Microphone and cryptography: extract 4,096-bit RSA keys from a distance of 10 meters
It is possible to protect against “acoustic crypto attacks”, but it is very difficult.

Equipment used during acoustic crypto attacks
A well-known expert in the field of cryptography, Adi Shamir (Adi Shamir) for several years working on a project of acoustic extraction of cryptographic keys. He began research in this area back in 2004 , and now he continues to improve the methods of “acoustic cryptanalysis”. The problem that Shamir is working on with the team is the ability to extract RSA keys using a microphone — a quality dedicated or smartphone microphone.
')
Earlier, an expert with a team of colleagues (it includes software developer Lev Pakhmanov) published a paper with a demonstration of the practical implementation of his idea. They managed to extract the RSA keys from a distance of 4 meters using a conventional parabolic microphone, and from a distance of 30 centimeters using a smartphone’s microphone. Now experts have improved the result, learning how to extract keys from a distance of 10 meters.
As mentioned above, now the developers have achieved a new result in terms of acoustic key extraction. The work is based on the effect of generating high-frequency sounds by working laptops and desktop PCs. These sounds are generated by a number of electronic components of computer systems, and it is these acoustic signals after analysis that reveal all the secrets of your PC, including software identification, cryptographic keys and a number of other data. More than 10 years ago, Adi Shamir pointed out the theoretical possibility of doing such work. But the practical implementation of the project followed 9 years later , when developer Lev Pakhmanov joined the team of researchers. Researchers are still working as a team, and this month they published a new article with the results of their project.
According to experts, for a long time, it was believed that reading information from a PC or laptop is possible only with direct physical (or remote) access to it. But the problem is that the processors of our PCs and laptops consist of a billion transistors, on the motherboard - a lot of miniature semiconductor elements. All this when working produces a high-frequency sound, which serves as a source of information about the victim's computer.
The authors decided to find answers to two questions. The first is whether it is possible to carry out a successful attack on a computer without gaining physical access to it and generally penetrating the system. The second question is the price, the cost of equipment, software and everything else that may be needed for such work. As mentioned above, both answers to these questions were found successfully. With the implementation of the “acoustic attack”, the experts managed to extract the 4096-bit key for about an hour. The work was carried out from a distance of 10 meters using a parabolic microphone. Also, similar work was carried out from a distance of 30 centimeters, using only the smartphone's microphone.
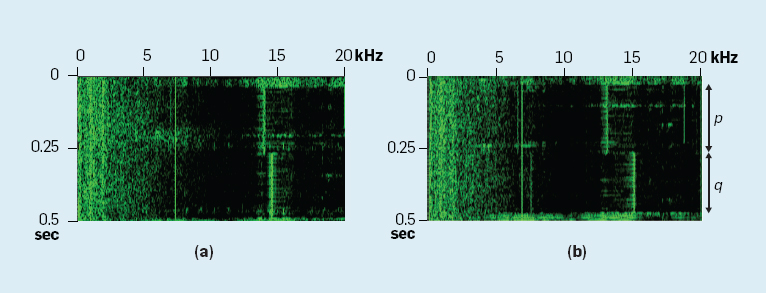
Laptop acoustic signal during operation
Research co-authors claim that an acoustic attack is not the only way to extract encryption keys. This can be done using other, faster methods — for example, analyzing the electric or electromagnetic fields of a target PC or laptop. This is a much faster channel for getting information.
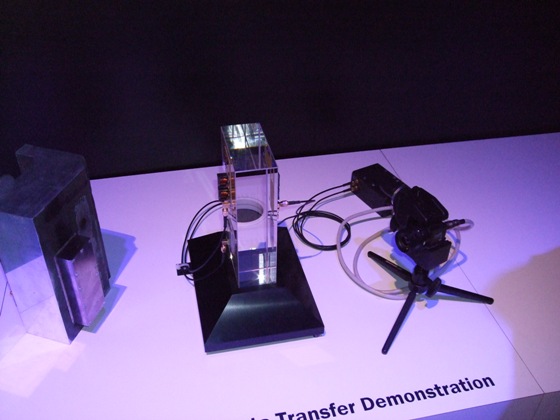
Researchers confirm the words with a deed: the same team proved the ability to extract keys from GnuPG on laptops within a few seconds by analyzing electromagnetic radiation when decoding coded text on a laptop. Scientists used the Funcube Dongle Pro +, connected to a small Android-based computer Rikomagic MK802 IV. The system worked only with a range of 1.6-1.75 MHz. As it turned out, you can even work with the usual AM radio connected to a smartphone. Such a system is practically worthless, however, for the practical implementation of the idea, special software is needed, which not everyone can write. But the cryptographers coped, and got a really working system.

