How much information can be transmitted through the CPU fan
15 bits per minute

Removal of information from an isolated computer that is not connected to the network (air-gapped) is a difficult but interesting task. Over the past ten years, several methods have been developed for such data exfiltration: for example, recording electromagnetic radiation from a video card and various components on the motherboard [1] , [2] [3] , [4] , recognition of keystrokes by sound, shooting information on the optical [5] and thermal [6] channels, audio transmission through speakers in audible and inaudible frequency ranges [7] , [8] [9] , radio transmission from monitor to AM radio receiver [10] and others.
But it never occurred to anyone to transmit the flow of information by changing the speed of the fan . But this seems like a trivial idea.
')
A malicious software system called Fansmitter was developed by Andrei Daidakulov, Iosef Solevich, Yuval Elovichi and Mordechai Guri from the Research Center for Computer Security at Ben Gurion University .
Removing information through a computer fan has one main advantage - there is such a fan in every desktop computer. True, it is absent in some modern notebook models, but such gadgets are still rare at nuclear facilities and other protected facilities in Russia and abroad. There are usually installed the most simple and reliable personal computers with a standard system unit.
Thus, the Fansmitter malware will work on virtually any PC, even if it does not have speakers and a microphone (audio-gap). In addition, the sound system can be turned off at the BIOS level to prevent accidental or intentional connection of external speakers to the audio jack. Turning off the audio system is very effective against conventional acoustic data exfiltration. But not against the Fansmitter. In this case, acoustic exfiltration does not involve the computer’s sound subsystem.
Signal transmission occurs through a change in the rotational speed of the fans on the processor. With a change in the speed of rotation, the sound characteristics also change. Information is recorded by a remote microphone at a distance of several meters, for example, a regular telephone.

If we classify various methods of exfiltration of data from an isolated computer, then Fansmitter is the fifth class of such methods, along with electromagnetic radiation, optical pickup (on LEDs), thermal and acoustic.
For a successful attack, Fansmitter needs to infect the victim’s computer and mobile phone directly. If there are no problems with the phone, then installing a malicious program on an isolated PC is the most difficult part of a hypothetical attack. Of course, the researchers do not pay attention to practical methods of installing malware on an isolated PC, but only talk about the technical part of the task, that is, directly about the methods of encoding digital data decoding through fan noise.
On modern computers, the CPU and system unit fans are usually controlled via a four-pin cable. The purpose of each contact is shown in the table.
| Contact | Designation | Function |
|---|---|---|
| 1 (red) | GROUND | Land |
| 2 (black) | 12 v | Power 12 volts |
| 3 (black) | FAN_TACH | Outgoing fan speed signal |
| 4 (yellow) | FAN_CONTROL | Input signal to indicate fan speed |
As you can see, the third cable constantly transmits a signal to the motherboard about the fan speed. The fourth cable transmits instructions to change the rotation speed using the pulse-width modulation signal (PWM) [11] . In older computers, the fourth cable is missing and the fan speed is not adjustable.
Changing the fan speed is carried out automatically or manually. In the latter case, this is done through the BIOS or by means of the operating system. There are several proprietary and open source programs for controlling and measuring the fan speed on various motherboards for Windows, Linux and macOS [12] [13] [14] .
It is known that with increasing fan speed increases its volume (acoustic noise). The diagram shows the graph of the perceived volume of the processor fan when the rotational speed changes from 1000 to 4500 RPM and back, from a distance of 1 meter (top) and 4 meters (bottom). In both cases, the sound is recorded by a mobile phone microphone.
