Another extortioner added to the collection of malware from the creators of Petya and Mischa - Trojan-Ransom.Win32.Satan (“Satana”)
As we remember, in May 2016, the attackers for the first time distributed the extortionist Petya , the method for decrypting which was described in detail on GeekTimes. The ways to solve the problem proposed by the experts turned out to be quite effective, which prompted the authors of the malware to create a better version of the Malvar strain under the pseudonym Misha , which operates according to the classical scheme and encrypts the data using the AES algorithm.
Recently, Kaspersky Lab experts came to the conclusion that the ideas underlying the creation of the first two malicious programs were further developed in the new creation of hackers - an extortionist named Satana.

Having access to the PC, Satana encrypts files with .bak, .doc, .jpg, .jpe, .txt, .tex, .dbf, .db, .xls, .cry, .xml, .vsd, .pdf, .csv extensions .bmp, .tif, .1cd, .tax, .gif, .gbr, .png, .mdb, .mdf, .sdf, .dwg, .dxf, .dgn, .stl, .gho, .v2i,. 3ds, .ma, .ppt, .acc, .vpd, .odt, .ods, .rar, .zip, .7z, .cpp, .pas, .asm, and then replace the Windows Master Boot Record (MBR) with their own version (unlike the similarly acting Petya, which encrypts the Master File Table), thereby depriving the user of the ability to boot the OS. In fact, Satana is a symbiosis of the classic extortionist and the mechanisms of work used in the already familiar Petya.
')
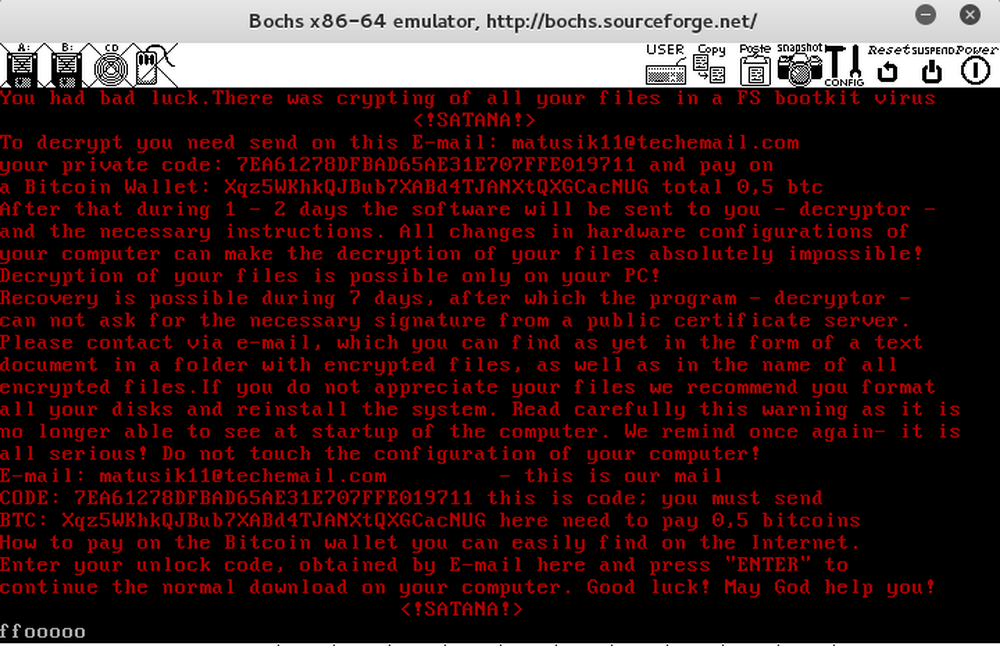
In the best traditions of cyber fraudsters, when they try to turn on an infected computer, the victim will see not the usual operating system window, but a message requesting a ransom.
The key to decrypt computer files will cost the victim a bitcoin equivalent of about $ 350. The email address at which the attackers suggest to contact to discuss payment details Satana adds to the top of the file names: "email address ____ filename.extension".