“Electric crypto-attack”, where a person is the main tool for intercepting electrical signals
True, physical access to the victim’s computer or laptop is already required here — you need to connect either a regular explorer or some additional systems like Funcube Dongle Pro +. This is not always possible to do. However, the experts successfully carried out an attack on PCs or laptops with different versions of GnuPG, which use different types of implementations of targeted encryption algorithms.
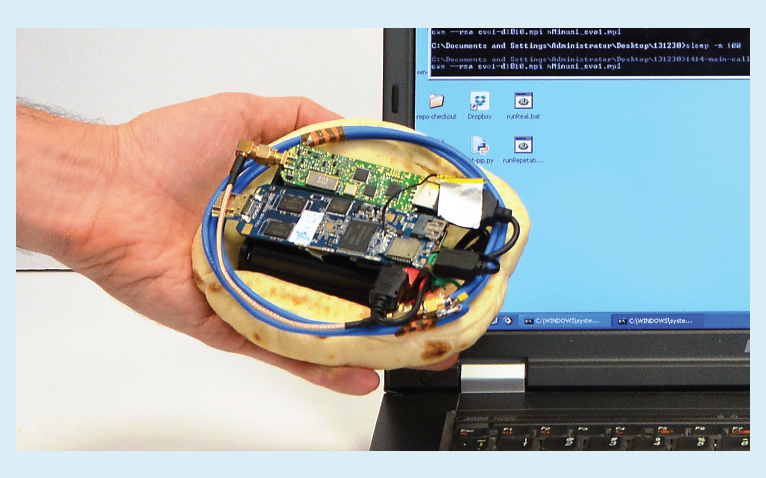
And this is an electromagnetic cryptaka (the receiver is hidden in the bread, yes)
How to protect yourself?
Yes, the authors of the work also offer methods of protection against the types of attacks they detect. This, for example, sound-absorbing coating of computer equipment, if we are talking about an acoustic attack. In the case of an electromagnetic attack, a “Faraday cage” can help, plus a fiber optic connection to the network and optoelectronic isolation. True, such methods of protection are not always convenient and quite costly. Therefore, the issue of protecting conventional laptops and desktop PCs remains open.
You can also use software protection. According to researchers, the software implementation of cryptographic algorithms should be designed in such a way as to exclude the possibility of analyzing and deciphering an acoustic or electromagnetic signal. This may be “digital noise” with obviously incorrect data, algorithmic modifications that complicate the analysis and other methods.

Equipment used during acoustic crypto attacks
A well-known expert in the field of cryptography, Adi Shamir (Adi Shamir) for several years working on a project of acoustic extraction of cryptographic keys. He began research in this area back in 2004 , and now he continues to improve the methods of “acoustic cryptanalysis”. The problem that Shamir is working on with the team is the ability to extract RSA keys using a microphone — a quality dedicated or smartphone microphone.
')
Earlier, an expert with a team of colleagues (it includes software developer Lev Pakhmanov) published a paper with a demonstration of the practical implementation of his idea. They managed to extract the RSA keys from a distance of 4 meters using a conventional parabolic microphone, and from a distance of 30 centimeters using a smartphone’s microphone. Now experts have improved the result, learning how to extract keys from a distance of 10 meters.
As mentioned above, now the developers have achieved a new result in terms of acoustic key extraction. The work is based on the effect of generating high-frequency sounds by working laptops and desktop PCs. These sounds are generated by a number of electronic components of computer systems, and it is these acoustic signals after analysis that reveal all the secrets of your PC, including software identification, cryptographic keys and a number of other data. More than 10 years ago, Adi Shamir pointed out the theoretical possibility of doing such work. But the practical implementation of the project followed 9 years later , when developer Lev Pakhmanov joined the team of researchers. Researchers are still working as a team, and this month they published a new article with the results of their project.
According to experts, for a long time, it was believed that reading information from a PC or laptop is possible only with direct physical (or remote) access to it. But the problem is that the processors of our PCs and laptops consist of a billion transistors, on the motherboard - a lot of miniature semiconductor elements. All this when working produces a high-frequency sound, which serves as a source of information about the victim's computer.
The authors decided to find answers to two questions. The first is whether it is possible to carry out a successful attack on a computer without gaining physical access to it and generally penetrating the system. The second question is the price, the cost of equipment, software and everything else that may be needed for such work. As mentioned above, both answers to these questions were found successfully. With the implementation of the “acoustic attack”, the experts managed to extract the 4096-bit key for about an hour. The work was carried out from a distance of 10 meters using a parabolic microphone. Also, similar work was carried out from a distance of 30 centimeters, using only the smartphone's microphone.

Laptop acoustic signal during operation
Research co-authors claim that an acoustic attack is not the only way to extract encryption keys. This can be done using other, faster methods — for example, analyzing the electric or electromagnetic fields of a target PC or laptop. This is a much faster channel for getting information.

Researchers confirm the words with a deed: the same team proved the ability to extract keys from GnuPG on laptops within a few seconds by analyzing electromagnetic radiation when decoding coded text on a laptop. Scientists used the Funcube Dongle Pro +, connected to a small Android-based computer Rikomagic MK802 IV. The system worked only with a range of 1.6-1.75 MHz. As it turned out, you can even work with the usual AM radio connected to a smartphone. Such a system is practically worthless, however, for the practical implementation of the idea, special software is needed, which not everyone can write. But the cryptographers coped, and got a really working system.

“Electric crypto-attack”, where a person is the main tool for intercepting electrical signals
True, physical access to the victim’s computer or laptop is already required here — you need to connect either a regular explorer or some additional systems like Funcube Dongle Pro +. This is not always possible to do. However, the experts successfully carried out an attack on PCs or laptops with different versions of GnuPG, which use different types of implementations of targeted encryption algorithms.

And this is an electromagnetic cryptaka (the receiver is hidden in the bread, yes)
How to protect yourself?
Yes, the authors of the work also offer methods of protection against the types of attacks they detect. This, for example, sound-absorbing coating of computer equipment, if we are talking about an acoustic attack. In the case of an electromagnetic attack, a “Faraday cage” can help, plus a fiber optic connection to the network and optoelectronic isolation. True, such methods of protection are not always convenient and quite costly. Therefore, the issue of protecting conventional laptops and desktop PCs remains open.
You can also use software protection. According to researchers, the software implementation of cryptographic algorithms should be designed in such a way as to exclude the possibility of analyzing and deciphering an acoustic or electromagnetic signal. This may be “digital noise” with obviously incorrect data, algorithmic modifications that complicate the analysis and other methods.
Source: https://habr.com/ru/post/394963/
All Articles