Mitsubishi Outlander SUV is easily cracked over Wi-Fi
Binary for remote disabling alarm will lay out in a week. Up to this point, car owners have time to deactivate Wi-Fi in the car.

A group of specialists from the British hacker company Pen Test Partners has published instructions on how to remotely (via Wi-Fi) get control over individual electronic systems of an SUV (urban crossover) Mitsubishi Outlander Hybrid. Hackers posted a five-minute video with a demonstration of hacking.
Among other things, the method allows you to turn off the car alarm. So the owners of Mitsubishi Outlander is better to deactivate the Wi-Fi access point. Although the car is very expensive (more than $ 50,000) and seems prestigious, but the security system is weak in it: the WPA-PSK key consists of eight characters and is quickly chosen by brute force.
Security vulnerability Mitsubishi Outlander is a mobile application that communicates with the machine directly. In many other cars, the mobile application establishes communication via the Internet, that is, through the company's server, but here the connection is established directly. In this respect, the Mitsubishi Outlander is different. The car has an access point, and the phone connects to it via Wi-Fi.
')
Each Mitsubishi Outlander car has a W-Fi access point with a unique name in the format [REMOTEnnaaaa], where “n” is a number, and “a” is a lower case letter.
For the owner to have direct access to the car via Wi-Fi is very convenient - right from the phone, you can turn the lights on or off at the touch of a button, remove the car from the alarm and so on.
Thieves also like this feature very much, because now they can easily track all the Mitsubishi Outlander cars in their city. Or track the movement of any particular car. You do not need to install a bug on it - just go to the search engine on WiGLE hotspots, enter the SSID and see where all the Mitsubishi Outlander are with hotspots turned on.
To connect to an access point, you must enter a key (pre-shared key) for WPA-PSK authentication. The key is indicated on a sheet of paper in the user manual. The problem is in this key - it is too short (only eight characters).
Pen Test Partners experts picked up a password in less than four days of brute force on a computer with four GPUs. If you rent an instance on AWS, then such a password is chosen "almost instantly," says one of the hackers.
After that, the question arose: if the key is chosen so simply, what other security measures are used to authenticate the smartphone, because it gets direct access to electronic vehicle control systems.
It turned out that no. No more security measures. The WPA-PSK key is enough to connect to the car and access many features.
The guys launched the program Wireshark, to study the network traffic between the access point and the host smartphone. In the case of a real attack, you need to wait for the owner to come home and park the car. After that, continuously break the connection of the smartphone with the home Wi-Fi router so that the smartphone still tries to authenticate in the vehicle's hotspot.

Intercepting traffic at the time of the connection of the smartphone with the car, we get the SSID hotspot. After examining the traffic between devices, you can organize a MiTM attack and send packets on behalf of the host smartphone.