When you try to turn on an infected computer, the victim sees not the usual operating system window, but a message requesting a ransom. If the victim pays the ransom, the cybercriminals promise to return access, removing the stub code from the MBR, decrypt the contents of what was stored there before, and return the contents to the site.
The authors of the blog The Windows Club posted on the resource pages detailed instructions for "repairing" the MBR through the OS recovery function in Windows. However, only experienced users who are able to work with the Windows command line and the bootrec.exe utility will be able to implement it, while an average user can be so inconvenient to solve the problem in this way.
The Malwarebytes researcher, known under the pseudonym hasherezade, reports that he seems to have found a way to decrypt and restore the original MBR, but this does not save the rest of the data. The malware uses a sufficiently powerful encryption algorithm, which has not yet been cracked. Nevertheless, the researchers of the problem still do not recommend paying the ransom to attackers:
“Even if the victim pays a ransom, but she or the attacker's managing server were offline at the time of the encryption, the payment will not solve the problem,” comments the hasherezade. The expert believes that the encryption key is stored only on the attackers server. And although encryption can be performed without an internet connection, the key will be lost in this case.
Also in the Malwarebytes report it is emphasized that Satana, as follows from the preliminary analysis of the code, is under active testing and refinement, since the malware code is replete with bugs. So the experts noted an error in the operation of the Bitcoin wallets generator. At the same time, a preliminary analysis of the malware led experts to conclude that Satana will continue to evolve, and we will hear about this encrypter more than once.
According to laboratory specialists, Kaspersky Internet Security identifies Satana as Trojan-Ransom.Win32.Satan and blocks attempts to encrypt content and block the system.
Detailed analysis of the malware on the blog pages Malwarebytes
Kaspersky Lab blog
That's all with you was Dronk.Ru. Do not forget to return money for purchases in China and subscribe to our blog , there will be many more interesting things.
We recommend:
- Save up to 8% on every purchase on AliExpress and other online stores in China
- Why do online stores give money for purchases?
- Return your money - Choose a cashback service for Aliexpress
- The history of the development of Dronk.ru - from choosing quadcopters to returning money for purchases on AliExpress and not only
- The best cashback service or 5 main criteria for evaluating cashback service
Recently, Kaspersky Lab experts came to the conclusion that the ideas underlying the creation of the first two malicious programs were further developed in the new creation of hackers - an extortionist named Satana.

Having access to the PC, Satana encrypts files with .bak, .doc, .jpg, .jpe, .txt, .tex, .dbf, .db, .xls, .cry, .xml, .vsd, .pdf, .csv extensions .bmp, .tif, .1cd, .tax, .gif, .gbr, .png, .mdb, .mdf, .sdf, .dwg, .dxf, .dgn, .stl, .gho, .v2i,. 3ds, .ma, .ppt, .acc, .vpd, .odt, .ods, .rar, .zip, .7z, .cpp, .pas, .asm, and then replace the Windows Master Boot Record (MBR) with their own version (unlike the similarly acting Petya, which encrypts the Master File Table), thereby depriving the user of the ability to boot the OS. In fact, Satana is a symbiosis of the classic extortionist and the mechanisms of work used in the already familiar Petya.
')
In the best traditions of cyber fraudsters, when they try to turn on an infected computer, the victim will see not the usual operating system window, but a message requesting a ransom.
The key to decrypt computer files will cost the victim a bitcoin equivalent of about $ 350. The email address at which the attackers suggest to contact to discuss payment details Satana adds to the top of the file names: "email address ____ filename.extension".

When you try to turn on an infected computer, the victim sees not the usual operating system window, but a message requesting a ransom. If the victim pays the ransom, the cybercriminals promise to return access, removing the stub code from the MBR, decrypt the contents of what was stored there before, and return the contents to the site.

The authors of the blog The Windows Club posted on the resource pages detailed instructions for "repairing" the MBR through the OS recovery function in Windows. However, only experienced users who are able to work with the Windows command line and the bootrec.exe utility will be able to implement it, while an average user can be so inconvenient to solve the problem in this way.
The Malwarebytes researcher, known under the pseudonym hasherezade, reports that he seems to have found a way to decrypt and restore the original MBR, but this does not save the rest of the data. The malware uses a sufficiently powerful encryption algorithm, which has not yet been cracked. Nevertheless, the researchers of the problem still do not recommend paying the ransom to attackers:
“Even if the victim pays a ransom, but she or the attacker's managing server were offline at the time of the encryption, the payment will not solve the problem,” comments the hasherezade. The expert believes that the encryption key is stored only on the attackers server. And although encryption can be performed without an internet connection, the key will be lost in this case.
Also in the Malwarebytes report it is emphasized that Satana, as follows from the preliminary analysis of the code, is under active testing and refinement, since the malware code is replete with bugs. So the experts noted an error in the operation of the Bitcoin wallets generator. At the same time, a preliminary analysis of the malware led experts to conclude that Satana will continue to evolve, and we will hear about this encrypter more than once.
According to laboratory specialists, Kaspersky Internet Security identifies Satana as Trojan-Ransom.Win32.Satan and blocks attempts to encrypt content and block the system.
Detailed analysis of the malware on the blog pages Malwarebytes
Kaspersky Lab blog
That's all with you was Dronk.Ru. Do not forget to return money for purchases in China and subscribe to our blog , there will be many more interesting things.
We recommend:
- Save up to 8% on every purchase on AliExpress and other online stores in China
- Why do online stores give money for purchases?
- Return your money - Choose a cashback service for Aliexpress
- The history of the development of Dronk.ru - from choosing quadcopters to returning money for purchases on AliExpress and not only
- The best cashback service or 5 main criteria for evaluating cashback service
Source: https://habr.com/ru/post/396213/
All Articles