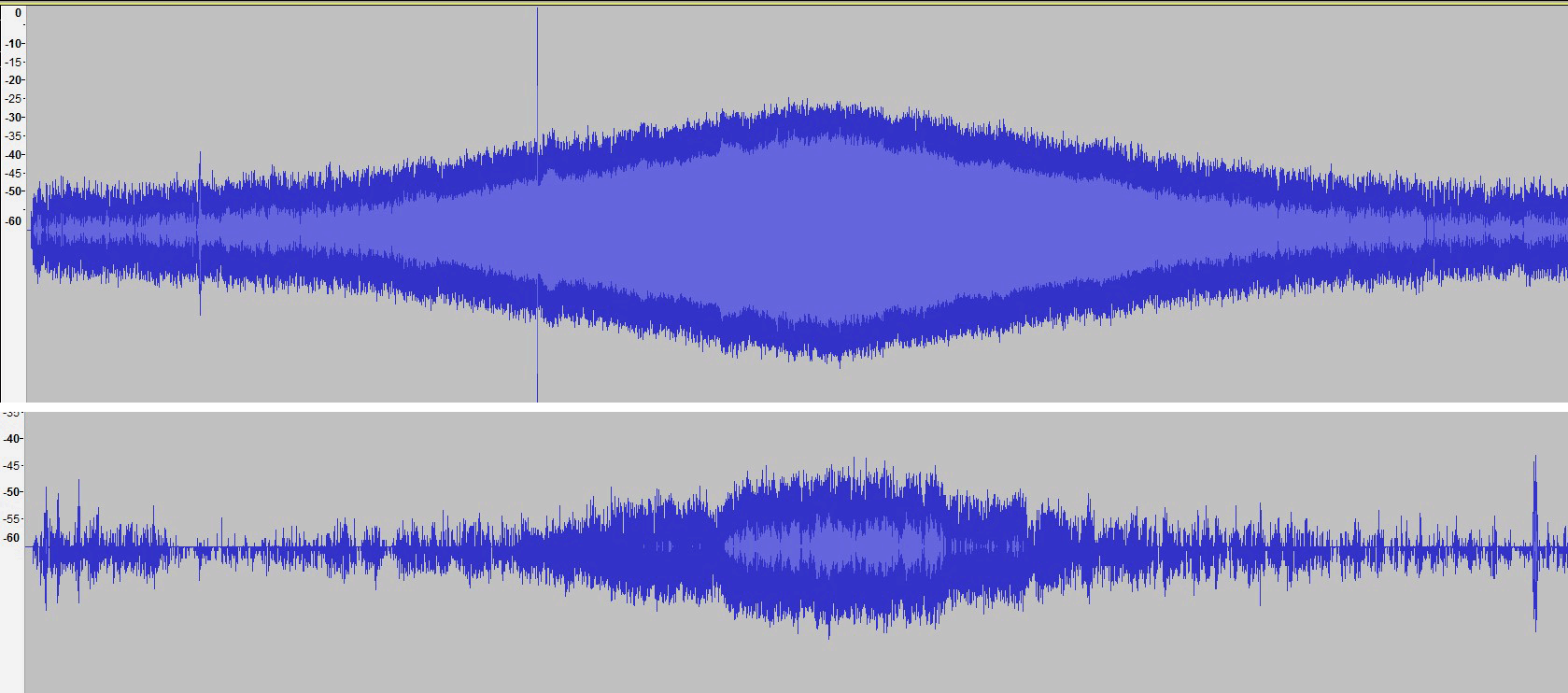
The volume may vary for different fan models, but the basic trend remains the same: the faster the fan rotates, the greater the noise.
In addition, with a change in the rotational speed, the pitch also changes - Blade pass frequency (BPF).
BPF (in Hertz) is measured by multiplying the number of blades ( n ) by the rotation speed R in revolutions per minute (RPM), so that
BPF = n * R / 60
The graph shows a typical fan noise spectrum of about 1000 RPM.
