Vulnerability in WPAD allows access to data protected with HTTPS and VPN
Researchers recommend urgently disable the WPAD protocol on Windows
 Web Proxy Auto-Discovery Protocol (WPAD) is an automatic proxy configuration protocol that is used by clients (browser) to locate (URL) the location of the configuration file using DHCP and / or DNS technologies. When making a request, the browser calls the FindProxyForURL function from the PAC file, where the URL and the host are passed to. The expected answer is a list of proxies through which access to this address will be made.
Web Proxy Auto-Discovery Protocol (WPAD) is an automatic proxy configuration protocol that is used by clients (browser) to locate (URL) the location of the configuration file using DHCP and / or DNS technologies. When making a request, the browser calls the FindProxyForURL function from the PAC file, where the URL and the host are passed to. The expected answer is a list of proxies through which access to this address will be made.WPAD is enabled by default in Windows and is supported by other operating systems. But this protocol is subject to a number of vulnerabilities, as shown by information security experts Alex Chapman (Alex Chapman) and Paul Stone (Paul Stone) at Defcon. Malefactors, using these vulnerabilities, can obtain data of the victim (search history, access to accounts, photos, documents, etc.), despite HTTPS or VPS connections. The type of attack that is used in this case is man-in-the-middle.
You can locate the configuration PAC file using Dynamic Host Configuration Protocol (DHCP), Domain Name System (DNS), or Link-Local Multicast Name Resolution (LLMNR). Cybercriminals can optionally exploit a WPAD vulnerability by specifying the location of a specially configured PAC file that will send a browser request through proxy servers that are under the control of intruders. This can be achieved in an open wireless network by compromising a router or access point, or by opening to everyone who wants access to their own access point, configured properly.
It is not necessary to compromise the attacked PC's own network, since the system will use WPAD to detect a proxy if it is connected via an open wireless network. At the same time, WPAD is also used in the corporate environment; this option is enabled by default on all Windows PCs, as mentioned above.
')
Own proxy server allows attackers to intercept and modify unencrypted HTTP traffic. This does not give too much to cybercriminals, since most sites now work on HTTPS (HTTP Secure). But, since PAC files provide the ability to set different proxy addresses for specific web addresses, and for these addresses you can force the DNS lookup, hackers-beloshlyapniki created a script that allows you to receive all HTTPS protected URLs on your own server.
The full HTTPS URL must be hidden because it contains authentication tokens and other private information. But an attacker can recover the address. For example, example.com/login?authtoken=ABC1234 can be restored by using the DNS query https.example.com.login.authtoken.ABC1234.leak and restored on the cybercriminary server.
Using this method, an attacker can get a list of victim search queries or see which articles of a particular resource the victim is currently reading. This is not too good in terms of information security, but it seems not too dangerous. True, the trouble of the victim does not end there.
The researchers have developed another type of attack that can be used to redirect the user of an open wireless access point to the fake access point page. Many wireless networks collect user data using special pages. After entering their data, the user gets access to the Internet (often this scheme is used by wireless providers at airports).
A page formed by hackers loads Facebook or Google familiar to the user in the background, and then performs 302 HTTP redirect to other URLs, provided the user is authenticated. If the user is already logged in to his account, and most people do not log out of their accounts on various resources, working from their PC or laptop, then the fraudster can obtain the identification data of the victim.

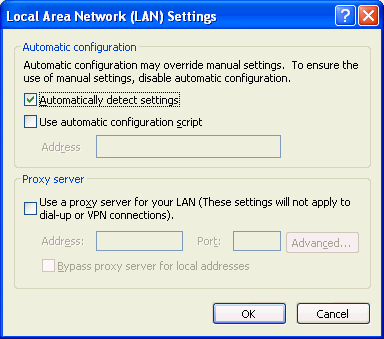
On Windows, WPAD is activated when the "Automatically detect settings" option is enabled. This option is enabled by default.
This applies to accounts on a variety of resources, and through direct links, an attacker can gain access to personal photos of the victim, as well as other data. Attackers can steal tokens for the popular OAuth protocol, which allows you to log in to various sites using your Facebook, Google or Twitter account information.
The possibilities of the new method specialists showed on Defcon. Using their technology, the experts got access to the victim's photo, history of coordinates, calendar reminders and Google account profile data, as well as access to all of the victim's documents on Google Drive. It is worth emphasizing that the attack does not affect HTTPS encryption, the data is still protected. But if WPAD is enabled in the OS, then HTTPS is already much less effective in protecting the user's private data. And it also concerns the information of those users who work with VPN. WPAD allows you to access this data.
The fact of the matter is that popular VPN clients, like OpenVPN, do not clear the network settings specified by WPAD. This means that if an attacker has already managed to establish his proxy settings on the victim's PC, before a VPN connection has been established on this PC, then the traffic will also go through the attacker's proxy server. This opens up the possibility of obtaining all the data mentioned above.
Most operating systems and browsers work with WPAD, and are vulnerable to this type of attack. The experts who discovered the problem reported it to the developers of various vulnerable software products. Patches released for OS X, iOS, Apple TV, Android, Google Chrome. Microsoft and Mozilla are still working on fixing the problem.
How to protect yourself?
The easiest way is to disable WPAD. If you need PAC files to work with, disable WPAD and configure URL exceptions yourself.
Chapman and Stone are not the only information security experts who have noticed the vulnerability of the WPAD protocol. A few days earlier, a similar type of attack was demonstrated at the Black Hat conference. And in May, a joint team of specialists from Verisign and the University of Michigan told that tens of millions of WPAD requests go online every day when users' laptops disconnect from corporate networks. These machines give requests for internal WPAD domains with extensions such as .global, .ads, .group, .network, .dev, .office, .prod, .hsbc, .win, .world, .wan, .sap, and .site .
The problem is that such domain zones already exist in the global network, and if desired, an attacker can register domains for which requests are received from corporate machines that are disconnected from the enterprise network. And this, in turn, allows attackers to “feed” self-configured PAC-files to machines that are disconnected from corporate networks, but which give WPAD requests to discover the global network addresses mentioned above.
Source: https://habr.com/ru/post/396719/
All Articles