Telegram authorization SMS codes continue to intercept
 About three months ago, Pavel Durov warned users that SMS authorization in the Telegram messenger was compromised. “Apparently, the security services of the Russian Federation decided to put pressure on communication operators so that they began to intercept the authorization SMS-code. Usually this is found only within the framework of the cannibalistic regimes that do not care about their reputation - Central Asia, and sometimes the Middle East. But suddenly it happened in Russia (if, of course, to cut off corruption inside the MTS), ”said Pavel Durov and promised to send a mailing to all users with the advice to include two-factor authorization, since Russian telecom operators as a verifier are unreliable.
About three months ago, Pavel Durov warned users that SMS authorization in the Telegram messenger was compromised. “Apparently, the security services of the Russian Federation decided to put pressure on communication operators so that they began to intercept the authorization SMS-code. Usually this is found only within the framework of the cannibalistic regimes that do not care about their reputation - Central Asia, and sometimes the Middle East. But suddenly it happened in Russia (if, of course, to cut off corruption inside the MTS), ”said Pavel Durov and promised to send a mailing to all users with the advice to include two-factor authorization, since Russian telecom operators as a verifier are unreliable.Unfortunately, even two-factor authorization is not a panacea. Yesterday, one of the Telegram users, Sergey Parkhomenko , described in detail how the attackers managed to destroy his account, on which two-factor authentication was enabled .
The essence of the events in brief:
One by one, codes for access to the account, which I did not request, suddenly fell on the phone. Then, when I tried to log in to my account, I was offered to do it as if it was the first time. In the opened interface it was found that the entire history of correspondence, all chats, all contacts disappeared. The account was new, as it were, pristine clean.
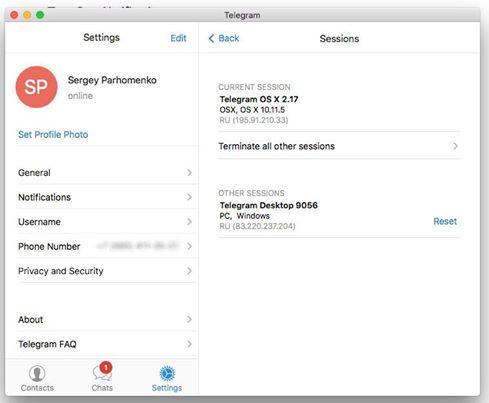
Among the open sessions, one was discovered - made from a foreign computer (I do not have a single PC).
')
In short, this means that the hackers failed to hack an account and divert the correspondence, but it was possible to destroy it. I had to bang it and open a new one again, already consciously, after going through the procedure of deleting and setting up an account, for reliability.
Below is a screenshot with a record of the "left" open session - for those who like to delve into IP addresses. Hello to the owner of this address. Hopefully one day you will all be judged.
After talking with Telegram technical support, Sergey Parkhomenko today managed to find out some details about hacking his Telegram account.
Firstly, the attackers did gain access to the victim’s SMS via the MTS provider.
They could not crack the account, because they did not know the password. But in the Telegram, there is a security vulnerability that allows you to delete an account and open a new one only by SMS, which the attackers did (possibly out of malice).
Telegram representatives have assured that they will close the vulnerability in the coming days.
Unfortunately, due to the high security level of Telegram, it is impossible to recover data in a deleted account.
It is rather strange that last time, and this time, hacking of accounts with interception of authorization codes by SMS was carried out using the same mobile operator. “Everyone has already learned: MTS merges the correspondence of subscribers to special services in the normal mode,” says Anton Nosik. - A specialist from the FSB is just sitting there, who does not need court decisions or prosecutors ’sanctions to read other people's messages. He monitors SMS correspondence, sometimes intercepts number management, sometimes simply merges messages in the media for publication , - It is clear that, in theory, in terms of vulnerability and controllability of special services, all Russian operators are in principle equally vulnerable. But it is also clear that the risks of users of Beeline and MegaFon are theoretical, and special services today receive and study the correspondence of MTS subscribers before studying the final recipients. ”

Fragment of Maxim Katz's SMS-correspondence, which the attackers have fully posted on the Internet
Source: https://habr.com/ru/post/396367/
All Articles