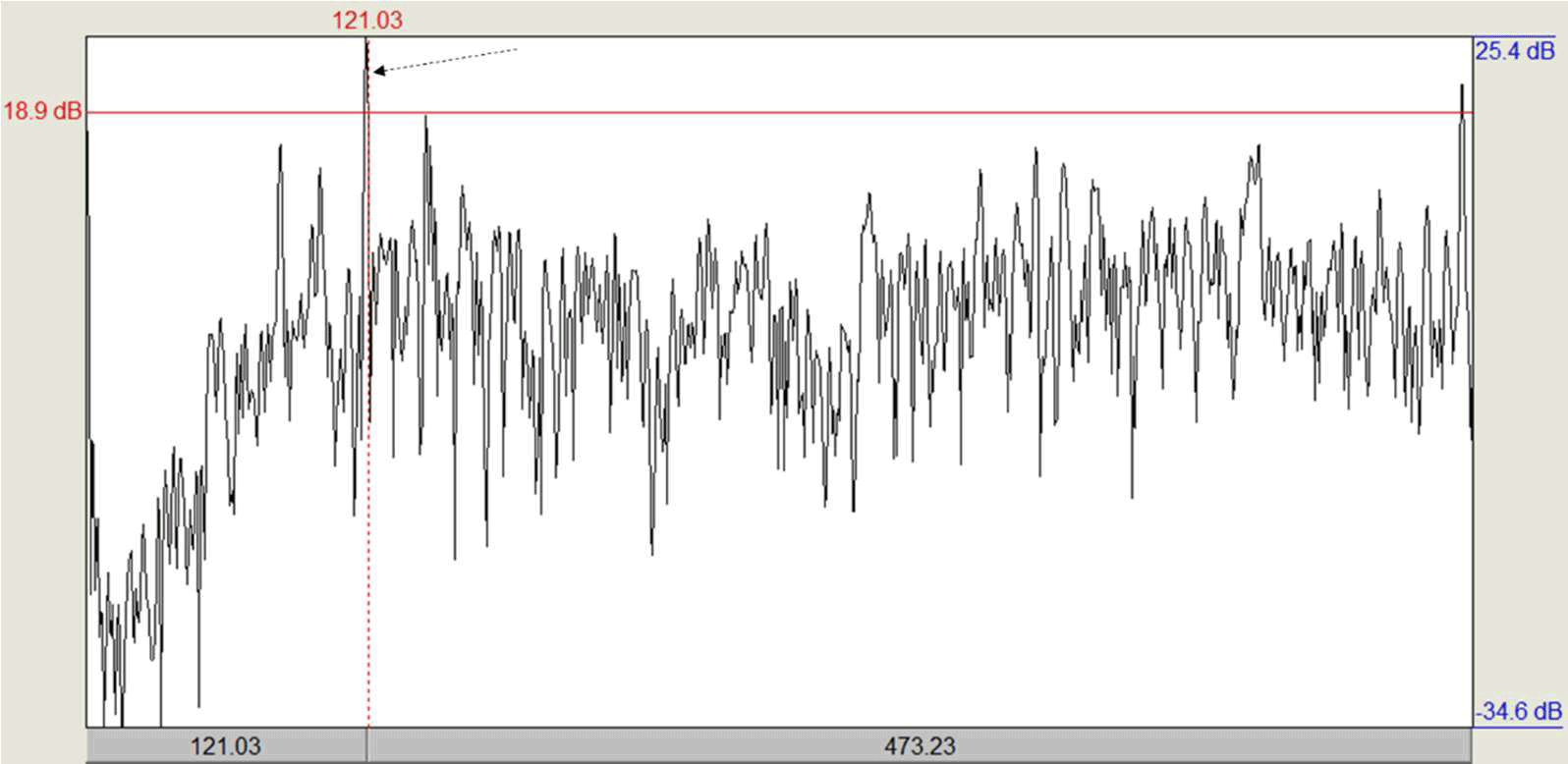
To analyze the audio signal, the sampling rate for simplicity was reduced from 44.1 kHz to 2 kHz and the signal was filtered in the necessary BPF bands. Thus, it turned out to make a table of which rotational speed corresponds to which BPF, for example, for a seven blade fan (in the table).
| R (RPM) | BPF (Hz) |
|---|---|
| 1000-1600 | 116-187 |
| 1600-3000 | 187-350 |
| 2000-2500 | 233-292 |
| 4000-4500 | 466-525 |
Unfortunately, frequencies in areas of 100-600 Hz are distinguishable by the human ear, so that the victim of an attack can catch the change in frequency by ear. The authors of the scientific work recommend using several methods to conceal an attack: 1) to conduct it at a time when the probability of the presence of a person is minimal; 2) use the lowest possible frequency of 140-170 Hz; 3) use close frequency ranges, with a difference of no more than 100 Hz between 0 and 1.
To modulate the signal, the researchers used two methods: amplitude modulation (Amplitude Shift Keying, ASK) and frequency modulation Frequency Shift Keying (FSK). The first method is more versatile and fits almost all fans, while the second method is more resistant to ambient noise. In both cases, the values 0 and 1 are transmitted by changing the fan rotation speed, but the variable parameter of the carrier signal is in the first case its amplitude, and in the second case the frequency of the carrier oscillation.
