US Secret Service warns about periscope skimmers
The other day , the US Secret Service has published on the network information about a new type of skimmer, which received the name "periscope skimmers." Accordingly, the process of data theft by such devices is called periscope skimming. These devices are connected directly to an ATM card to steal credit card data. Among other duties of the Secret Service is the investigation of various types of financial fraud and identity theft.
Such systems were first discovered on August 19, 2016 in Connecticut, USA. The second time a skimmer of a new type was found at an ATM installed in one of the settlements of Pennsylvania, USA (September 3 of this year). According to experts who have studied such "periscopes", the devices can be inside the system for about two weeks. The memory capacity of the device allows the skimmer to remember the data of 32,000 credit cards.
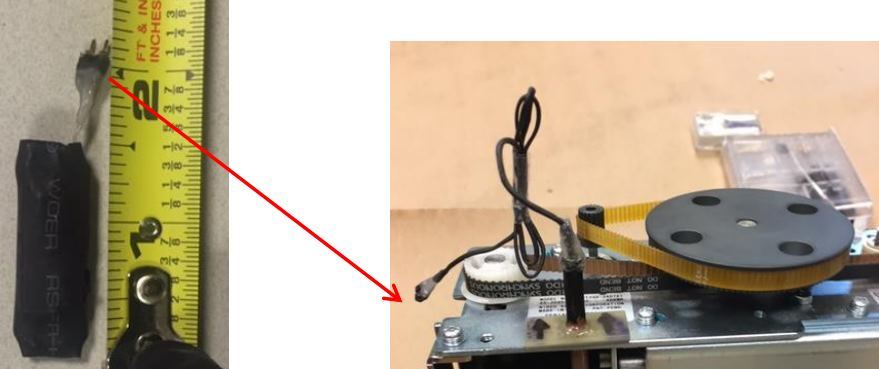
Apparently, intruders who install such skimmers have a key that allows access to the ATM electronics. Having opened the system, hackers install two devices inside, connected together by wires. The first model is installed in the case of the card reader, near the receiving slot.
')
Scammers connect certain skimmer contacts to the ATM card, which is responsible for transferring credit card data readable with magnetic tape. The module is fixed with glue. The only visible part of the skimmer is the wires that connect the first module to the second. The second module is a control system that houses the battery, data storage and control electronics. Data storage looks like a small hard drive.

Technologies that are used by attackers to steal credit card data of ATM users are becoming more sophisticated. A new type of skimmer is probably a way to avoid detecting such devices using anti-skimmer technologies that also do not stand still. The fact is that in a number of countries bank employees and police began to use reliable skimmer detection systems. They work with almost 100% accuracy, in case the skimmer is installed outside the ATM.
Another interesting point is that in the “periscope skimmers” there is no camera that could read the data of the cards of banks' customers. Based on this, information security experts conclude that "periscopes" are only a prototype, a test preliminary sample of a real device. Perhaps the scammers are not going to use the cameras, but are planning to install an invoice keyboard that completely repeats the original. But this is only an assumption. As before, the security guards advised to close the credit card data by hand

Unfortunately, this method, firstly, does not always help. Secondly, it is used by a very limited number of ATM users.
According to some experts, the only reliable way to reduce the activity of ATM hackers is to remove the magnetic tape from the card. It is still the most vulnerable element of the credit card. But in the near future this is unlikely to happen, since it is the magnetic tape that allows, for example, to make sure that the user has inserted the credit card correctly. In addition, a magnetic tape on a credit card is a modern standard. If you start to change something, then banks and their servicing organizations will have to spend considerable money on redeveloping ATMs and changing cards.
Scammers do not need to use a key to access the insides of ATMs. There are many other ways that criminals resort to. For example, since 2013, it is known about installing skimmers on portable terminals in stores and other points of sale of goods and services. All this is done very quickly, and the installation of the overlay panel takes seconds.
This is what the overlay panel and the original terminal panel look like.
Some criminals do not work with skimmers, preferring to install malicious software on ATMs with the help of special devices. This is not a very common way to hack ATMs, but a number of criminals are still using it. Protection of software platforms for ATMs is not 100% reliable, and often banks use ATMs with old software shells, where there are many vulnerabilities .

In order to remain undetected, fraudsters use miniature devices. They can stay on ATMs for a long time. This is especially true for systems that are installed in remote regions, where control is not carried out too carefully.

Some scammers use brute force to install skimmers inside the ATM, not outside. Here is a simple example of such a case:

And to detect a skimmer installed in the hole on the body of the ATM is much more difficult than seeing a third-party device outside. Not all ATMs are equipped with systems that report attempts at physical hacking, and the method has not yet been completely eliminated.
Another original way to install a skimmer is to work with the bank door. Instead of trying to attach a skimmer to the ATM itself, the criminals place it at the door , closing access to the room with the ATMs. These doors can be opened with a card outside the bank hours. The fraudsters install a skimmer on the door, and when opening the door, it reads the necessary information from the magnetic strip. A video camera that removes a set of pin-code, as usually located in the area of the ATM.
Some fraudsters use the consequences of the careless employees of the bank, who leave the communication nodes of their networks available to almost anyone. This happens quite often with external ATMs and terminals that are installed by the bank at airports, shops, train stations and other places.

Scammers just need to figure out which item is available and what can be done with it. For professionals, all this is just a children's task.
So far, the safest ATMs are those that are built into the walls of banks by banks. In this case, fraudsters can only access the external panel of the device, and there are already fewer options than in the case of other types of ATM.
Source: https://habr.com/ru/post/397423/
All Articles