NSA has exploited Cisco PIX firewall vulnerabilities for over a decade

Cisco's PIX firewall protection for years seemed as reliable as a brick wall. But no
An information security team has published a note that a vulnerability in Cisco's PIX line firewalls allowed the NSA to remotely retrieve encrypted keys in clear text for ten years. The results of the work carried out by researchers are of great importance, since the PIX-systems, presented by Cisco in 2002, were supported until 2009. A large number of organizations used these systems after this date, as the company decided to provide limited support for the PIX firewall lineup for four years, up to 2013. Many companies, organizations and individuals work with PIX firewalls even now.
As it turned out, all these years, users of PIX systems have been vulnerable to attacks from cybercriminals and cyber spies. The danger remains relevant now. The results of the investigation of information security experts helped explain the publication of Edward Snowden in Der Spiegel . This publication stated that NSA employees were able to decipher the traffic of thousands of VPN connections per hour.
“This means that the NSA had the opportunity to extract private keys from a Cisco VPN for ten years,” said Mustafa Al-Bassam, one of the representatives of the investigation team of experts. "And now it’s clear how they could decrypt the traffic of thousands of VPN connections, as indicated in the publication Der Spiegel ."
')
Using the search service Shodan, you can make sure that even now more than 15,000 networks of various sizes all over the world work with PIX. Among the countries for which the NSA has established a very close observation, includes Russia, USA, Australia. For PIX systems, versions 5.3 (9) to 6.3 (4) are vulnerable. In addition, the specialists managed to exploit a similar vulnerability in version 6.3 (5).
Cisco, in turn, said that indeed, PIX versions 6.x and lower are vulnerable. Version 7.0 and higher are safe.
Experts from BenignCertain were able to exploit a vulnerability in the Internet Key Exchange version from Cisco. This is a protocol where digital certificates are used to establish a secure connection between two parties. During an attack on a vulnerable PIX device, specially formed data packets are sent. The parser, which is part of the exploit, extracts the key from the VPN traffic, if necessary, an attacker can get other data. The tool that was used by the NSA allowed any user connected to the global network to exploit the vulnerability in the PIX. No special preparatory work is required to exploit the vulnerability. Information security experts have published a screenshot of the progress of the attack:
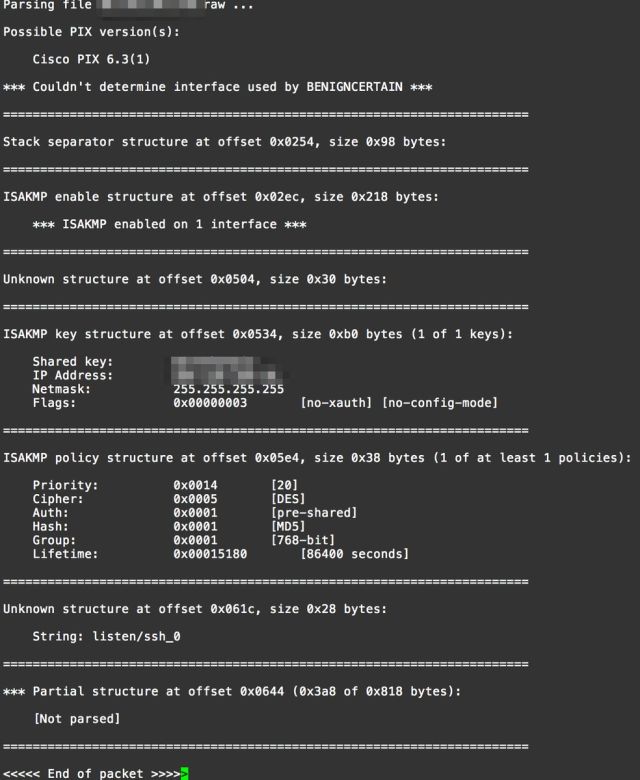
Interestingly, the Adaptive Security Appliance, which replaced the PIX, contained a similar vulnerability in the Internet Key Exchange, which Cisco fixed just three months ago. Moreover, as long as the vulnerability was active, the firewalls of more than a dozen other providers also remained vulnerable. It may well be that the problem is relevant not only for PIX, but also for products from other manufacturers.
The private key extraction exploit becomes an even more powerful tool for intruders when combining it with the Equation Group tools. For example, the FalseMorel tool allows you to gain control over the PIX-system with administrator rights. BenignCertain tool allows attackers to know if any firewall is vulnerable to FalseMorel.
A few days earlier, the ShadowBrokers group managed to obtain a number of NSA tools that were used by the staff of the Equation Group (Five Eyes / Tilded Team) for conducting cyber espionage. A number of exploits are aimed at bypassing the firewalls of Cisco PIX & ASA devices, Juniper Netscreen, Fortigate, and others.

Immediately, several cyber security expert groups stated that the leak was indeed related to the Equation Group, and all the software that the hackers of the NSA servers had acquired was authentic. The documents previously submitted by Evard Snowden contained instructions for NSA operators. The manual said that the operator must use the 16-character data string "ace02468bdf13579" to track one of the cyber attack tools. And this line is contained in a leak from ShadowBrokers, in software called SECONDDATE. Exactly this name was given in the documents of Snowden.
SECONDDATE has an important role to play in the global cyber espionage system built by the US agencies. With this system, millions of PCs around the world have been infected.
Source: https://habr.com/ru/post/397021/
All Articles