The Wireshark program allows you to explore the packages of the original Mitsubishi Outlander Hybrid mobile application when certain commands are sent from a smartphone. Then it is enough to repeat these packets in order to duplicate the commands. From the mobile application, hackers managed to successfully turn on and off lights. Then they determined how the battery charging function is activated, so that in the event of an attack, they can deliberately start charging the car at the most expensive electricity tariff, which would cause the owner financial damage of a few dollars. In the end, they learned how to turn the air conditioning and heating system on and off, with which you can effectively discharge the battery of the Mitsubishi Outlander Hybrid (so that the financial damage to the owner increases to tens of dollars).
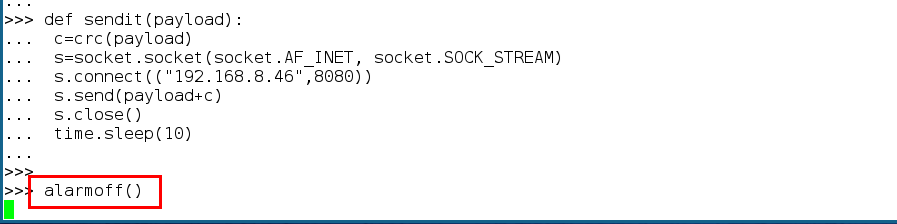
But the most important thing is that the hackers finally managed to turn off the car alarm. This is already a major achievement. Turning off the alarm, it is enough for a thief to knock out the glass in order to silently get inside the cabin and open the car door from the inside. True, the hackers did not put in open access a specific code (payload), which must be sent to disable the alarm, so you have to pick it up yourself (if there is such a desire). Or wait a week or two, when the payload still appears.
Having penetrated the salon with the alarm turned off, the attacker gets the opportunity to conduct various types of attacks. There is already direct access to the diagnostic port, so the laptop connects directly to the car computer. In the past, computer security experts have repeatedly shown what can be done in different car models, if you connect via OBD. For example, a month ago, one pretty owner of the Tesla car and an experienced hacker-linux under the nickname Hemera even managed to hack into the computer system and install their favorite Gentoo operating system there instead of the built-in Ubuntu, which Ilon Mask prefers.
Hackers say that with the internal network stuffing SUV still have to figure out in more detail. Well, they offer a temporary solution to the owners of Mitsubishi Outlander Hybrid cars: deactivate the Wi-Fi access point. To do this, you must first connect to the hotspot from your smartphone, then go to the settings of the mobile application (Settings) and select the 'Cancel VIN Registration' option.

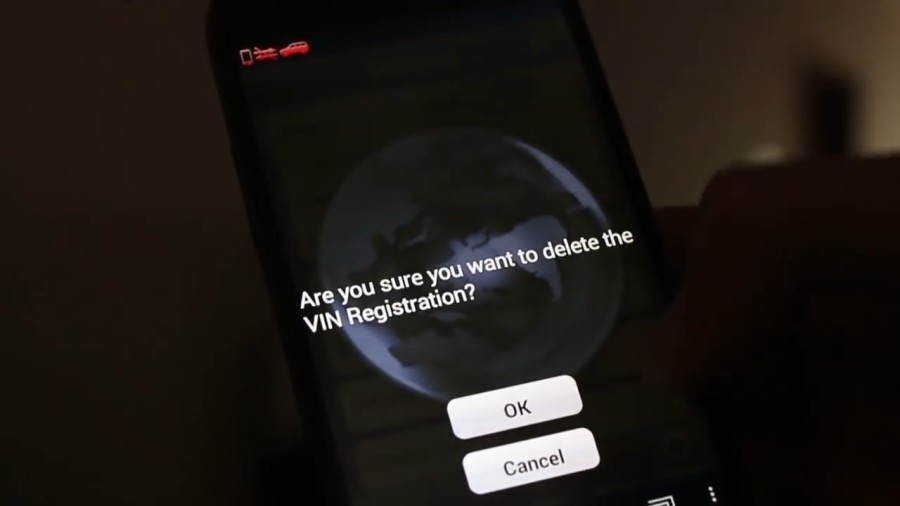
When all mobile devices are turned off, the Wi-Fi module in the vehicle is deactivated. It can no longer be activated until you press the button on the remote control key ten times in a row. “A cool security feature,” commented the guys from Pen Test Partners.
Hackers believe that the manufacturer should urgently release a firmware update for the Wi-Fi wireless module in order to eliminate the security vulnerability. By installing a new firmware, motorists can activate car hotspot back and use the mobile application again.
In general, experts recommend Mitsubishi to abandon the use of Wi-Fi to communicate with a smartphone, and switch to more modern web technologies by connecting to the phone via the Internet via GSM.
As it should be, the Pen Test Partners group notified Mitsubishi in advance about the bug, but their information did not arouse any interest from the automaker. Then the hackers contacted the BBC television channels and made a short story on television. “From this point on, Mitsubishi has become very responsive,” they say.
Hackers promise to lay out a binary to turn off the alarm after a week or two, leaving enough time for car owners to turn off the alarm.
Source: https://habr.com/ru/post/395147/
All Articles