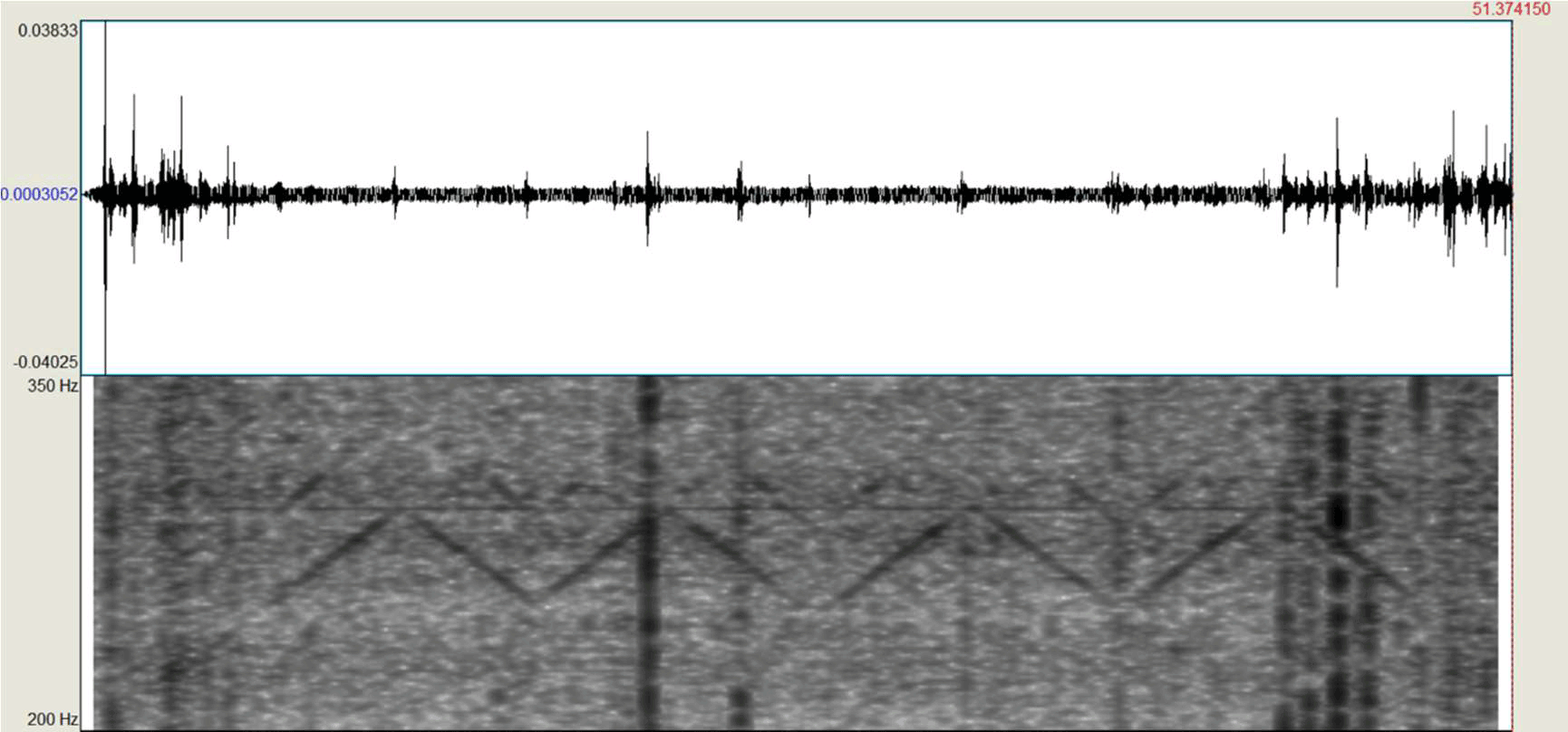
The diagrams below show the difference in the recorded signal, which is transmitted by the method of amplitude modulation (above) and frequency modulation (below). In both cases, the signal 101010 is transmitted with a time frame of 5 seconds when the fan speed changes between 1000 RPM and 1600 RPM. In the first case, the transfer was carried out within 60 seconds, in the second case - 150 seconds.

