be recorded and analyzed by your interlocutors. They can find out what you are entering, including passwords and other very personal things. ”
During a conversation on Skype, we deal in parallel with other things: we send letters, chat messages, take notes. Pressing a key makes a sound that is transmitted to the other side. Many use Skype and other VoIP-applications to talk with relatives, but very often software is used for business meetings, and partners who are “on the other side” cannot always be friends. If the attacker has an idea of how the victim uses the computer, he will not encounter any obstacles in his path. You can build a profile of acoustic radiation generated by each key on the keyboard. For example, the sound that “H” publishes on a MacBook Pro differs from the same key on other manufacturers' laptops. In addition, "H" differs in sound from "J", which is located next to it.
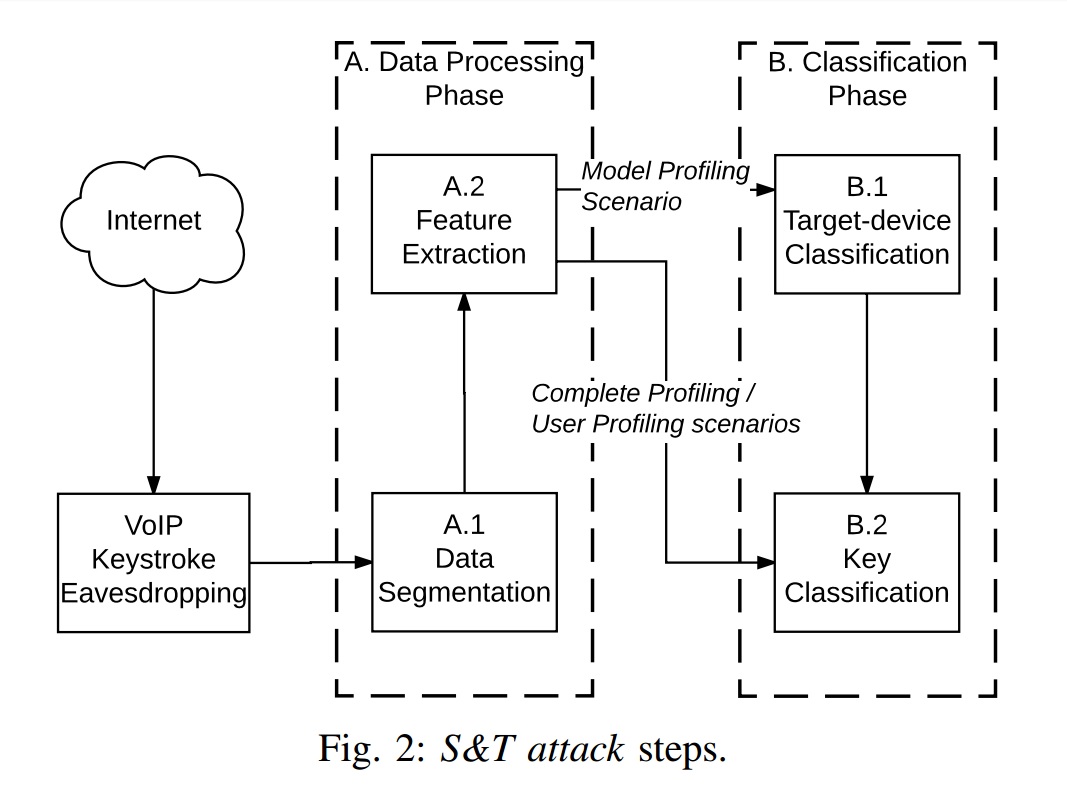
Even without knowing anything about the keyboard or typing style, the attacker has every chance to guess (42%) which key a person presses. Keyboards on touchscreens are also vulnerable to Skype & Type. When a person during a conversation on VoIP dials something on the keyboard, be it a password or any other target text, acoustic radiation from the keyboard is recorded by the microphone and transmitted to the hacker. All his actions can be divided into two phases - data processing and their classification. At the processing stage, data segmentation and feature extraction are performed. In the second phase, the attacker classifies the target devices and the main stages of the attack itself.
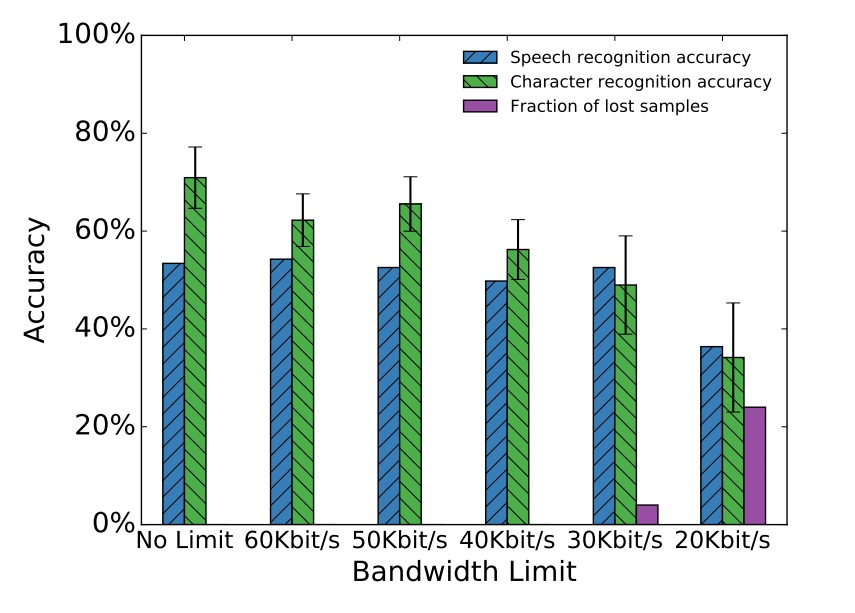
One of the potential uses of an attack could be the entry of a password set on a hacker-proposed site or in an application. Researchers say that their attack method can significantly reduce the amount of effort required by attackers to obtain user data. The victim’s voice will not be disturbed by the victim’s voice while typing the target text and the weak connection bandwidth: Skype & Type is resistant to various VoIP problems, which confirms the expediency of the attack.
A possible defense against a new type of attack may be the so-called ducking effect , which is widely used to create electronic music. In this case, the user needs to reduce the microphone volume and block the sound of keystrokes with some other sound. The problem with this method is that along with the volume of the audio signal of the keys, the sound of the voice is muffled. “Effective countermeasures should be less intrusive and, if possible, drown out only the sound of the keys, without interfering with the conversation,” the article says.
The history of eavesdropping physical signals dates back to 1943, when it was discovered that an oscilloscope can extract from the electromagnetic radiation of Bell Telephone 131-B2, which was used by the US Army to encrypt communication, plain text. The common goal of all physical attacks are peripheral input devices, such as keyboards and touch screens. Previously, hackers have already used electromagnetic and acoustic keyboards for their own purposes, as well as video, where users enter confidential data on a keyboard or touch screen.
The question of eavesdropping user input on the keyboard is quite a popular area of research. Studies of the acoustic signals of the keyboard originate from the moment when Dmitry Asonov and Rakesh Agraval announced the exposure of the keyboard of telephones, computers and ATMs to acoustic cryptanalysis. They showed that by teaching a neural network on a specific keyboard, it achieved great success in eavesdropping input on the same keyboard or keyboards of the same model. They also investigated why this is possible and found that the plate under the keyboard, on which the sensors are located, behaves like a drum when you press a key. This feature allows you to distinguish the sounds of individual keys.
Source: https://habr.com/ru/post/398545/
All Articles