Amplitude modulation

Frequency modulation
The researchers propose to use the method of dynamic synchronization during data transmission to eliminate errors when the receiver and transmitter change their location relative to each other during transmission. With dynamic synchronization, a 4-bit control frame is transmitted before each 12-bit frame of payload.
The researchers developed a data exfiltration method on a Dell OptiPlex 9020 computer with an Intel Core i7-4790 motherboard and an Intel Q87 (Lynx Point) chipset. As already mentioned, the method is universal and can be used with computers of different models.
The Samsung Galaxy S4 (I9500) mobile phone was used as a signal receiver.
The experiment was conducted in a laboratory with a standard level of ambient noise, where several other computers and air conditioning systems operated.
The experiment showed that the speed of data transmission through the fan strongly depends on the signal-to-noise ratio (SNR). The stronger the ambient noise in relation to the useful signal - the lower the transmission rate.
This is how payload transmission looks like a sequence of bits 01010101 with different transmission parameters and at different distances between the receiver and transmitter.
Distance of 1 meter, fan rotation speed 1000-1600 RPM, B-FSK modulation method. The effective transfer rate is 3 bits per minute.

Distance 1 meter, fan speed 4000-4250 RPM, modulation method B-FSK. The effective transfer rate is 15 bits per minute.

4 meters distance, fan rotation speed 2000-2500 RPM, B-FSK modulation method. The effective transfer rate is 10 bits per minute.
In the experiment, we managed to record and decode the signal from a mobile phone at a distance of up to 8 meters. Of course, the SNR level will be much higher if you use directional microphones and other specialized equipment.
Literature
[1] MG Kuhn and RJ Anderson, "Soft Tempest: Hidden data transmission using electromagnetic emanations," Information hiding , Springer-Verlag, 1998, pp. 124-142. Back to article
[2] MG Kuhn, “Compromising emanations: Escaping risks for computer displays”, University of Cambridge, Computer Laboratory, 2003. Return to article
[3] M. Vuagnoux and S. Pasini, "Compromising Electromagnetic Wiring and Wireless Keyboards" USENIX security symposium , 2009. Return to article
[4] M. Guri, A. Kachlon, O. Hasson, G. Kedma, Y. Mirsky and Y. Elovici, "GSMem: Data Exfiltration from Air-Gapped Computers over GSM Frequencies," Washington, DC, 2015. Back to article
[5] J. Loughry and AD Umphress, “Information leakage from optical emanations,” ACM Transactions , vol. 5, no. 3, pp. 262-289, 2002. Back to article
[6] M. Guri, M. Monitz, Y. Mirski and Y. Elovici, “BitWhisper: Covert Signing Channels between Air-Gapped Computers using Thermal Manipulations,” in Computer Security Foundations Symposium (CSF), IEEE 2015. Back to article
[7] VTM t. CA-GS f. PN Attack, “Eunchong Lee; Hyunsoo Kim; Ji Won Yoon, Information Security Applications , vol. 9503, pp. 187-199, 2015. Return to article
[8] M. Hanspach and M. Goetz, “On Covert Acoustical Mesh Networks in Air”, Journal of Communications , vol. 8, 2013. Return to article
[9] A. Madhavapeddy, R. Sharp, D. Scott and A. Tse, “Audio networking: the forgotten wireless technology”, Pervasive Computing, IEEE , vol. 4, no. 3, 2008. Return to article
[10] E. Thiele, Tempest for Eliza, 2001. [Online]. Available:
www.erikyyy.de/tempest . [Accessed 4 10 2013]. Back to article
[11] Alfredo Milani Comparetti, “What is the PWM and what is the difference between Analog and Digital?”, 2004. [Online]. Available: www.almico.com/sfarticle.php?id=1 . Back to article
[12] SpeedFan, [Online]. Available: www.almico.com/sfdownload.php . Back to article
[13] Mac / SMC Fan Control for Windows (+ Temp), [Online]. Available: sourceforge.net/projects/macfan . Back to article
[14] "fanCON - Fan control for Linux systems", [Online]. Available: sourceforge.net/projects/fancon . Back to article
Source: https://habr.com/ru/post/395417/
All Articles